We’re excited to share ANY.RUN‘s latest malware trends analysis for Q2 2024! Our quarterly update provides insights into the most widely deployed malware families, types, and TTPs we saw during the last 3 months of the year.

Summary
In Q2 2024, ANY.RUN users ran 881,466 public interactive analysis sessions, which is a 0.5% increase from Q1 2024. Out of these, our data marks 162,258 (18.4%) as malicious, and 61,619 (7.0%) — suspicious.
Compared to last quarter, the percentage of malicious tasks increased slightly from 17.8% in Q1 2024 to 18.4% in Q2 2024. The share of suspicious tasks also saw a big increase from 3.5% to 7.0%.
As for IOCs, users collected a total of 351,423,662 IOCs this quarter, and 73,233,314 (20.8%) of them were unique.
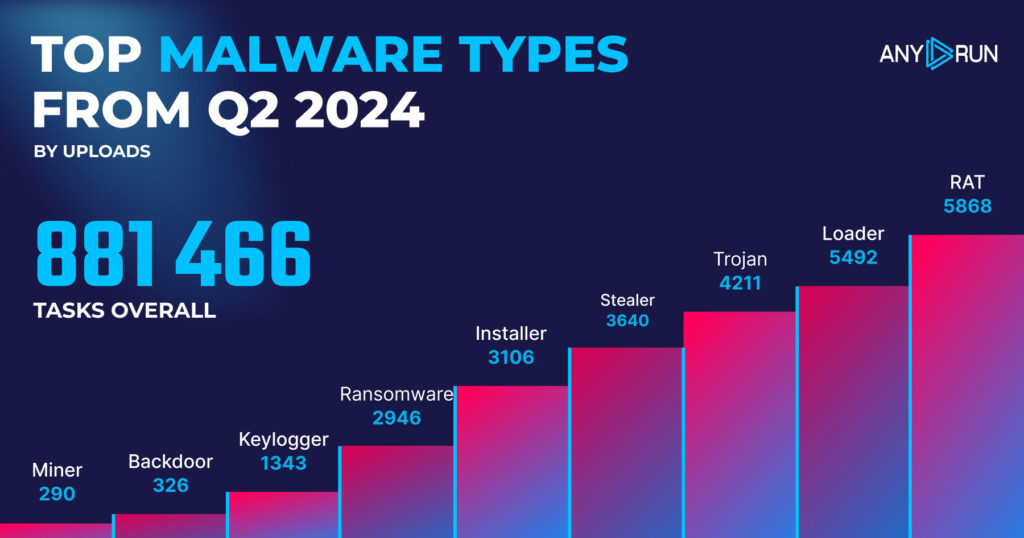
Top Malware Types in Q2 2024
Let’s take a closer look at the most common malware types identified by ANY.RUN’s sandbox.
- RAT: 5868
- Loader: 5492
- Trojan: 4211
- Stealer: 3640
- Installer: 3106
- Ransomware: 2946
- Keylogger: 1343
- Backdoor: 326
- Miner: 290
Let us show you how ANY.RUN can help your SOC team – book a call with us ⬇️
Top malware types: highlights
In Q2 2024, there were big shifts in the malware landscape compared to the previous quarter. RATs have taken the lead as the most prevalent malware type, with 5,868 detections. This is an increase from Q1 2024, where RATs were in second place with 4,956 detections.
Loaders maintained a strong presence, slightly increasing from 4,770 in Q1 to 5,492 in Q2, securing the second position. Trojans made a notable entry into the top three with 4,211 detections.
Stealers, which were the most common threat in Q1 with 5,799 detections, have dropped to fourth place with 3,640 detections in Q2. This represents a decrease of 37.2% in stealer activity.
A new category, Installers, appeared in the top five with 3,106 detections. Ransomware detections decreased from 4,065 in Q1 to 2,946 in Q2, a 27.5% reduction, moving it to sixth place.
Keylogger detections remained relatively stable, with a slight decrease from 1,682 in Q1 to 1,343 in Q2. Backdoor and Miner detections saw minor changes, maintaining their positions at the bottom of the list with 326 and 290 detections respectively.
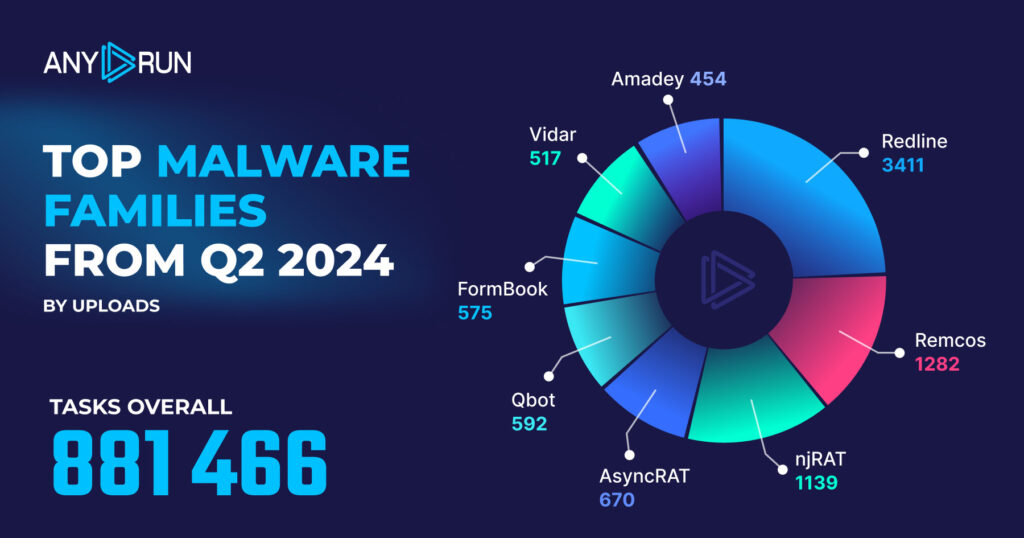
Top Malware Families in Q2 2024
- RedLine: 3411
- Remcos: 1282
- NjRAT: 1139
- AsyncRAT: 670
- Qbot: 592
- Formbook: 575
- Vidar: 517
- Amadey: 454
- AgentTesla: 439
- DCRat: 299
In Q2 2024, RedLine has made a dramatic comeback, surging to the top spot with 3,411 instances. This represents a 379% increase from its fifth-place position in Q1 (712 instances), making it by far the most prevalent threat this quarter.
- Remcos, which led in Q1 with 1,817 instances, has dropped to second place with 1,282 instances – a 29.4% decrease.
- NjRAT maintained its third-place position, with a slight decrease from 1,219 to 1,139 instances.
- AsyncRAT saw a considerable drop, with 670 instances, a 42% decrease from its 1,155 detections in Q1.
- Qbot has emerged as a new entrant in the top 5, securing the fifth position with 592 instances.
- Formbook and Vidar have both moved up in the rankings, now occupying the sixth and seventh spots respectively.
- AgentTesla, which was the second most prevalent malware in Q1 with 1,739 instances, has dramatically fallen to ninth place with only 439 instances, marking a 74.8% decrease.
- DCRat rounds out the top 10, showing a slight decrease from 388 to 299 instances but maintaining its presence in the list.
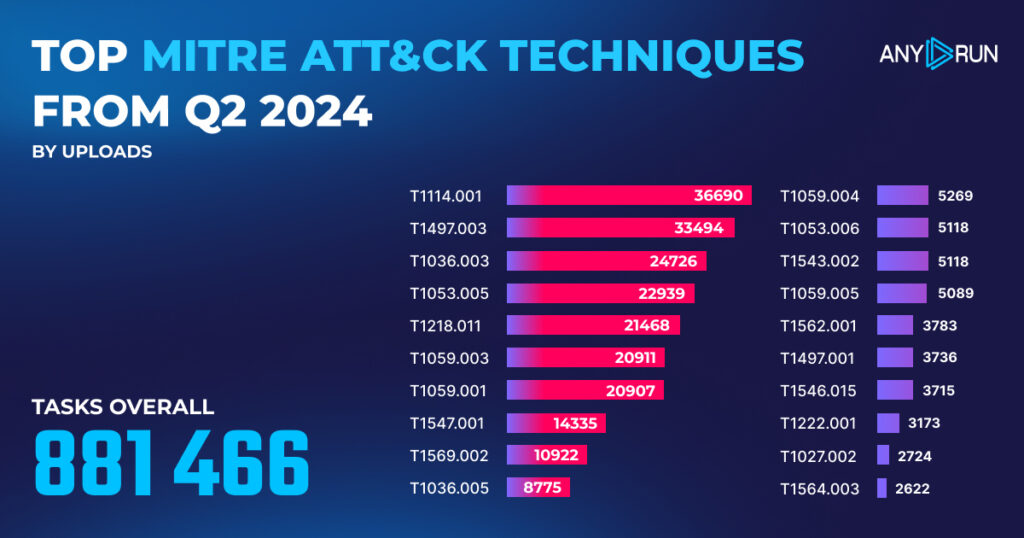
Top MITRE ATT&CK techniques in Q2 2024
The MITRE ATT&CK framework categorizes adversary behavior into tactics and techniques, helping malware analysts more efficiently identify, assess, and respond to threats. Here are the top 20 techniques observed in Q2 2024:
| # | MITRE ATT&CK Technique | № of detections |
|---|---|---|
| 1 | Email Collection: Local Email Collection, T1114.001 | 36,690 |
| 2 | Virtualization/Sandbox Evasion: Time Based Evasion, T1497.003 | 33,494 |
| 3 | Masquerading: Rename System Utilities, T1036.003 | 24,726 |
| 4 | Scheduled Task/Job: Scheduled Task, T1053.005 | 22,939 |
| 5 | System Binary Proxy Execution: Rundll32, T1218.011 | 21,468 |
| 6 | Command and Scripting Interpreter: Windows Command Shell, T1059.003 | 20,911 |
| 7 | Command and Scripting Interpreter: PowerShell, T1059.001 | 20,907 |
| 8 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder, T1547.001 | 14,335 |
| 9 | System Services: Service Execution, T1569.002 | 10,922 |
| 10 | Masquerading: Match Legitimate Name or Location, T1036.005 | 8,775 |
| 11 | Command and Scripting Interpreter: Unix Shell, T1059.004 | 5,269 |
| 12 | Scheduled Task/Job: Cron, T1053.006 | 5,118 |
| 13 | File Execution: Exploitation for Client Execution, T1543.002 | 5,118 |
| 14 | Command and Scripting Interpreter: Visual Basic, T1059.005 | 5,089 |
| 15 | Impair Defenses: Disable or Modify Tools, T1562.001 | 3,783 |
| 16 | Virtualization/Sandbox Evasion: System Checks, T1497.001 | 3,736 |
| 17 | Event Triggered Execution: XDG Autostart Entries, T1546.015 | 3,715 |
| 18 | File and Directory Permissions Modification: Windows File and Directory Permissions Modification, T1222.001 | 3,173 |
| 19 | Obfuscated Files or Information: Software Packing, T1027.002 | 2,724 |
| 20 | Hide Artifacts: Hidden Window, T1564.003 | 2,622 |
- T1114.001 (Email Collection: Local Email Collection) retained its top position, with a slight increase from 32,967 to 36,690 detections.
- T1497.003 (Virtualization/Sandbox Evasion: Time Based Evasion) remained in second place, with detections increasing from 24,949 to 33,494.
- T1053.005 (Scheduled Task/Job: Scheduled Task) saw a dramatic rise, jumping from the 11th position with 5,025 detections in Q1 to the 4th position with 22,939 detections in Q2 – that’s a 356% increase.
- T1059.003 (Command and Scripting Interpreter: Windows Command Shell) dropped from 4th to 6th place showing similar detection numbers around 20,000.
- T1053.006 (Scheduled Task/Job: Cron), a new technique, appeared in the 12th position with 5,118 detections.
Report methodology
For our report, we looked at data from 881,466 interactive analysis sessions. This information comes from researchers in our community who contributed by running public analysis sessions in ANY.RUN.
About ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Advantages of ANY.RUN
ANY.RUN helps you analyze threats faster while improving detection rates. The platform detects common malware families with YARA and Suricata rules and identifies malware behavior with signatures when detection by family is not possible.
With ANY.RUN you can:
- Detect malware in under 40s.
- Interact with samples in real time.
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior.
- Collaborate with your team
- Scale as you need.








0 comments