Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


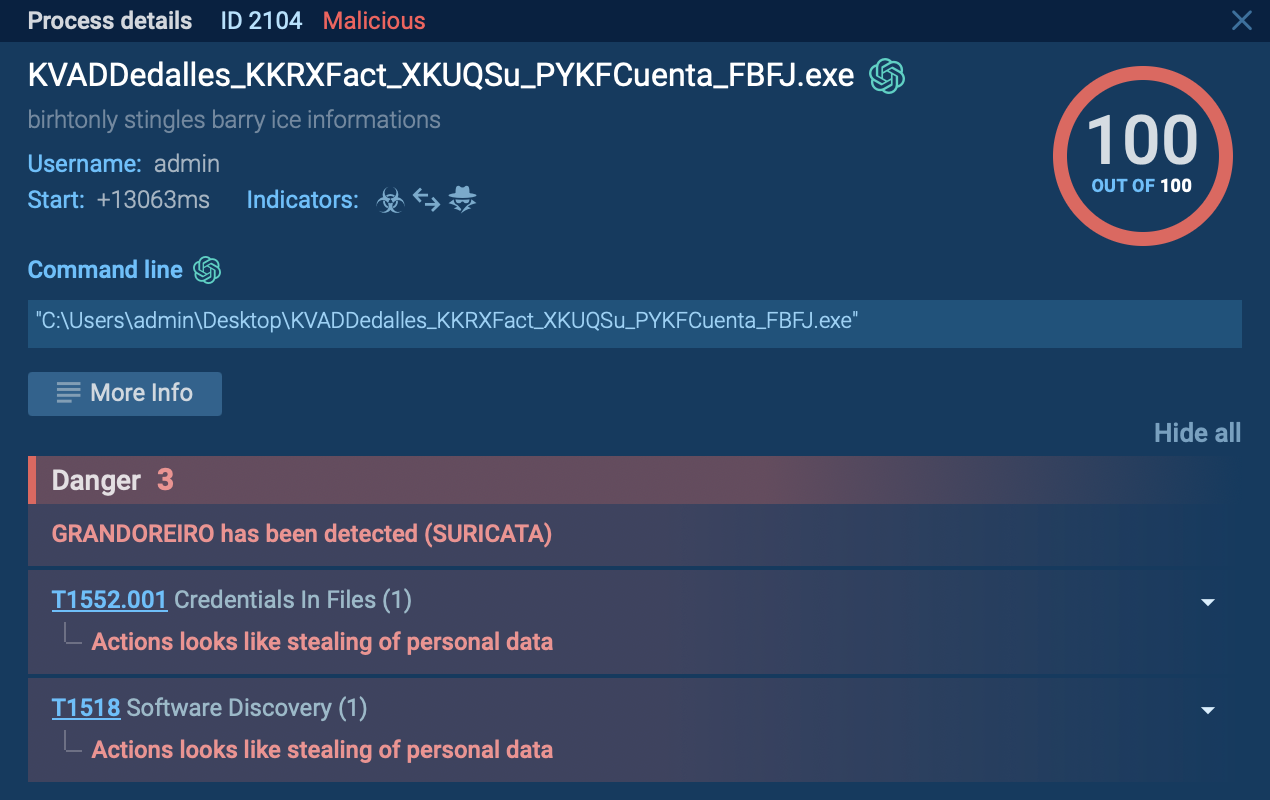
WarZone RAT is a remote access trojan, which is written in C++ and offered as a malware-as-a-service. It packs a wide range of capabilities, from stealing victims’ files and passwords to capturing desktop activities. WarZone RAT is primarily distributed via phishing emails and receives regular updates from its C2.
|
RAT
Type
:
|
Ex-USSR
Origin
:
|
|
4 December, 2018
First seen
:
|
6 February, 2026
Last seen
:
|
|
Type
:
|
Ex-USSR
Origin
:
|
|
4 December, 2018
First seen
:
|
6 February, 2026
Last seen
:
|

 421
421
 0
0

 2239
2239
 0
0

 4358
4358
 0
0
WarZoneRAT is a remote access trojan (RAT) that has been distributed via the malware-as-a-service (MaaS) model since 2018 on both Clearnet and Darknet.
The range of capabilities of the malware includes information stealing, infected systems manipulation, and initiation of targeted attacks against organizations. Easy accessibility, frequent updates, and the ever-expanding set of features make WarZone RAT one of the most prevalent RATs in the global threat landscape.
When it was first discovered, researchers believed that the malware is fairly simple and won't follow Ryuk ransomware's story. After the later analysis, it was revealed that this virus has advanced functions under its hood, such as privilege escalation and remote camera control. According to the analysis, Ave Maria Trojan is capable of stealing a wide range of data from infected machines. Even such well-protected information such as credentials stored in Mozilla Firefox is not safe despite the utilized PK11 encryption.
However, some parts of the malware appear to be unfinished. And it looks like the authors are still working on expanding its functionality even further. Considering how effective this RAT already is, this idea is nothing but worrying.
WarZoneRAT uses a DLL hijacking exploit that, at this point, doesn’t have a foreseeable fix. It allows the malware to escalate privileges of a Windows process and enable a malicious process to gain administrative control of an infected machine. Unfortunately, the malware is also capable of avoiding detection on many target machines.
Once the malware achieves this initial target, it downloads additional plugins and even other viruses like Lokibot to the machine.
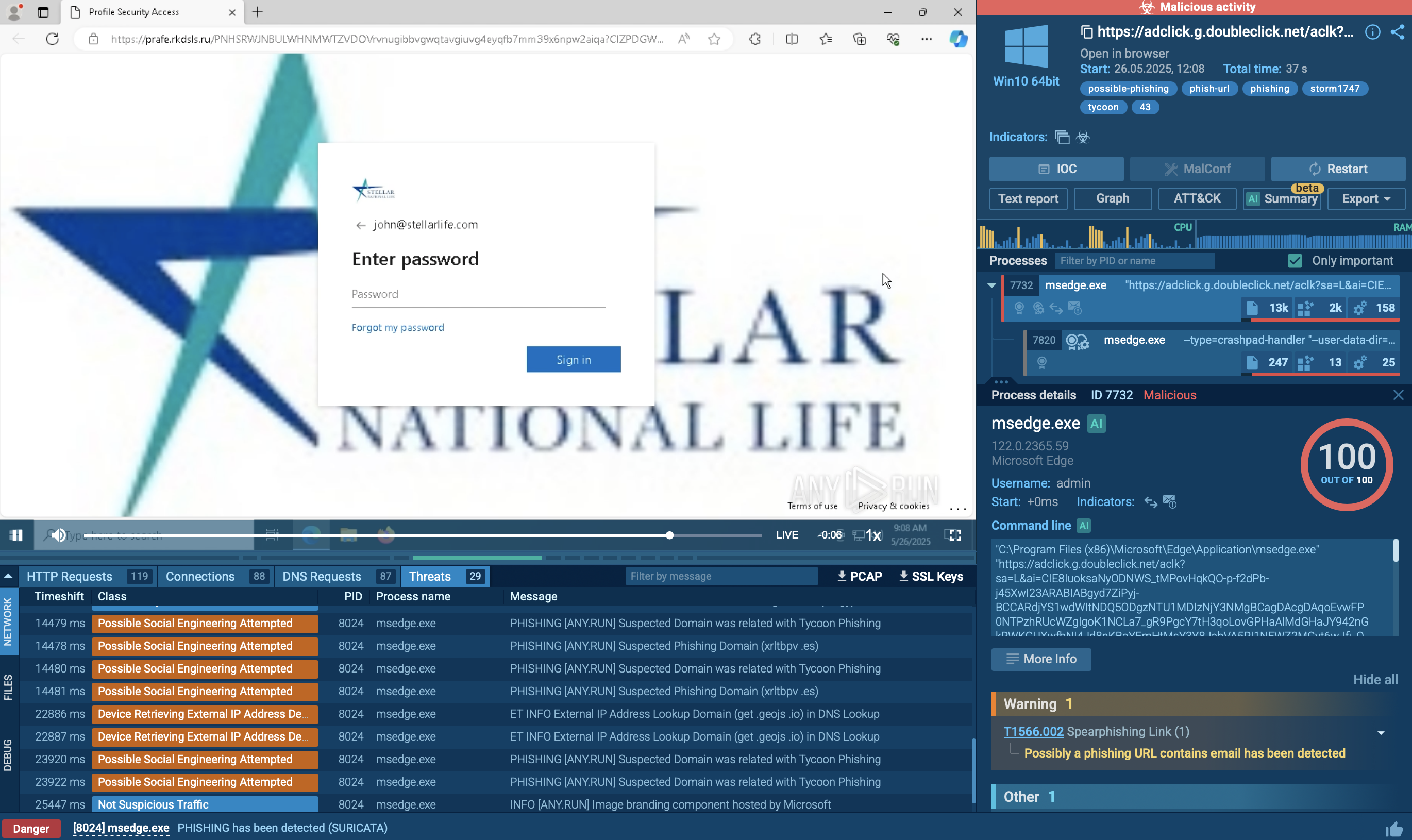
WarZoneRAT operates by infiltrating a target's computer through a range of techniques, such as phishing emails. Once installed, it establishes an encrypted link with its command and control (C2) server, allowing the attacker to manage the compromised computer from a remote location.
The malware is equipped with a broad selection of features, some of which include:
One noteworthy aspect of WarZone RAT is its use of C++. While many RATs are built with .NET Framework (e.g., njRAT), which limits their operation to MS Windows, WarZoneRAT can function on any system with a C++ compiler.
The malware also implements obfuscation and evasion techniques to make detection a challenge. For instance, WarZone RAT can bypass User Account Control (UAC) to escalate privileges, installing itself on the victim's system. It also leverages process hollowing, which involves executing malicious binary as part of a legitimate process. Additionally, it makes use of anti-debugging mechanisms, complicating analysts’ investigations.
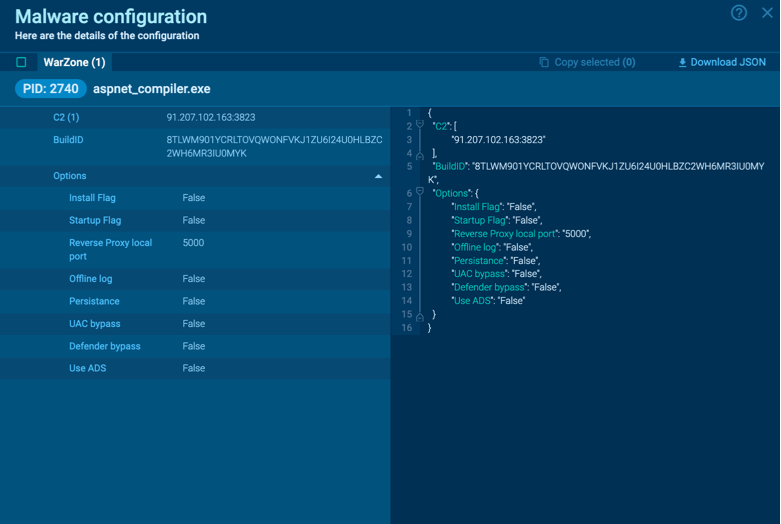 WarZoneRAT’s configuration
WarZoneRAT’s configuration
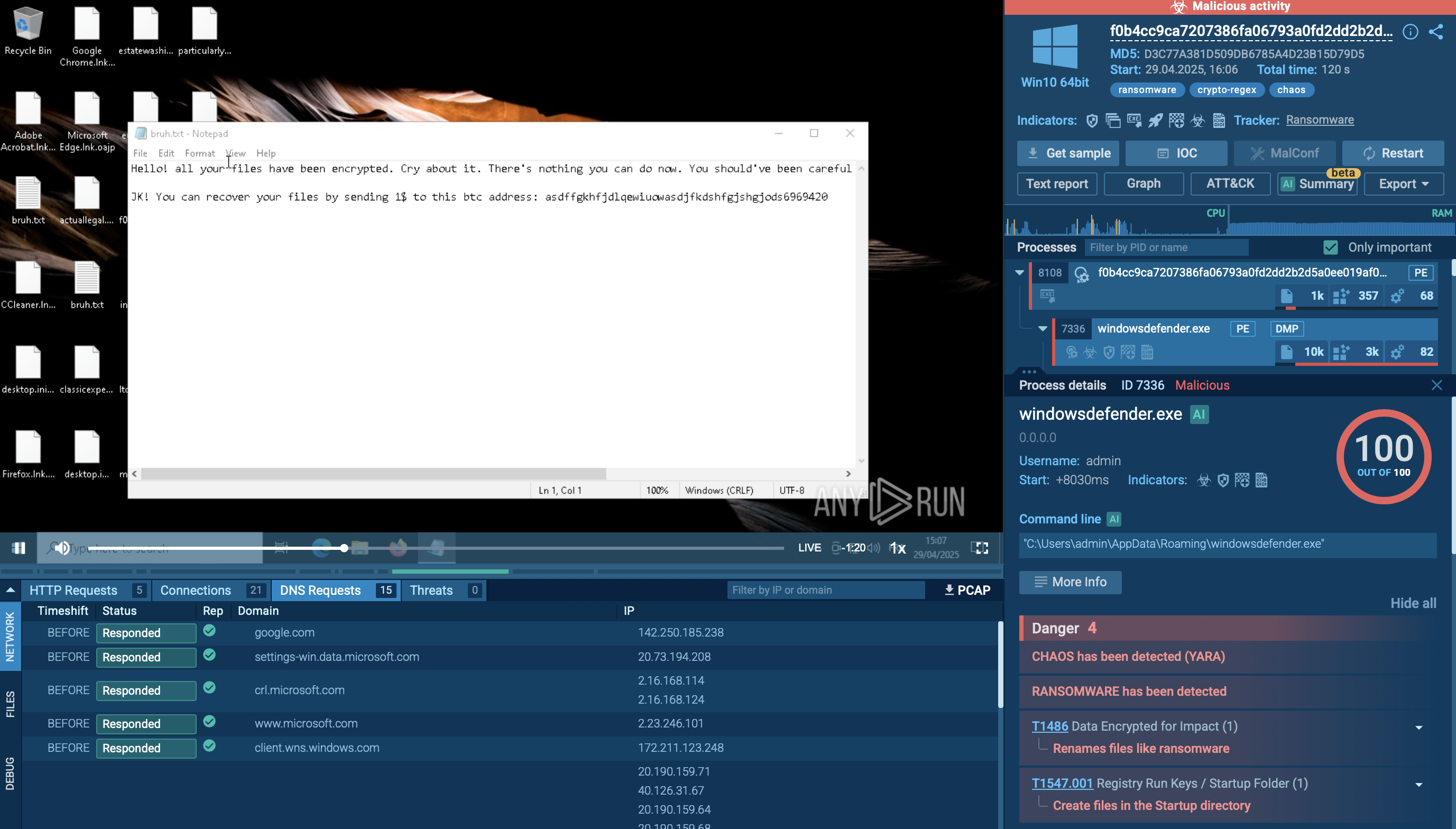
By uploading a sample of WarZone RAT to the ANY.RUN sandbox, you can see the complete execution path of this malware, which may vary in different versions of WarZoneRAT.
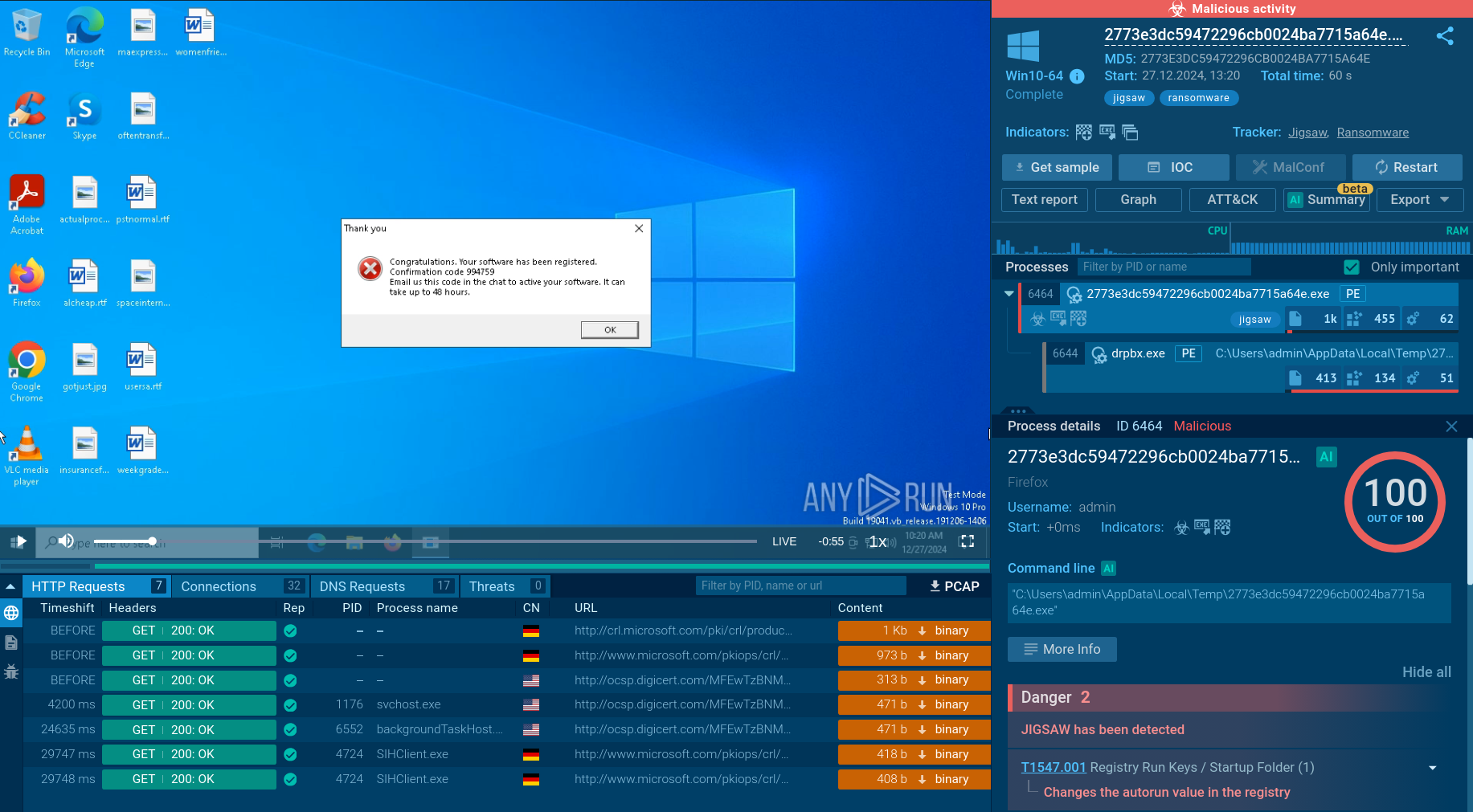
Once the RAT makes its way into the system and begins execution, it uses cmd to collect information about the network configuration. To evade process-based defenses, it often employs process injection. In our case, Warzone utilizes the process hollowing technique (T1055.012) to inject its malicious code into the legitimate process aspnet_compiler.exe.
After WarZone RAT starts the hijacked process, it begins its malicious activity, such as stealing sensitive information and collecting credentials. In our sample, the malware does not receive a response from the Command & Control (C&C) server and is waiting for further instructions.
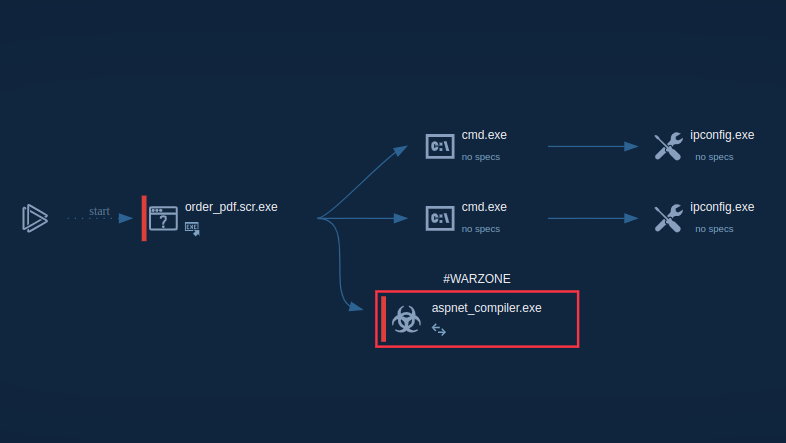 WarZoneRAT’s process graph
WarZoneRAT’s process graph
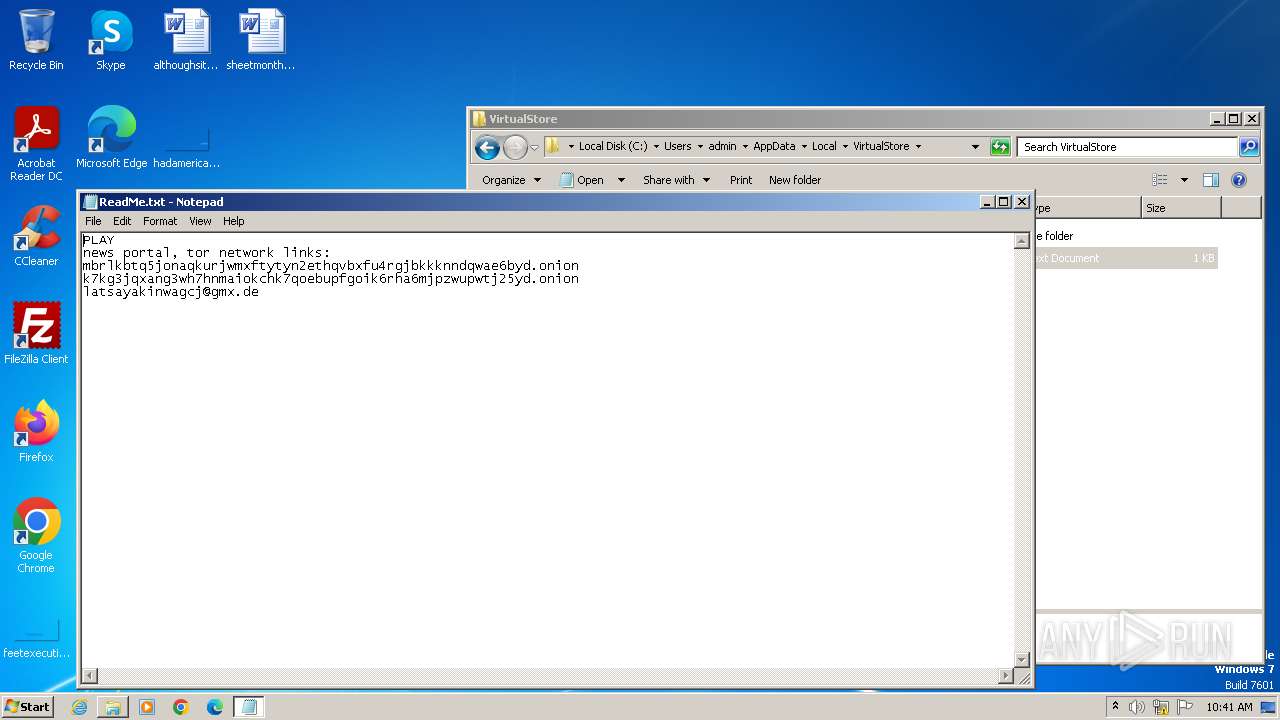
Although there are plenty of ways WarZoneRAT can make it to a victim’s computer, the malware has been observed to utilize phishing emails as the primary method of distribution, which is also extensively employed by Vidar. Such emails contain malicious attachments that, when opened, install the malware on the victim's computer. For example, one of the occurrences of this malware was attributed to fake Hungarian government emails, which contained a WarZoneRAT executable in a .zip folder.
Additionally, the malware can be distributed as part of Microsoft 365 files, particularly .doc and .xml ones, injected with malicious code. When users open such files, the payload instantly gets downloaded, infecting their systems. The malware also can be accidentally downloaded by unsuspecting users visiting malicious websites. Similarly, some of the samples of this program were found on cloud storage platforms, disguising themselves as ordinary files.
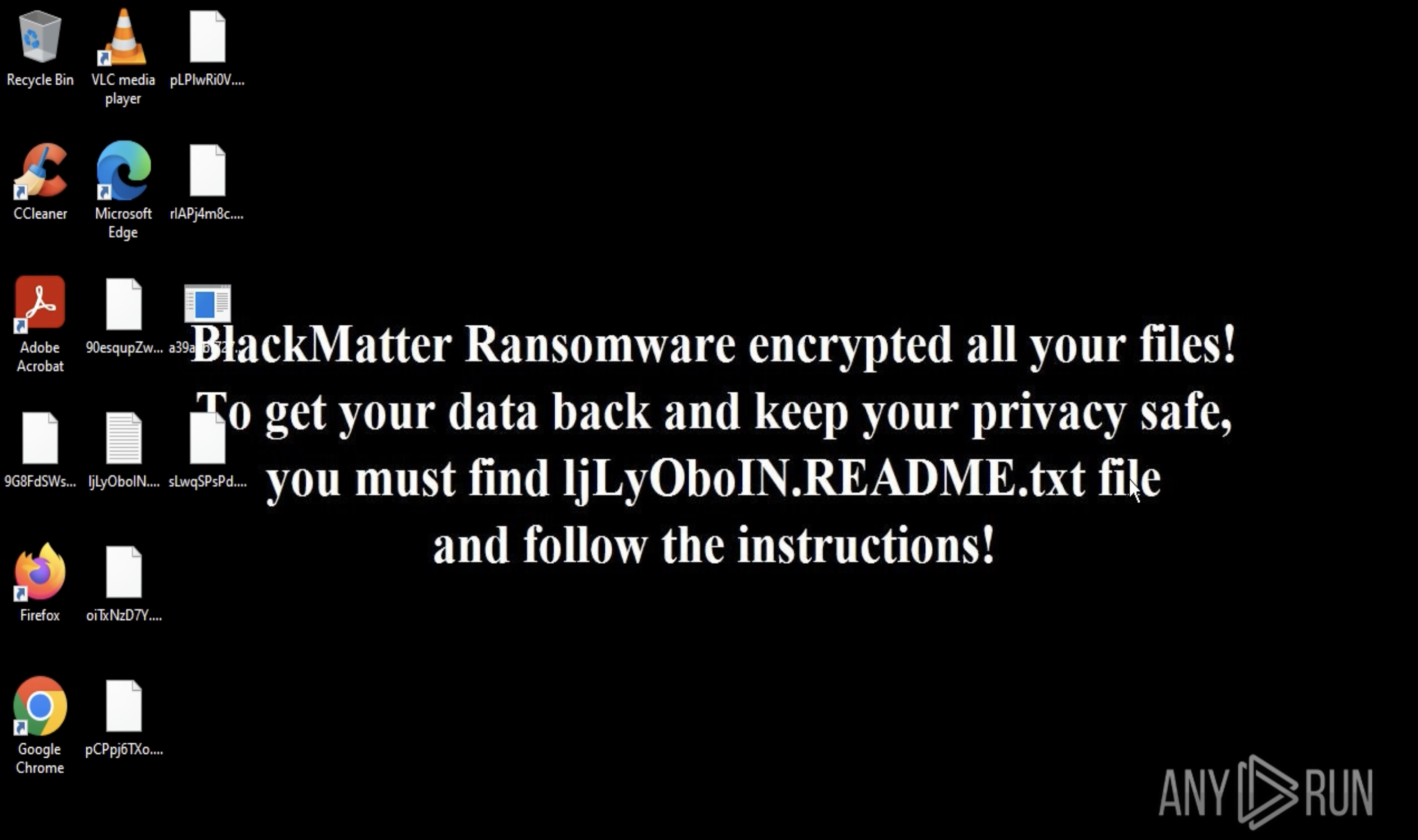
Unlike ransomware, WarZone RAT malware performs information stealing offline which causes it to save data locally on an infected system. To get the analysis of what information was stolen by Ave Maria RAT, take a look inside files that it creates using "Static Discovering." These files often have names in the dd-mm-yy_hh.mm.ss format. To open a file, click on a file’s name and start the analysis.
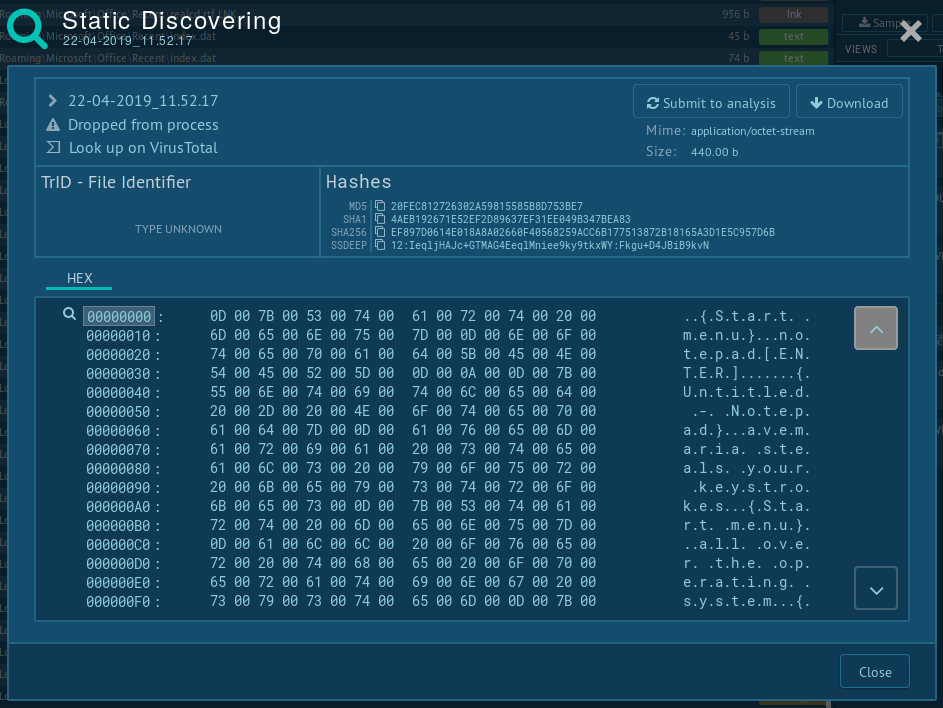 Information is stolen by WarZone RAT
Information is stolen by WarZone RAT
WarZoneRAT is a serious threat to organizations and individuals, and it is vital to be aware of the malware's capabilities and distribution methods to avoid infection. The most effective solution to protecting your infrastructure from this malicious program is to steer clear of downloading attachments and files from senders and sources you do not know or trust.
You can also check any suspicious file or URL in the ANY.RUN sandbox to receive a conclusive verdict on whether it is malicious or not.