Welcome to ANY.RUN’s Q2 2023 malware trends report. We’re continuing to share quarterly breakdowns of the most popular malware types, families, and TTPs.
Summary
In our most recent quarterly review, ANY.RUN received 758,582 submissions. From this pool, we classified 226,418 tasks, or 29.9%, as malicious, and another 34,285, or 4.5%, as suspicious.
Our users, through their analysis of these tasks, managed to gather approximately 45 million unique Indicators of Compromise (IOCs) and an accumulative total of 240,581,447 IOCs.

In this report, we’ll:
- Look at the most widespread malware types and families in Q2 2023
- Compare our findings to Q1 2023 report.
- And provide insights into the most used MITRE ATT&CK TTPs
Top Malware Types in Q2 2023
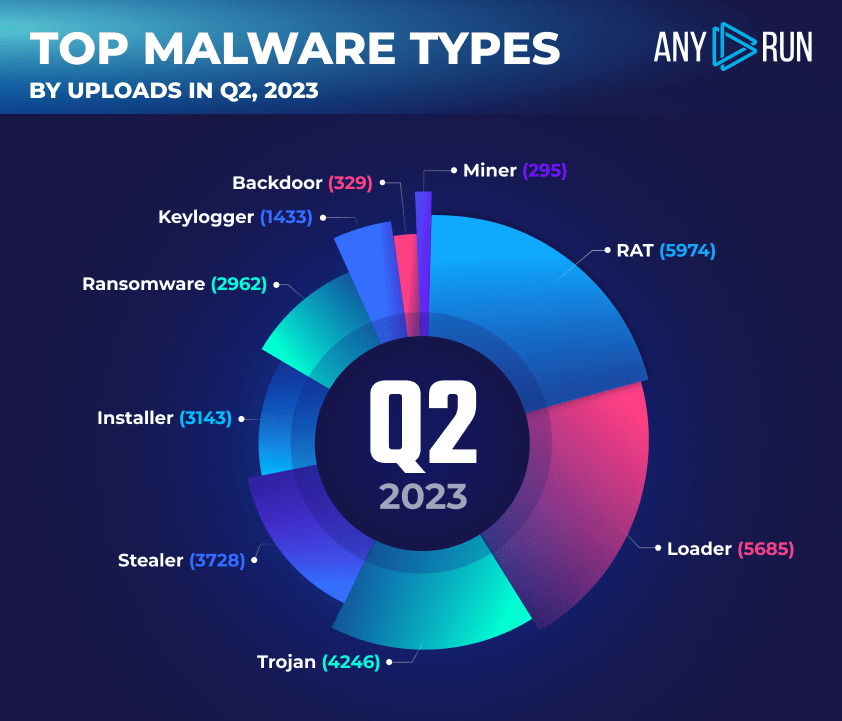
Highlights
In Q2 2023, the three most prevalent types of malware remained RAT, loader, and trojan, mirroring the trends from Q1 2023.
Specifically, we observed a 12.8% increase in RAT instances, rising from 5296 in Q1 to 5974 in Q2. Conversely, loader instances saw a decrease of 27.3%, dropping from 7820 in Q1 to 5685 in Q2. Most notably, trojan instances experienced a significant decrease of 44.8%, plummeting from 7696 in Q1 to just 4246 in Q2.
Top Malware Families in Q2 2023
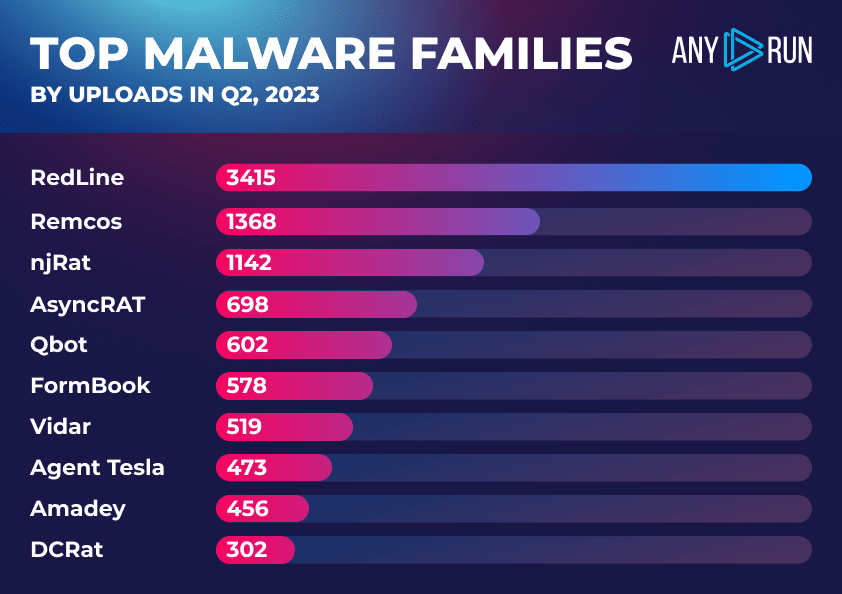
Highlights:
- The hierarchy of top malware families remains unchanged. RedLine, the most prevalent malware family, saw a significant surge in instances, jumping 80.2% from 1895 in Q1 to 3415 in Q2.
- Remcos, holding steady as the second most frequently uploaded malware on ANY.RUN, experienced a marginal decrease of 1.2%, with instances dipping slightly from 1385 in Q1 to 1368 in Q2.
- Rounding out the top three, the njRat family exhibited a modest increase of 4.2%, with instances rising from 1096 in Q1 to 1142 in Q2.
Top MITRE ATT&CK techniques in Q2 2023
| MITRE ATT&CK Technique | Count |
| T1059.003 Command and Scripting Interpreter: Windows Command Shell | 14,233 |
| T1059.001 Command and Scripting Interpreter: PowerShell | 9,081 |
| T1497.003 Virtualization/Sandbox Evasion: Time Based Evasion | 8,130 |
| T1218.011 System Binary Proxy Execution: Rundll32 | 5,505 |
| T1053.005 Scheduled Task/Job: Scheduled Task | 5,450 |
| T1547.001 Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | 4,919 |
| T1574.002 Hijack Execution Flow: DLL Side-Loading | 3,817 |
| T1059.005 Command and Scripting Interpreter: Visual Basic | 3,672 |
| T1059.007 Command and Scripting Interpreter: JavaScript | 3,054 |
| T1222.001 File and Directory Permissions Modification: Windows File and Directory Permissions Modification | 2,986 |
Highlights:
The data we’ve collected during the second quarter of 2023 indicates a significant shift in most-used TTPs. Here are some of the highlights:
- T1059.003, Command and Scripting Interpreter: Windows Command Shell, despite experiencing a significant drop in instances from 22,030 in Q1 to 14,233 in Q2 (a decrease of 35.4%), has moved up in the ranking to become the most prevalent technique in Q2.
- T1059.001, Command and Scripting Interpreter: PowerShell, has also climbed in the ranking, moving from the tenth position in Q1 to the second in Q2. This is in spite of a relatively small increase in instances from 8,209 in Q1 to 9,081 in Q2 (an increase of 10.6%).
- T1497.003, Virtualization/Sandbox Evasion: Time Based Evasion, has also risen in the ranking, moving from the seventh position in Q1 to the third in Q2.
- Notably, T1036.005, Masquerading: Match Legitimate Name or Location, which was the most prevalent technique in Q1 with 78,101 instances, is no longer in the top ten in Q2.
Report methodology
We’ve examined data submitted to our public threat database by a diverse community of researchers, who have opted to make their analyses public, totaling 758,582 tasks.
ANY.RUN is a cloud malware sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams. Every day, 300,000 professionals use our platform to investigate incidents and streamline threat analysis.
Request a demo today and enjoy 14 days of free access to our Enterprise plan.








0 comments