Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases
A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection.

 779
779
 0
0

 476
476
 0
0

 2720
2720
 0
0
Loaders, also known as downloaders, are a type of malware that is built for the purpose of penetrating the security infrastructure of devices and subsequent delivery of malicious payloads. This kind of malware is used during the initial stage of multi-stage malware attacks to download and execute the core malware on a compromised system.
Loaders are usually developed and run by organized crime groups that specialize solely in infiltrating computers and then charging clients, various threat actors, for deploying their specific malware on these endpoints. The particular type of malware deployed on infected systems by loaders ranges from spyware to ransomware and even other loaders.
Since loaders are a type of remote access trojans (RATs), they allow their operators to maintain full or partial remote control over compromised endpoints. This is usually done through a control panel. For instance, in the case of PrivateLoader, criminals can track their activity, including the overall number of successful installations, as well as add and remove extra payloads that they wish to deliver to infected devices.
Although loaders are designed with the sole purpose in mind of spreading other malware across compromised systems, developers often equip them with a range of other advanced capabilities, directly or indirectly related to their primary functionality. As a result, most loaders can:
Many loaders are modular, meaning that they can be easily configured to carry out extra functions by simply integrating the corresponding module. For instance, Smoke Loader has an additional capability of stealing data on victims’ devices. It not only collects system information, but also passwords and other credentials from browsers and apps and then exfiltrates them to the attacker.
Threat actors employ a variety of methods to spread loader malware. One of the most common methods is through phishing campaigns. These campaigns involve sending emails to unsuspecting users that appear to be from legitimate organizations or individuals. Such emails often contain a link to a malicious website or an attachment in the form of a document or archive. When users download and run these attached files, they trigger an infection chain that leads to the deployment of a loader on their system and the subsequent delivery of additional payloads.
Prevent loader infection by proactively analyzing suspicious files in the ANY.RUN sandbox – request a demo.
Another common way for loaders to find their way onto users' computers is through fake software. For example, GCleaner, a loader that disguises itself as a legitimate PC program, actually just downloads and installs other malware. It operates based on a pay-per-install model, where criminals pay GCleaner operators each time their payload is dropped on an infected system.
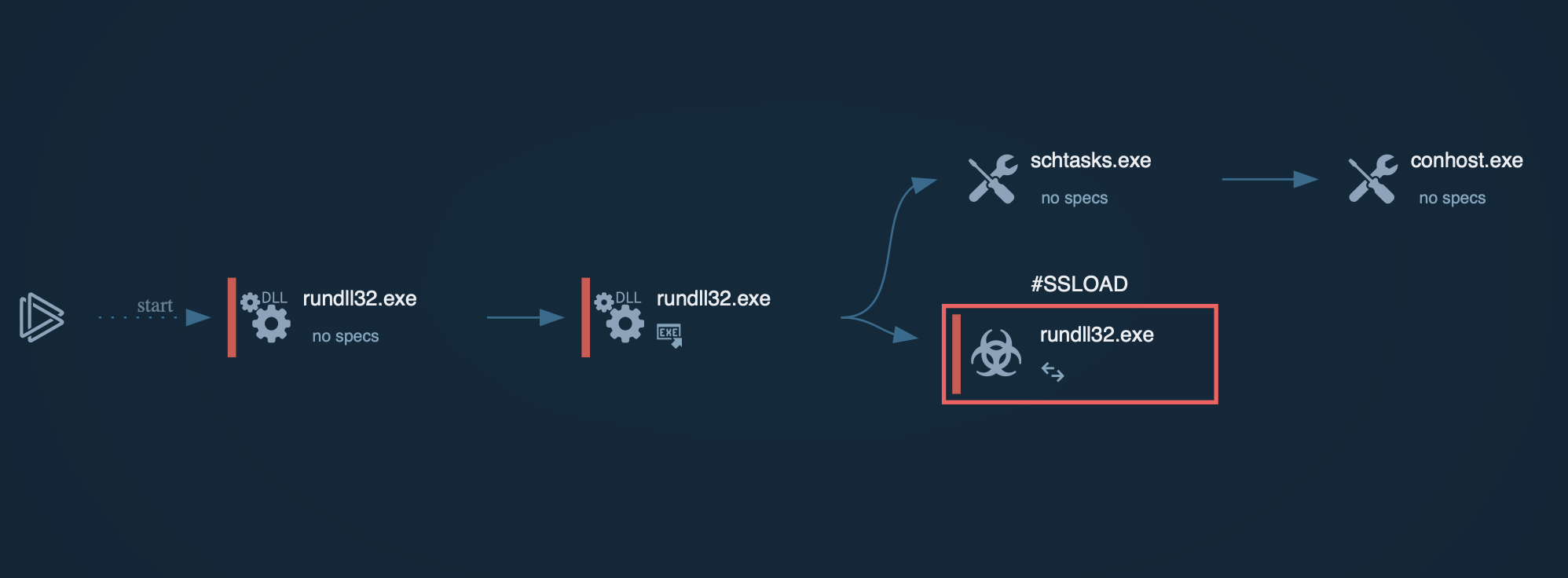
Once loaders are launched, they first establish persistence on the infected machine through various mechanisms. For instance, they can create new processes or exploit legitimate Windows processes’ privileges. This allows loaders to avoid detection by security software. To ensure that the loader remains active after rebooting it often adds its process to the startup using Task Scheduler.
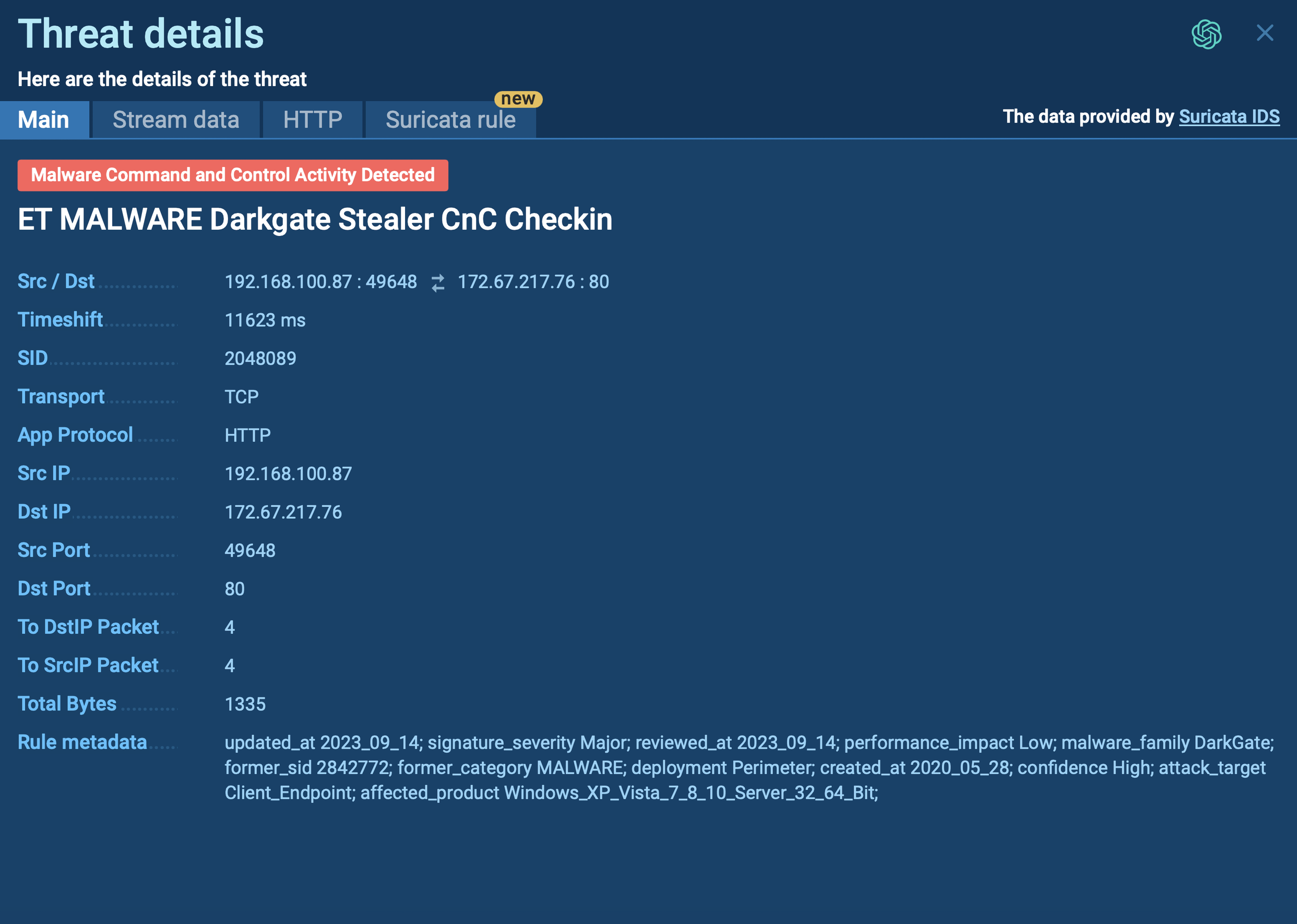
Next, the loader malware collects information about the system and attempts to establish connection with its C2 server to transmit the data to attackers. The server then responds with an encrypted payload that the loader executes and infects the system with a new malware family. It is worth noting that loaders often make use of the Dead Drop Resolver technique, where they host malicious code on the servers of popular services and apps, such as Discord.
Loaders also utilize encryption in order to prevent professionals from analyzing its code and C2 communication. They also employ anti-debugging to further make it difficult to understand how it works.
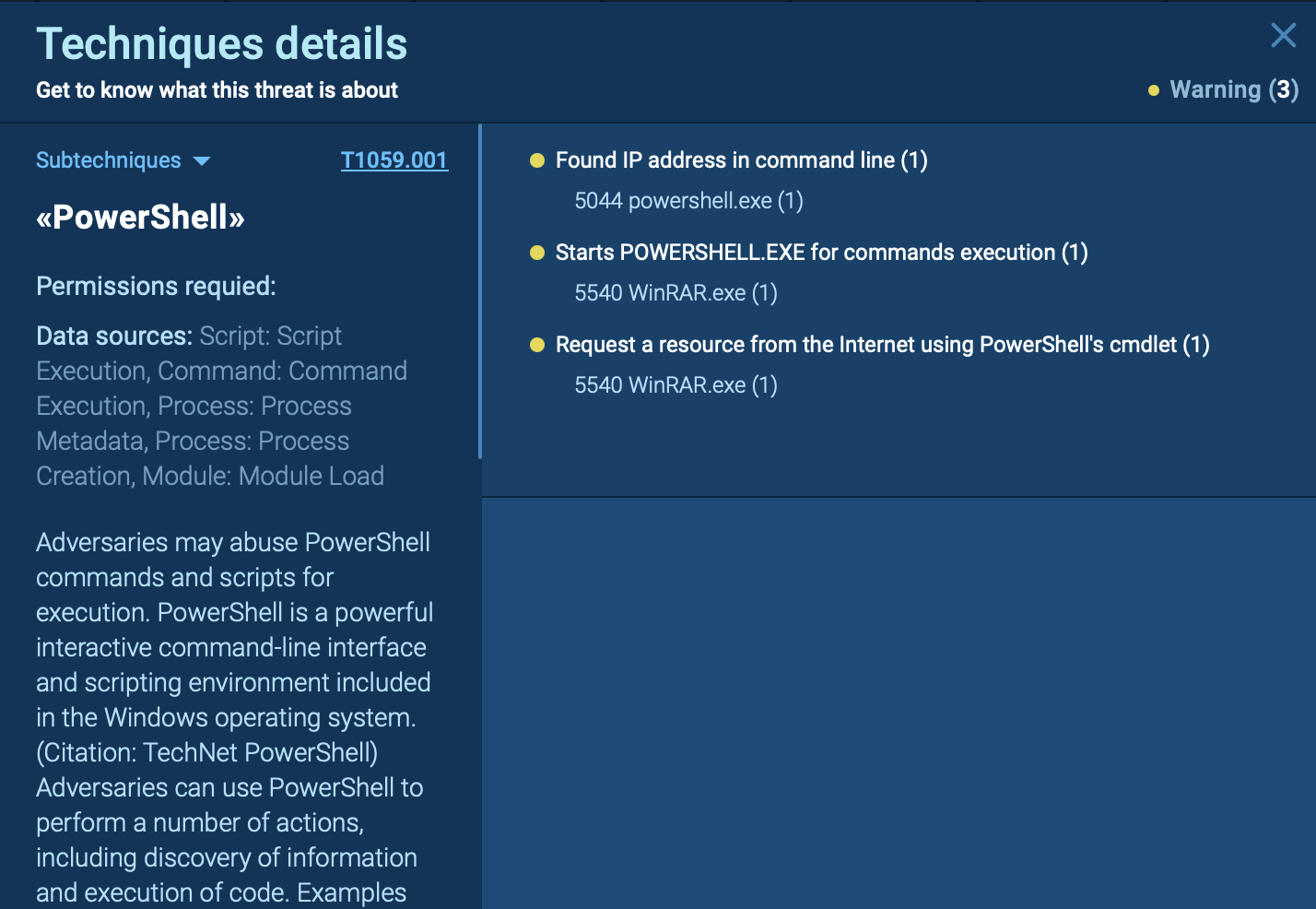
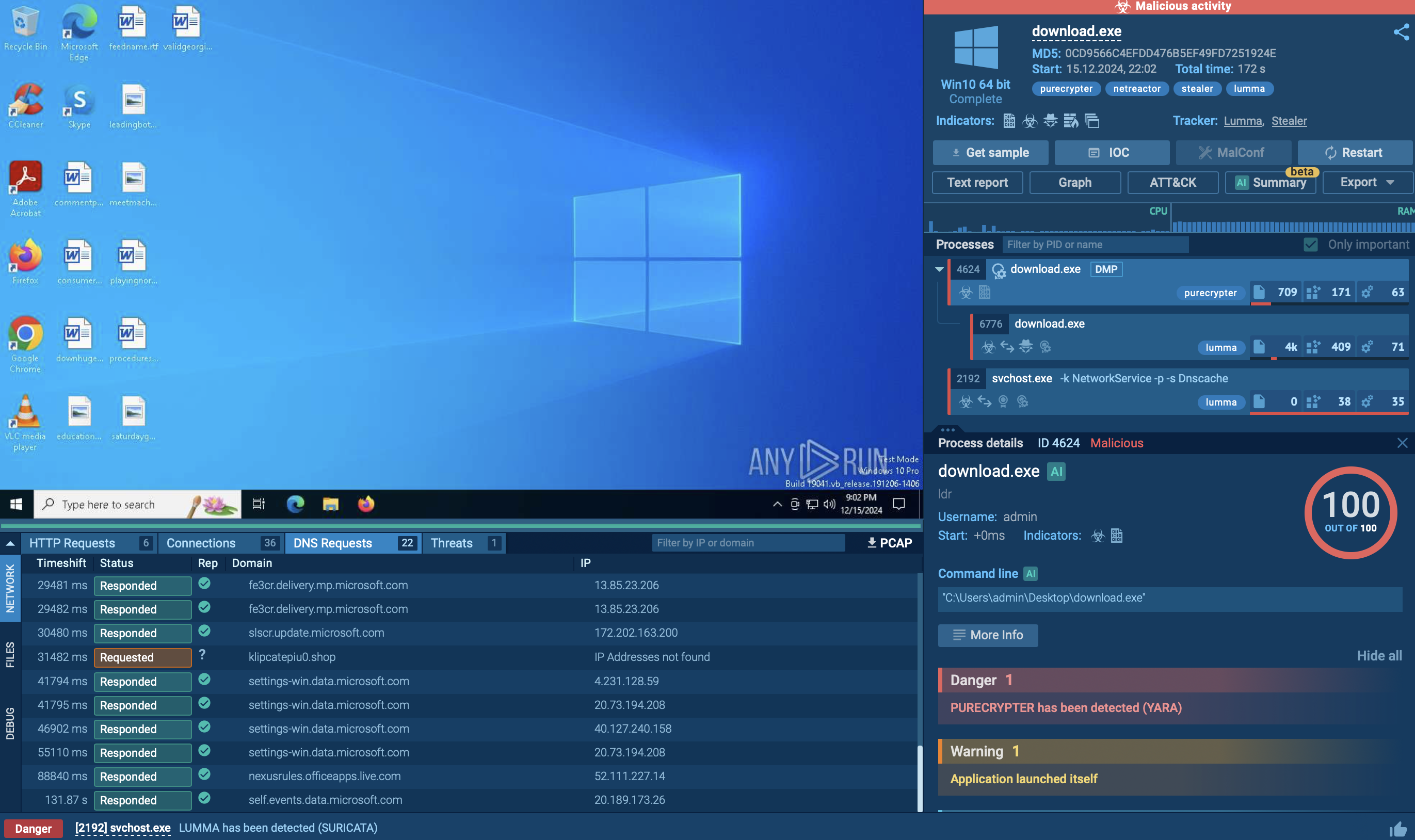
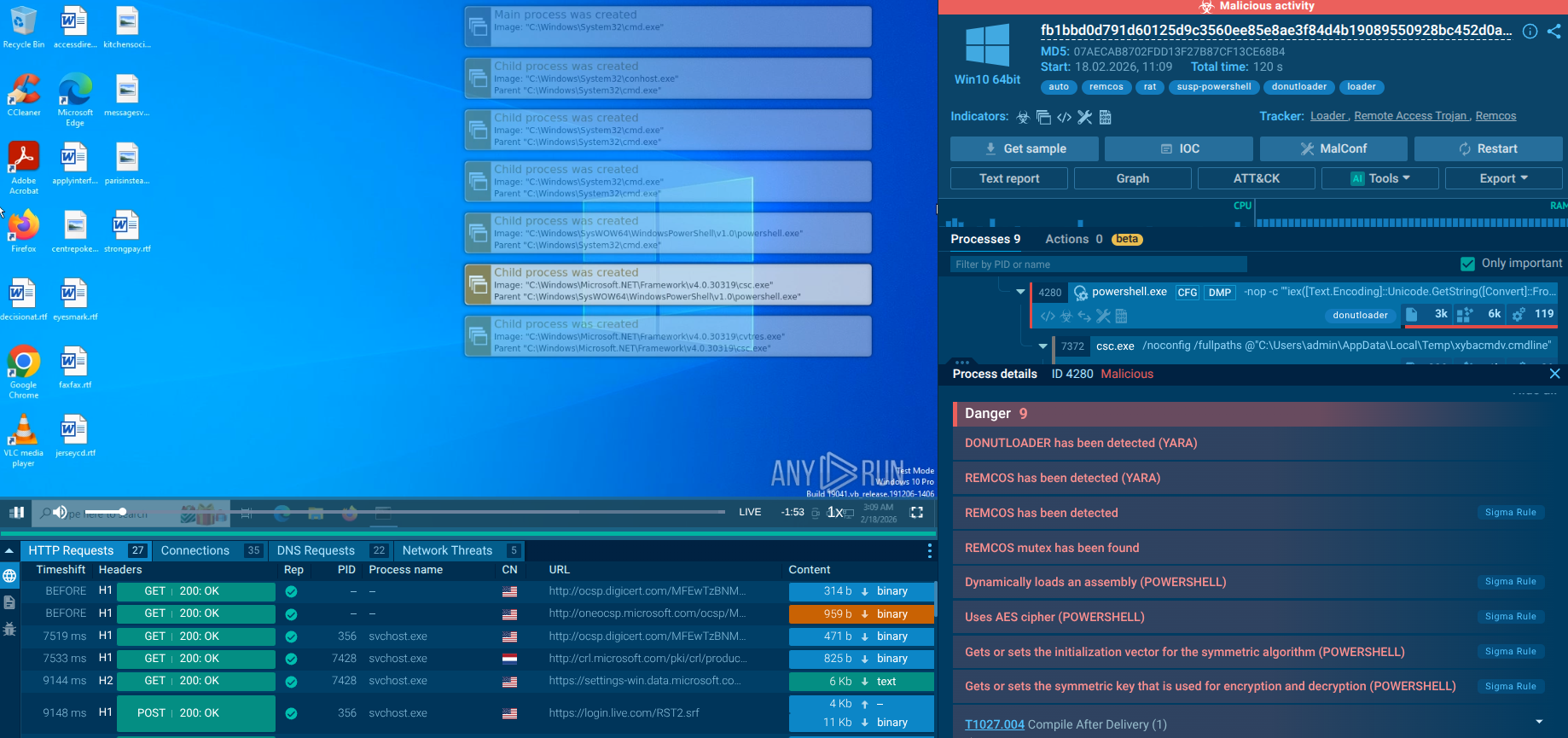
To see in detail how a typical loader operates, we can upload a sample of PrivateLoader to the ANY.RUN sandbox.
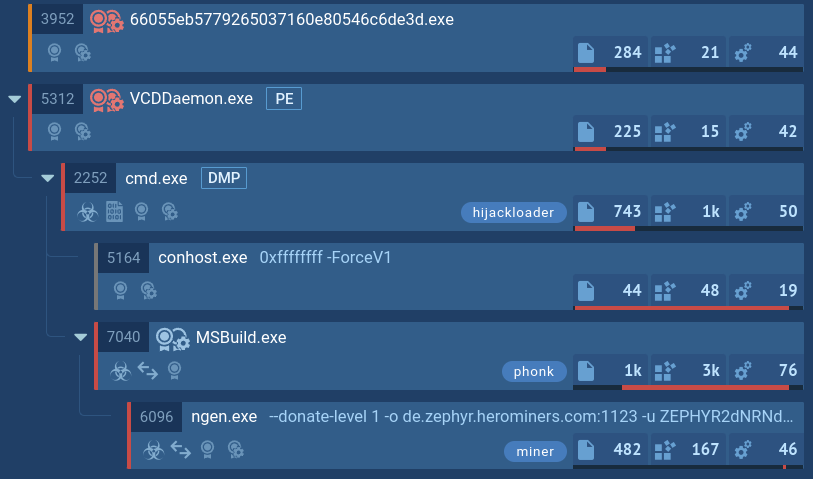
Upon infiltrating the target device, the primary PrivateLoader process spawns a child process whose executable file resides in the user's "Pictures" directory. This newly created child process is subsequently incorporated into the system's startup routine using Task Scheduler.
Examination of the HTTP requests reveals connections and data transfers with the C2 server. Both the sent and received content in POST requests is BASE64-encoded. Further analysis of the indicators reveals that the malware steals user credentials from web browsers.
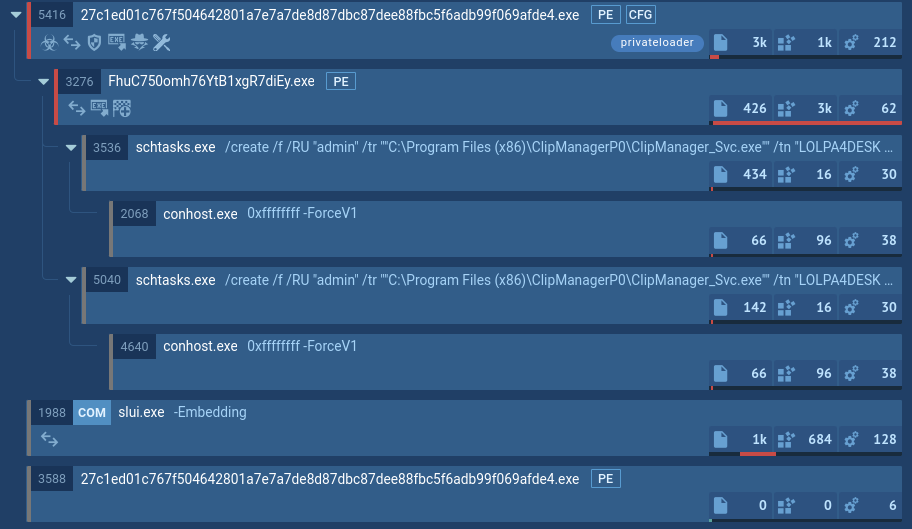 A process tree of a PrivateLoader sample demonstrated by ANY.RUN
A process tree of a PrivateLoader sample demonstrated by ANY.RUN
Having a clear threat visibility and knowing which loaders are active at the moment is critical for organizations’ proactive cybersecurity. To track both emerging and persistent malware, use ANY.RUN’s Malware Trends Tracker.
Here are top three Loaders right now, according to the service:
Protecting your organization from loaders and other malicious software requires a solid stack of security solutions. One of the key elements of proper security posture is malware analysis sandboxes.
ANY.RUN is a cloud-based sandbox that lets users analyze files and URLs and quickly discover whether they are malicious or not. On top of advanced analysis capabilities, the platform provides comprehensive reports on threats submitted by users, containing relevant IOCs and malware configs.
Try ANY.RUN for free – request a demo!