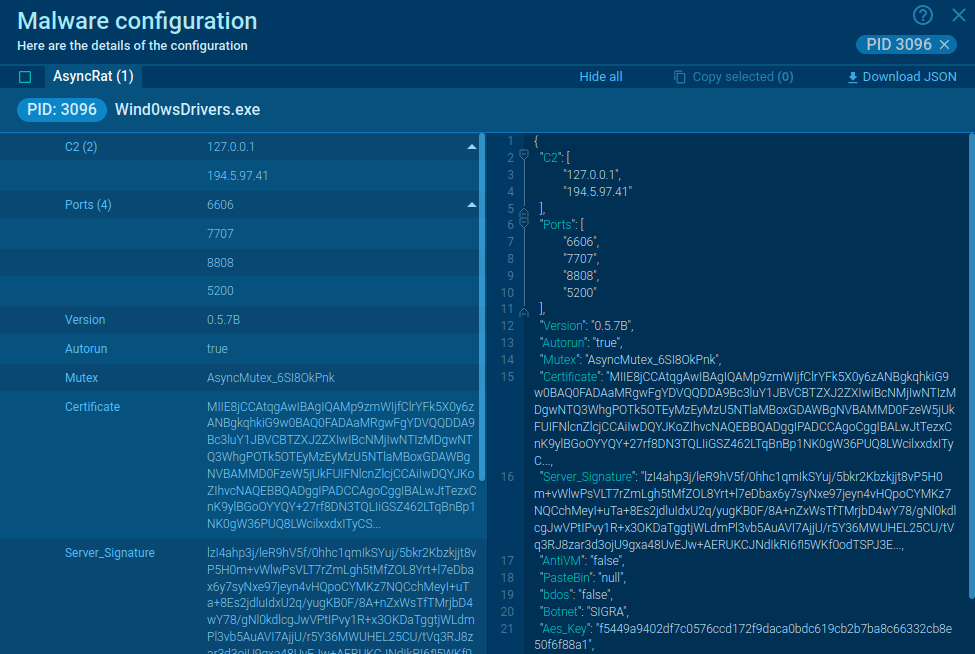
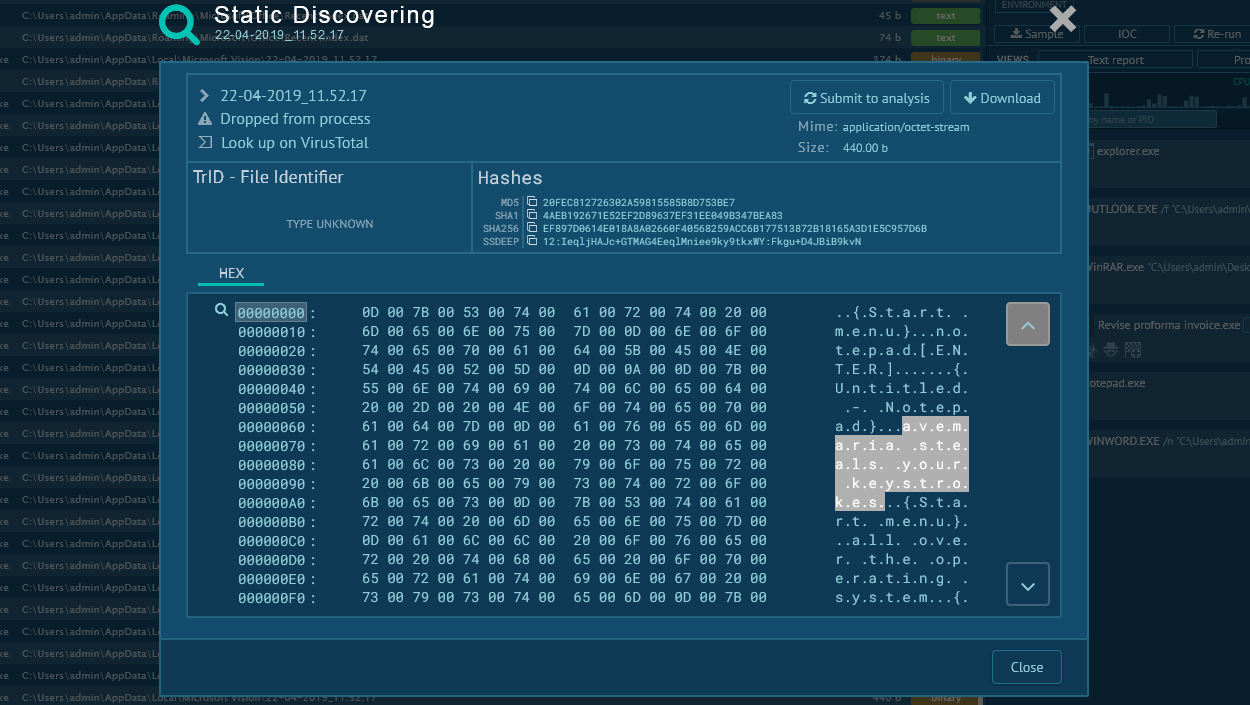
What is RedLine Stealer?
RedLine Stealer or RedLine is malware that can collect users’ confidential information and deliver other malicious programs. The availability and flexibility of the stealer cause financial loss, data leakage, targeting both enterprise and personal devices. Healthcare and manufacturing sectors suffer the most from these attacks.
The malware appeared in March 2020 according to the Proofpoint investigation. Since then RedLine has just gained steam. It was on the rise during the COVID-19 pandemic and is still active. On July 1st, 2021 the malware was found on the legit-looking website that provides privacy tools. However, based on the payload analysis, only malware can be found there.
General description of RedLine malware
RedLine is an infostealer that takes information about users from browsers, systems instant messaging, and file transfer protocol clients. The main target is passwords, credit card information, username, location, autofill data, cookies, software set, and even hardware configuration like keyboard layout, UAC settings, etc. The virus is also capable of stealing cryptocurrency.
The malicious program acts as a typical stealer such as Raccoon or Pony: it uploads and downloads files, executes commands, and reports information about the infected machine. Moreover, attackers make use of RedLine to deliver ransomware, RATs, trojans, and miners.
The infostealer is quite popular as there is no problem finding it. Underground forums, C&C panels offer different options such as malware-as-a-service versions or a subscription. The price varies from $100 to $200.
One cannot tell that RedLine Stealer is a sophisticated malware like ransomware. It has the usual features typical for this family. However, it is .Net malware written in C# and the code quality is high enough to reveal an experienced programmer behind it. Cybercriminals also work hard to update malware, like downloading secondary payloads and advanced filtering features.
RedLine malware analysis
ANY.RUN allows researchers to perform the analysis and watch the RedLine in action in an interactive sandbox simulation
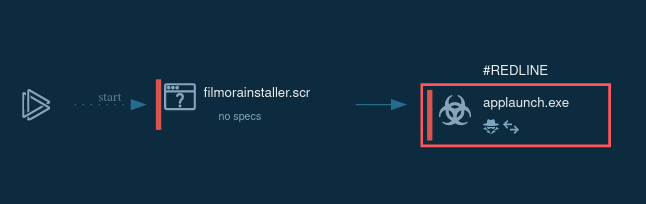
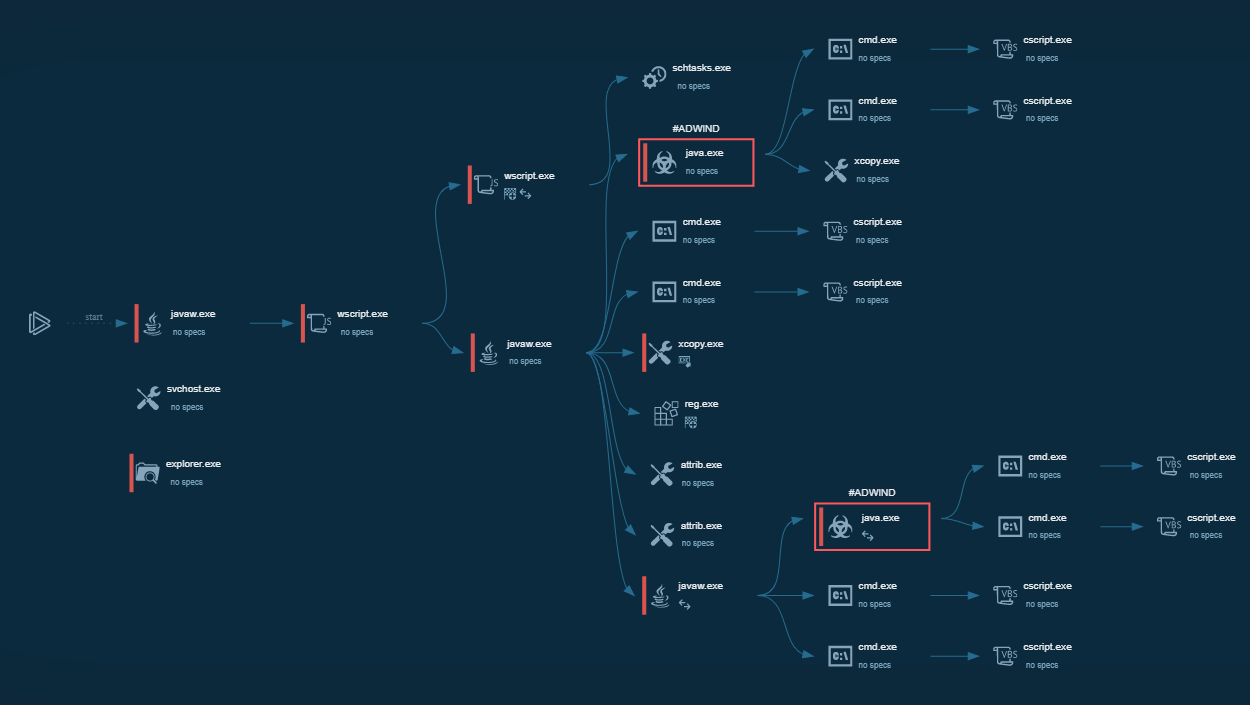
Figure 1: Displays the lifecycle of RedLine in a visual form as a process graph generated by ANY.RUN
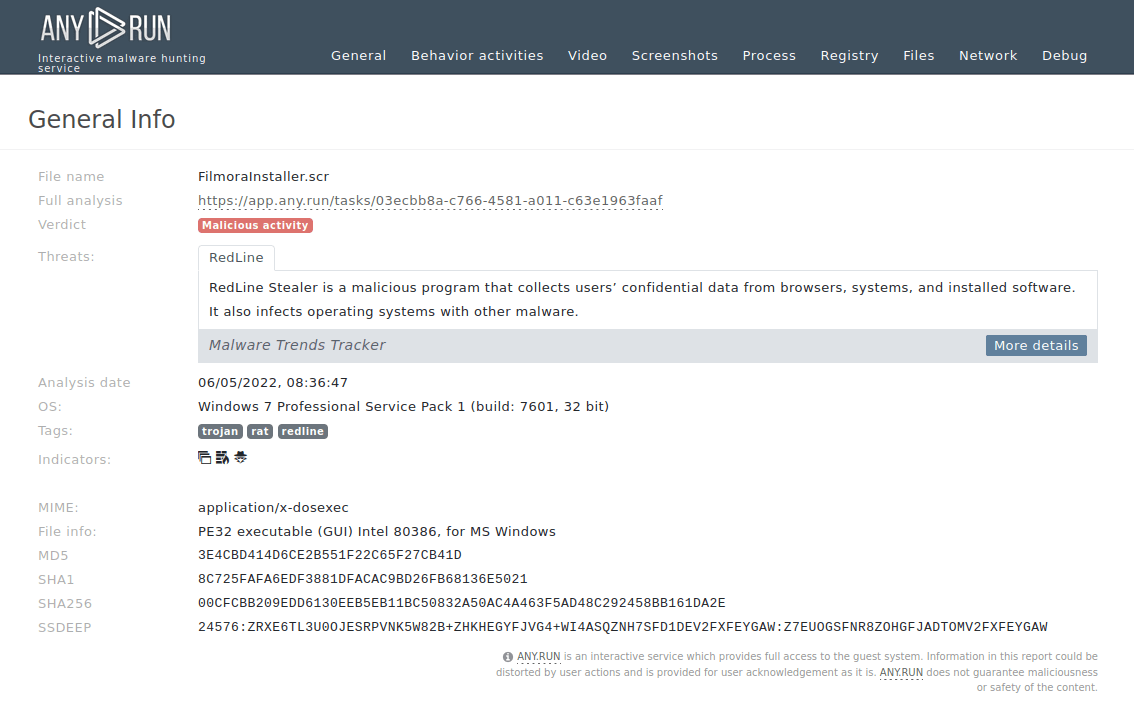
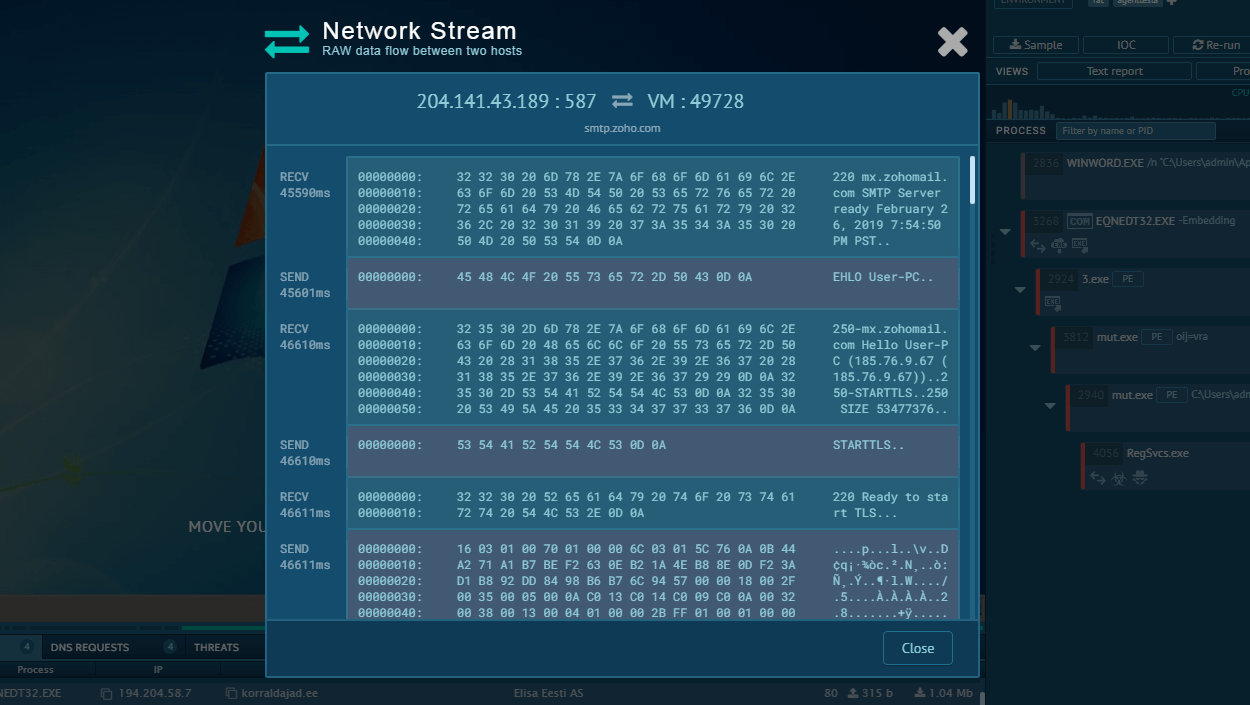
Figure 2: A customizable text report generated by ANY.RUN allows users to take an even deeper look at the malware and helps to share the research results.
RedLine Stealer execution process
Typically the execution process of that stealer is plain and straightforward. Based on the analysis, the main binary launches itself and the parent process stops. It also may be dropped from another binary or be the main binary itself. When a child process is created, the main malicious activity starts – RedLine collects information from the infected system such as passwords and others, and sends it to the Command & Control panel. When all information is collected and sent, the stealer just quits execution. Stolen information is sent in both non-encrypted and base64 encoded formats.
Distribution of RedLine
Attackers are not very creative with the delivery method of the virus. However, as the ransomware story, the method works perfectly – social engineering for different email campaigns including business email compromise, spam, fake updates, ads in Google result in malicious attachments or links. We can notice the big variety of file formats here:
- Office
- RAR and ZIP
- Executable files
- JavaScript
If you open the files in the attachment, RedLine will download other malicious programs.
How to detect RedLine infostealer using ANY.RUN?
At the moment, analysts can quickly recognize the info stealer because it will be tagged after Suricata IDS rules are triggered. Since the malicious program sends the stolen info to its panel just right after the start of the execution, it won't take a lot of time.
Conclusion
The best way to protect your organization or device from RedLine is to be cautious with suspicious files and links that get into your email. Your staff should be aware that even trustworthy sources can lead to infection and password or other credentials’ theft. It won’t take long to check a file in a sandbox such as ANY.RUN. Several minutes will be enough to detect RedLine and you will be good to go. Stay safe.


 0
0