Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


BlackMatter is a ransomware strain operating as a Ransomware-as-a-Service (RaaS), designed to encrypt files, remove recovery options, and extort victims across critical industries. Emerging in 2021, it quickly became a major concern due to its ability to evade defenses, spread across networks, and cause large-scale operational disruption, forcing security teams to act against a highly destructive and persistent threat.
|
Ransomware
Type
:
|
Unknown
Origin
:
|
|
1 August, 2021
First seen
:
|
27 February, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 August, 2021
First seen
:
|
27 February, 2026
Last seen
:
|

 787
787
 0
0

 478
478
 0
0

 2728
2728
 0
0
BlackMatter, first identified in mid-2021, is a ransomware strain operating under the Ransomware-as-a-Service (RaaS) model. It is designed to target organizations across multiple industries, including healthcare, telecommunications, finance, education, government, and other critical infrastructure, making it one of the more disruptive threats in circulation.
In contrast to opportunistic ransomware, BlackMatter is deployed strategically. Once active, it encrypts files on both local and network resources, disables recovery mechanisms, and prevents victims from restoring data without negotiating with the attackers.
The malware features advanced evasion capabilities, such as Safe Mode encryption, partial file encryption to accelerate attacks, and anti-debugging techniques. It leverages a hybrid cryptographic approach, Salsa20 for file content and RSA-1024 for session keys, to lock data securely while remaining under detection thresholds.
Since its emergence, BlackMatter has been observed in both Windows and Linux campaigns, with incidents continuing into 2025. Its operators often deliver the ransomware via phishing emails, malicious attachments, or by exploiting stolen credentials to move laterally through a network.
Attackers commonly spread BlackMatter through:
Like other modern ransomware families, BlackMatter often disguises its processes under legitimate Windows services (such as svchost.exe) to evade detection and maintain persistence within the system.
BlackMatter ransomware campaigns were notable for targeting large enterprises and critical infrastructure rather than indiscriminate attacks on individuals. Although the group publicly claimed to avoid healthcare and government sectors, many victims still came from sensitive industries.
Typical targets included:
The ransomware was distributed globally, with most confirmed victims in North America, Europe, and Asia. Reported ransom demands ranged from $80,000 to $30 million, with attackers typically requiring cryptocurrency payments.
Some of the most high-profile cases included:
The group struck more than 50 organizations in just four months of active operations, with an average ransom demand of $5.3 million.
Despite its short lifespan after launching in mid-2021, BlackMatter quickly built a reputation as one of the most prolific ransomware operations of its time. Following law enforcement pressure and a wave of arrests in Europe, the operators announced their shutdown in November 2021. Still, successor activity, blending tactics from DarkSide and REvil, ensured that organizations across multiple sectors continued to face derivative campaigns into 2025.
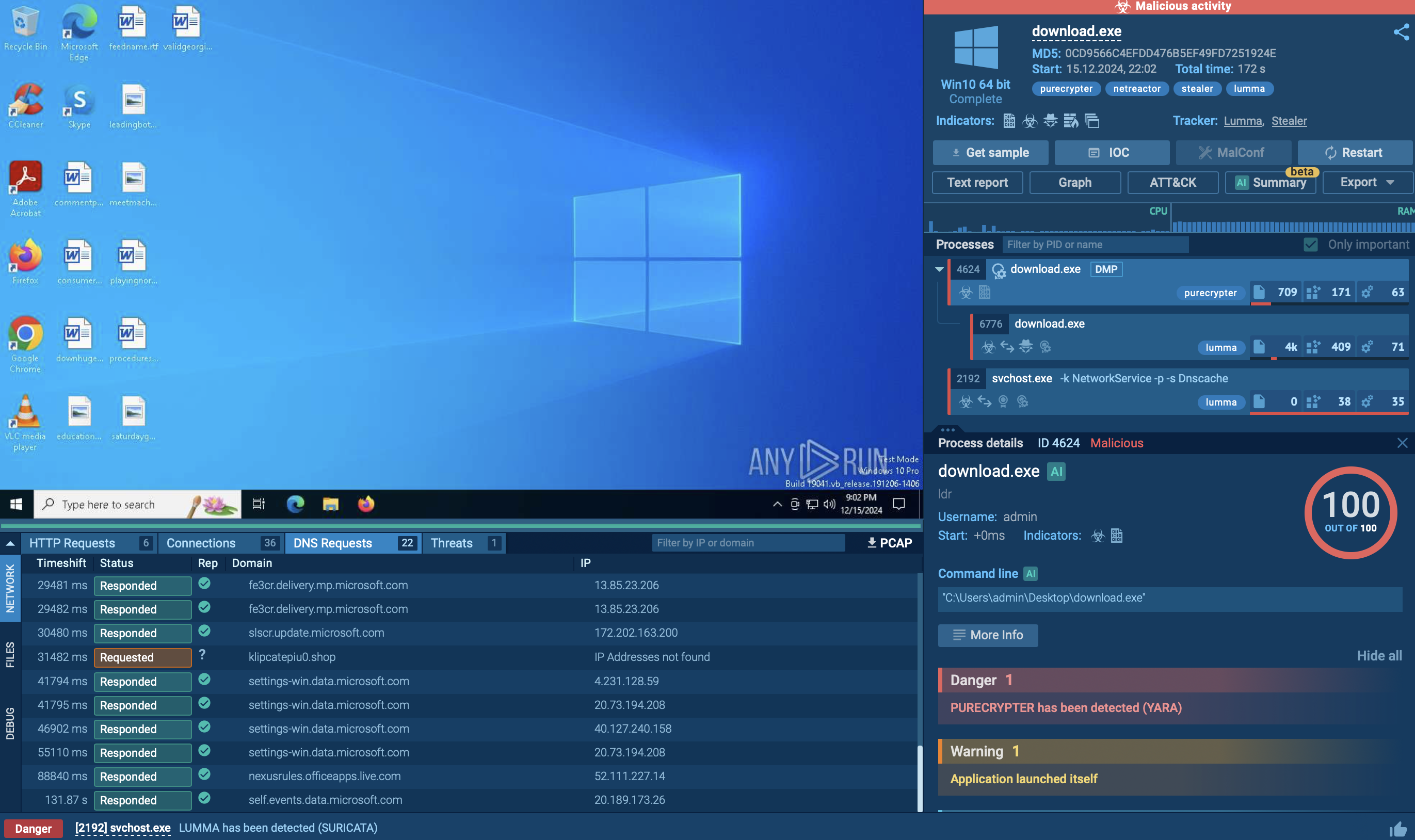
There are numerous BlackMatter ransomware samples detonated in ANY.RUN’s Interactive Sandbox and analyzed by SOC teams worldwide. Let’s walk through how a typical infection unfolds.
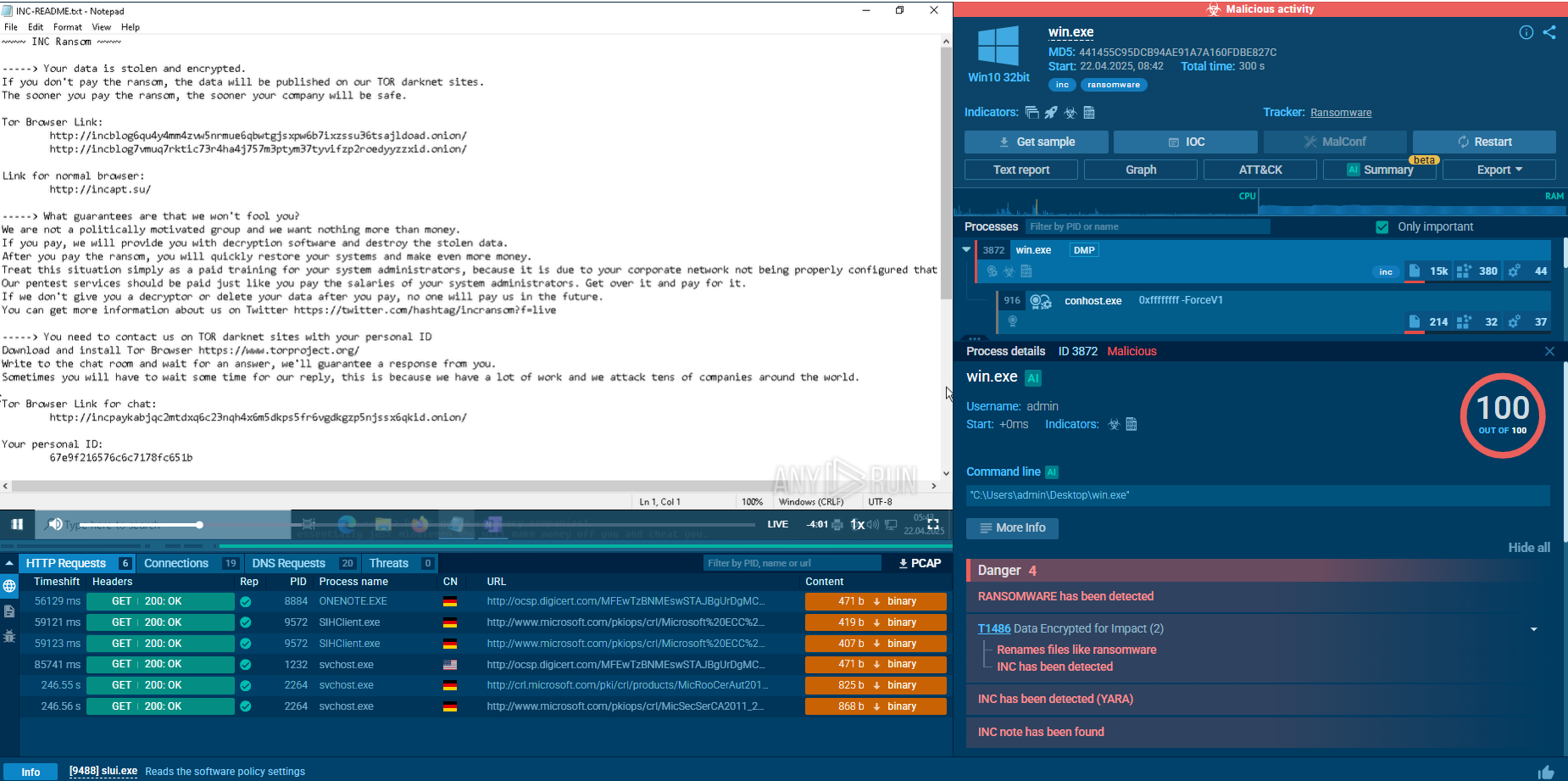
View analysis session with BlackMatter RAT
BlackMatter RAT analyzed inside ANY.RUN sandbox
Once executed, BlackMatter begins with a system check, creates the mutex Global\SystemUpdate_svchost.exe, copies itself into a new directory, and registers for autorun to ensure persistence. It then bypasses UAC, escalates privileges, and modifies the PowerShell execution policy to allow malicious commands to run without restriction.
Next comes the destructive preparation stage. The ransomware deletes shadow copies and backups (vssadmin, wbadmin), disables the Windows Recovery Environment (reagentc), and modifies boot configuration settings (bcdedit) to prevent recovery. In parallel threads, it uses net.exe and sc.exe to stop critical services and applications such as antivirus software, SQL databases, and backup tools, clearing the way for uninterrupted encryption.

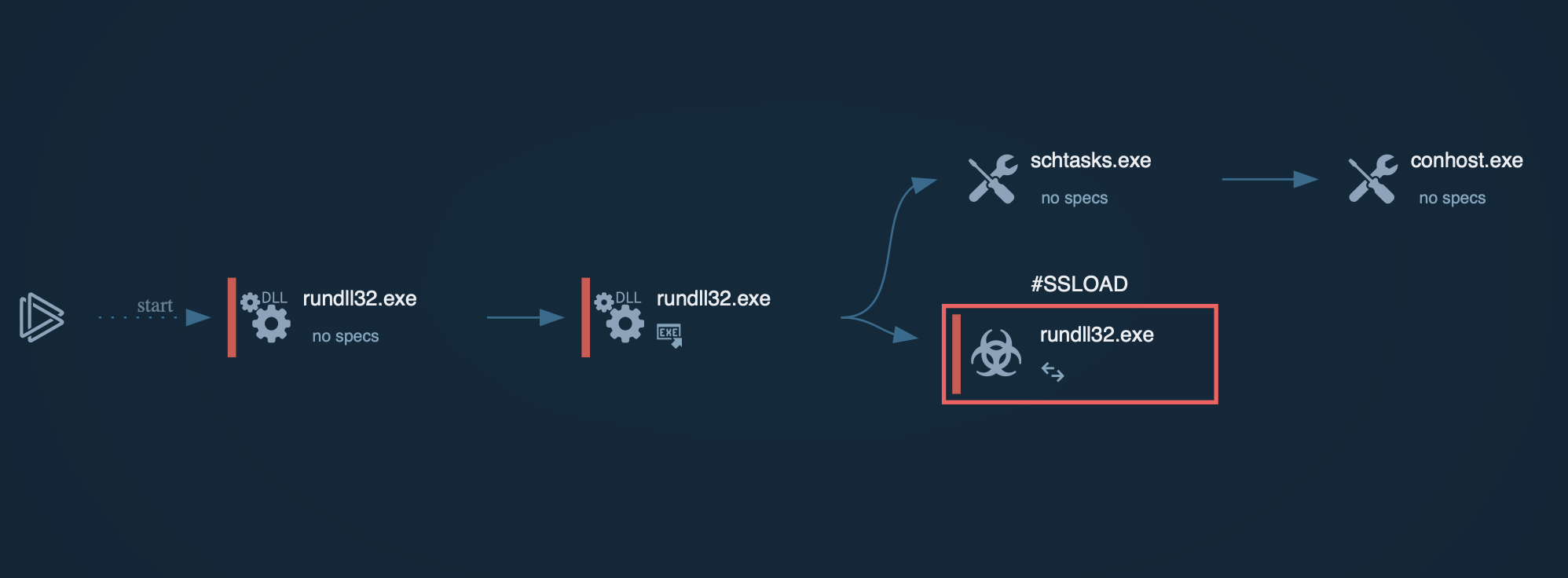
Relevant TTPs displayed inside ANY.RUN sandbox
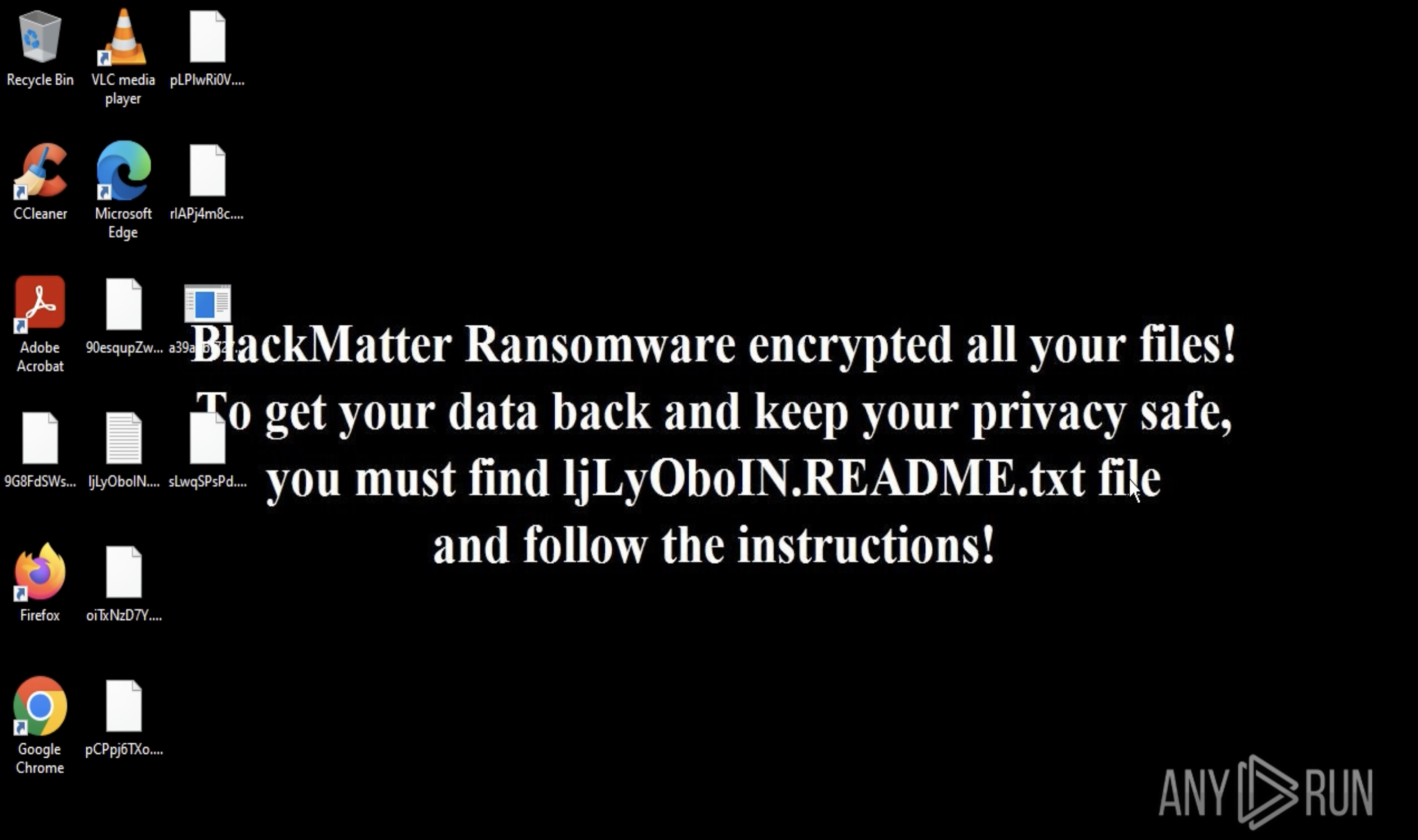
Finally, BlackMatter scans local and network drives, encrypts files with its own extension, and drops ransom notes with payment instructions in every affected directory. It also replaces the victim’s desktop background with a warning message, pointing to the ransom note for further details.
 Ransom note displayed inside ANY.RUN’s sandbox
Ransom note displayed inside ANY.RUN’s sandbox
Once deployed, BlackMatter executes a destructive sequence designed to ensure full control and maximum damage. Its capabilities include:

System information discovery, including computer name, Machine GUID and language settings

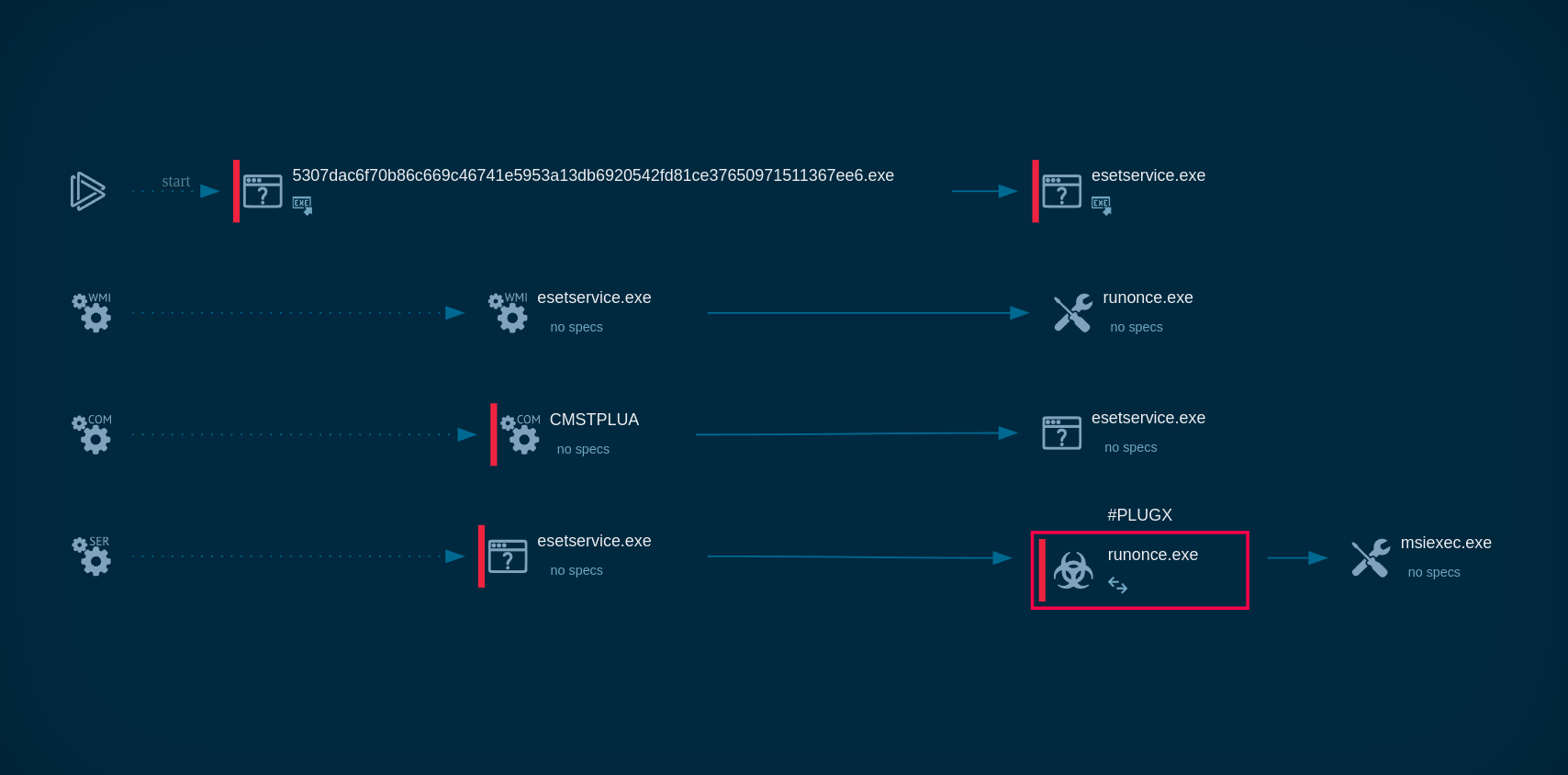
Creation of scheduled task exposed inside ANY.RUN sandbox

Sc.exe and net.exe used for service control

Malicious .bat files visible inside ANY.RUN’s sandbox
BlackMatter is built for speed and disruption rather than long-term control. Its architecture combines:
This streamlined design allows attackers to cripple organizations in a short window of access, leaving defenders with almost no opportunity to intervene once execution begins.
For organizations, BlackMatter ransomware poses a severe threat that extends far beyond the encryption of individual files. Its design ensures maximum operational disruption, financial loss, and reputational damage.
Integrating threat intelligence into security operations is essential for detecting and mitigating BlackMatter attacks. Threat intelligence provides fresh indicators of compromise (IOCs), such as malicious IP addresses, domains, and file hashes, that can be used to block command-and-control infrastructure and monitor for early signs of compromise.
It also supports proactive threat hunting, enabling SOC teams to look for BlackMatter’s presence before encryption begins. Detection can rely on known behaviors, including registry modifications for persistence, use of tools like vssadmin and bcdedit for recovery elimination, and service control via sc.exe and net.exe.
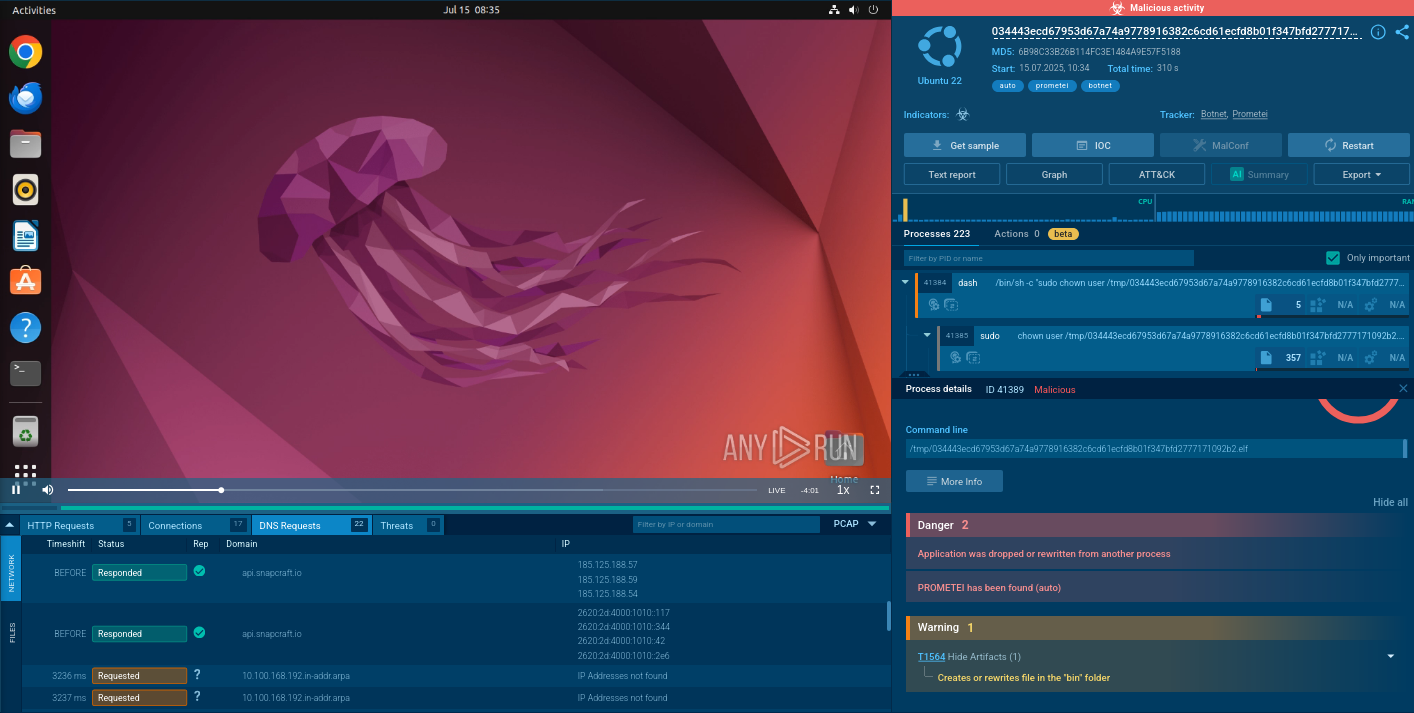
Start gathering IOCs and behavioral data with the malware name search request to Threat Intelligence Lookup:
 BlackMatter ransomware samples found via TI Lookup
BlackMatter ransomware samples found via TI Lookup
BlackMatter highlights how ransomware groups now operate like professional businesses, capable of paralyzing entire organizations in hours. By wiping recovery options, halting services, and demanding multimillion-dollar ransoms, it forces executives, IT teams, and SOC analysts into crisis mode.
For security leaders, this means preparing not just technically but organizationally: ensuring SOC teams can spot ransomware behaviors early, aligning with legal and communications teams for incident response, and protecting brand trust when critical services are disrupted.
Staying ahead requires threat intelligence that goes beyond file signatures; context on attacker tactics, visibility into live campaigns, and shared IOCs that teams can act on quickly.
Gather fresh actionable threat intelligence via ANY.RUN’s TI Lookup: start with 50 trial requests.