Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


X-FILES Stealer is a sophisticated malware designed to infiltrate systems and steal sensitive information, targeting login credentials for email, social media, and other personal accounts. It captures data and transmits it back to the attacker’s command-and-control server. X-FILES Stealer employs advanced evasion techniques to avoid detection, making it a persistent threat in the cyber landscape.
|
Stealer
Type
:
|
Unknown
Origin
:
|
|
15 March, 2021
First seen
:
|
27 February, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
15 March, 2021
First seen
:
|
27 February, 2026
Last seen
:
|

 850
850
 0
0

 505
505
 0
0

 2783
2783
 0
0
X-FILES is a sophisticated infostealer that primarily targets sensitive data, including login credentials, financial information, and other personal details. Since its initial discovery in March 2021, the malware has undergone various updates that have enhanced its capabilities and delivery methods.
While specific campaigns are not widely publicized, X-FILES Stealer has been involved in various phishing campaigns targeting users and organizations, particularly focusing on individuals who store sensitive information in browsers and email clients.
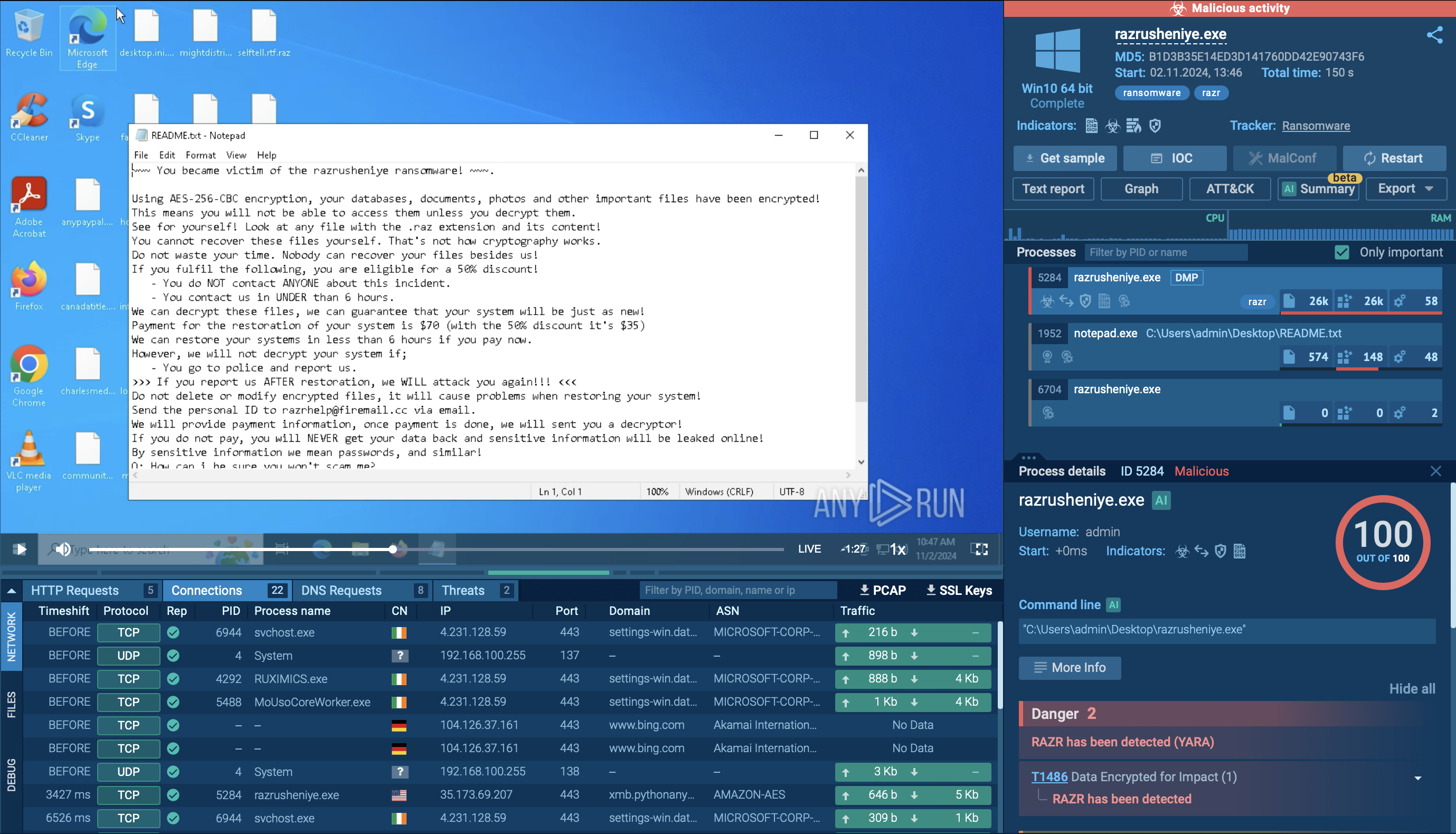
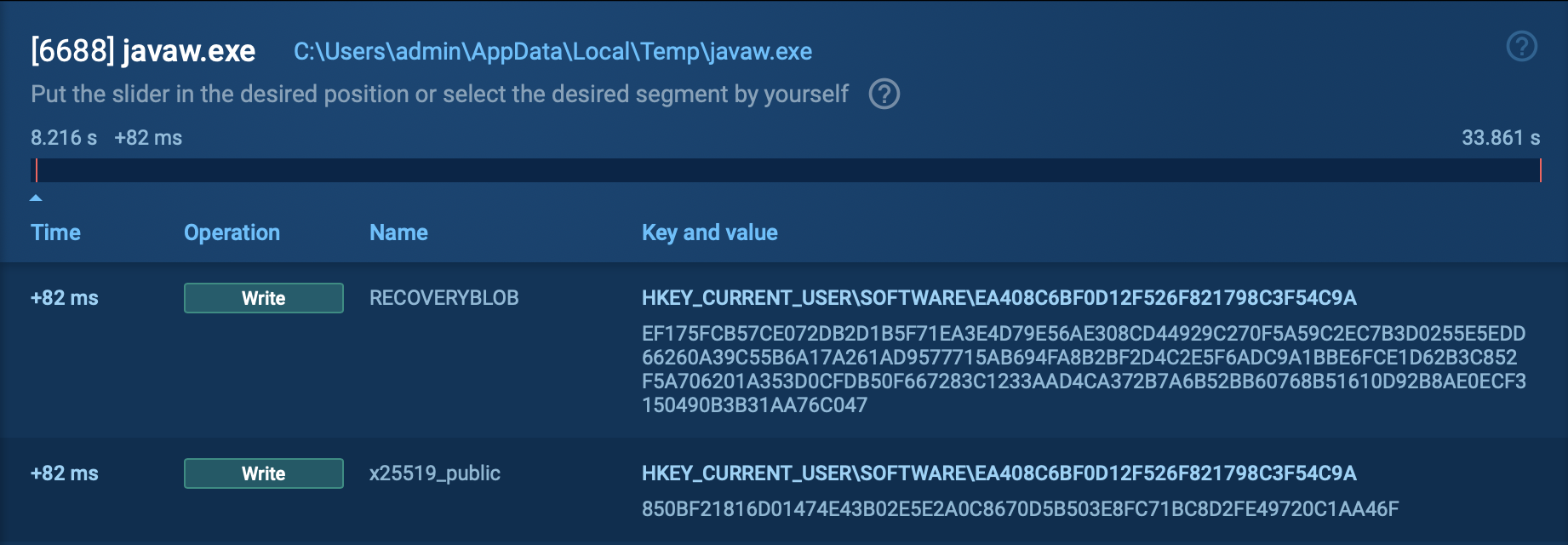
X-FILES Stealer steals login credentials, hijacks accounts, and exfiltrates other sensitive data to its command-and-control (C2) servers. The malware can also use the compromised accounts to spread further infections.
The primary functionalities of X-FILES malware include:
Cybercriminals often use a variety of file types to deliver X-FILES Stealer and other malware through phishing emails. These files include executable files (.exe), archive files like RAR and ZIP, and documents such as PDFs, JavaScript files, and Microsoft Office documents. The attachments are designed to appear legitimate, luring users into opening them and unknowingly initiating the malware infection.
A significant aspect of X-FILES Stealer’s operation is its integration with Telegram. The malware utilizes Telegram as a communication platform to exfiltrate stolen data.
This method is advantageous for attackers because Telegram offers end-to-end encryption, providing a level of anonymity and security that makes it difficult for cybersecurity professionals to trace the data back to its source. The malware sends the exfiltrated data directly to a Telegram bot or channel controlled by the attackers, where it can be accessed remotely and anonymously.
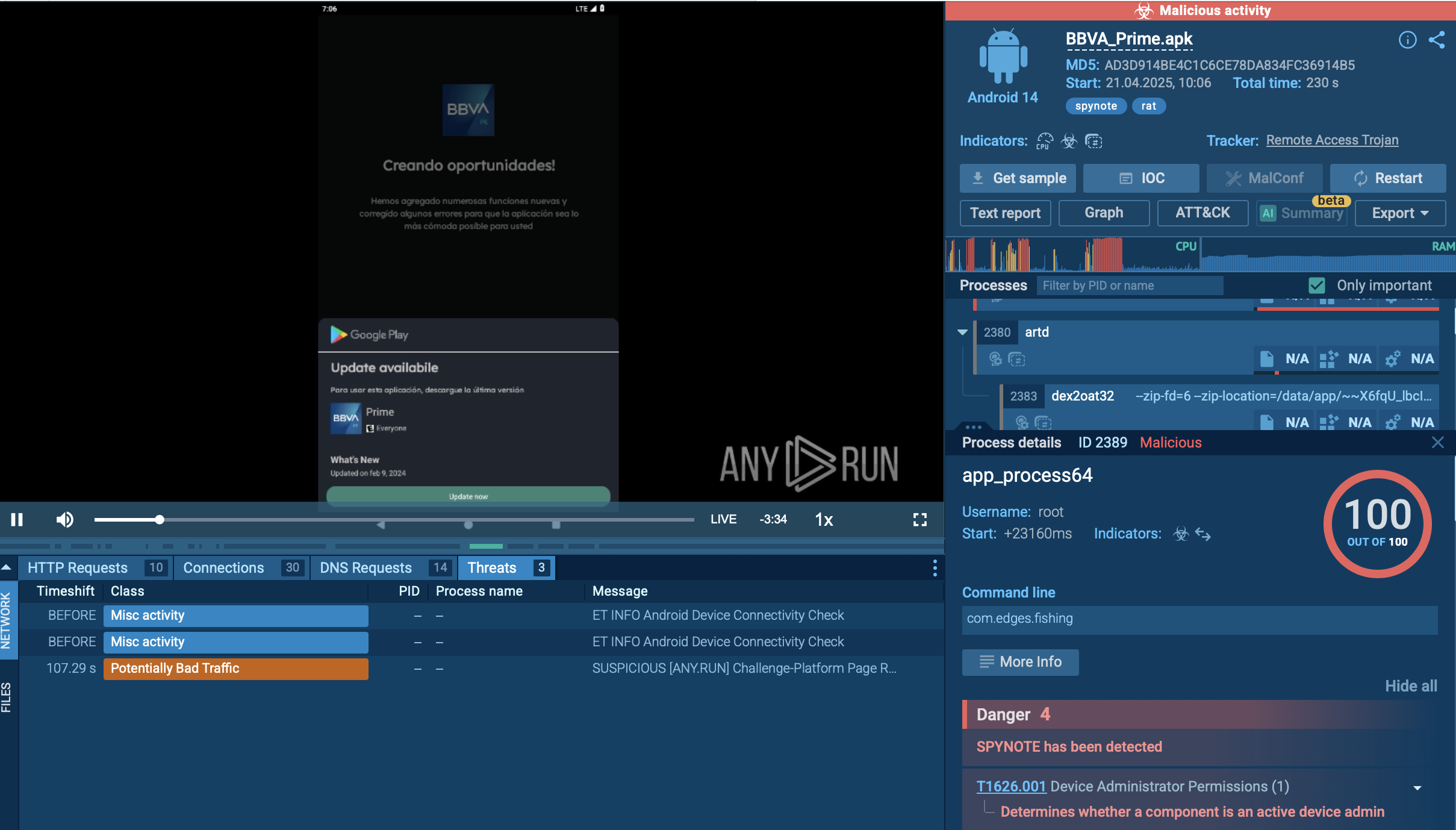
To see how X-FILES stealer operates, let’s upload its sample to the ANY.RUN sandbox.
The infection chain usually begins with phishing emails containing malicious attachments, which are often disguised as legitimate documents, such as Word, Excel, or other Office files. When users open these documents, they may unknowingly execute embedded scripts that trigger the malware's payload.
One of the recent variants of X-FILES uses the Follina vulnerability (CVE-2022-30190), which allows attackers to execute PowerShell commands simply by opening a Word document. This document contains an OLE object that references an external HTML file, which subsequently executes JavaScript to download the malware payload.
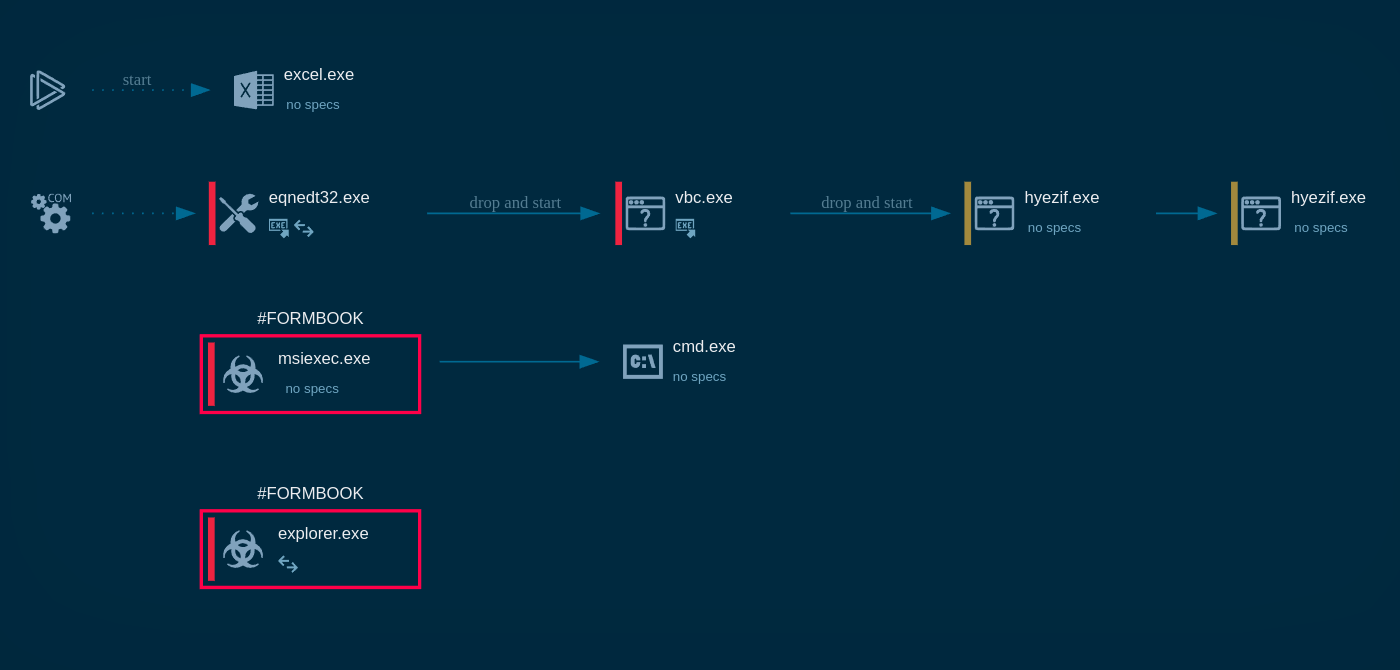
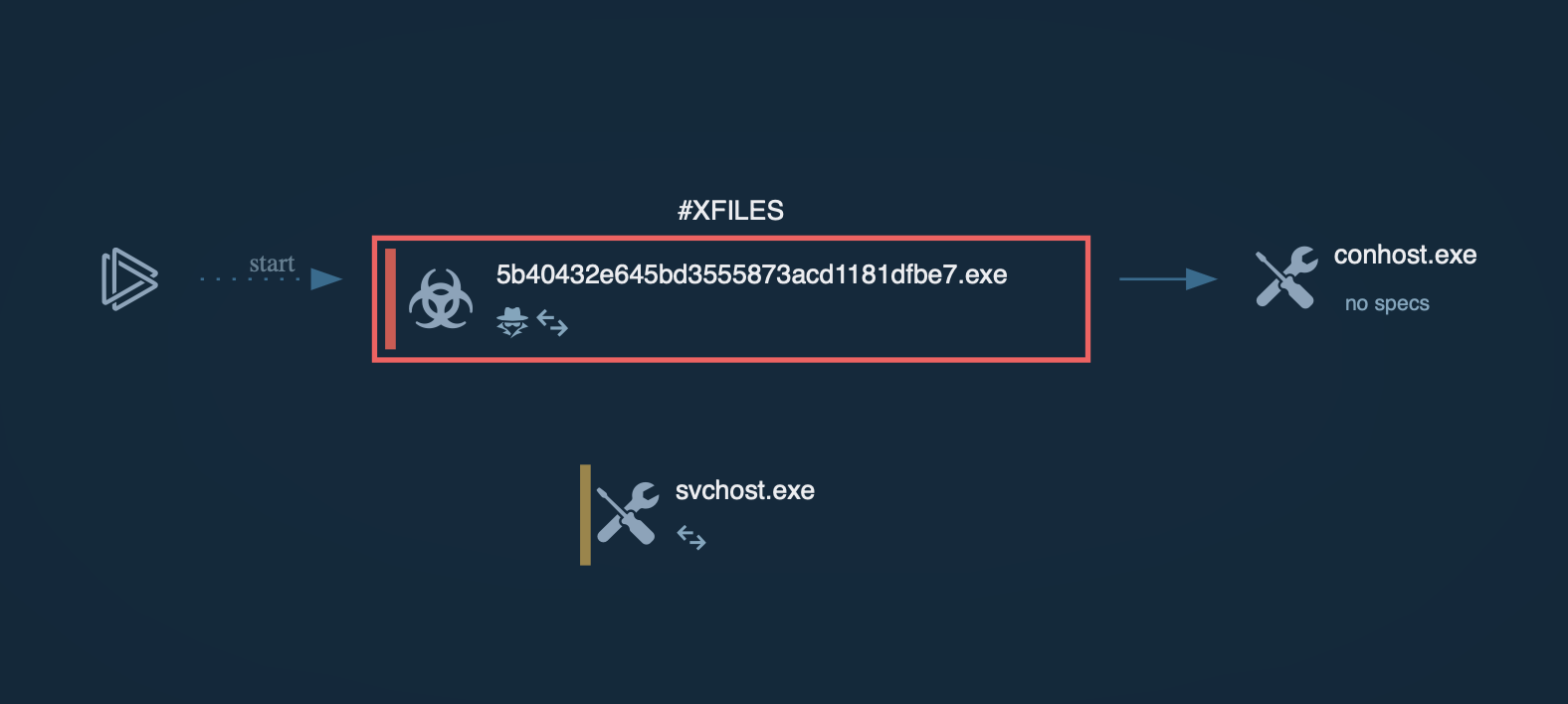 X-FILES Stealer process graph shown in ANY.RUN sandbox
X-FILES Stealer process graph shown in ANY.RUN sandbox
Once the document is opened, it retrieves a base64-encoded string containing PowerShell commands. These commands establish persistence on the infected machine by placing the malware in the Windows startup directory and executing it.
The main payload includes encrypted shellcode, which is decrypted and executed in memory. This approach enables the malware to run without leaving significant traces on the disk, making it more difficult to detect.
The stolen data is typically stored in newly created directories on the infected machine and is exfiltrated using secure channels, often via Telegram, providing attackers with a degree of anonymity.
X-FILES Stealer is distributed through a variety of methods, each designed to exploit common vulnerabilities and user behaviors:
X-FILES Stealer’s focus on hijacking accounts and exfiltrating sensitive data highlights the need for strong security measures. Protecting against X-FILES Stealer requires a combination of security practices, including proactive analysis of suspicious emails, files, or links using a malware sandbox.
ANY.RUN offers a powerful solution for this, allowing anyone to analyze and understand the behavior of threats like X-FILES Stealer in a controlled environment. By using ANY.RUN, you can proactively identify and respond to these threats before they can compromise your data.
Sign up for a free ANY.RUN account to analyze malware and phishing without limits!