ANY.RUN community analyses an average of 6000 files and websites every day. That means that researchers submit 42,000 potentially malicious resources every week, 168,000 every month. And we are just one service. The variety and the sheer number of attack groups and malicious tools today are incredible.
Danger can come in so many shapes and forms that absolutely nobody — not even the most prepared and well equipped of cybersecurity teams — can categorize and learn the behavior of each threat. That’s a problem. We all know the most effective way of protecting against an attack: learning the threat’s behavior.
Enter the ATT&CK framework by MITRE. It came up with ATT&CK all the way back in 2003 to help the cybersecurity industry overcome the seemingly impossible challenge of learning the behavior of hundreds of malware samples. Since then, the framework became a staple in cybersecurity.
MITRE created a common classification for malicious behaviors and the most comprehensive database of adverse techniques on the planet. So, let’s talk about the MITRE ATT&CK framework and why you, as a malware hunter, should start using it today.
What is the Mitre ATT&CK Framework?
MITRE ATT&CK is a constantly updated database of adversary tactics and techniques. The framework looks like a sheet document with columns correlating to attack stages, from initial access to impact, and rows correlating to techniques.
Each technique is a description of malware behavior derived from real-world recordings of previous attacks: information in the MITRE framework has represents years of experience and observations, collected, сottegorzed, and described in a single place. Researchers can easily apply the knowledge learned by studying the MITRE ATT&CK table since it represents real-world malware behavior.
How to use MITRE ATT&CK to benefit the cybersecurity of your organization?
There are a lot of ways to use the framework. These are some of the most common:
- Behavioral analytics: when executing, a malicious program generates files, establishes connections, and alters processes. These actions are traceable and can help identify an ongoing attack, aid during analysis, or develop a cybersecurity strategy to protect against known malware strains. With MITRE ATT&CK, researchers can study the behavior of any known malware, which is greatly beneficial.
- Attack group identification: MITRE ATT&CK connects techniques with attack groups. Some attack groups focus on particular industries, so analysts can identify threats that pose the most danger to their business, depending on the field, and develop custom-tailored defenses and response strategies.
- Defense evaluation: by learning which malware is likely to attack business and what processes it is going to spawn, analysts can evaluate how effective their countermeasures will be without putting themselves into any kind of danger.
How to Use the MITRE ATT&CK Framework in ANY.RUN?
MITRE ATT&CK makes it much easier to understand how a particular malware sample functions. In ANY.RUN, you can bring up the ATT&CK matrix for any given sample to study its behavior.
What’s more, you can click on any technique to bring up a detailed explanation.
Let’s say we are analyzing one of the most active malware strains out there — Agent Tesla.
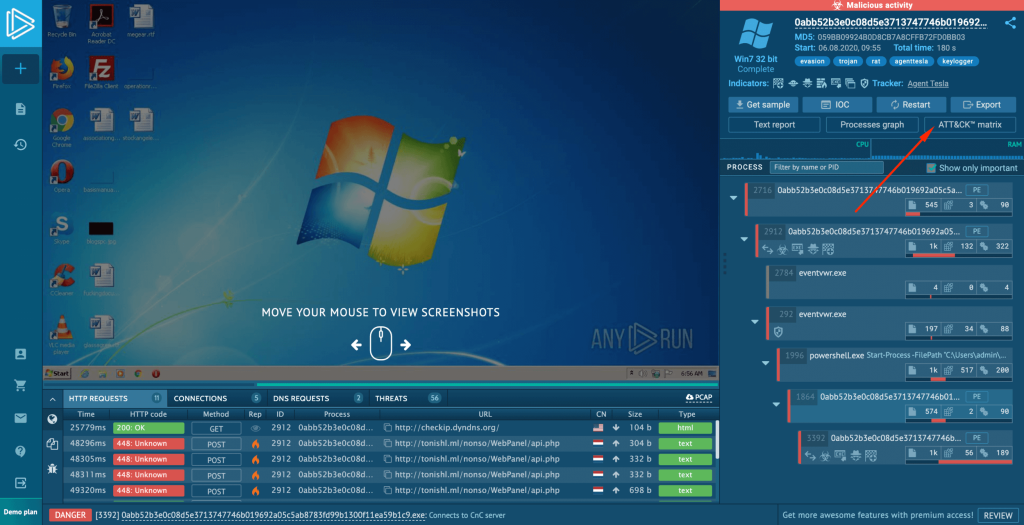
Clicking on the “ATT&CK Matrix” button will bring up the framework.
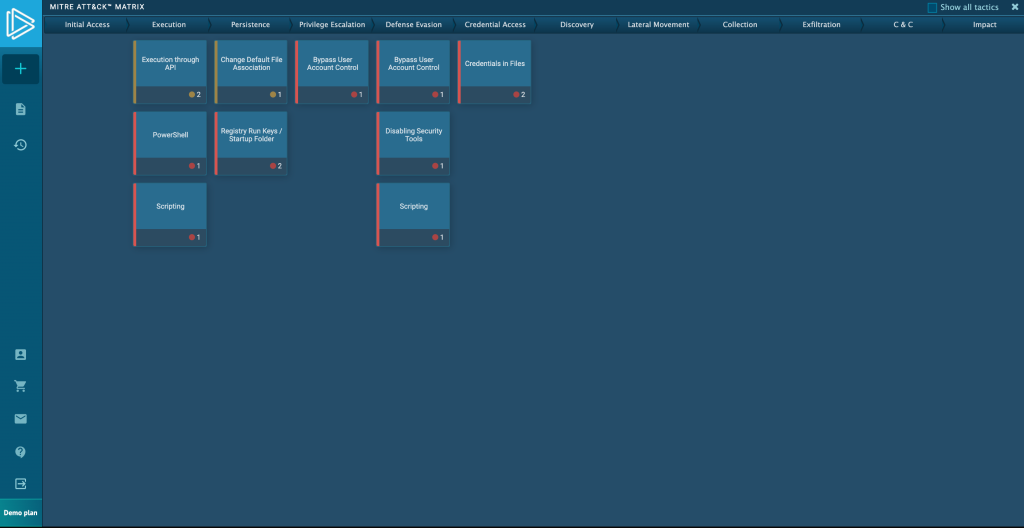
Here, you will be able to see documented techniques associated with this malware.
Clicking on a technique will bring up the expanded description, process ID, and name. You can go even further by clicking on the indicator: this will bring up the additional details, like registry keys and the command line input.
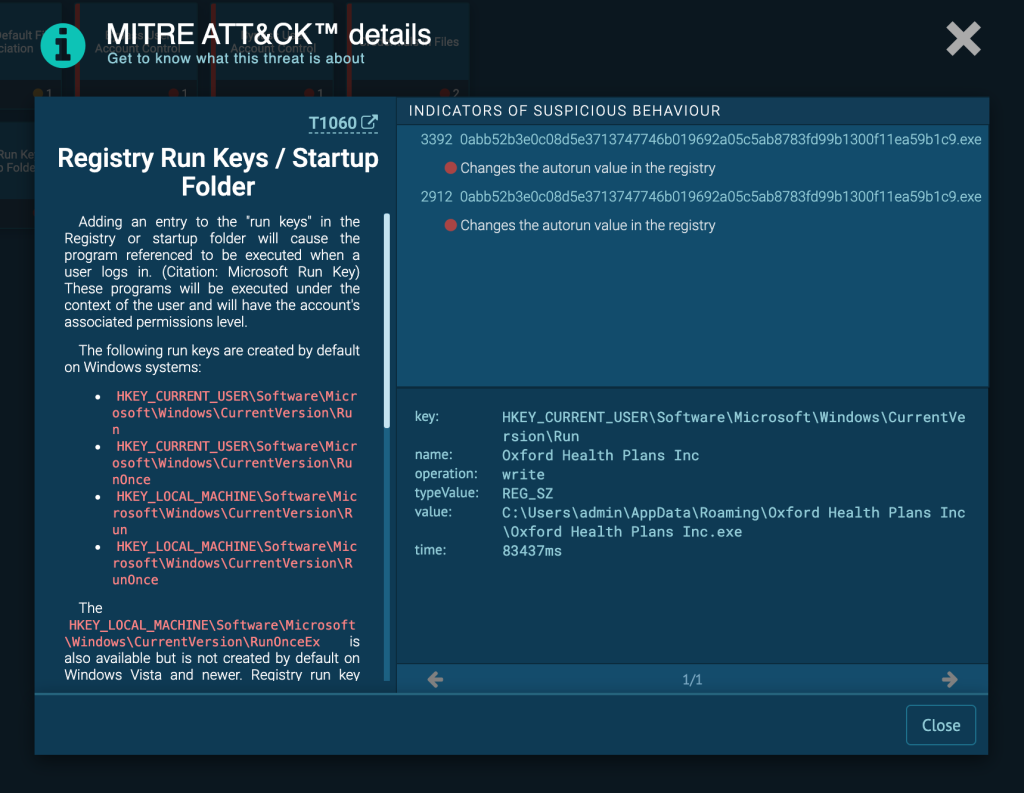
The arrows on the bottom switch between events if there were more than one of them.
But what if you want to see all techniques, not just those related to a particular sample? That’s easy enough: just use the “Show all tactics” checkbox at the top-right of the screen.
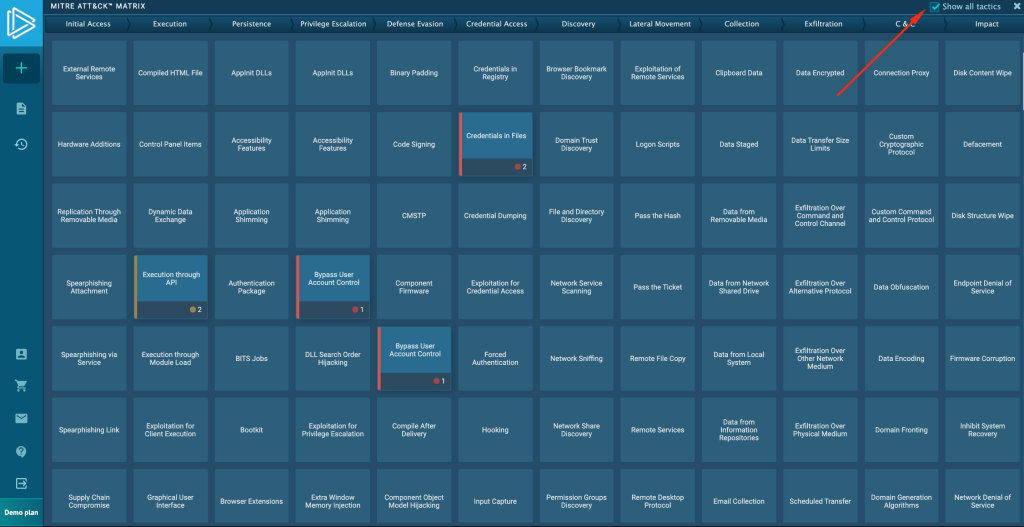
Techniques related to the reviewed malware will be highlighted on the screen.
You can also search for other malware that uses the same attack techniques as the sample which you were viewing.
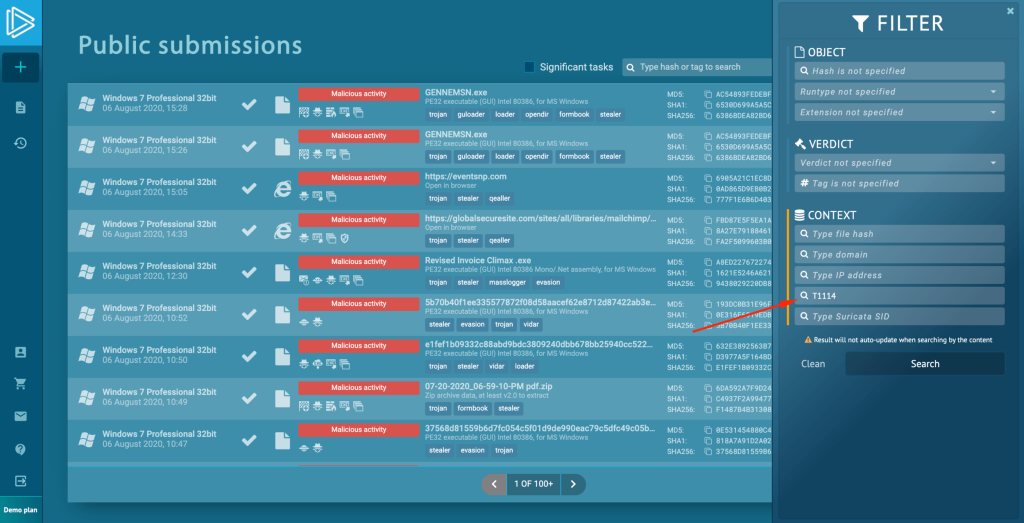
To do so, just copy and paste the MITRE ID into the ATT&CK filed on the public submissions page. This function is useful for learning how attackers use any given technique in different malware strains.
There are a few ways how you can use the search function. Netwalker ransomware uses “Visual C# command-line compiler”. By filtering with the correlating MITRE ATT&CK ID, we can find a particular malware type.
Or, if we are looking at Masslogger, we notice a technique called “Email collection“, with a MITRE ID T1114. If we search with this number, we can find other malware that can steal sensitive information from emails.
Conclusion
The MITRE ATT&CK framework is one of the most robust tools in the arsenal of a cyber-security professional. It can be used to learn about the behavior of countless malware strains and can help incorporate that knowledge into the web-defense of a business.
The framework is also a great way for beginner malware hunters to learn about malware behavior: it provides context and allows searching for malware with the same functions and techniques.
Hopefully, this article gave you an idea of how to use MITRE ATT&CK in conjunction with ANY.RUN public submissions. Together, these two tools allow researchers with any experience level to quickly and efficiently find particular malware samples, or learn about new strains with similar behavior or capabilities.
If you haven’t used MITRE ATT&CK before, make sure you give it a try!
3 comments







I conceive you have remarked some very interesting details, appreciate it for the post.
Thanks so much for sharing the information.
Hi Irene,
Thank you for your kind words.
Consider checking out other articles from us at https://any.run/cybersecurity-blog/.
Best,
The ANY.RUN team