Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


VanHelsing is a sophisticated ransomware strain that appeared in early 2025, operating via the Ransomware-as-a-Service (RaaS) model and targeting primarily USA and France. It threatens mostly Windows systems but has variants for Linux, BSD, ARM, and ESXi, making it a multi-platform malware. It is also notable for its advanced evasion techniques, double extortion tactics, and rapid evolution.
|
Ransomware
Type
:
|
Unknown
Origin
:
|
|
1 March, 2025
First seen
:
|
4 February, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 March, 2025
First seen
:
|
4 February, 2026
Last seen
:
|

 793
793
 0
0

 482
482
 0
0

 2730
2730
 0
0
With its affiliate program launching in the dark web on March 7, 2025, VanHelsing ransomware spread rapidly infecting three victims within two weeks. This RaaS’s affiliates are demanded “not to target the Commonwealth of Independent States (CIS)”. VanHelsing’s double extortion model involves encrypting valuable data and threatening to leak it to extort ransom.
Known to demand up to $500,000 in Bitcoin, VanHelsing operates as a scalable platform, allowing affiliates to join with a $5,000 deposit and keep 80% of ransom payments, while operators take 20%. Government, manufacturing, pharmaceuticals have become the most affected industries, with further expansion to finance, healthcare, and critical infrastructure.
VanHelsing employs multiple initial access vectors: phishing emails, unpatched software or systems, RDP weaknesses, VPN services, cloud misconfigurations, legitimate remote management tools, supply chain attacks.
Once inside, VanHelsing uses techniques like Windows Management Instrumentation (WMI) for stealthy execution and credential dumping to escalate privileges. It encrypts files using strong encryption algorithms and appends the “.vanhelsing” extension, rendering them inaccessible. Then it alters the desktop wallpaper and drops a ransom note.
VanHelsing hunts for sensitive data (personal details, financial records, or corporate documents) for double extortion. Its persistence is maintained by modifying registry, scheduling tasks, or installing bootkits.
VanHelsing poses significant risks due to:
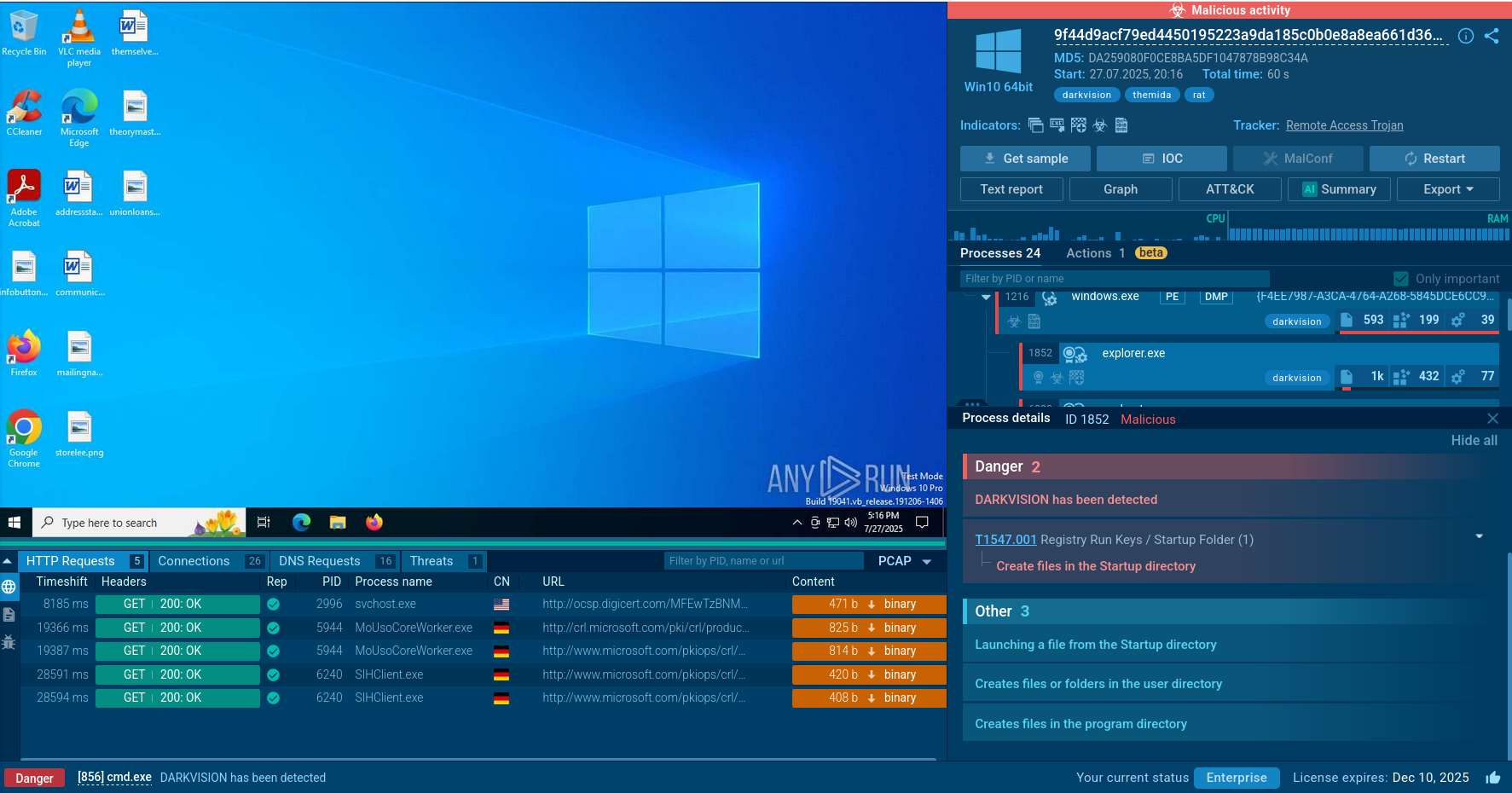
An illustrative example of VanHelsing’s attack paradigm can be found in the repository of fresh malware samples of ANY.RUN’s Interactive Sandbox.
View VanHelsing kill chain to explore its processes, connections, and IOCs.
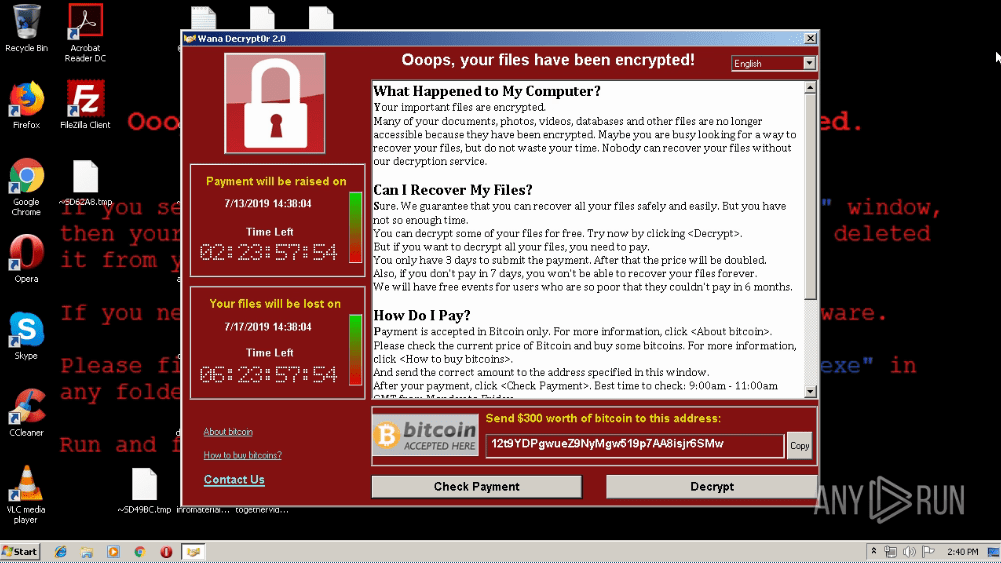
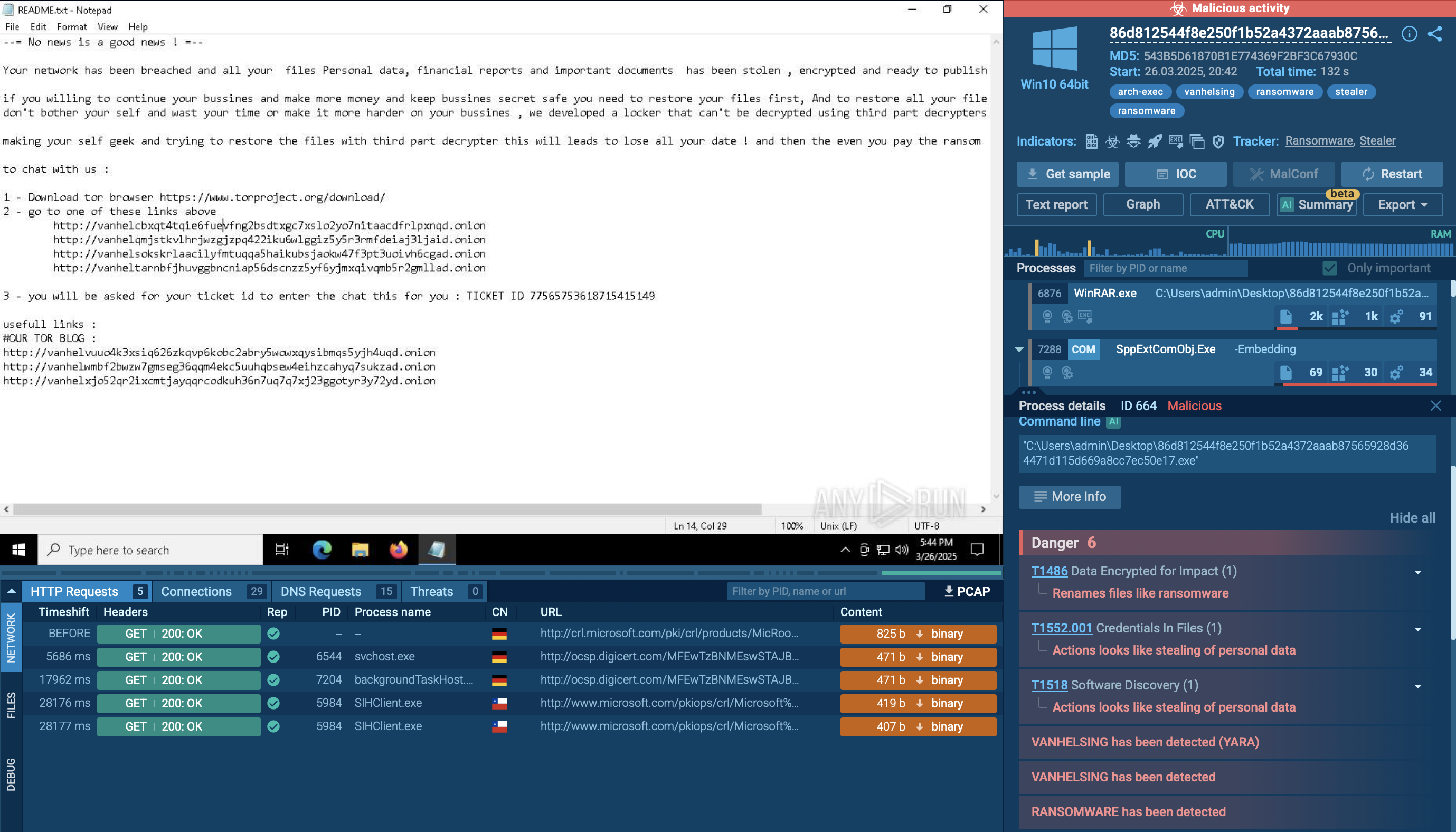 _ VanHelsing Ransomware sample in ANY.RUN's Interactive Sandbox_
_ VanHelsing Ransomware sample in ANY.RUN's Interactive Sandbox_
Once executed, the ransomware first enumerates all available drives on the system, including both local and network drives, while deliberately avoiding core system files to prevent rendering the system unbootable.
After identifying its targets, VanHelsing generates a unique encryption key and nonce. It uses the ChaCha20 algorithm for file encryption, with the key and nonce subsequently encrypted using an embedded Curve25519 public key. For files smaller than approximately 1 GB, the entire file is encrypted; for larger files, only the first 30% is encrypted to accelerate the process while retaining leverage over the victim.
The encrypted data, along with the key and nonce metadata, is stored in a structured format within each file. As files are encrypted, the ransomware appends the ".vanhelsing" or, in some cases, ".vanlocker" extension to the affected files. It also drops a ransom note — typically named README.txt — in every encrypted directory. This note informs the victim of the breach, warns against using third-party decryptors due to the risk of permanent data loss, and demands a ransom — often a significant amount in Bitcoin — for decryption and deletion of exfiltrated data.
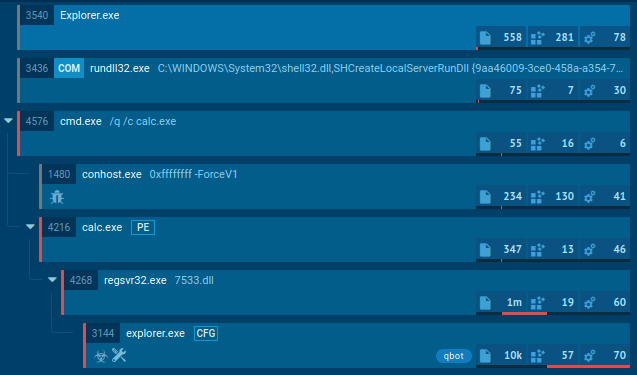
VanHelsing creates a mutex named "VanHelsing" to prevent multiple instances from running simultaneously on the same system. It may also change the desktop wallpaper to display its branding. Additionally, this ransomware supports command-line arguments for silent execution, verbose logging, and selective targeting of specific drives, directories, or files. In our case, it used CMD and WMIC commands to delete shadow copies on the infected system.
Why Specific Attack Details Are Limited
Threat intelligence is one of the main tools for detecting and preventing damage from VanHelsing. It is essential to monitor Indicators of Compromise (IOCs) like the “.vanhelsing” file extension, Tor-based C2 domains, or Bitcoin wallet addresses employed by ransomware operators. IOCs, IOA, IOBs, and malware samples found via ANY.RUN’s Threat Intelligence Lookup will provide you with actionable indicators for setting up monitoring and alerts, as well as with insights into the ransomware behavior and adversaries’ tactics.
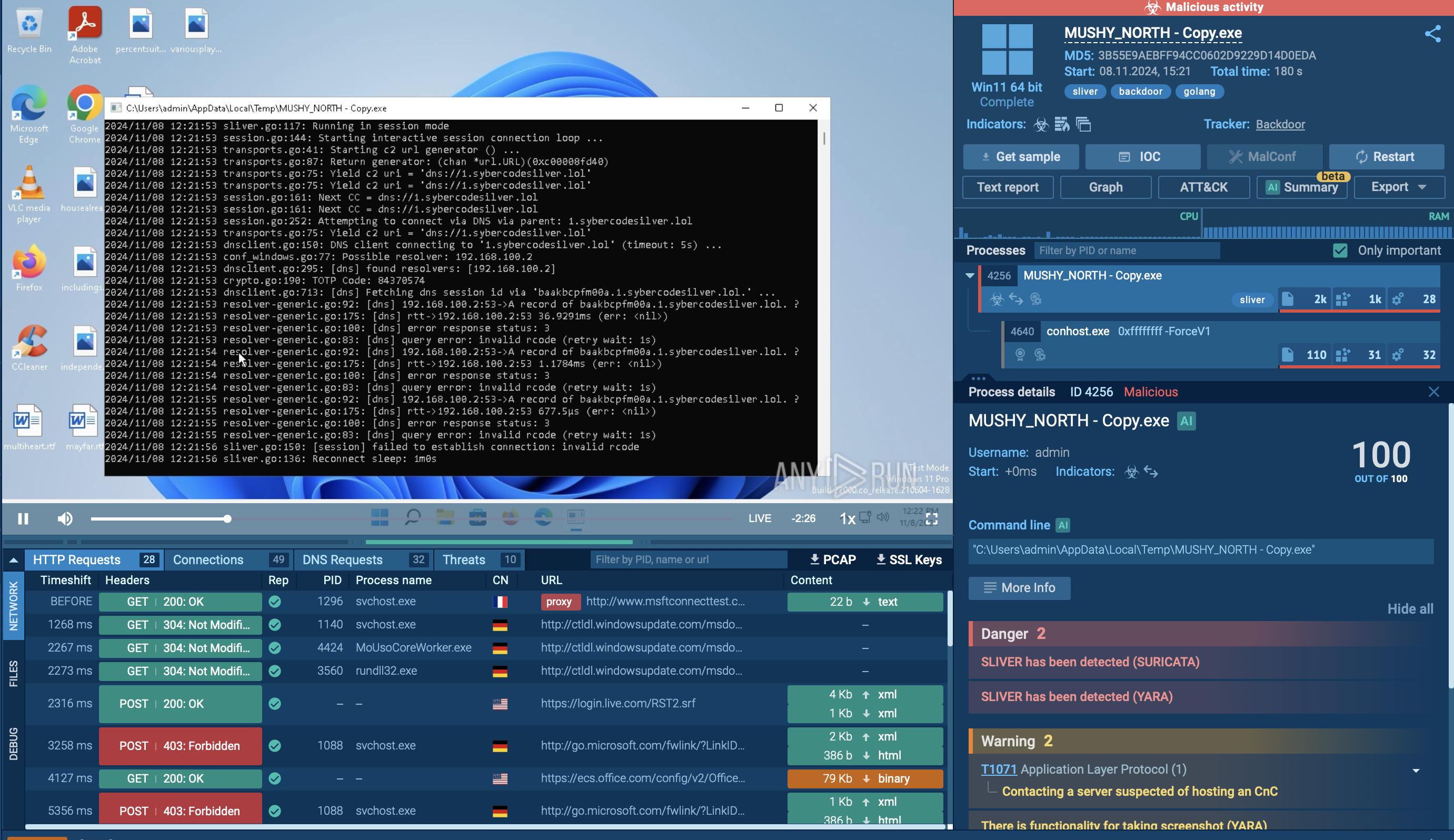
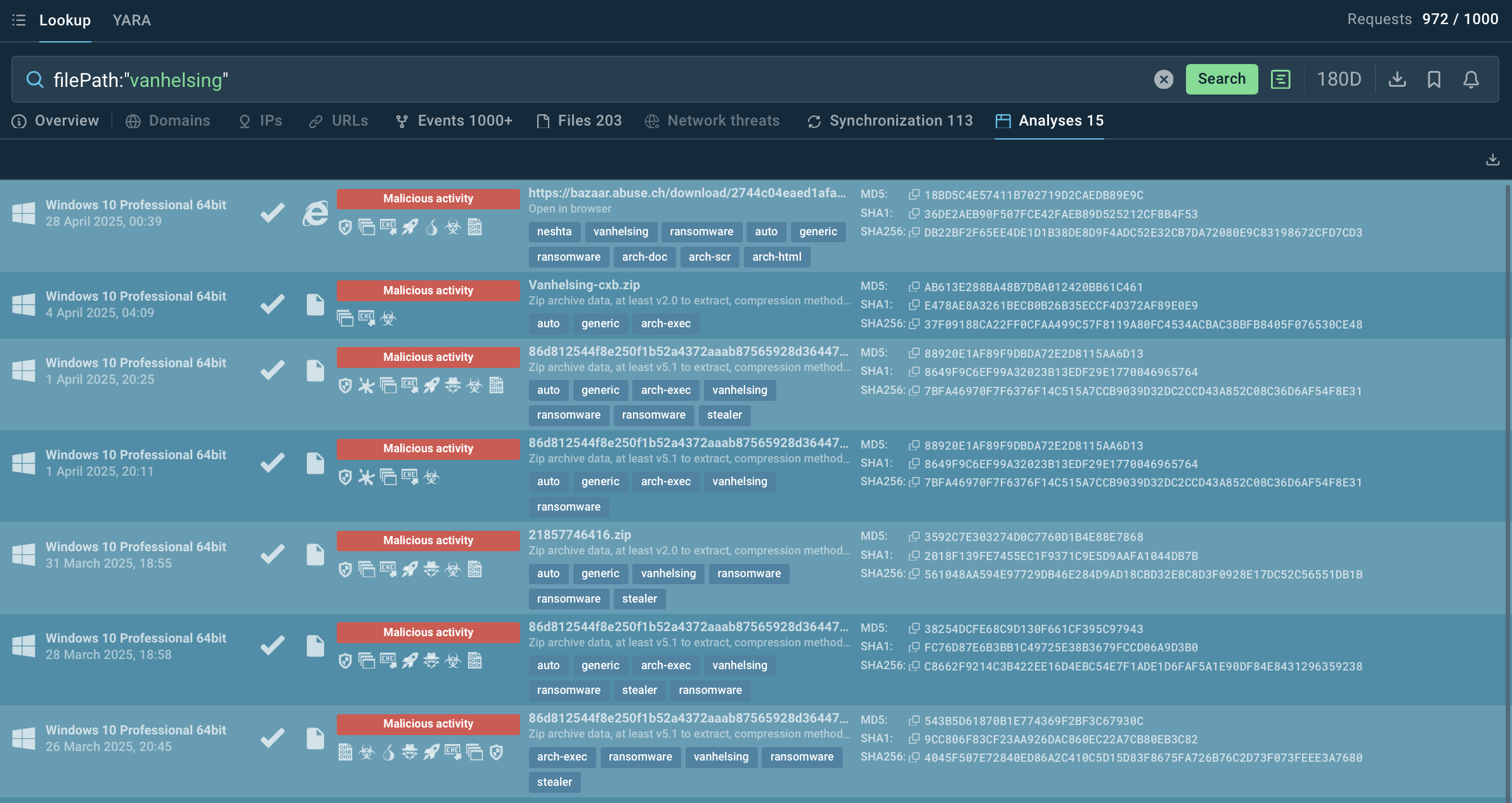 Sandbox malware analyses featuring VanHelsing
Sandbox malware analyses featuring VanHelsing
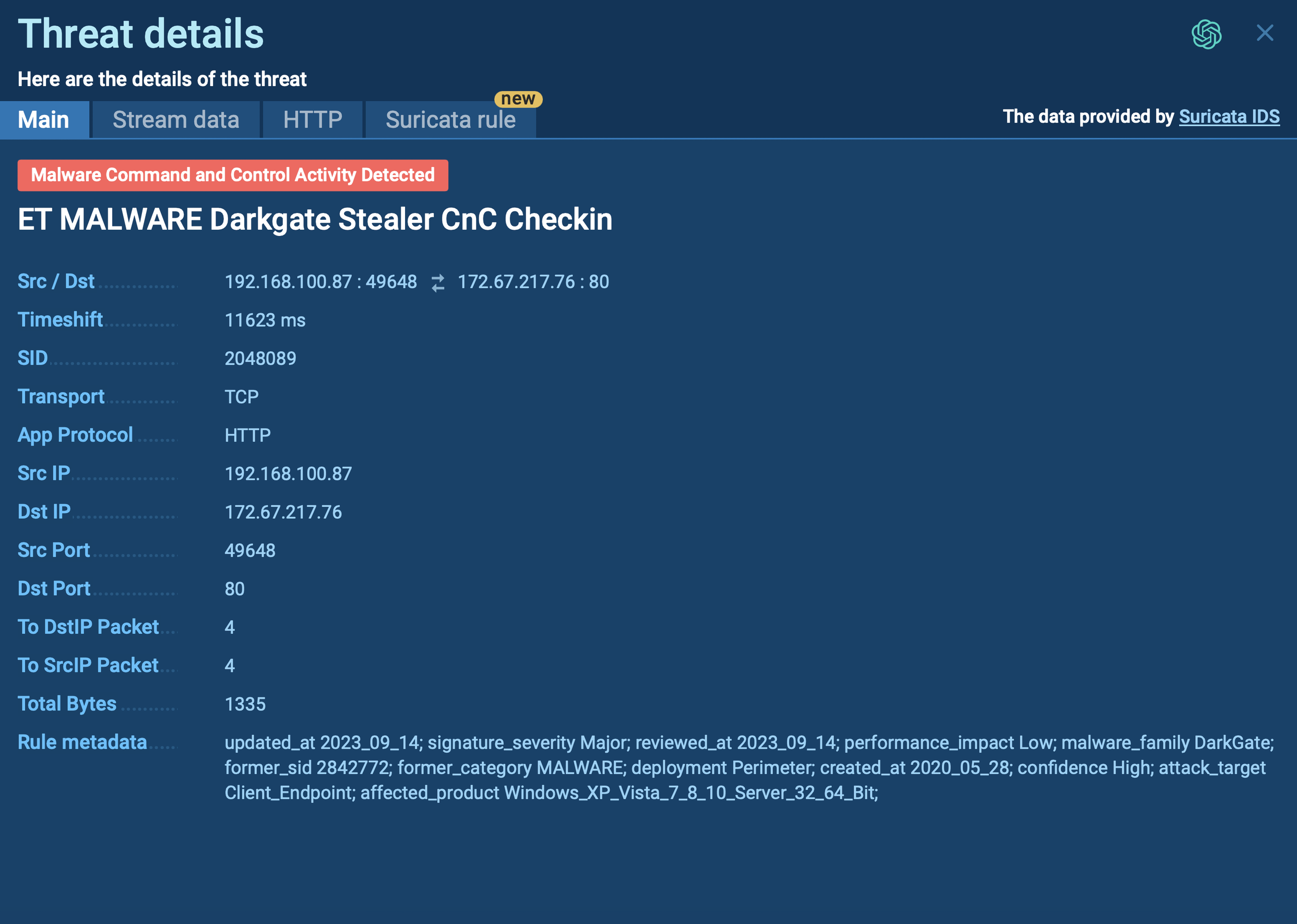
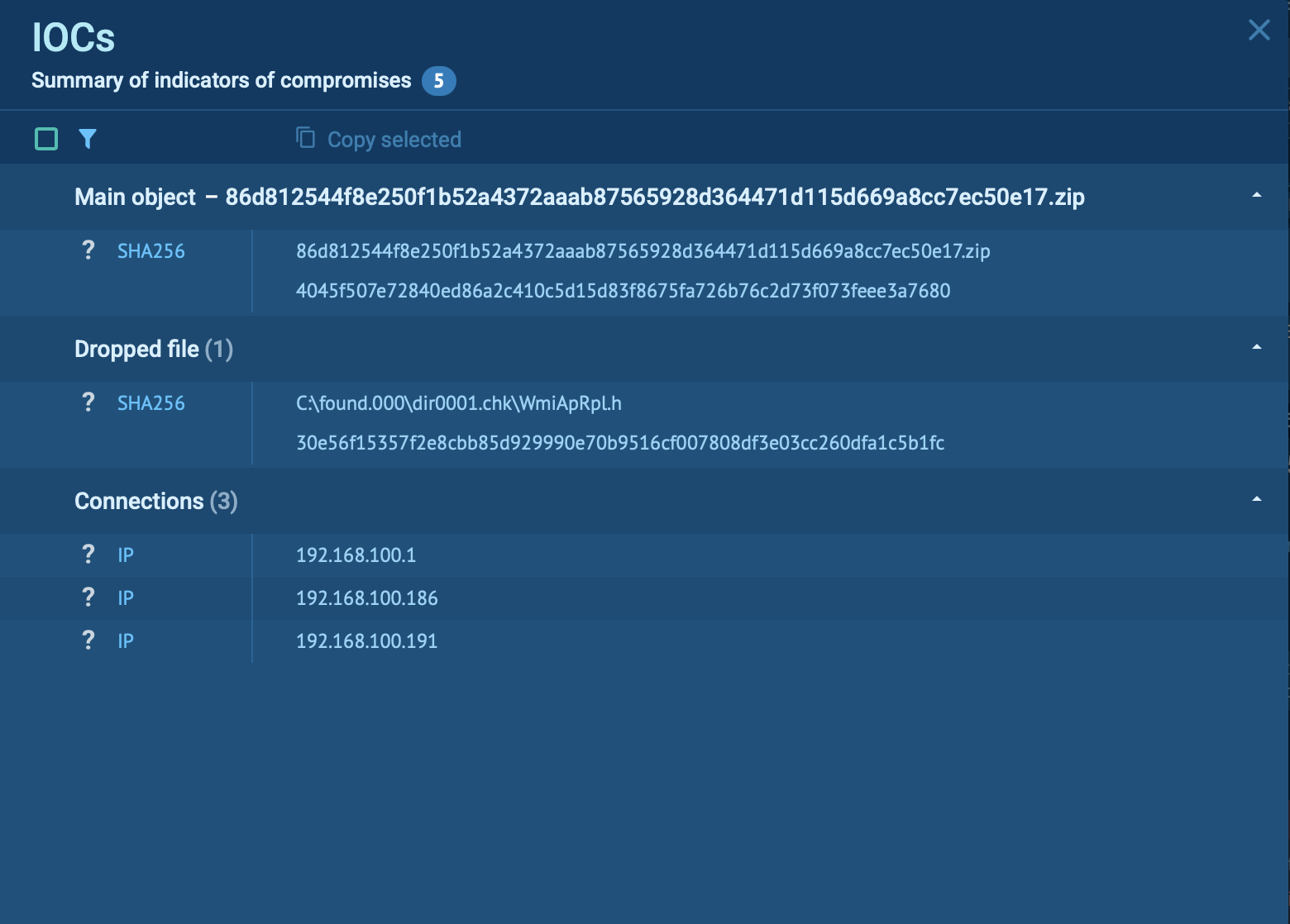 Additional VanHelsing IOCs retrieved in a sandbox analysis session
Additional VanHelsing IOCs retrieved in a sandbox analysis session
VanHelsing’s rapid growth and evolving tactics suggest it will remain a significant threat. Its multi-platform capabilities could lead to attacks on critical infrastructure, while the RaaS model ensures scalability. Organizations must adopt a proactive, intelligence-driven approach to stay ahead of this threat.
By combining robust cybersecurity measures, advanced detection tools, and real-time threat intelligence provided by TI Lookup, businesses can mitigate the risks posed by VanHelsing and similar ransomware strains.