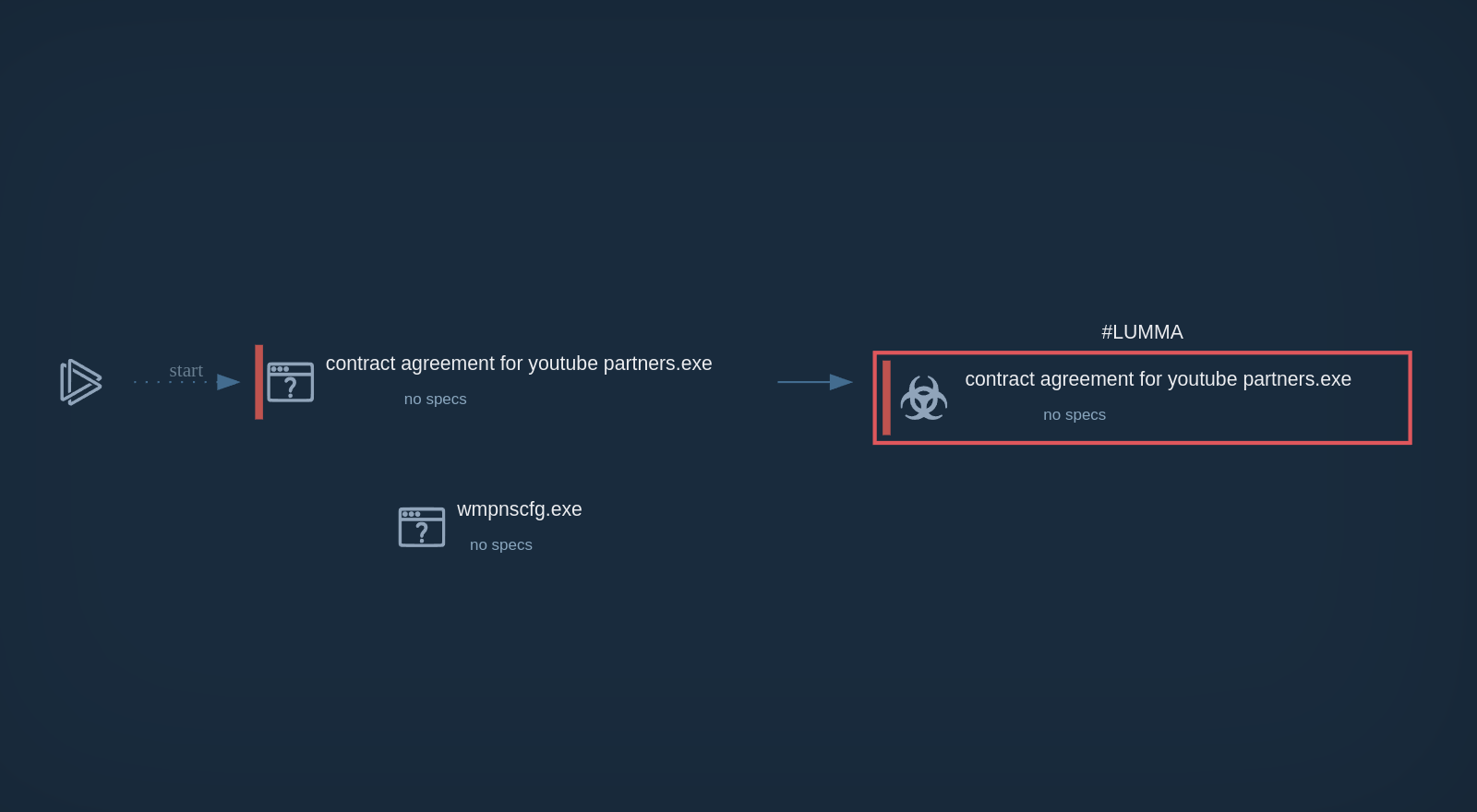
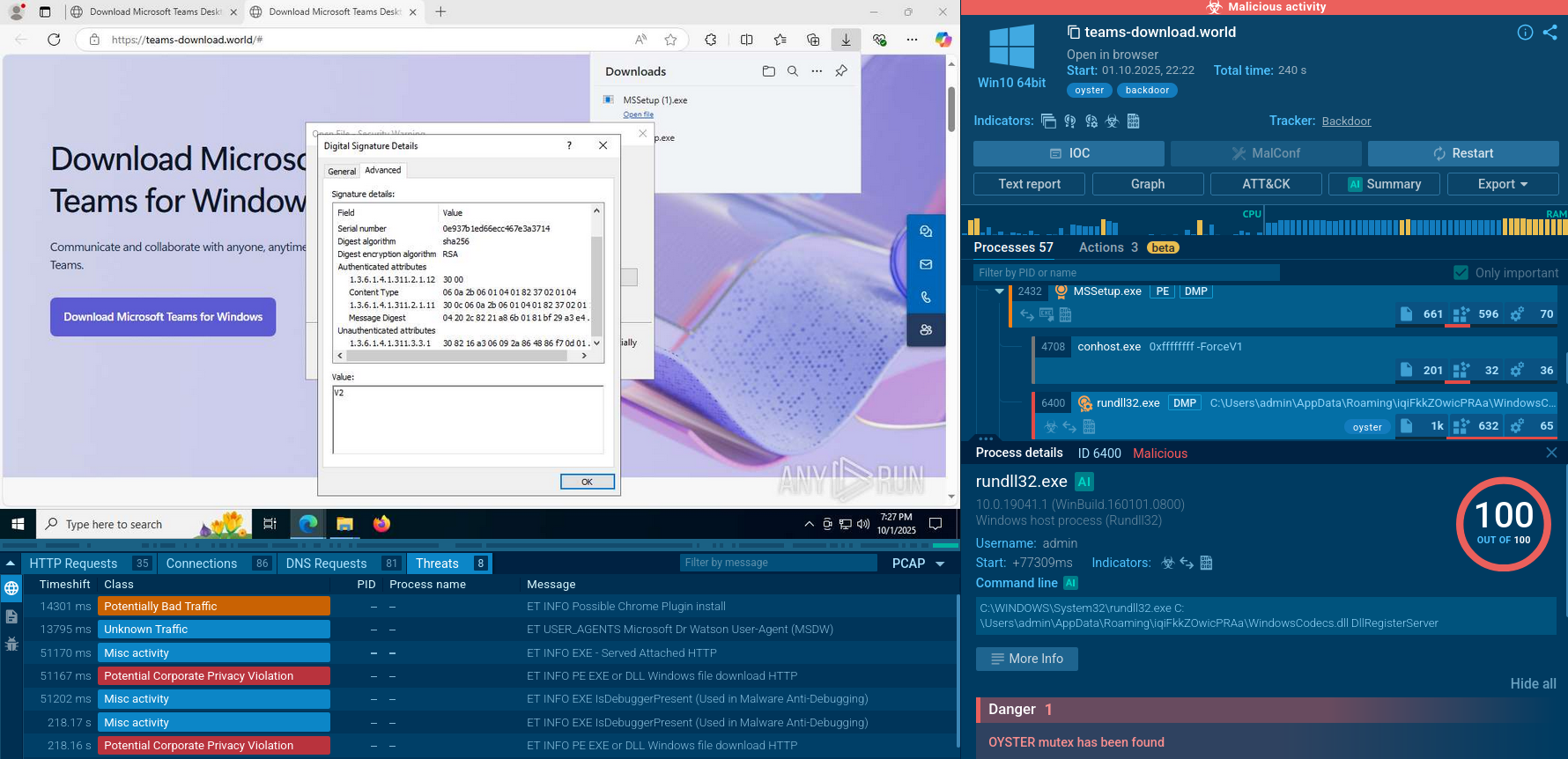
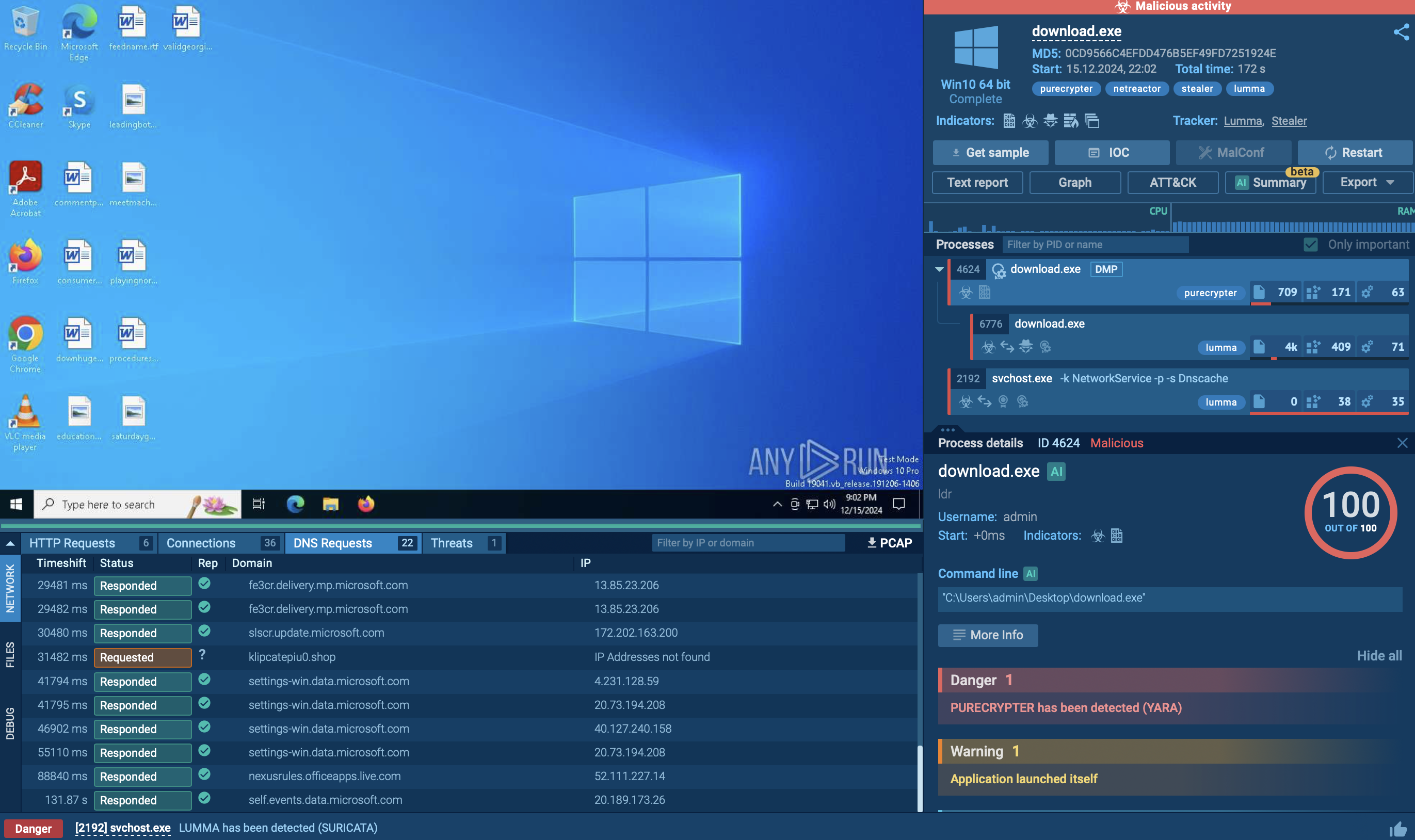
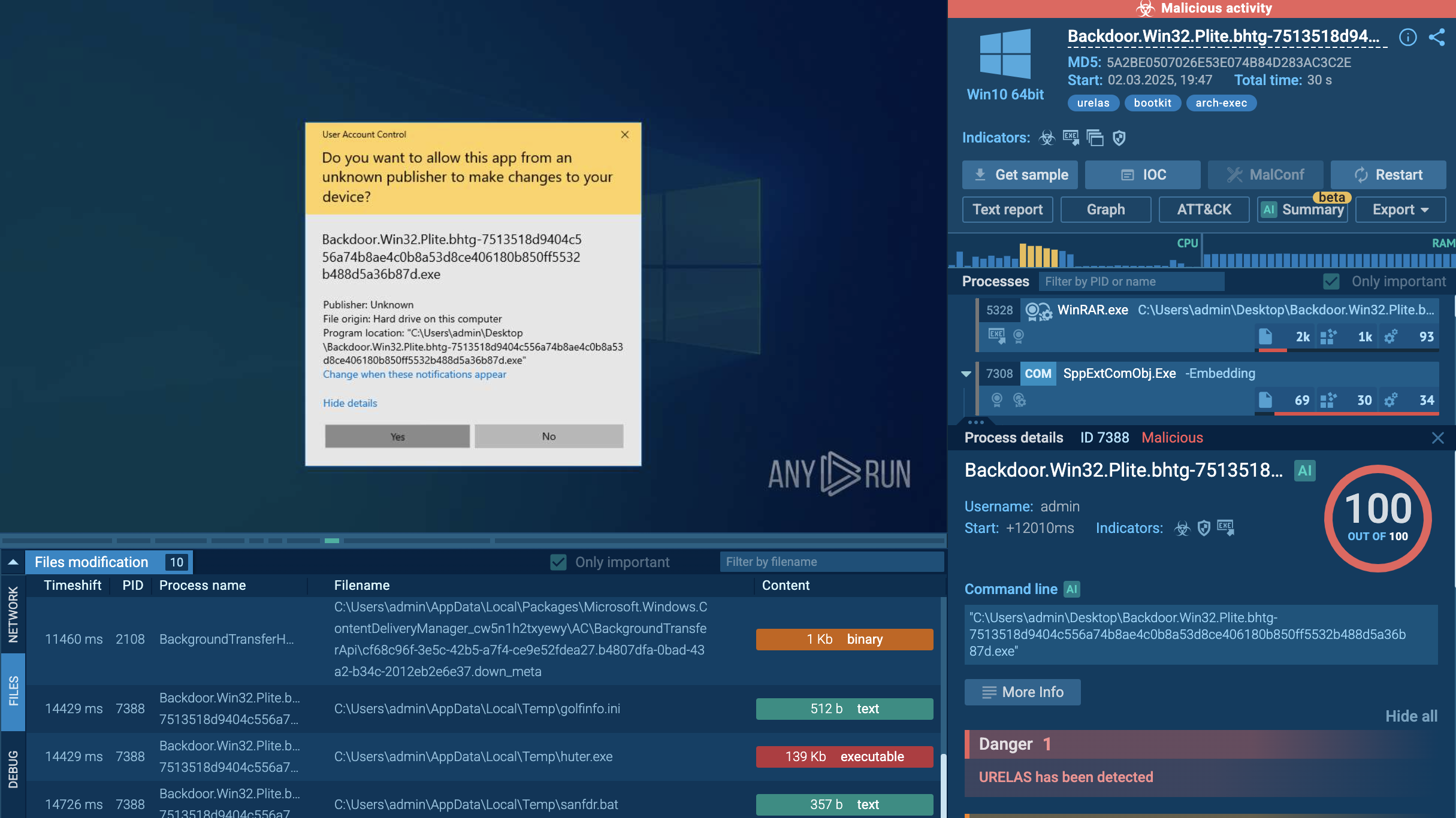
Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


Mirai is a self-propagating malware that scans the internet for vulnerable IoT devices and infects them to create a botnet. Mirai variants utilize lists of common default credentials to gain access to devices. Mirai's primary use is for launching distributed denial-of-service (DDoS) attacks, but it has also been used for cryptocurrency mining.
|
Botnet
Type
:
|
USA
Origin
:
|
|
1 September, 2016
First seen
:
|
7 February, 2026
Last seen
:
|
|
Type
:
|
USA
Origin
:
|
|
1 September, 2016
First seen
:
|
7 February, 2026
Last seen
:
|

 429
429
 0
0

 2259
2259
 0
0

 4388
4388
 0
0
Mirai is a botnet that has been targeting Internet of Things (IoT) devices since September 2016. It initially gained notoriety with denial-of-service attacks on several high-profile targets, including Krebs on Security, a blog run by the notable cybersecurity expert and journalist Brian Krebs. The botnet exploited the lack of security in IoT devices in the form of weak passwords, using them to generate massive traffic to overwhelm the target services.
The original developers, three college students from the United States, made the Mirai malware source code public in 2017 in an attempt to demonstrate their willingness to abandon criminal activity. However, this led to the creation of numerous variants of the malware, such as Hajime and Sylveon, as well as an influx of new threat actors employing these in their attacks.
Since then, the botnet has been experiencing a continuous evolution, gaining additional capabilities and exploiting new vulnerabilities found in different devices. It has been employed in numerous campaigns, by 2022 becoming one the largest botnets. According to some estimates, the Mirai malware has been used to infect over half a million IoT products.
Mirai's rise and scale can be attributed to a combination of factors. These include efficient spreading based on Internet-wide scanning and the widespread use of insecure default passwords in IoT products.
On the basic level, Mirai uses brute forcing to infect new devices. Here are the four stages that define its typical operation:
The malware usually communicates with the command-and-control (C2) over the TCP protocol. Yet, there are also TLS-capable variants.
After establishing its presence on a device, Mirai kills any processes associated with the activity of other botnets, such as Gafgyt, that might have infected it prior.
Over the past years, Mirai variants have been able to infect thousands of devices by abusing various vulnerabilities. For instance, in 2020, one Mirai variant took advantage of a security flaw (CVE-2020-9054) in Zyxel NAS devices, which allowed the malware to employ special characters to inject malicious commands and take control of devices.
Another vulnerability used by Mirai, which was identified in Comtrend VR-3033 routers in 2020, was CVE-2020-10173. It enabled attackers to compromise the network managed by the router by injecting malicious commands into its authentication process.
In 2022, Mirai was observed to explore the Spring4Shell vulnerability (CVE-2022-22965) by uploading its executable to target devices’ '/tmp' folder and leveraging the 'chmod' command to launch it.
Many variants of Mirai implement modified UPX packing to complicate the analysis process of their executables and make them more lightweight.
One of the latest variants of Mirai, NoaBot, which was first spotted in 2024, leverages SSH login brute forcing capabilities. Instead of launching DDoS attacks, it turns infected devices into crypto-mining machines.
Let’s take a look at how a typical Mirai malware attack unfolds by submitting a sample of this malware to the ANY.RUN sandbox.
Mirai infects the Ubuntu system typically through exposed and vulnerable Telnet or SSH ports. Once access is gained, Mirai downloads its binary from a C2server or through a peer-to-peer network onto the infected system.
To ensure persistence, Mirai may attempt to disable security software, delete competing malware, and create copies of itself in various system directories. It may also modify system startup scripts or use cron jobs to ensure it is executed on system reboot.
The infected system starts scanning the internet for other vulnerable devices by randomly generating IP addresses and attempting to log in using the same list of default credentials, infecting more devices.
The infected device establishes a connection with a C2 server to receive instructions from the botnet operator. These instructions can include launching DDoS attacks, downloading additional payloads, or updating.
It's important to note that the exact execution chain can vary depending on the variant of Mirai and the specific configuration of the infected system.
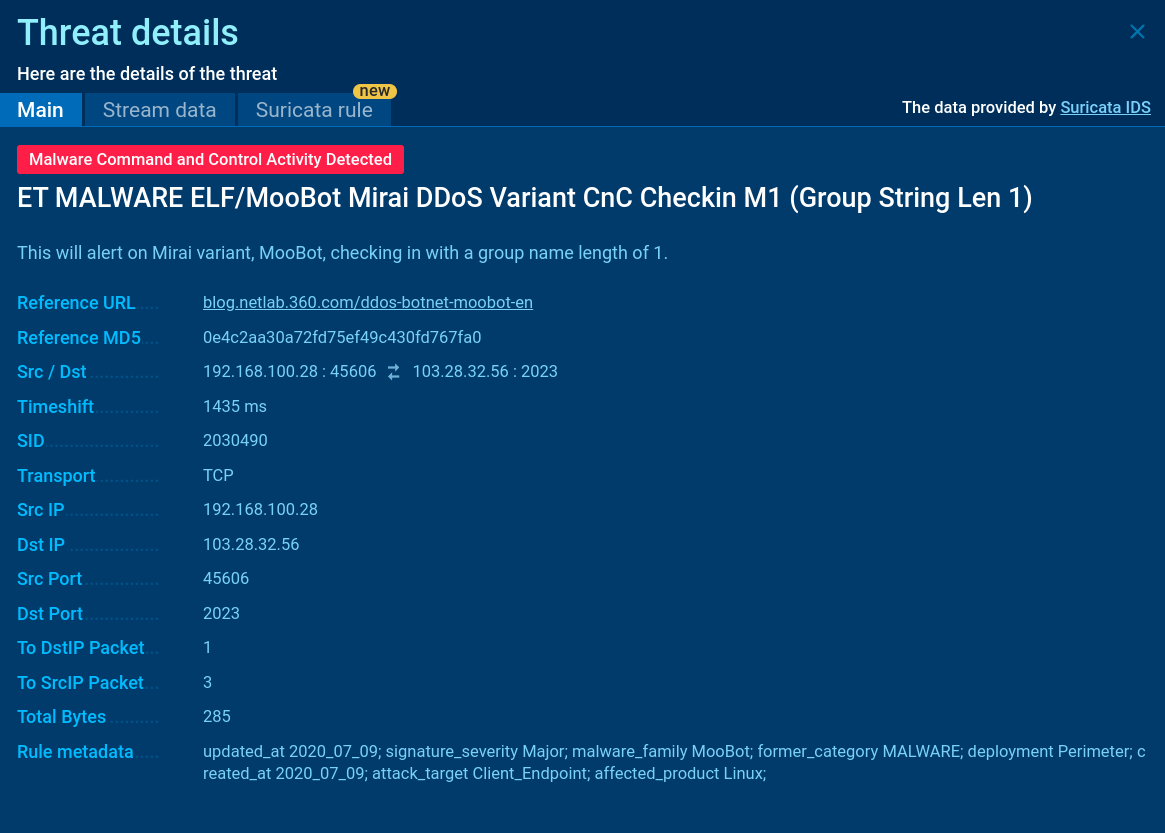 Suricata rule used for detecting Mirai in ANY.RUN
Suricata rule used for detecting Mirai in ANY.RUN
Unlike most malware families, such as Remcos and NjRAT, Mirai is not distributed via phishing emails or other common attack vectors. Instead, since it is a botnet, Mirai relies on self-propagation. This allows the botnet to grow rapidly and become more powerful, enabling it to launch larger and more devastating attacks.
To protect against Mirai and its variants, it is important to ensure that all IoT devices are secured with strong, unique passwords and that any known vulnerabilities are patched as soon as possible. To conduct Mirai malware analysis to see how the latest variants operate, use the ANY.RUN sandbox.
By executing Mirai in a controlled environment, you can observe its behavior and network activity without risking infection of your own infrastructure. This will enable you to identify the vulnerabilities employed by the malware, as well as expose its C2 servers.
Sign up for ANY.RUN now – it’s free!