Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


REvil, also called Sodinokibi, is a notorious ransomware strain known for its use of sophisticated encryption techniques, high-profile targeted attacks, and connections to GandCrab.
|
Ransomware
Type
:
|
ex-USSR
Origin
:
|
|
1 April, 2019
First seen
:
|
24 February, 2026
Last seen
:
|
|
Type
:
|
ex-USSR
Origin
:
|
|
1 April, 2019
First seen
:
|
24 February, 2026
Last seen
:
|

 736
736
 0
0

 460
460
 0
0

 2688
2688
 0
0
REvil, also known as Sodinokibi, is a ransomware strain that emerged in 2019. This malicious software encrypts the victim's files and demands a ransom payment, typically in the form of cryptocurrency, to restore access to the encrypted data.
Believed to have originated from a cybercriminal group based in a former USSR country, REvil gained notoriety in the ransomware landscape due to its high-profile attacks on businesses, governments, and organizations worldwide.
The group behind REvil operates on a ransomware-as-a-service (RaaS) model, in which they develop the malware and manage the infrastructure, while affiliates responsible for distributing the ransomware receive a percentage of the ransom payments.
This ransomware is notorious for its bold attacks, which include, but are not limited to:
Numerous incidents caused by REvil led to significant supply chain disruptions, placing the gang in the crosshairs of international law enforcement. The infamous operation was eventually shut down due to an international law enforcement operation called GoldDust. The gang was reportedly dismantled in January 2022. However, some researchers believe that the malware family may resurface under a different name.
REvil is believed to be a successor to another notorious ransomware—GandCrab. Connections between REvil and GandCrab can be drawn from similarities in their operations and technical aspects. GandCrab, a ransomware strain that operated from January 2018 until its developers claimed to have "retired" in June 2019, boasted millions of dollars in profits. Shortly after GandCrab's supposed retirement, REvil emerged and rapidly gained prominence in the ransomware landscape.
Several reasons lead researchers to believe that the two crews are closely connected or even are the same crew:
Code and functionality similarities exist between GandCrab and REvil. Both strains employ similar methods to evade detection and achieve persistence in the infected system. Additionally, the ransom notes left by REvil bear a resemblance to those left by GandCrab in terms of language and structure.
Both GandCrab and REvil operated on a RaaS model and utilized similar affiliate programs. In these programs, the ransomware developers provide the infrastructure and receive a share of the ransom payments, while affiliates are responsible for distributing the malware.
REvil's code and ransom note compositions also share similarities with another active ransomware gang—DarkSide. This may suggest that the latter is an offshoot or a partner of the former, especially considering that REvil's code isn't publicly available.
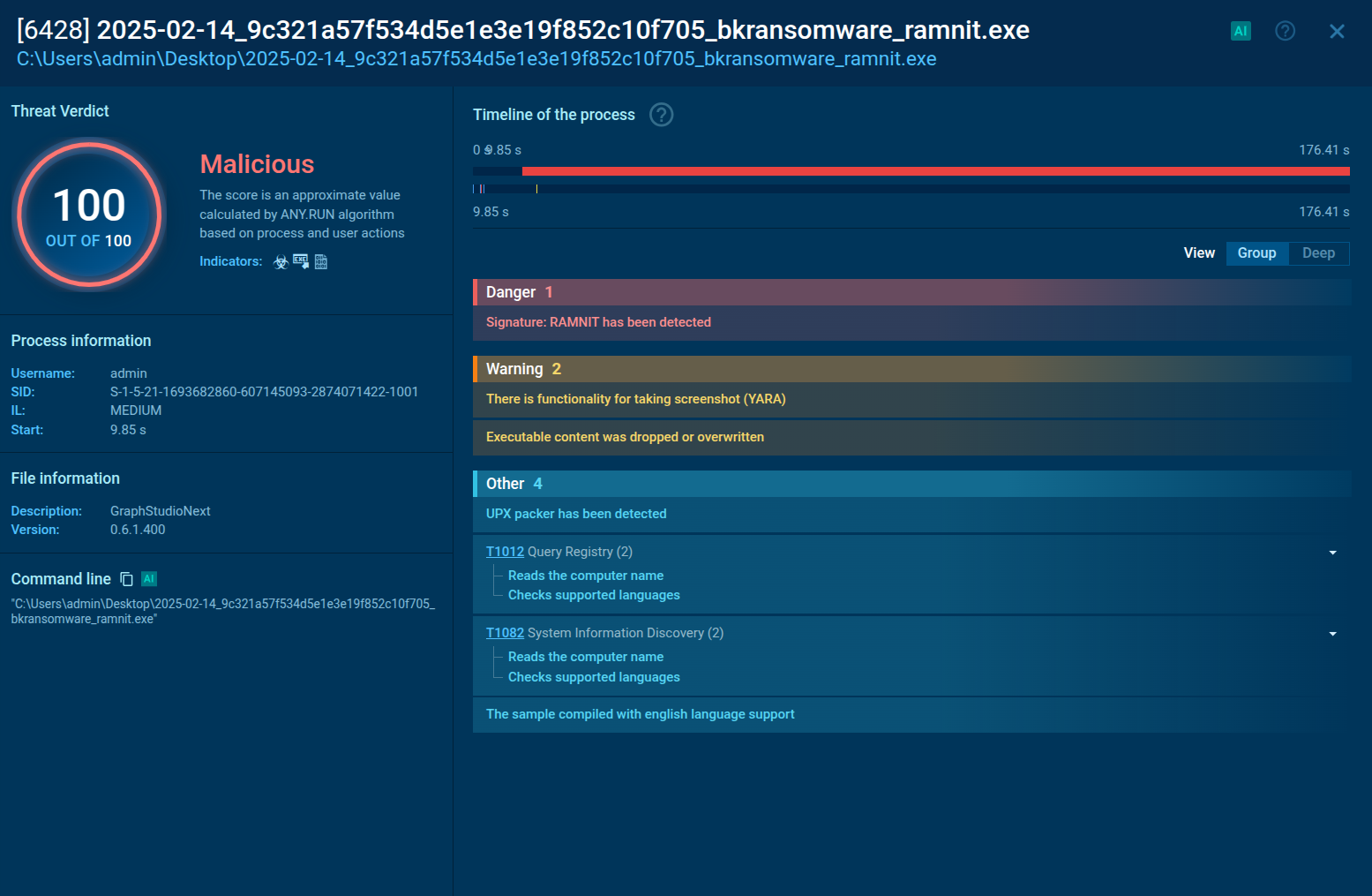
A recent variant of REvil employs a Safeboot routine to bypass security solutions that do not operate in Safemode. The ransomware also uses DLL sideloading to evade detection by running under the context of legitimate files or processes. In the Kaseya supply chain compromise, PowerShell commands were observed disabling Windows Defender.
SharpSploit, an attack framework with credential access capabilities using the Mimikatz module, has been observed in recent REvil campaigns. The gathered information is sent back to the threat actors using various methods, including the installation of FileZilla or third-party sync tools like MegaSync, FreeFileSync, and Rclone (64-bit).
REvil communicates with its command and control (C&C) infrastructure by generating pseudorandom URLs based on a fixed format. The URLs follow the pattern "https://{Domain}/{String 1}/{String 2}/{random characters}.{String 3}", with domain and strings extracted from the configuration file.
The encryption process has remained largely consistent since REvil's inception. The ransomware attempts to escalate privileges using exploits or token impersonation and creates a mutex. It then decrypts its JSON configuration file using the RC4 function to determine the subsequent routines. The configuration file contains various parameters, including public encryption keys, campaign IDs, whitelisted directories, and domains to contact after encryption.
Interestingly, REvil uses Elliptic Curve Diffie-Hellman (ECDH) is an asymmetric key exchange protocol that allows two parties to securely exchange cryptographic keys over a public channel. REvil uses ECDH to protect the Salsa20 or AES keys that were used to encrypt individual files, making its encryption algorithm practically uncrackable.
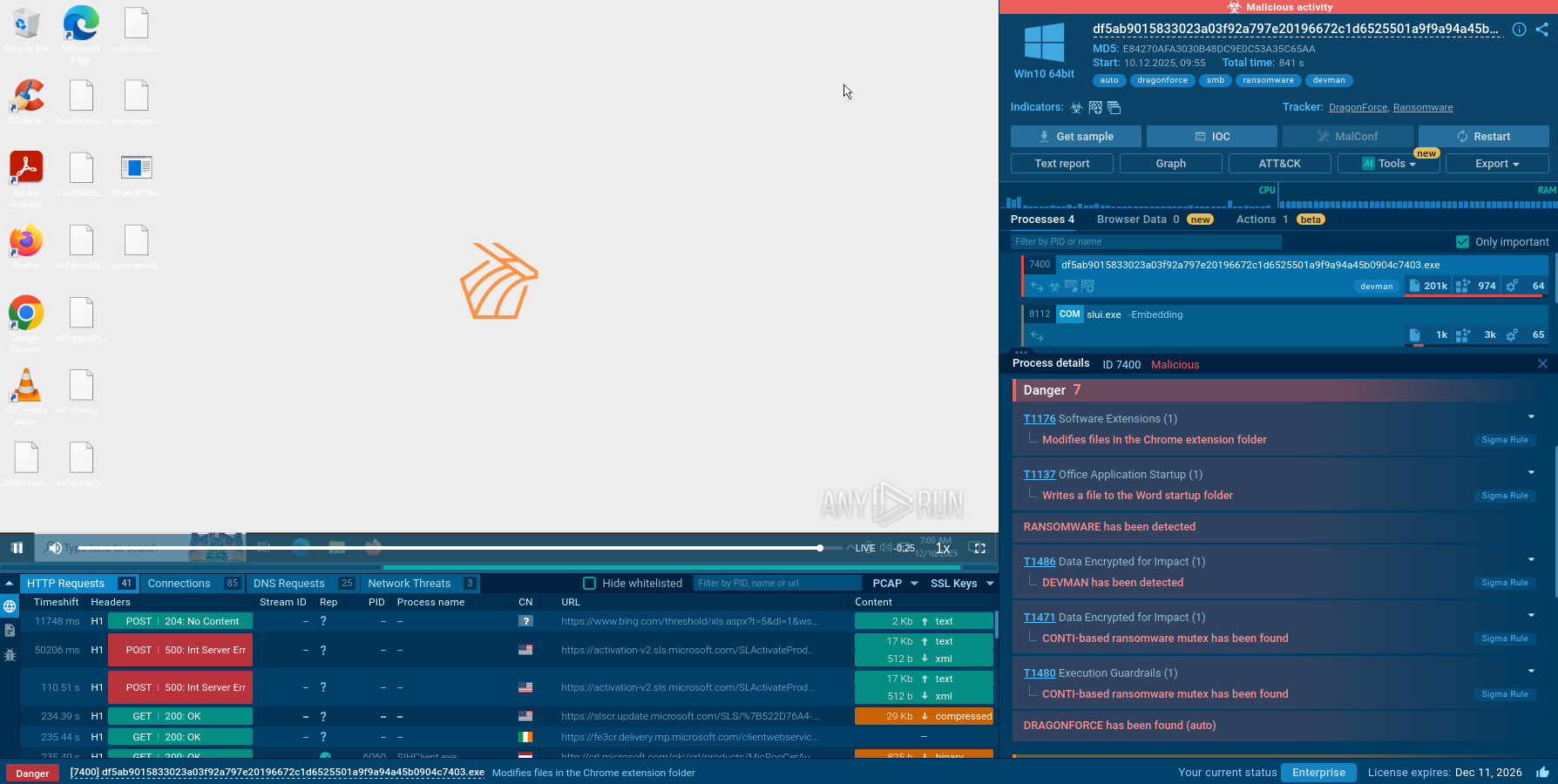
ANY.RUN's cloud interactive sandbox allows you to effortlessly analyze REvil samples. Our platform automatically gathers and presents the execution data in easy-to-read formats, collecting artifacts and IOCs in real time.
ANY.RUN provides the ability to watch the REvil in action and perform the ransomware analysis via an interactive virtual sandbox simulation.
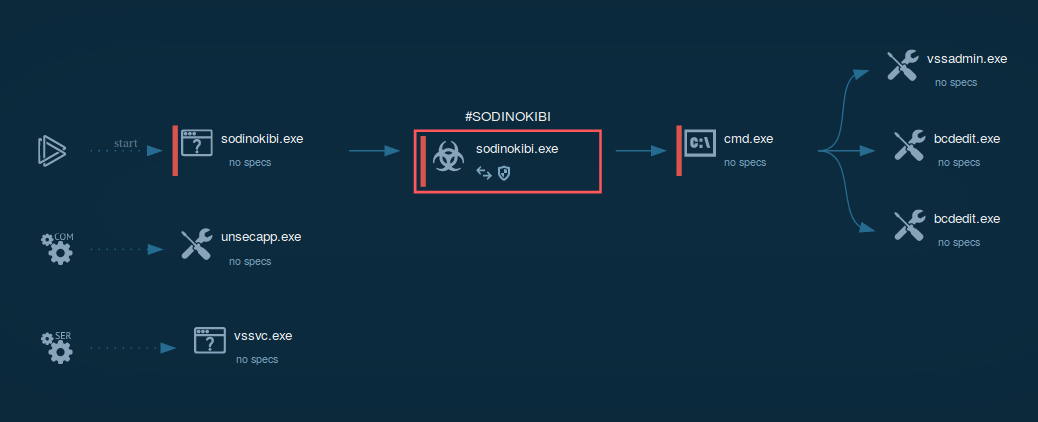 Figure 1: illustrates the processes launched by REvil during its life cycle.
Figure 1: illustrates the processes launched by REvil during its life cycle.
Through time, the "team" behind Revil\Sodinokibi changed the ransomware in a way to avoid detection. The earliest versions of it were easily detected by checking of creation of particular keys in the registry. After they got rid of this, there were still detection based on the similarity of ransom notes dropped inside the infected system. From the beginning, detection by Yara rules was possible.
It was known that crooks behind REvil offered the decryption of three images for free. When the malware was active, you could use the interactivity of ANY.RUN to take additional steps in the analysis:
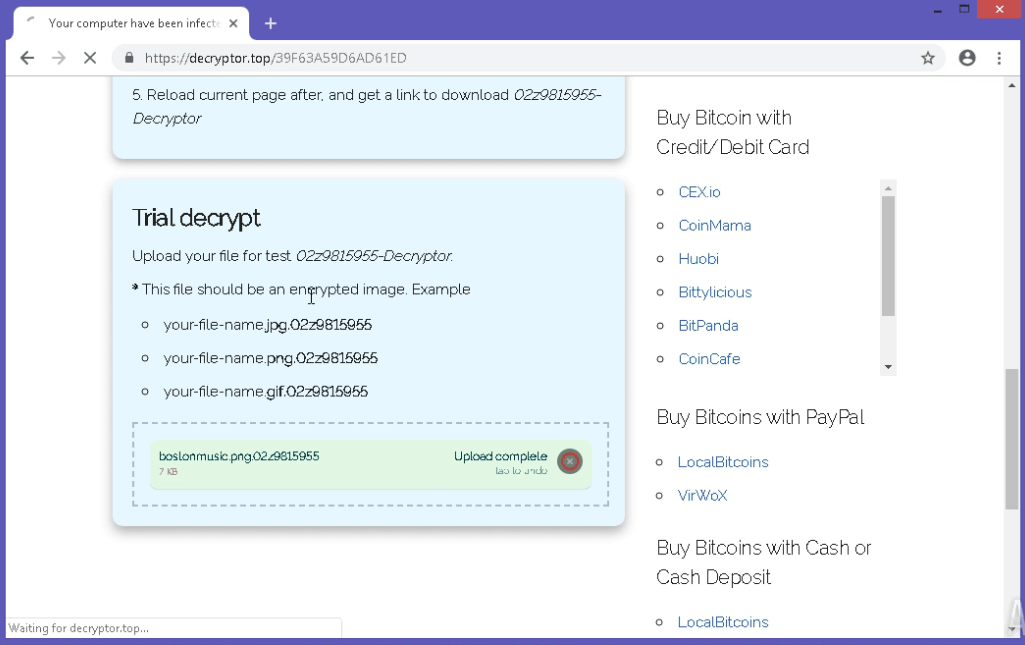 Figure 3: REvil payment website
Figure 3: REvil payment website
REvil won't run malicious activity on systems where UI and keyboard languages are set to a specific value, such as Russian, Ukrainian, and 18 others. Although Sodinokibi is a "qualitative" type of malware, its execution, and system infection process, in general, is quite straightforward and similar to other ransomware - it decrypts files, erases shadow copies, and places ransom notes across the file system.
The process tree also doesn't look very exciting because all main activities are provided by a single executable. For all infected files, the ransomware changes extensions to generated. The added extension is the same as an ID which is unique and made by combining the hash of the value given by CPUID instruction and the volume serial number.
It should be noted that REvil will also try to encrypt files on network shares. After completion of the decryption process, the ransomware sets the background wallpaper to a ransom message.
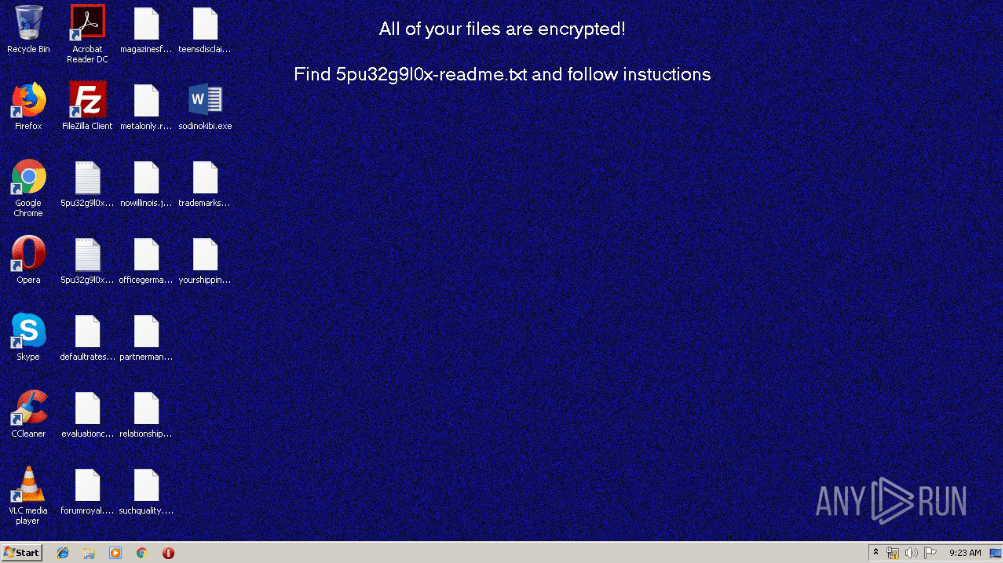 Figure 2: Wallpapers with ransom message set by REvil
Figure 2: Wallpapers with ransom message set by REvil
Interestingly, the authors of Sodinokibi created a high-quality website available at the domain decryptor.top, where victims can use a trial decryptor and have the opportunity to decrypt three images for free. Besides the decryption function, this website provides information such as the countdown (after time runs out, the ransom amount will be set to 5 000 dollars), instructions on how to buy bitcoins, and where to send them as well as information about the decryption process. If decryptor.top is not available, there is a possibility for victims to visit its .onion clone through the Tor web browser.
REvil and its affiliates are known for highly-targeted attacks, and the infiltration vector can be tailored to suit the victim. Over time, this has led to a wide variety of distribution methods employed by this ransomware.
REvil can arrive through spear phishing emails containing an infected Microsoft Office or PDF document. Social engineering techniques are then used to trick the victim into downloading the payload and executing it by running a malicious script or macro. REvil can also be dropped by other malware, such as Qakbot and IcedID.
Another popular distribution method involves exploit kits. The use of the following exploits has been recorded:
Attackers may also attempt to gain access to a target network by brute-forcing Remote Desktop Protocol (RDP) credentials. And in the Kaseya VSA attack, the group exploited a zero-day vulnerability to compromise vulnerable VSA servers and distribute the ransomware to MSPs and their clients.
Following the initial infiltration, REvil likes to move laterally within the network to maximize the impact of the attack. For example, the adversary may attempt to extract user credentials from the infected system by dumping password hashes or using tools like Mimikatz to extract plaintext passwords from memory.
Lateral movement helps REvil to maximize the attack surface and exacerbate damages caused, giving it more leverage to demand a high ransom amount — often in the millions of US dollars.
Although REvil — one of the most high-profile ransomware operations in history — was allegedly squashed in a massive international law enforcement operation, the crew has a history of pulling temporary disappearance acts and is likely to come back again.
This might be the perfect time to study this threat, regroup, and prepare — because if and when REvil comes back, the new name might be different, but much of the code, techniques, and tactics employed will be the same.
Interested in more ransomware analysis like this one? Check out our breakdown of WannaCry ransomware — perhaps the only other malware that beats REvil in notoriety.
Or check out our analysis of IcedID— a malware that is known to drop REvil in some campaigns. By understanding the methods and strategies used by these notorious ransomware strains, you can better prepare your organization for potential future attacks and bolster your cybersecurity defenses.