Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


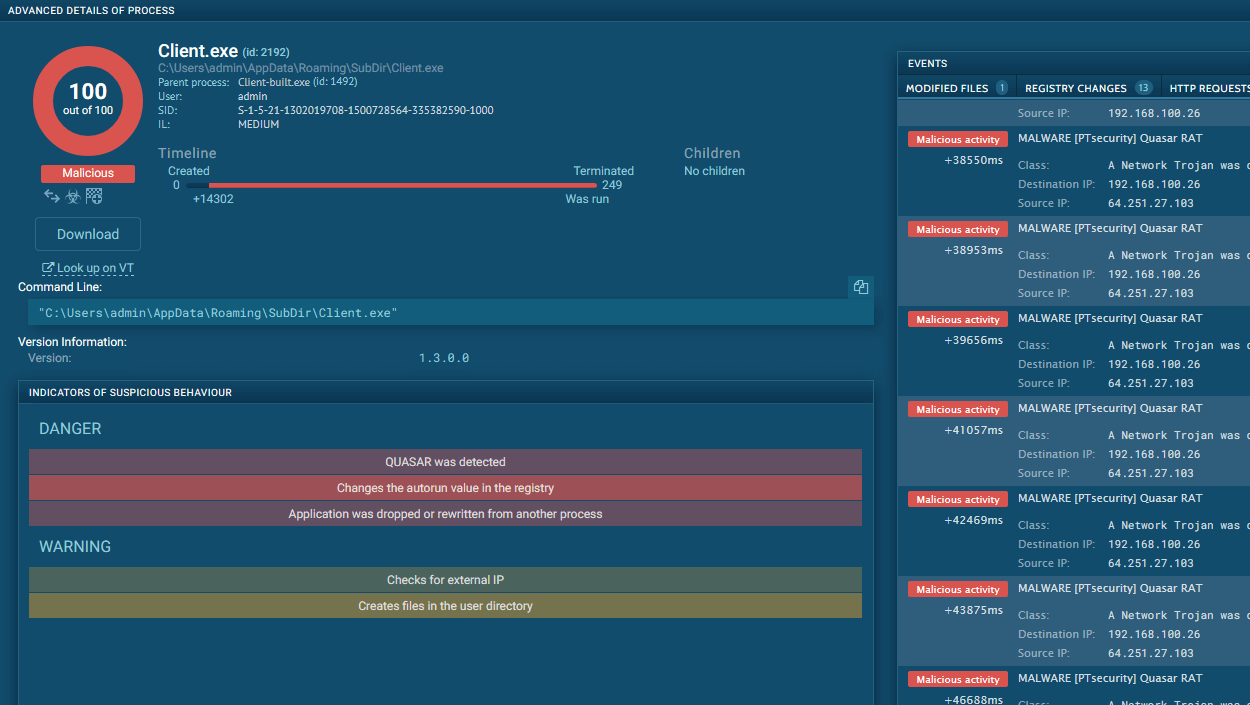
Zloader is a banking trojan that uses webinjects and VNC clients to still banking credentials. This Trojan is based on leaked code from 2011, but despite its age, Zloader’s popularity has been only increasing through early 2020, when it relied on COVID-19 themed attacks.
|
Banking trojan
Type
:
|
Unknown
Origin
:
|
|
1 May, 2016
First seen
:
|
27 February, 2026
Last seen
:
|
|
Banking trojan
Type
:
|
Unknown
Origin
:
|
|
1 May, 2016
First seen
:
|
27 February, 2026
Last seen
:
|

 793
793
 0
0

 482
482
 0
0

 2730
2730
 0
0
Zloader, also known as Terdot and Zbot is a banking trojan. It uses web injects to steal passwords and auth codes of its victims. The trojan was first spotted in 2016 but it has seen a sudden surge of activity in the winter of 2019, appearing in over 100 email campaigns.
Zloader is constructed using the leaked code of the well-known ZeuS malware. ZeuS code was made public in 2011 and became a base for various malware samples. The fact that its variants are still being used goes to show how effective the original malware was.
Researchers first observed Zloader, also known at the time as DELoader, in 2016, when it started attacking Canadian banking organizations. The malware’s name highlights two facts: the letter “Z” shows that it is based on the Zeus Banking Trojan and the word “loader” highlights the malware’s unique design. Zloader makes its way into the machines of the victims using a loader that installs the final payload.
Zloader became quite popular and served as the main tool for several hackers, with TA511 also known as Hancitor being the most acknowledged. After working with Zloader for almost 2 years, Hancitor made a jump to Panda Banker. Others soon followed suit and Zloader became abandoned until 2019, when researchers detected a sudden surge of attacks.
Possibly, attackers pursued the opportunity presented with the confusion that surrounds the COVID crisis, launching a new wave of campaigns in December 2019, with the number of sightings only increasing by March 2020.
Although, previously Zloader focused on finding victims in Canada, starting with 2020 it expanded the geography of operations. The newer campaigns attack financial institutions all over the world, including the US, Australia, and Europe.
The malware uses a technique called web injects to trick victims into revealing their authentication codes. Zloader replaces the banking website of the victim with an identical copy fetched from a custom file so that unsuspecting users give away credentials thinking that they are logging into their bank. In reality, the sensitive information, including auth codes, is sent to the C&C controlled by the attackers.
Additionally, Zloader can fetch information from browsers, accessing cookies and passwords — a standard functionality for banking trojans.
Interestingly, the 2019 version of Zloader is less advanced than its predecessor, seen in 2016. Researchers think that it might be a revision of an older iteration of the malware that lacked some of the sophisticated malicious techniques.
Among the missing features are code obfuscation and string encryption — those are both techniques threat actors use to complicated static analysis of malware by making the code unreadable.
However, that does not mean that Zloader should be taken lightly. It's still top-level malware and it is highly dangerous.
For example, if attackers manage to get a hold of the credentials, they use a smart technique to log into the account without raising red flags with the bank. The threat actors log in with a virtual network computing client, so all the bank sees is another session from the normal victim’s machine. This way, not only can attackers withdraw money without raising any alarms but proving that the transaction fraudulence is also difficult.
On top of that, the malware still uses some anti-evasion techniques like Command & Control blacklisting and Windows API function hashing, making the analysis more complicated. Another worrying sign is the constant maintenance of Zloader. No less than 18 versions have been seen circulating in the wild from January to March 2020. The malware is being constantly improved.
We can watch the complete execution process of Zloader in a video recorded in the ANY.RUN interactive malware hunting service. Moreover, check out other malware analyses such as FlawedAmmyy.

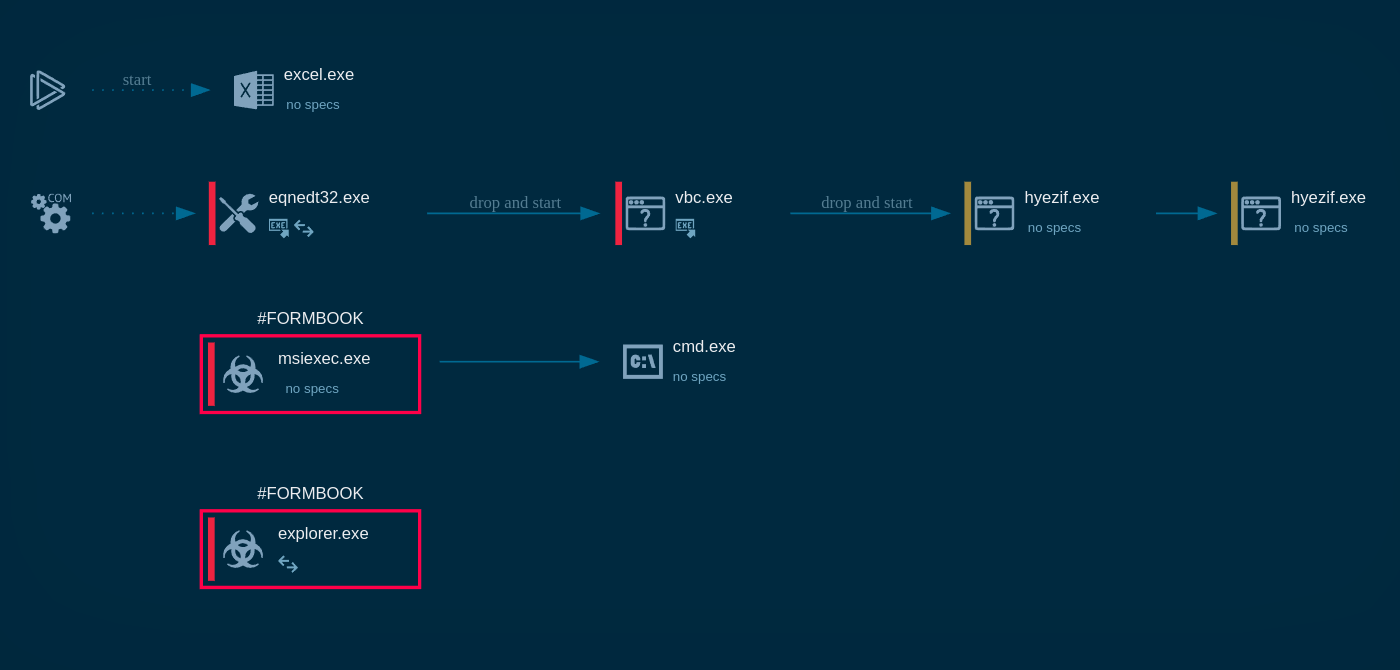
Figure 1: Shows the process graph, automatically created in ANY.RUN
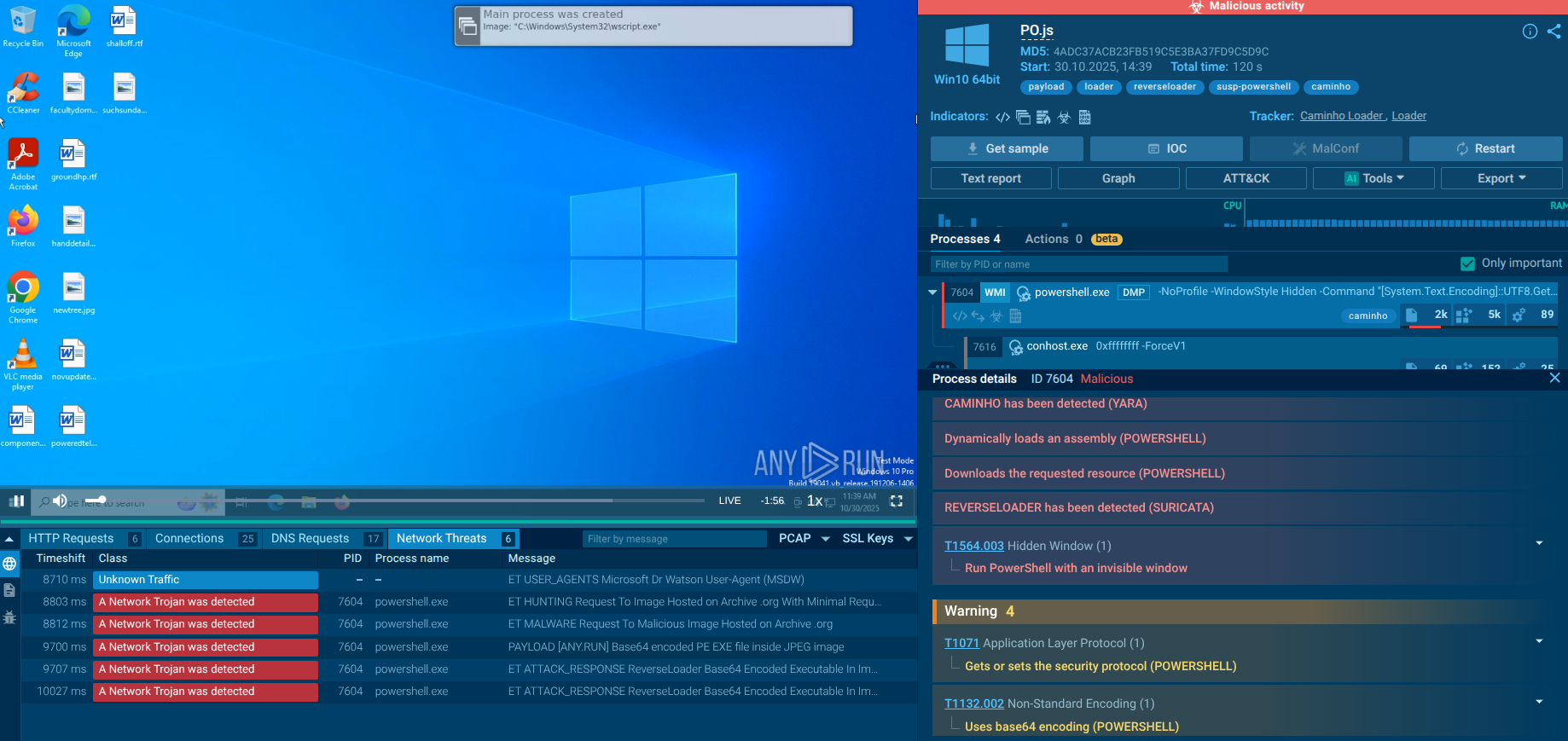
Zloader usually makes its way into systems as an executable or as a script file. When entering as a script file, it runs and compiles into the library by the wscript process. As an executable file, the malware makes an injection into the msiexec.exe process. After that Zloader tries to connect to Command & Control server over HTTPS to download additional modules.
Zloader is distributed to victims with malspam. Emails are crafted to look like government notices or financial support offered due to the COVID-19 epidemic. Attached to emails are malicious files, normally with Microsoft Office file extensions, but PDF files were also observed.
When opened, the files ask the victim to enable macros. If users compile, the macros download a loader that establishes a connection with the command and control server and installs the final payload — Zloader.
Since Zloader creates registry keys with pseudo-random names under HKEY_CURRENT_USER\Software\Microsoft and directories with pseudo-random names inside the %APPDATA% directory. This activity can help analysts detect this malware family. To take a look at the registry changes and created directories, just click on the msiexec process and then click on the “More info” button.
Despite being based on code that was leaked no less than 9 years ago, Zloader still poses a massive threat to cybersecurity.
From late 2019, this banking trojan targets financial institutions all around the world with COVID-19 themed attacks. It appeared in over 100 email campaigns after being inactive for nearly 2 years and now wreaks havoc on the banking world, using web injects and VNC sessions to steal credentials.
Thankfully, using ANY.RUN, researchers can analyze Zloader in a secure online environment and take advantage of our interactive sandbox. With our service, malware hunters can get results on the fly, while still being in control of all simulation variables, saving massive time on dynamic analysis. Studying threats like Zloader is a sure way to develop a sound cybersecurity strategy or prepare an action plan should your organization come under attack.