Summarizing the past year’s threat landscape based on activity observed in ANY.RUN’s Interactive Sandbox, this annual report provides insights into the most detected malware types, families, TTPs, and phishing threats of 2025.
For additional insights, view ANY.RUN’s quarterly malware trends reports.
Key Takeaways
- Threat activity surged, with total sandbox sessions up 72% and malicious detections growing proportionally, reflecting increased frequency and depth of analysis among SOCs.
- Stealers and RATs maintain dominance, tripling in activity compared to 2024.
- Lumma and XWorm led malware family rankings, highlighting sustained reliance and mature and adaptable malicious ecosystems.
- Phishing, driven by MFA-bypassing PhaaS kits like Tycoon 2FA and EvilProxy, evolved into an advanced malicious vector.
- Widespread TTPs shifted toward stealth and trust abuse, with root certificate installation as the most detected technique of the year.
Summary
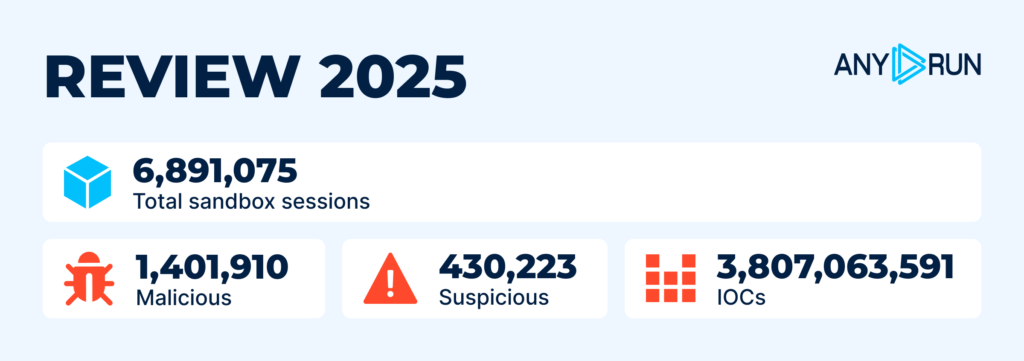
| Total | 6,891,075 |
| Malicious | 1,401,910 |
| Suspicious | 430,223 |
| IOCs | 3,807,063,591 |
In 2025, ANY.RUN experienced significant growth alongside a rise in malicious activity. The numbers reflect a substantial growth of deep investigations and the detections of evasive threats facilitated by Interactive Sandbox:
- 6.8 million sandbox sessions were launched — +72.2% compared to 2024.
- The number of malicious samples grew by a similar number: 77.3%. This shows that the overall sandbox activity and malicious detections grow proportionally.
- Suspicious samples more than doubled and rose from 211,517 in 2024 to 430,223 in 2025.
- The total number of IOCs collected by ANY.RUN’s global community: 3.8 billion, nearly 2 billion more than the year before.
As investigation volume and behavioral visibility increase, 15K+ security teams gain earlier detection, richer context, and faster response capabilities with ANY.RUN.
Interactive Sandbox helps them ensure a strong, enterprise-grade defense system by enabling:
- Early Detection: Minimize risks to safeguard your infrastructure and reputation with 36% higher detection rates.
- Higher Efficiency & ROI: Cut MTTR by 21 minutes to power quicker incident resolution.
- Smarter Decision-Making: Flexible solutions enhance visibility into threats for insights-driven action.
Top Malware Types: Highlights
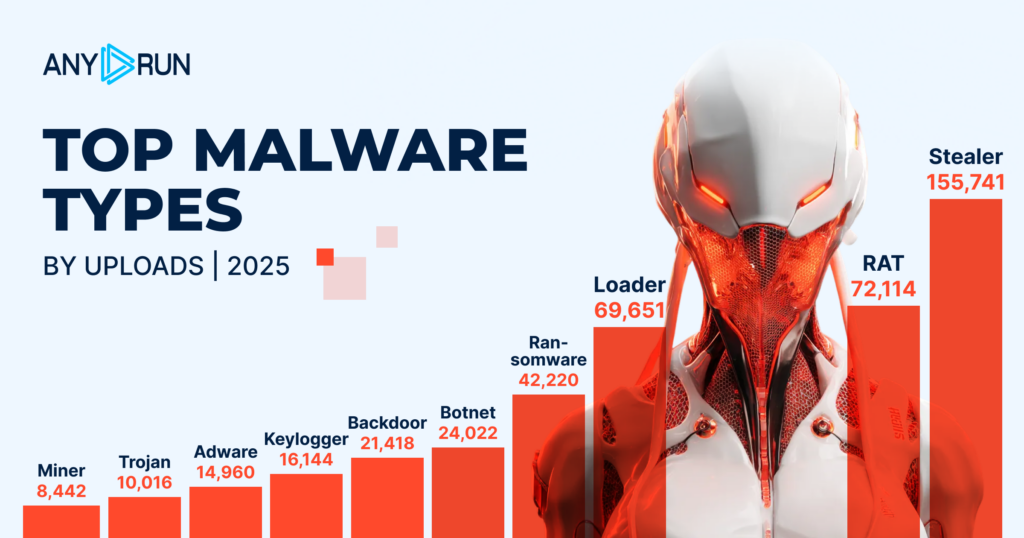
- Stealer 155,741
- RAT 72,114
- Loader 69,651
- Ransomware 42,220
- Botnet 24,022
- Backdoor 21,418
- Keylogger 16,144
- Adware 14,960
- Trojan 10,016
- Miner 8,442
The upper part of the most active malware types chart closely resembles that of 2024. The top four most detected threats remained unchanged, underscoring the long-term impact and growth in activity of Stealer and RAT (their intensity grew 3x), Loader (2.5x) and Ransomware (2x) malware.
- Widespread stealers: Lumma, Stealc, Blank Grabber
- Widespread RATs: XWorm, Quasar RAT, AsyncRAT
- Widespread loaders: Smoke Loader, PureCrypter, HijackLoader
Other types have seen notable growth, too. Particularly dramatic increases are seen in Backdoor and Adware attacks. This points to an ongoing trend towards persistent access, credential theft, and multi-stage malware campaigns as opposed to short-spanned attacks.
A new addition to the list is Botnet with 21K+ detections that secured fifth place for this malware type.
Malware Families

- Lumma 31,111
- XWorm 31,093
- AsyncRAT 16,372
- Remcos 16,002
- AgentTesla 14,584
- Snake 13,556
- Quasar 13,512
- Vidar 10,303
- Stealc 9,927
- Amadey 9,533
From 2024 to 2025, most recurring malware families at least doubled in activity, as indicated by ANY.RUN’s statistics.
XWorm that led the ranking in 2024 was detected 4.3x times more often in 2025. Despite the sharp growth, it moved a place down and gave way to Lumma, this year’s leader, which grew from 12K to 31K+ detections.
Third and fourth places are taken by AsyncRAT and Remcos: both doubled in activity and were detected roughly 16K times.
A notable 3x growth in activity is seen in Snake threats, which occupied sixth place with 13,556 total detections.
Quasar and Vidar families newly entered the top list, signaling renewed RAT and stealer diversification.
You can browse Threat Intelligence Lookup for further insights into threats relevant for you country or industry. For that, use requests like:
threatName:”xworm” AND industry:”Finance”
SOC teams can use these insights from a searchable indicator databases with IOCs, IOAs, and IOBs to:
- Build Proactive Defense: Actionable threat intelligence drives targeted and insightful research for staying ahead.
- Ensure Rapid Triage and Response: Instant enrichment of indicators with behavioral context makes for fast and smart decisions.
- Optimize Workload: Rich threat data empowers Tier 1 analysts to work sustainably, reducing escalations to Tier 2.
Phishing Threats
Phishing APTs
| Actor | Total Detections |
|---|---|
| Storm-1747 | 92,147 |
| TA569 | 11,012 |
| Storm-1575 | 1,539 |
| TA558 | 720 |
| TA582 | 315 |
Phishing remained a key initial infection and credential-harvesting method
throughout 2025. In ANY.RUN’s Interactive Sandbox, phishing-related activity was detected 541,225 times.
- Among key APT groups, Storm-1747 dominated the list consistently from Q1 through Q4, accounting for a total of 92,147 detections.
- TA569 held second position from quarter to quarter as well, with 11K detections overall.
The dominance of these actors over the months highlights the superiority of these groups on the threat landscape, which allows them to take up a disproportionately large share of phishing operations.
The year’s top three is concluded by Storm-1575 with significantly fewer detections than the chart’s leaders, emphasizing the gap between the leading actors and other groups.
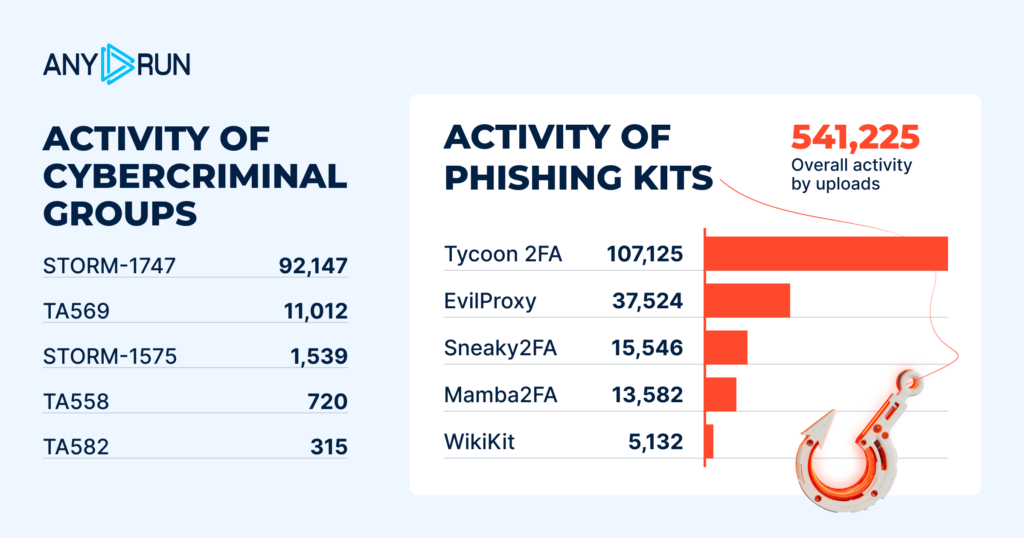
Phishing Kits
| Kit | Total Detections |
|---|---|
| Tycoon2FA | 107,125 |
| EvilProxy | 37,524 |
| Sneaky2FA | 15,546 |
| Mamba2FA | 13,582 |
| WikiKit | 5,132 |
Tycoon2FA and EvilProxy reigned among most detected phishing kits throughout the year. Their total number of detections: 107,125 and 37,524 respectively, underscoring a clear dominance of phishing-as-a-service (PhaaS) platforms capable of bypassing multi-factor authentication at scale.
Third place is taken by Sneaky2FA, another threat that has shown steady growth from quarter to quarter, reflecting focus on session hijacking and interception of credentials in real time.
The top five in 2025 phishing threats is rounded out by Mamba2FA and WikiKit, with roughly 13.5K and 5K total detections respectively.
These figures prove that phishing has evolved into a large-scale threat built around MFA abuse, modular tooling, and reusable infrastructures.

You can ensure eraly threat detection of phishing threats like Tycoon2FA, EvilProxy, and more with Threat Intelligence Feeds delivering 99% unique threat data directly into your SIEM and other security solutions.
- Refine Detection and Response: Indicators like IPs, URLs, and domains are enriched with threat context, making it possible to power your SOC for proactive defense.
- Mitigate Breach Risks: 15,000 companies contribute to TI Feeds data in real time, instantly expanding your threat coverage and visibility to helps you stay ahead.
- 3x Performance Rates: Filtered, noise-free indicators safely delivered via STIX/TAXII beat alert fatigue and enforce early detection.
Protectors/Packers
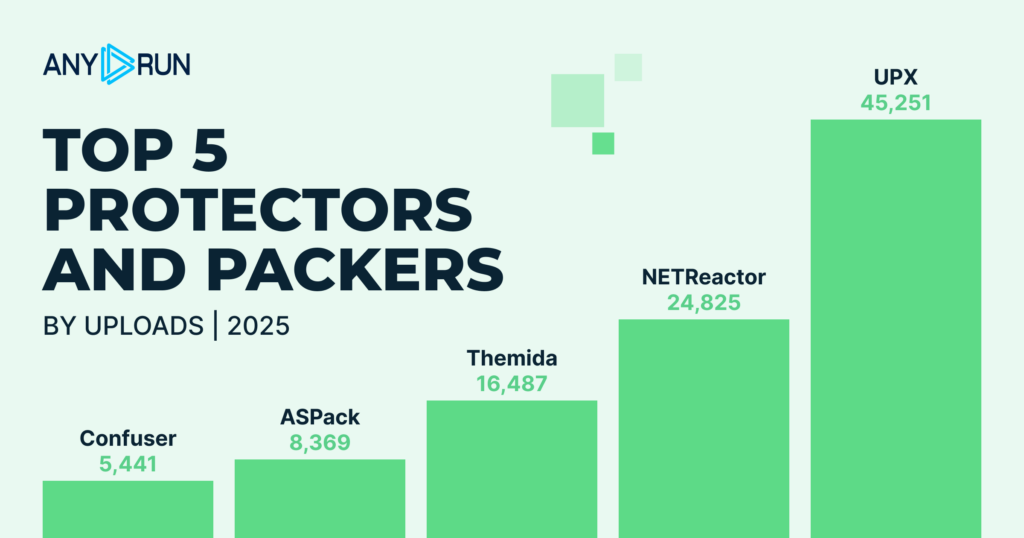
| Packer | Total Detections |
|---|---|
| UPX | 45,251 |
| NETReactor | 24,825 |
| Themida | 16,487 |
| ASPack | 8,369 |
| Confuser | 5,441 |
The list of top protectors and packers used by attackers during 2025 remained mostly stable throughout the year, reflecting continued reliance on established obfuscation tools.
- The ultimate leader is UPX with a significant gap from other packers secured by 45K+ detections.
- It’s followed by NETReactor with 24K+ detections and Themida with 16K+, both commonly leveraged to protect commodity malware and evade static analysis.
TOP TTPs
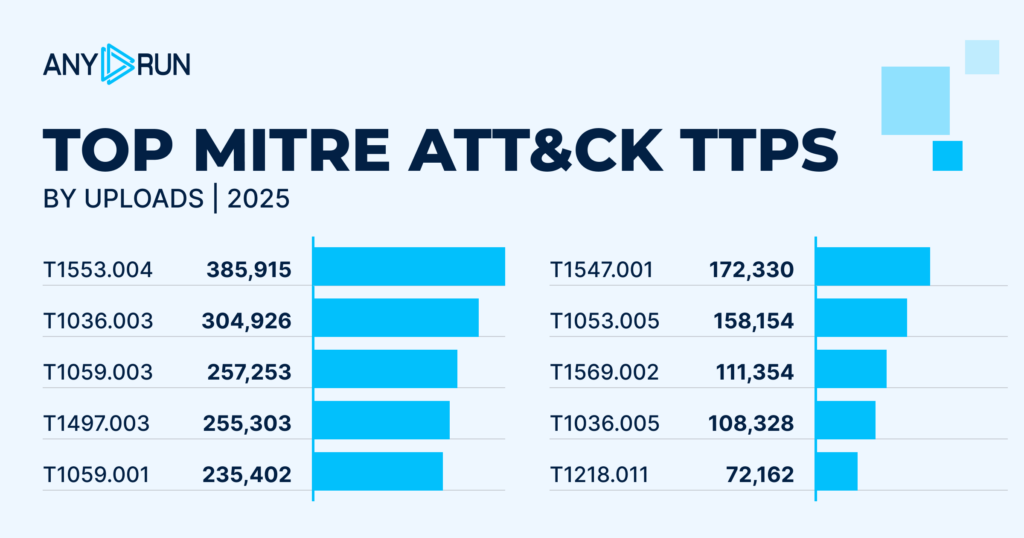
| Rank | TTP ID | Name | Total Detections |
|---|---|---|---|
| 1 | 1553.004 | Subvert Trust Controls: Install Root Certificate | 385,915 |
| 2 | 1036.003 | Masquerading: Rename Legitimate Utilities | 304,926 |
| 3 | 1059.003 | Command and Scripting Interpreter: Windows Command Shell | 257,253 |
| 4 | 1497.003 | Virtualization/Sandbox Evasion: Time Based Checks | 255,303 |
| 5 | 1059.001 | Command and Scripting Interpreter: PowerShell | 235,402 |
| 6 | 1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | 172,330 |
| 7 | 1053.005 | Scheduled Task/Job: Scheduled Task | 158,154 |
| 8 | 1569.002 | System Services: Service Execution | 111,354 |
| 9 | 1036.005 | Masquerading: Match Legitimate Name or Location | 108,328 |
| 10 | 1218.011 | System Binary Proxy Execution: Rundll32 | 72,162 |
Among widespread TTPs, a new 2025 leader is T1553.004 – Subvert Trust Controls: Install Root Certificate with 385K+ detections. This technique didn’t appear on the list a year before, signaling a shift toward TLS interception, traffic inspection, and deep trust abuse.
Second place is taken by T1036.003 – Masquerading: Rename Legitimate Utilities. This TTP moved two places up with a 2.4x growth in total detections.
Other recurring TTPs like T1059.003 – Command and Scripting Interpreter: Windows Command Shell and T1497.003 – Virtualization/Sandbox Evasion: Time-Based Checks
also experienced drastic increases in activity, confirming a rise in evasive behavior and the use of reliable execution methods, especially in phishing-delivered malware.
Key Security Insights for Businesses in 2026
- Credential theft remains the primary risk: Stealers and RATs tripled year over year, making identity compromise the fastest path to enterprise intrusion.
- Phishing is now an access operation, not a one-off attack: MFA-bypassing PhaaS kits enable scalable, repeatable breaches targeting employees at all levels.
- Persistence outweighs speed: Growth in backdoors, scheduled tasks, and autostart techniques shows attackers prioritize long-term access over quick impact.
- Trust abuse is a top concern: Root certificate installation emerged as the most detected technique, enabling traffic interception and stealthy control.
- Fewer actors, greater impact: A small number of mature threat groups drove a disproportionate share of phishing and malware activity.
- Behavioral visibility is critical: The scale and sophistication of 2025 threats highlight the need for interactive analysis and fresh threat intelligence in 2026.
ANY.RUN: Integrated Detection Accelerates SOC Performance

Understanding what happened is the first step to knowing what to do next. This report is built on threat intelligence gathered from millions of real investigations conducted by 15,000+ SOC teams worldwide throughout 2025. For actionable insights, high-quality threat data, and in-depth, dynamic analysis available in your security system 24/7, integrate ANY.RUN:
- Scalable Efficiency: Save time and resouces on manual triage and unneccessary escalations with analysts focused on high-impact work.
- Risk Mitigation: SOC teams expose evasive threats in minutes, gaining real-time behavioral visibility investigate faster.
- Smart Response: Each investigation is enriched with historical context from millions of prior analyses, delivering broader coverage and significantly more actionable indicators.
Conclusion
Overall, 2025 was marked by strong growth in investigation activity, increased malware sophistication, and a clear shift toward persistence, evasion, and trust abuse among threat actors, underscoring the need for continuous monitoring and proactive threat analysis.
About ANY.RUN
ANY.RUN builds advanced solutions for malware analysis and threat hunting. Its interactive malware analysis sandbox is trusted by 600,000+ cybersecurity professionals worldwide, enabling hands-on investigation of threats targeting Windows, Linux, and Android environments with real-time behavioral visibility.
Threat Intelligence Lookup and Threat Intelligence Feeds help security teams quickly identify indicators of compromise, enrich alerts with context, and investigate incidents at early stages. This empowers analysts to gain actionable insights, uncover stealthy threats, and strengthen their overall security posture.
Request ANY.RUN access for your company
Frequently Asked Questions (FAQ)
It is ANY.RUN’s annual analysis of global malware activity in 2025, based on millions of sandbox investigations and billions of collected indicators.
The report is derived from activity in ANY.RUN’s Interactive Sandbox, reflecting real-world investigations conducted by security teams, researchers, and SOCs worldwide.
Stealers, RATs, and phishing campaigns—especially those using MFA-bypassing phishing kits—were the most prevalent and impactful threats.
Phishing evolved into a scalable access mechanism in 2025, enabling attackers to bypass MFA, harvest sessions, and gain persistent access to corporate environments.
Attackers increasingly relied on stealth, persistence, and trust abuse, including masquerading, sandbox evasion, and root certificate installation.
Enterprises should prioritize behavioral detection, continuous monitoring, and fresh threat intelligence to detect evasive and persistent threats early.
ANY.RUN’s Interactive Sandbox and threat intelligence solutions enable hands-on analysis, early detection, and faster response to modern, evasive attacks.








0 comments