Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


XRed operates as a stealthy backdoor, enabling cybercriminals to gain unauthorized remote access to infected systems. XRed has gained particular notoriety for its distribution through trojanized legitimate software and hardware drivers, making it exceptionally dangerous due to its ability to masquerade as trusted applications.
|
Backdoor
Type
:
|
Unknown
Origin
:
|
|
1 April, 2019
First seen
:
|
4 March, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 April, 2019
First seen
:
|
4 March, 2026
Last seen
:
|

 165
165
 0
0

 448
448
 0
0

 1911
1911
 0
0
XRed, also known as Synaptics worm, is a sophisticated backdoor malware that has emerged as a significant cybersecurity threat since at least 2019. It is designed for long-term system infiltration and control and stealing sensitive data. It combines elements of remote access Trojans (RATs), infostealers, and backdoors to execute a range of malicious activities.
The malware demonstrates advanced capabilities including self-replication, persistence mechanisms, and remote command execution. What makes XRed particularly concerning is its professional development quality.
The malware operates through a multi-stage infection process, beginning with initial compromise through trojanized software and progressing to establish persistent access for data exfiltration and system control. XRed employs various anti-detection techniques and creates multiple infection vectors to ensure continued access to compromised systems. The backdoor’s architecture allows for modular payload delivery, enabling threat actors to customize attacks based on specific targets and objectives.
XRed is often associated with cybercriminal groups and, in some cases, state-sponsored actors, who use it to target high-value assets for financial gain, espionage, or disruption.
The malware’s ability to remain undetected stems from its use of legitimate system tools (living-off-the-land techniques) and its capacity to mimic benign software processes. XRed’s development is believed to be part of the growing Cybercrime-as-a-Service (CaaS) ecosystem, where malware kits are sold on the dark web, enabling even low-skill attackers to deploy it effectively.
XRed targets a broad spectrum of victims, with particular focus on:
Individual Users:
Business Sectors:
Geographically, attacks have been reported predominantly in North America, Europe, and the Asia-Pacific region, with a notable spike in the APAC region in 2024. Individuals with access to high-value credentials, such as IT administrators or executives, are prime targets for XRed’s credential-harvesting capabilities, often through spear-phishing campaigns.
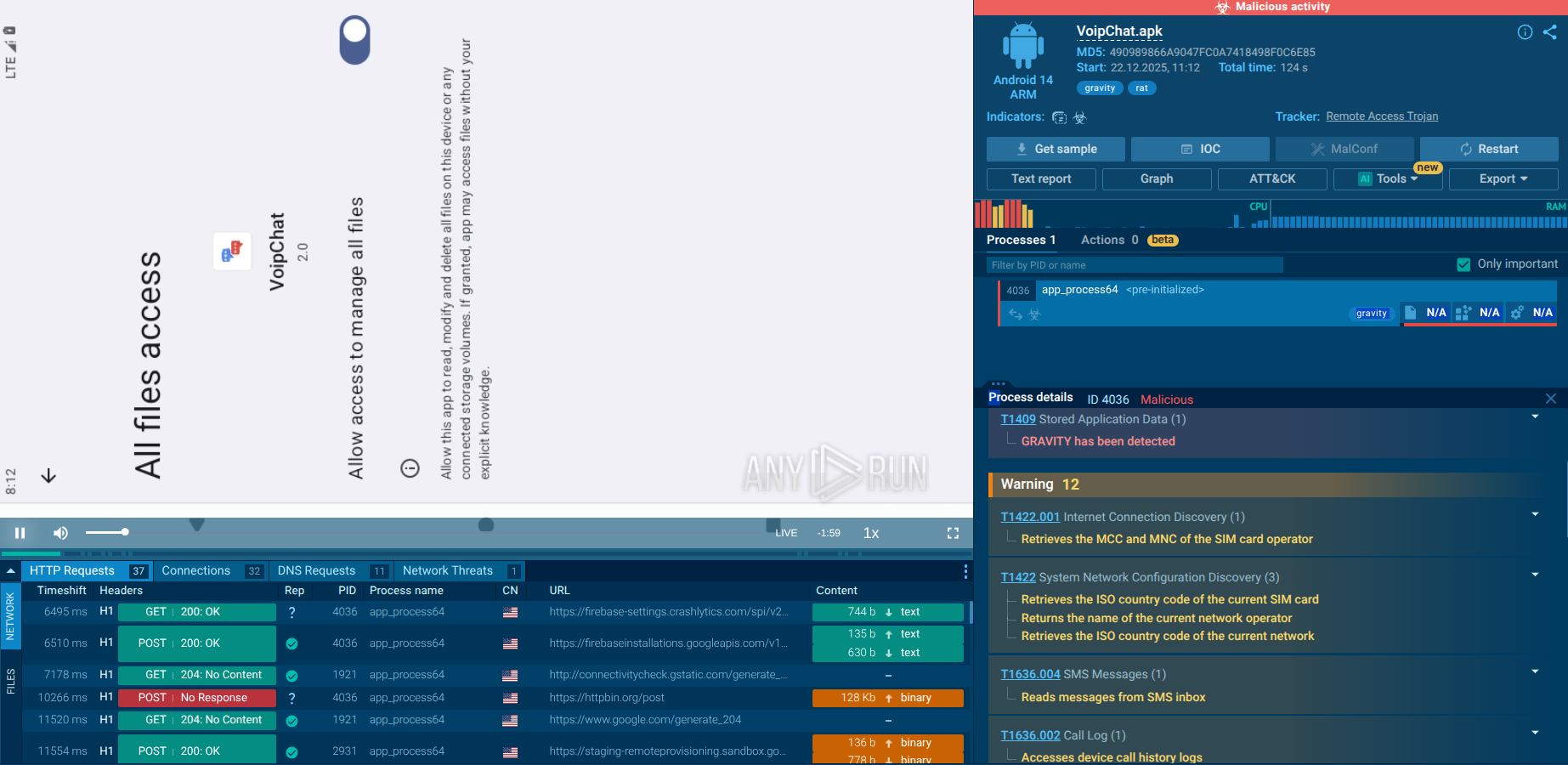
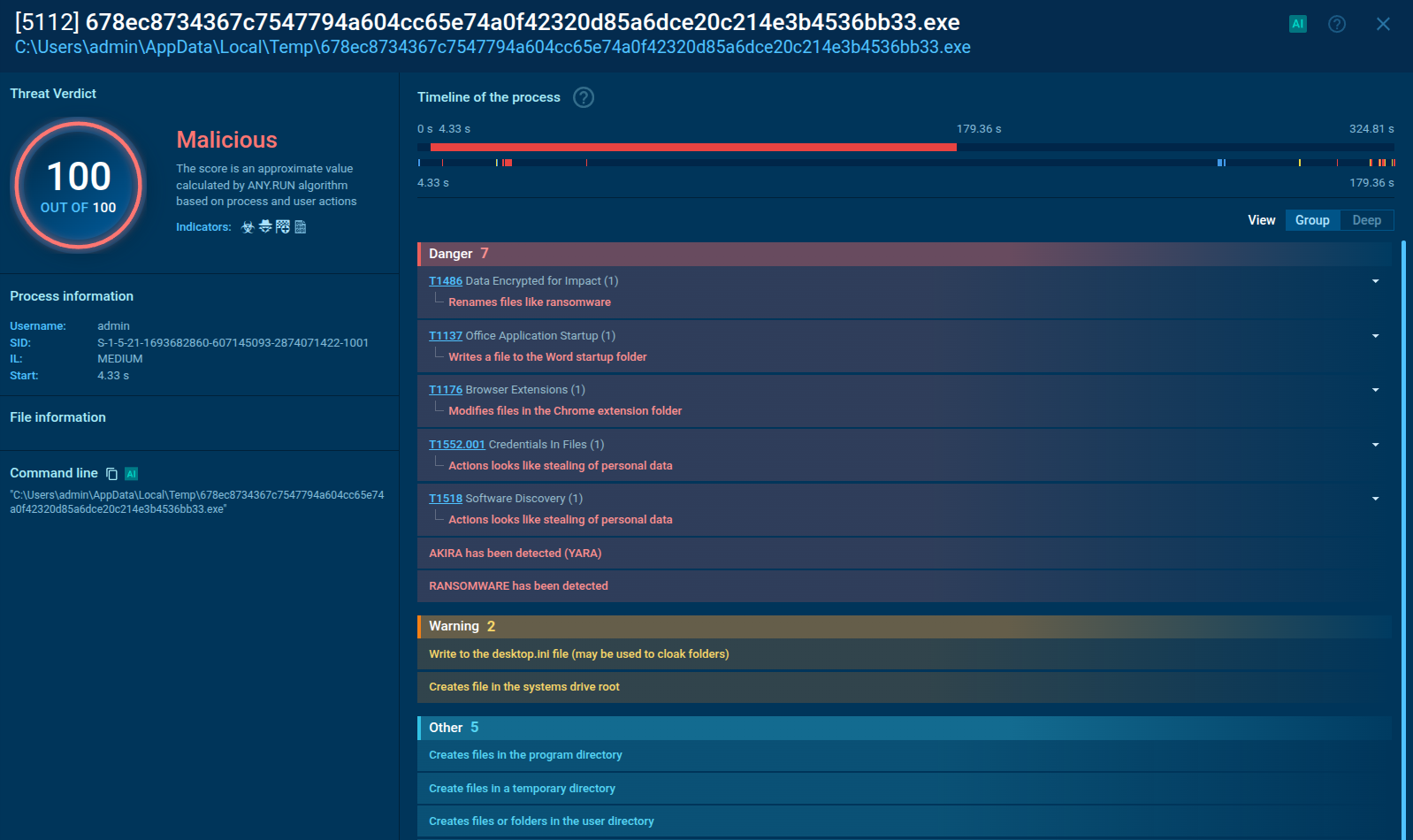
ANY.RUN’s Interactive Sandbox contains an assortment of XRed analysis sessions featuring different associated malware and attack vectors. By detonating XRed samples, we can understand the key points of its attack chain.
 XRed sample analysis in the Interactive Sandbox
XRed sample analysis in the Interactive Sandbox
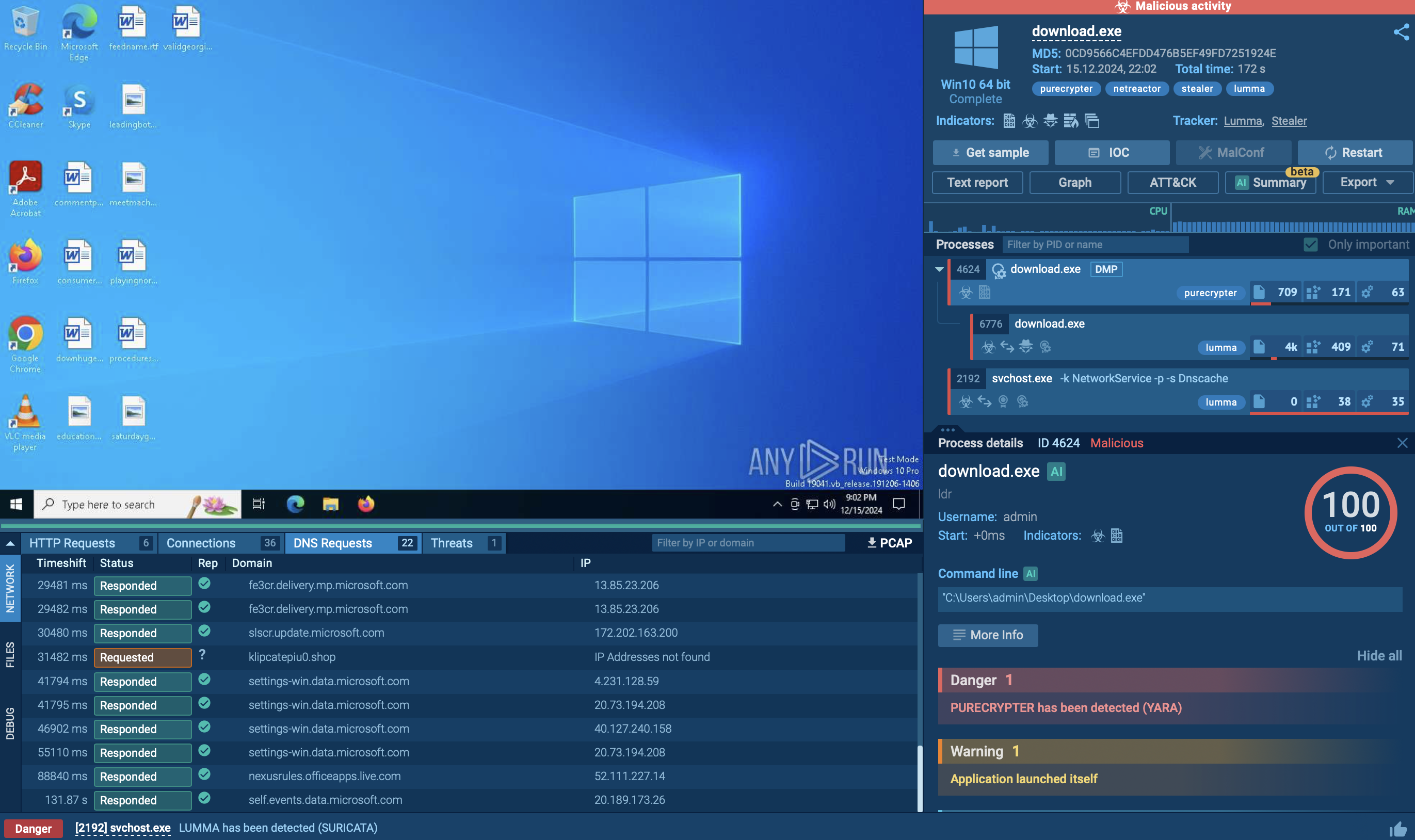
XRed is delivered through trojanized programs that pose as legitimate software. When activated, the malicious file usually launches the legitimate utility it's disguised as to avoid detection.
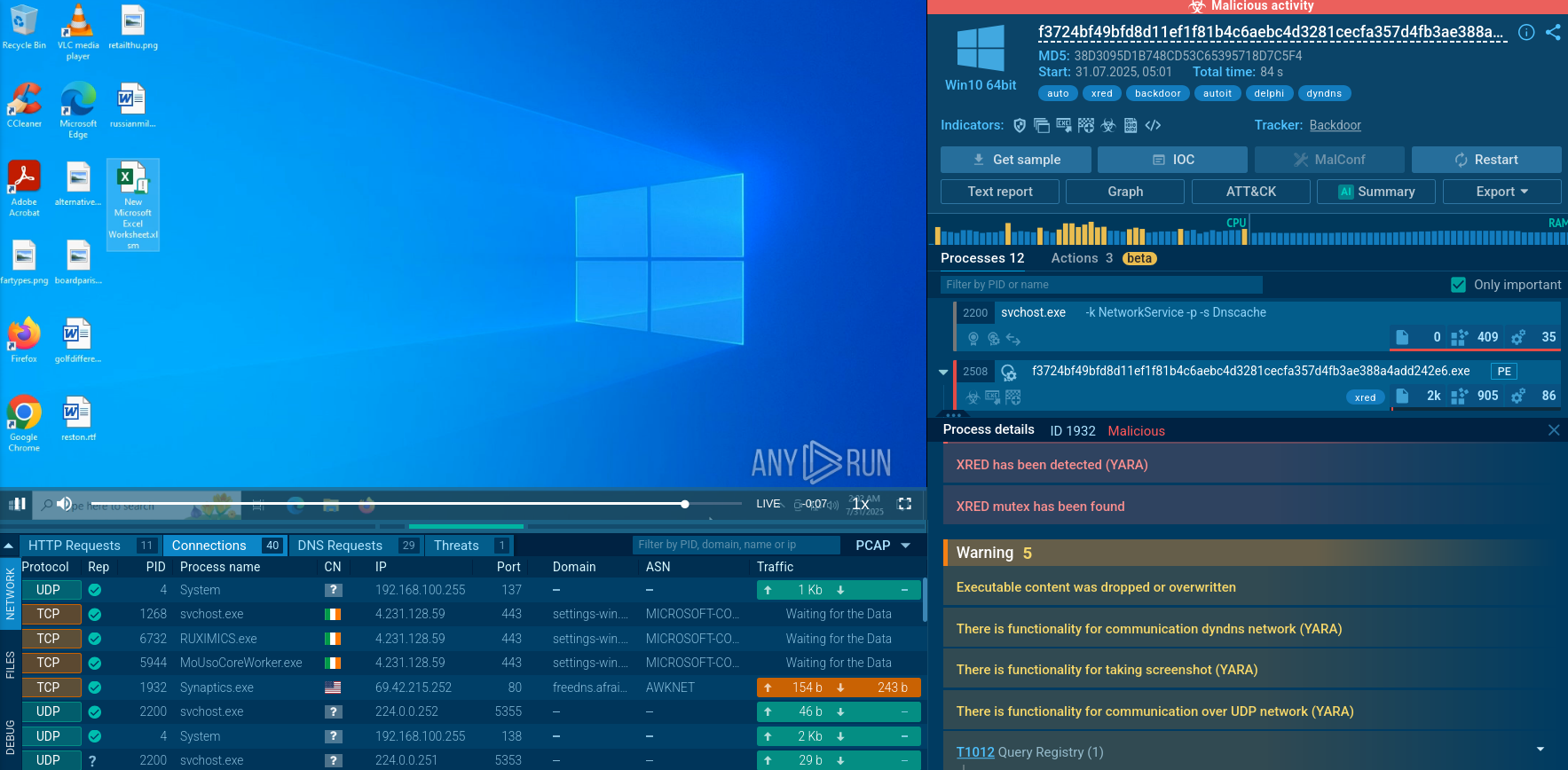
To prevent multiple instances from running, XRed checks for the Synaptics2X mutex, which remains unchanged in the samples, and masquerades as Synaptics.exe. These are typical IOCs for XRed, and they are preserved in most instances. After creating Synaptics.exe, the file is added to the system's startup.
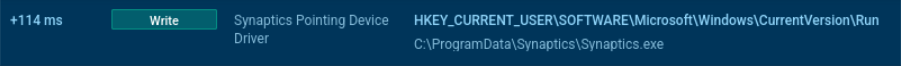 XRed adds file in autorun
XRed adds file in autorun
Once initialized, XRed gathers system data. The backdoor also provides remote system control, supporting commands for taking screenshots, accessing the command line, managing files, and listing drives and directories.
XRed also infects Excel files by embedding a VBA script that includes malicious code, as seen in the example of file interaction.
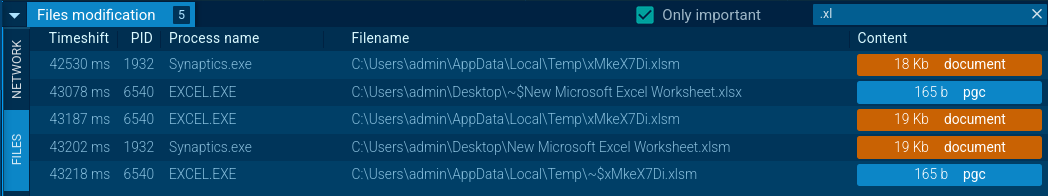 XRed file modifications filtered by extension
XRed file modifications filtered by extension
The embedded VBA can be viewed using the sandbox functionality.
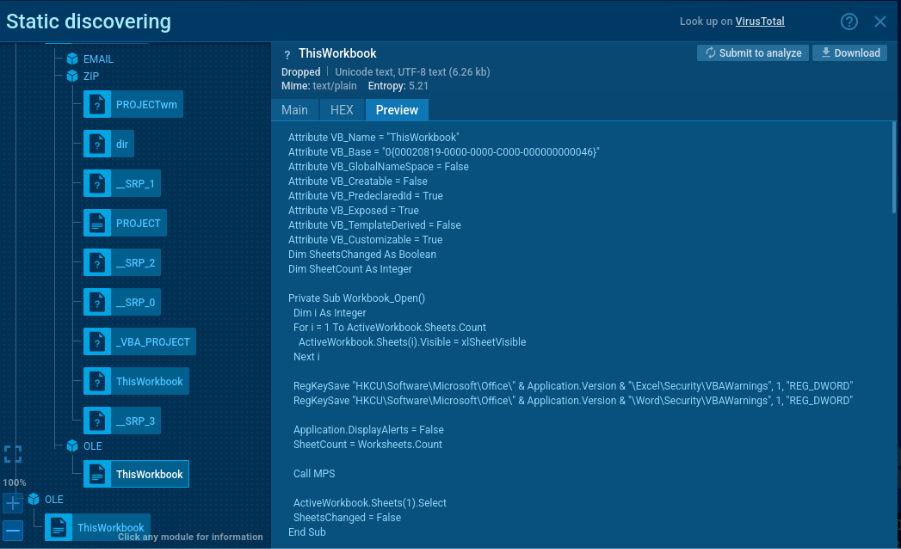 VBA file modified by XRed
VBA file modified by XRed
Exploring the sandbox analyses, we can observe the key features of XRed:
XRed operates leverages several sophisticated mechanisms:
Primary Distribution Vectors:
Persistence Mechanisms:
Data Exfiltration:
Evasion Techniques:
Modular Architecture:
While specific XRed attacks are not well-documented in public sources due to its recent emergence, several high-profile incidents in 2024 align with its TTPs:
By integrating threat intelligence into security operations, organizations can stay ahead of XRed’s evolving threat landscape. It provides indicators of compromise (e.g., malicious IPs, domains, or file hashes) to block XRed’s C&C communications and offers insights into XRed’s tactics, techniques, and procedures, enabling tailored defense strategies.
It also fuels proactive threat hunting allowing organizations to search for XRed’s presence before it causes damage, using tools like YARA rules or SIEM integrations.
Start gathering IOCs and behavioral data with the malware name search request to Threat Intelligence Lookup:
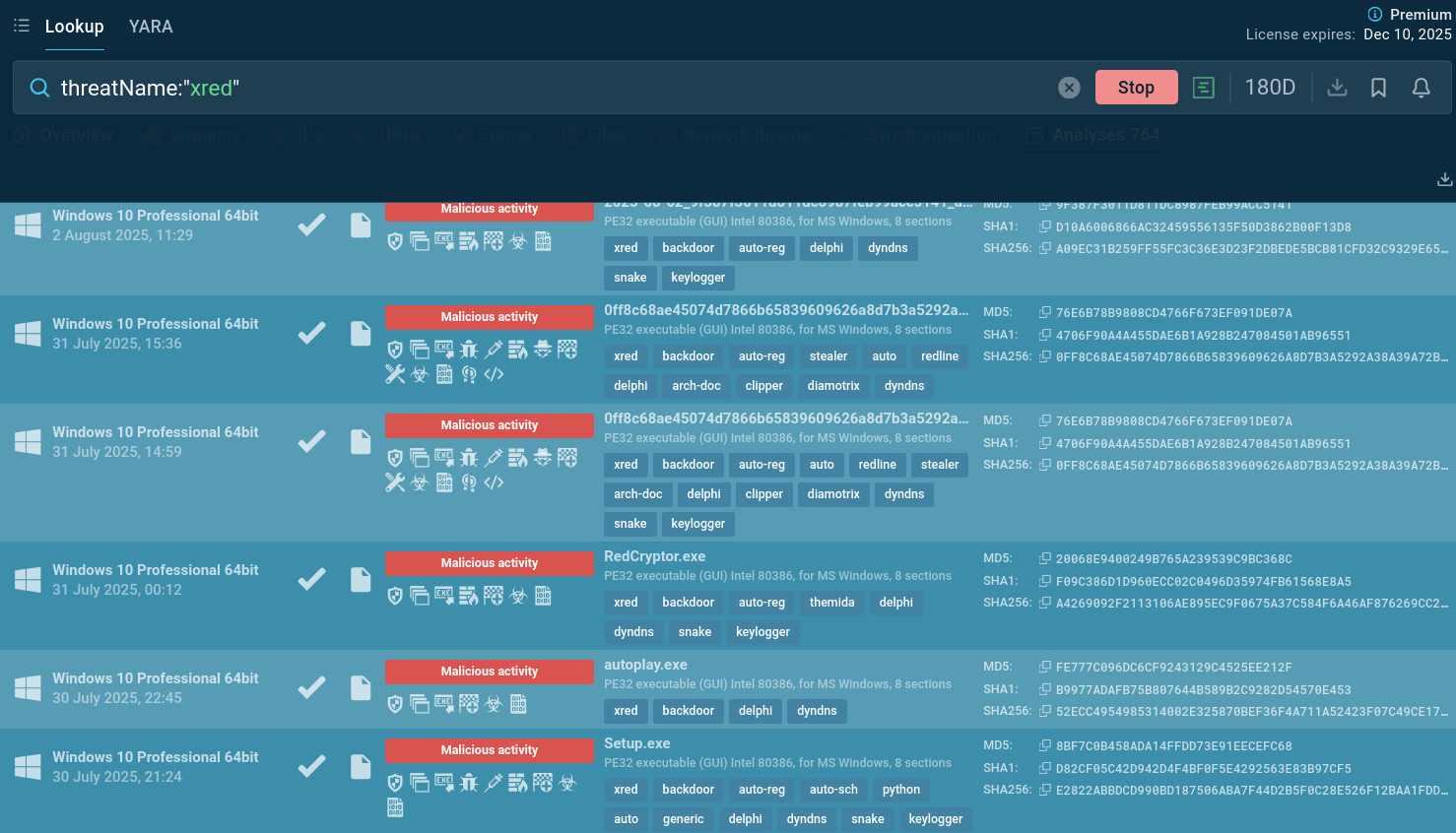 XRed malware samples found via TI Lookup
XRed malware samples found via TI Lookup
You can also search TI Lookup for the above-mentioned mutex engaged in most of the malware versions being a reliable IOC:
syncObjectName:"Synaptics2X" AND imagePath:"ProgramData\Synaptics\Synaptics.exe"
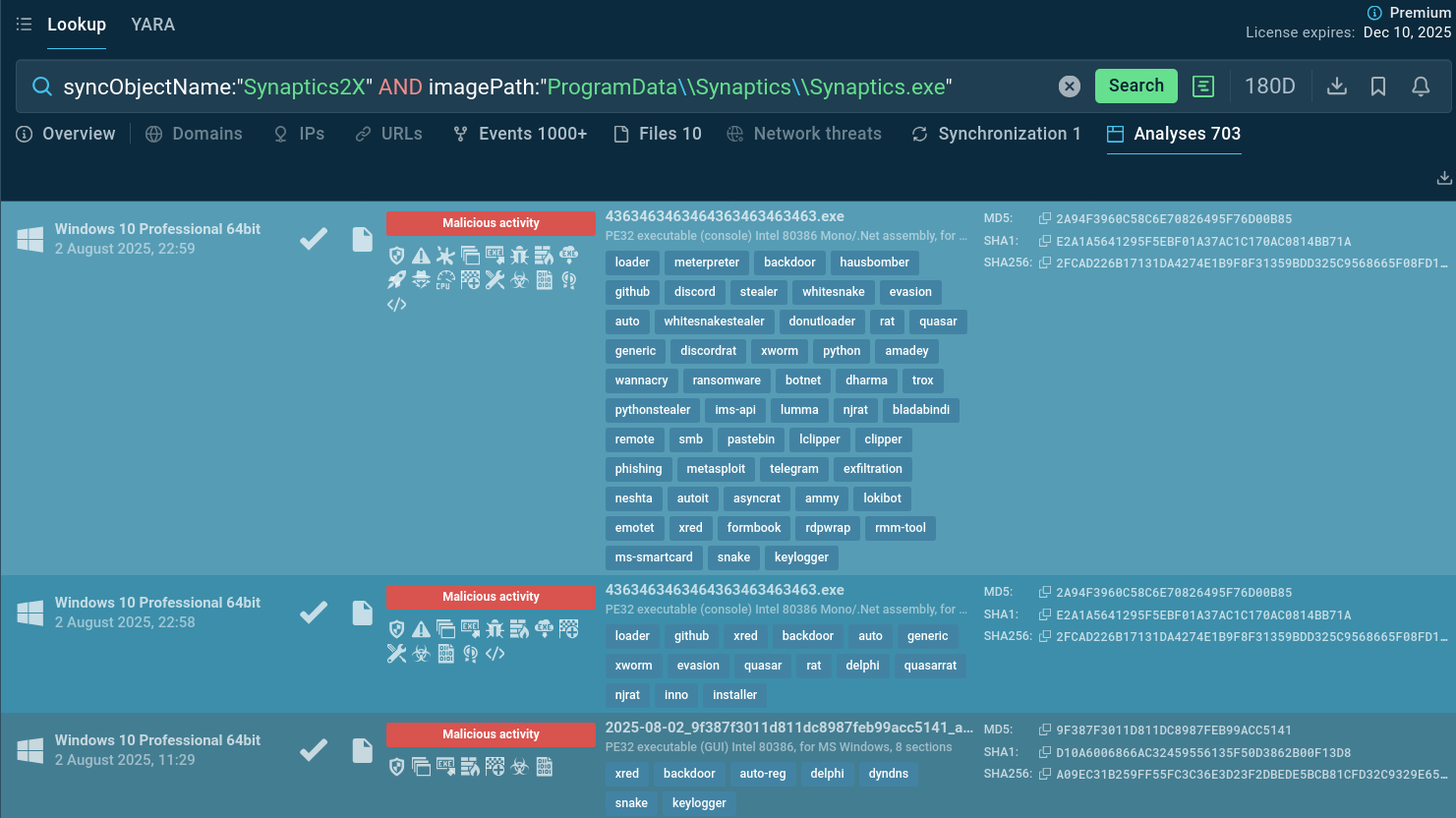 XRed malware samples featuring Synaptics mutex
XRed malware samples featuring Synaptics mutex
XRed is a sophisticated and adaptable threat that demands constant vigilance. Its modular design, stealthy operation, and high-impact potential make it one of the more dangerous malware families targeting modern enterprises. Robust detection mechanisms, proactive threat intelligence, and a security-first culture are critical in defending against it.
Gather fresh actionable threat intelligence via ANY.RUN’s TI Lookup: start with 50 trial requests.