We’re glad to present our regular quarterly report highlighting the most prominent malicious trends of the last three months of 2025, as observed by ANY.RUN’s community.
Following the release of our annual report on key threats and milestones, this report offers a closer look at the threat landscape of the final chapter of 2025.
The Malware Trends report Q4 features top malware types, families, phishing kits, TTPs, APTs, and other notable insights.
You can turn to the previous Q3 report for reference.
Key Takeaways
- Threat activity remained steady, with sandbox usage up 6% quarter over quarter and over 1 billion IOCs collected, reflecting sustained investigative demand rather than volume spikes.
- Stealers still dominate, even after a 16% decline, confirming credential theft as a primary attacker objective.
- RATs and backdoors gained momentum, with RATs up 28% and backdoors up 68%, signaling a shift toward persistent access and modular malware.
- XWorm and open-source RATs surged, with XWorm up 174%, showing attackers favor adaptable, widely shared toolsets over saturated stealer families.
- Phishing continued to evolve, led by Tycoon and EvilProxy, underscoring the growing sophistication of PhaaS and 2FA bypass campaigns.
Summary
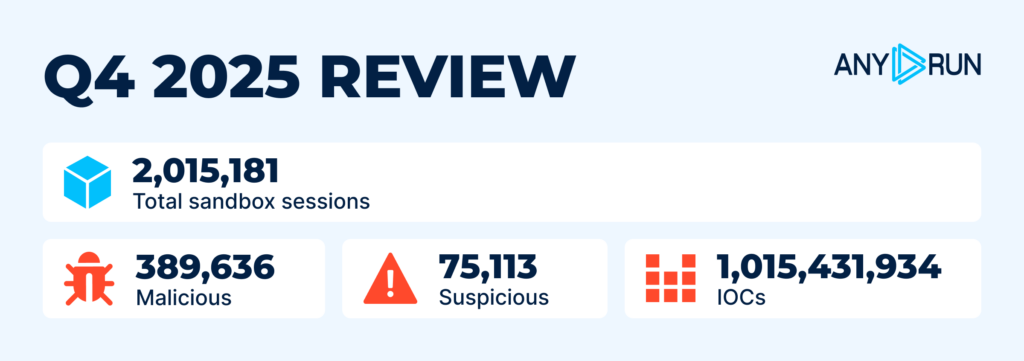
- Total sandbox sessions: 2,015,181
- Malicious: 389,636
- Suspicious: 75,113
- IOCs: 1,015,431,934
During the last quarter of 2025, overall threat investigation activity remained stable — no drastic growth in volume. The total number of sandbox analyses conducted in ANY.RUN’s Interactive Sandbox increased slightly by 6%, surpassing 2 million since Q3.
Over one billion indicators were gathered by our community during analysis sessions. A total of 389,636 samples were labeled as malicious, and 75,113 as suspicious.
Top Malware Types: Highlights
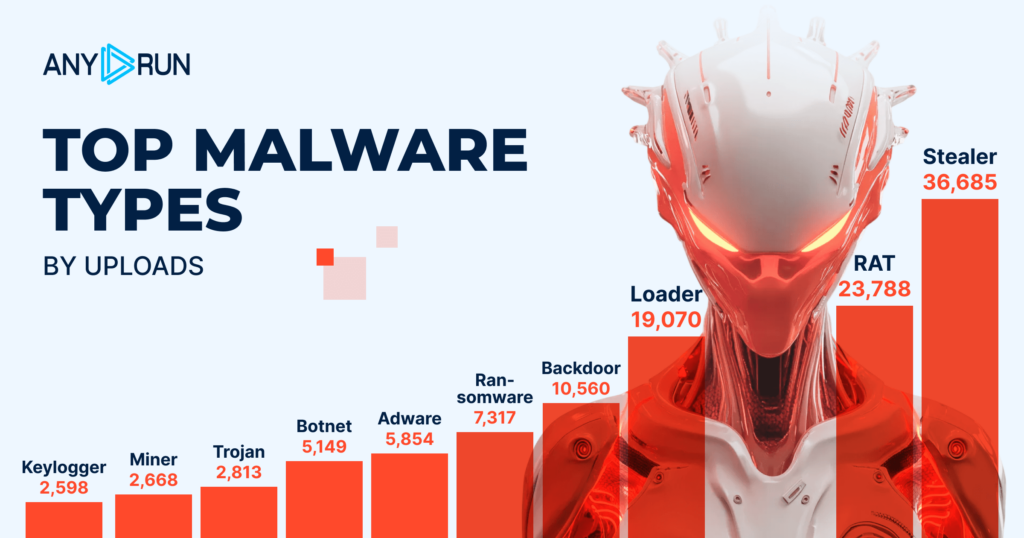
- Stealer: 36,685
- RAT: 23,788
- Loader: 19,070
- Backdoor: 10,560
- Ransomware: 7,317
- Adware: 5,854
- Botnet: 5,149
- Trojan: 2,813
- Miner: 2,668
- Keylogger: 2,598
Although the list of top malware types looks similar to Q3 at first glance, several notable changes in activity levels should be pointed out:
- Stealer dominance persists despite a 16% drop. This signals that credential theft remains a priority for attackers targeting financial sectors.
Widespread families: Lumma, Stealc, Blank Grabber
- RAT surged (+28%), overtaking Loaders’ second place. A clear indication of remote access tools gaining traction for persistent post-exploitation in enterprise environments.
Widespread families: XWorm, Quasar RAT, AsyncRAT
- Loader threats moved one place down despite a slight decrease in detections.
Widespread families: Smoke Loader, PureCrypter, HijackLoader
Backdoor‘s 68% activity growth reflects modular malware kits proliferating, enabling easier customization and evasion of traditional defenses.
Adware moved up two places with a 31% rise in activity, while ransomware detections decreased by the same percentage.
At the lower end of the list there are Botnet with 5K detections, Trojan with 2.8K, Miner with 2.6K, and Keylogger with 2.5K.
Detect evasive threats with ANY.RUN’s Interactive Sandbox
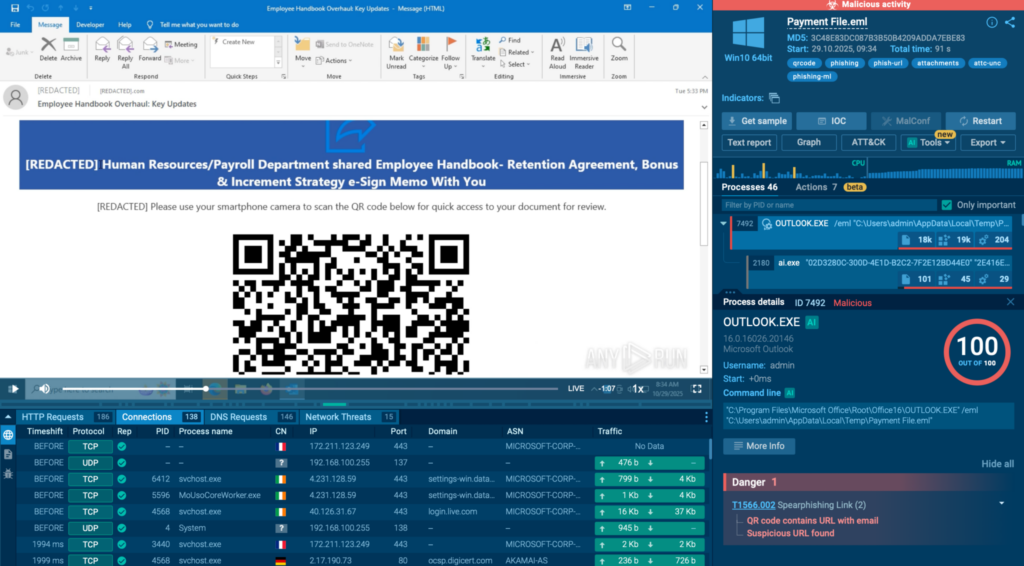
ANY.RUN’s Interactive Sandbox enables businesses and SOC teams to proactively identify cyber threats by analyzing files and URLs inside interactive Windows, Linux, Android VMs.
- Stronger Protection for Businesses: Early detection and shorter MTTD minimize risks, safeguarding infrastructure and reputation.
- Higher Efficiency & ROI: Faster investigations cut costs, reduce analyst load, and power quicker incident resolution.
- Smarter Decision-Making: Flexible, enterprise-grade solution enhances visibility into threats, allowing for insight-driven action.
Top Malware Families
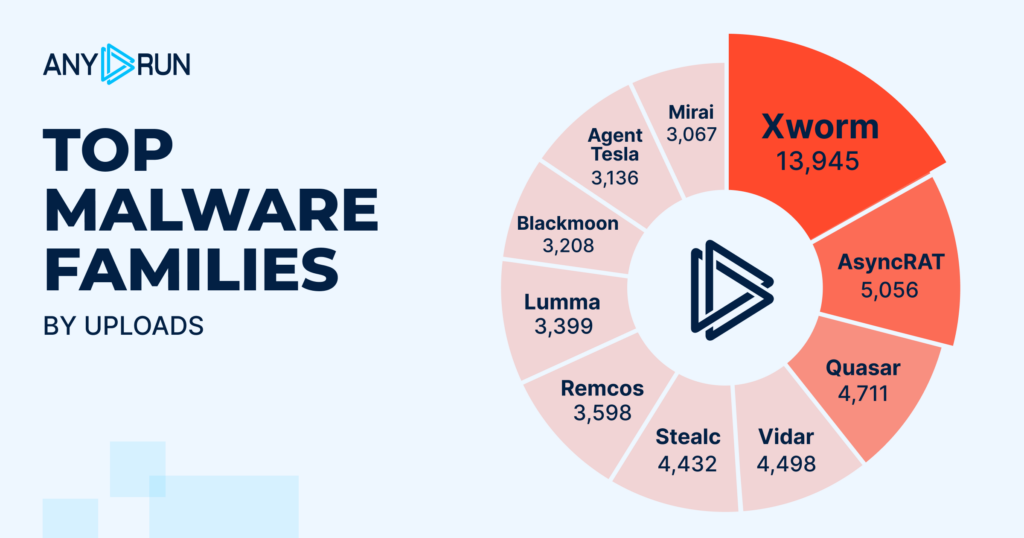
- XWorm: 13,945
- AsyncRAT: 5,056
- Quasar: 4,711
- Vidar: 4,498
- Stealc: 4,432
- Remcos: 3,598
- Lumma: 3,399
- Blackmoon: 3,208
- AgentTesla: 3,136
- Mirai: 3,067
This section indicates a number of drastic changes in intensity and volume of certain threats. Key observations include:
XWorm, driven by its adaptability across industries like manufacturing and healthcare, showed a +174% surge.
XWorm IOCs from Threat Intelligence Lookup
- centre-instruction[.]gl[.]at[.]ply[.]gg
- uk-compete[.]gl[.]at[.]ply[.]gg
- 176[.]113[.]73[.]167
Find more IOCs in TI Lookup with this query:
threatName:”xworm” AND domainName:””
- AsyncRAT and Quasar grew by 46% and 27%, showing open-source RATs outpacing commercial stealers, fueled by underground sharing and rapid evolution.
AsyncRAT IOCs from Threat Intelligence Lookup
- xoilac[.]livecdnem[.]com
- asj299[.]com
- 94[.]154[.]35[.]160
Find more IOCs in TI Lookup with this query:
threatName:”asyncrat” AND domainName:””
Lumma’s fall from first to eighth place with a -65% plunge highlights attacker shifts to newer, less-detected families, reducing reliance on saturated stealer platforms.
Lumma IOCs from Threat Intelligence Lookup
- handpaw[.]click
- mattykp[.]click
- 159[.]198[.]70[.]75
Find more IOCs in TI Lookup with this query:
threatName:”lumma” AND domainName:””
Vidar and Stealc with 4K+ detections each re-emerged in Q4, indicating a sudden end-of-year growth.
Another addition to the chart is Blackmoon with 3,208 detections. At the same time, AgentTesla and Remcos threats saw a reduction in detections and went from second and fourth places to tenth and seventh respectively.
Ensure early threat detection via Threat Intelligence Feeds
Gain a live view of the threat landscape with fresh, actionable IOCs delivered to you from investigations done across 15,000 companies.
- Refine detection and response: Rich threat context and integration opportunities power your SOC for proactive defense.
- Mitigate risks of breaches: Expanded threat coverage and visibility into threats help stay ahead of attackers without wasting time on false alarms.
- Improve performance rates: Unique, noise-free indicators beat alert fatigue and promote early detection even for hidden and evasive threats.
Top TTPs
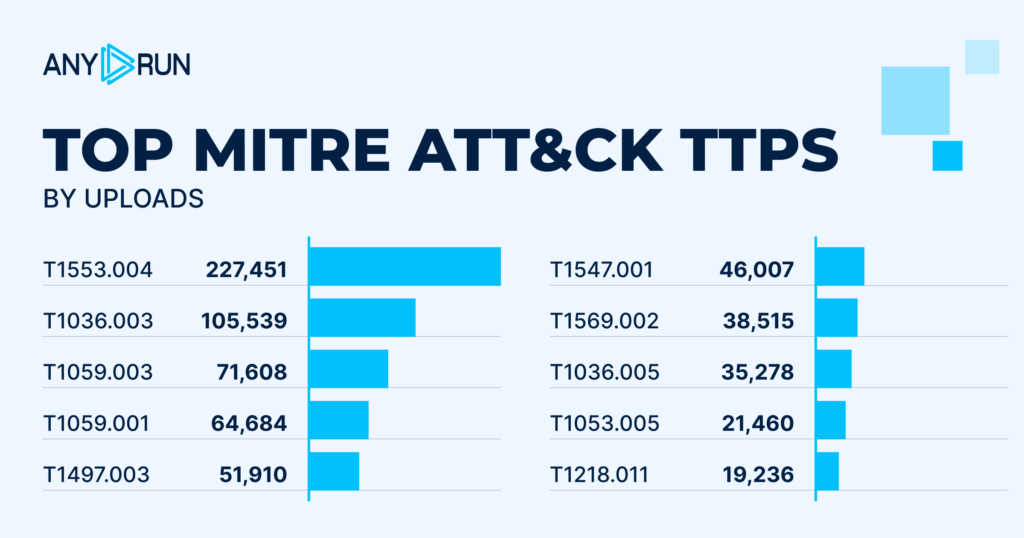
The top 10 most detected techniques, tactics, and procedures (TTPs) show significant shifts from quarter to quarter — a reminder that threat actors never stop refining and changing their methods.
The number of detections for TTPs mostly grew: the first place is taken up by Subvert Trust Controls: Install Root Certificate, T1553.004 with 227,451 detections. In Q3, the first place was taken by a TTP with activity rate twice as small.
Second place was still occupied by Masquerading: Rename Legitimate Utilities, T1036.003 with 105,539 detections (+9%).
A new addition to the list, Command and Scripting Interpreter: Windows Command Shell , T1059.003, came third with 71,608 detections.
1. Subvert Trust Controls: Install Root Certificate, T1553.004: 227,451
2. Masquerading: Rename Legitimate Utilities, T1036.003: 105,539
3. Command and Scripting Interpreter: Windows Command Shell, T1059.003: 71,608
4. Command and Scripting Interpreter: PowerShell, T1059.001: 64,684
5. Virtualization/Sandbox Evasion: Time Based Checks, T1497.003: 51,910
6. Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder, T1547.001: 46,007
7. System Services: Service Execution, T1569.002: 38,515
8. Masquerading: Match Legitimate Resource Name or Location, T1036.005: 35,278
9. Scheduled Task/Job: Scheduled Task, T1053.005: 21,460
10. Signed Binary Proxy Execution: Rundll32, T1218.011: 19,236
Collect Fresh Threat Intelligence with Threat Intelligence Lookup
TI Lookup offers a searchable database of fresh Indicators of Compromise (IOCs), Attack (IOAs), and Behavior (IOBs) belonging to the latest cyber attacks on 15,000 companies.
- Build proactive defense: Actionable threat intelligence drives targeted and insightful research for staying ahead.
- Ensure rapid triage and response: Instant enrichment of indicators with behavioral context makes for fast and smart decisions.
- Optimize workload: Rich threat data empowers Tier 1 analysts to work sustainably, reducing escalations to Tier 2.
Phishing Activity in Q4 2025
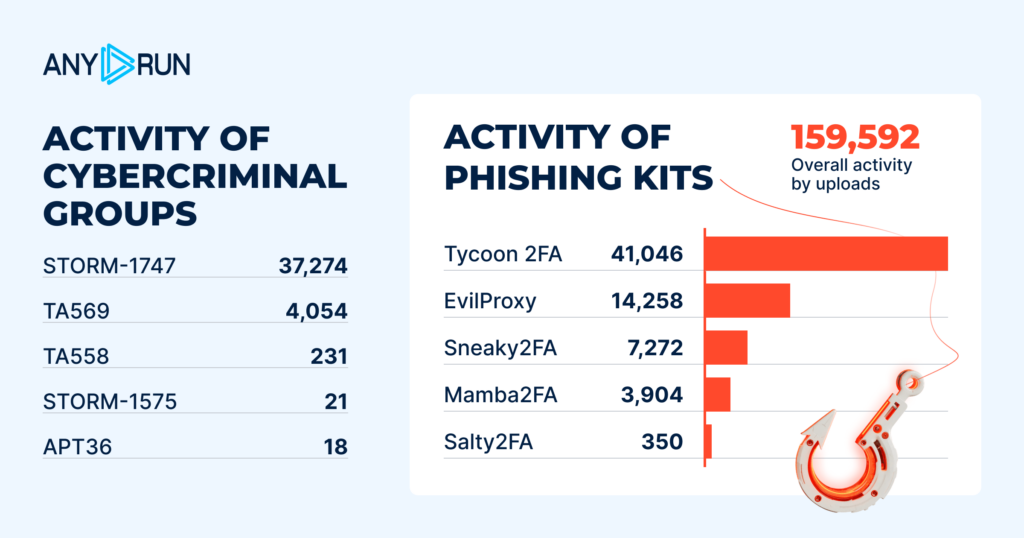
Overall phishing activity by uploads: 159,592
Activity by phishing kits
Phishkits:
- Tycoon: 41,046
- EvilProxy: 14,258
- Sneaky2FA: 7,272
- Mamba2FA: 3,904
- Salty2FA: 350
Q4’s results align with our annual report’s conclusions: phishing is a prevalent type of cyber threat and Tycoon dominates in this category:
- It remained at the top of the list with double the intensity of detections. Same with EvilProxy: it stayed second with 51% increase in volume. This underscores PhaaS maturation, with kits now bundling advanced 2FA bypass for high-value targets.
- Sneaky2FA moved from fourth to third place with a whopping +138% rise in activity.
- Salty2FA moved two places down, pointing to 2FA fatigue exploitation accelerating in enterprise phishing campaigns.
- Mamba2FA, absent from the list in the previous quarter, took fourth place with 3.9K detections.
Activity by cyber criminal groups
- Storm1747: 37,274
- TA569: 4,054
- TA558: 231
- Storm1575: 21
- APT36: 18
Key observations regarding APT activity in Q4 2025:
- Storm1747’s dominance continued with a 51% rise in activity, likely tied to phishing infrastructure evolution targeting finance across EU/NA regions.
- TA558‘s jumped into top ranks with +83% detections, suggesting expanded operations, possibly leveraging modular loaders for broader campaign reach.
- At the lower part of the list, we can see APTs’ displaying sharp 70-97% declines, likely due to the detection improvements or operational pauses. The focus shifted to more opportunistic actors.
Top Protectors and Packers
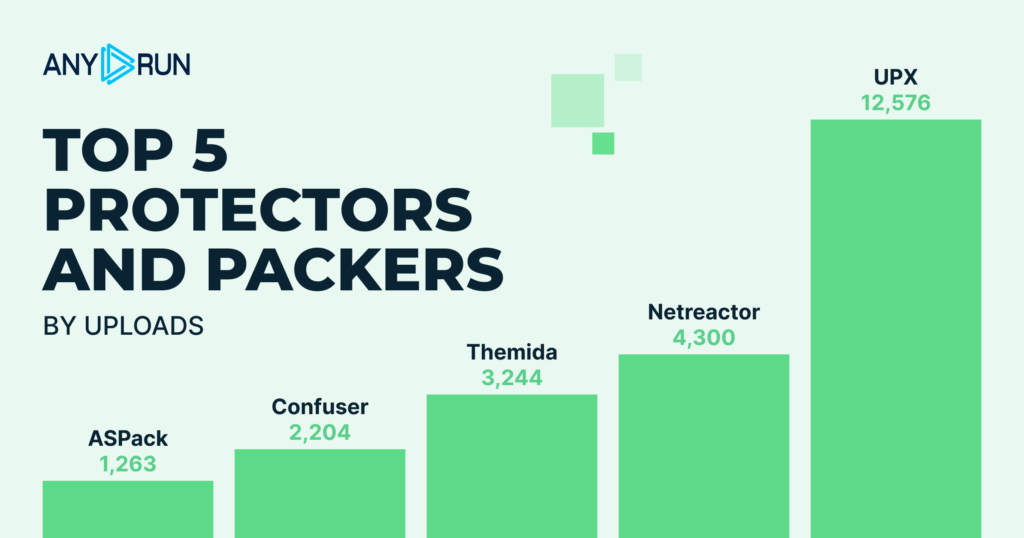
- UPX: 12,576
- NetReactor: 4,300
- Themida: 3,244
- ASPack: 1,263
- Confuser: 2,204
Top 5 most detected protectors and packers correspond with those of Q3. However, there are differences in terms of their intensity:
- UPX remains dominant despite an 11% drop, remaining attackers’ go-to for simple, fast obfuscation across commodity malware.
- NetReactor and Themida’s sharp declines (-49% and -37% respectively) signal detection improvements and attacker shift to newer .NET-focused protectors.
- Confuser kept its fifth place with a 48% growth that reflects .NET malware boom. Attackers favor it for evading static analysis in enterprise-targeted payloads.
Conclusion
Q4 2025 shows a stable but evolving threat landscape. Key trends include persistent stealer activity, rising RATs and backdoors, and a dynamic phishing landscape. These insights underscore the importance of continuous monitoring and proactive threat analysis to stay ahead of emerging risks.
About ANY.RUN
ANY.RUN develops solutions for malware analysis and threat hunting. Its interactive malware analysis sandbox is used by over 500,000 cybersecurity professionals worldwide. It enables detailed investigation of threats targeting Windows, Android, and Linux systems with hands-on analysis and instant visualization of malware behavior.
ANY.RUN’s threat intelligence solutions, including Threat Intelligence Lookup and Threat Intelligence Feeds, allow teams to quickly identify indicators of compromise, enrich alerts, and investigate incidents early on. As a result, analysts gain actionable insights, uncover hidden threats, and improve overall cybersecurity posture.







0 comments