Let’s take a moment to reflect on 2023. We’ve analyzed the most prevalent malware families, types, and TTPs of the year, and we’re bringing you the highlights in this article.
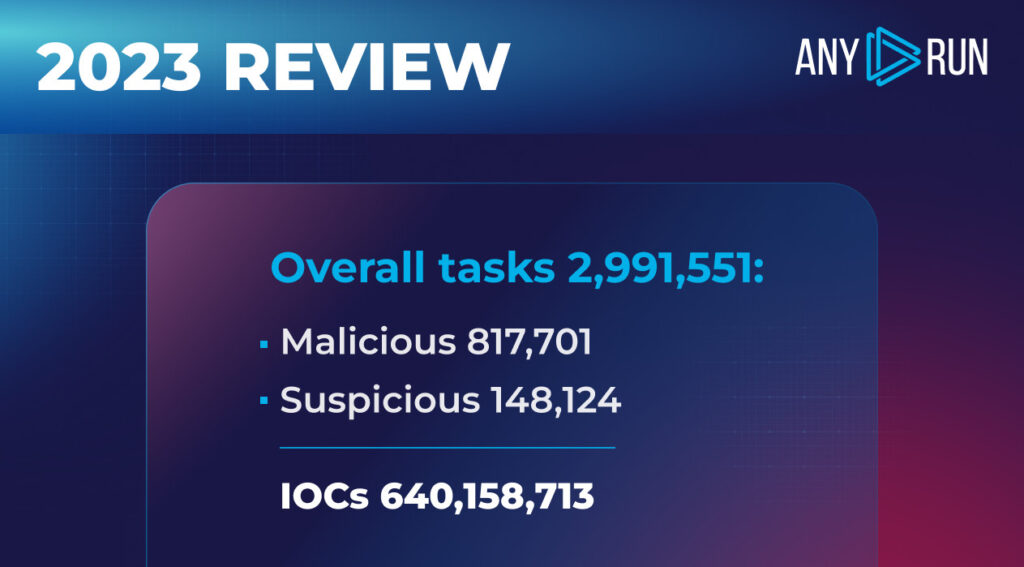
This report is based on the analysis of 2,991,551 public tasks created by our community in 2023. Out of these, 817,701 were tagged as malicious, and 148,124 as suspicious. Overall, ANY.RUN helped the cybersecurity community identify 640,158,713 IOCs in 2023.
Top Malware Types in 2023
Let’s begin by taking a closer look at the most common types of malware identified by ANY.RUN’s sandbox. In 2023, loaders, stealers, and RATs took the lead with 24,136, 18,290, and 17,431 detections respectively. Around 15,630 detections were attributed to trojans:
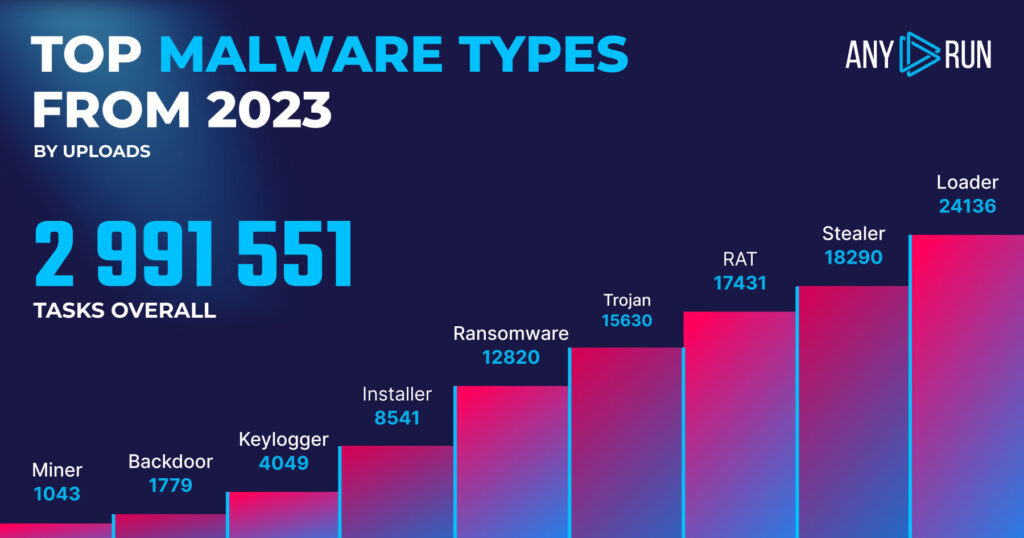
- Loader: 24,136
- Stealer: 18,290
- Remote Access Trojan (RAT): 17,431
- Trojan: 15,630
- Ransomware: 12,820
- Installer: 8,541
- Keylogger: 4,049
- Backdoor: 1,779
- Miner: 1,043
Top Malware Families in 2023
In terms of malware families, Redline was by far the most popular (9205 detections), spotted more than twice as frequently as the second-most used malware Remcos (4407 detecitions). Redline is popular among cybercriminals because it’s easy to buy online and it can evade detection through polymorphic code, rootkit functionalities, and intricate obfuscation methods.
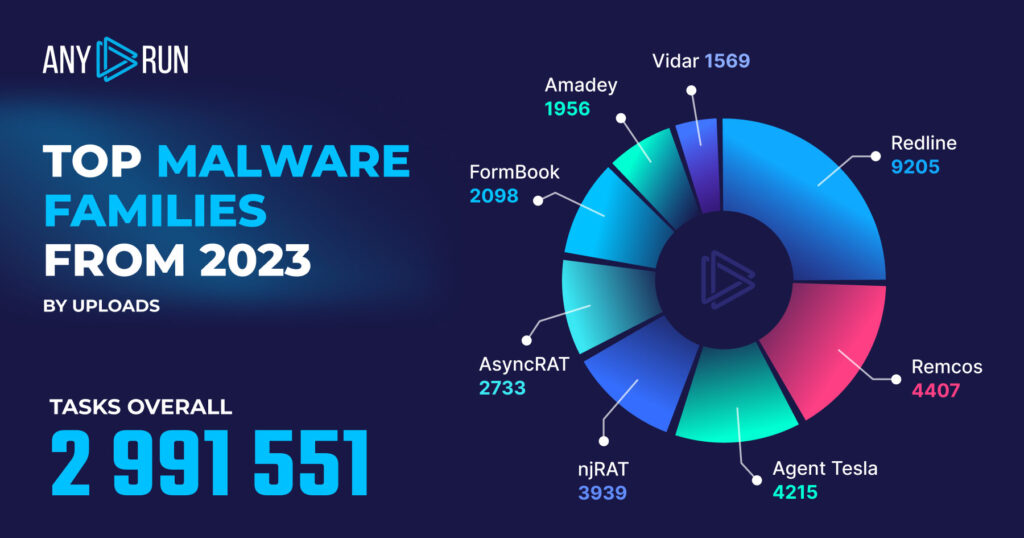
- Redline: 9,205
- Remcos: 4,407
- Agent Tesla: 4,215
- njRAT: 3,939
- AsyncRAT: 2,733
- FormBook: 2,098
- Amadey: 1,956
- Vidar: 1,569
Top MITRE ATT&CK techniques in 2023
MITRE ATT&CK is a widely recognized framework used globally. It categorizes various adversary actions into tactics and techniques. It’s an essential tool for malware analysts to identify, assess, and address threats more effectively.
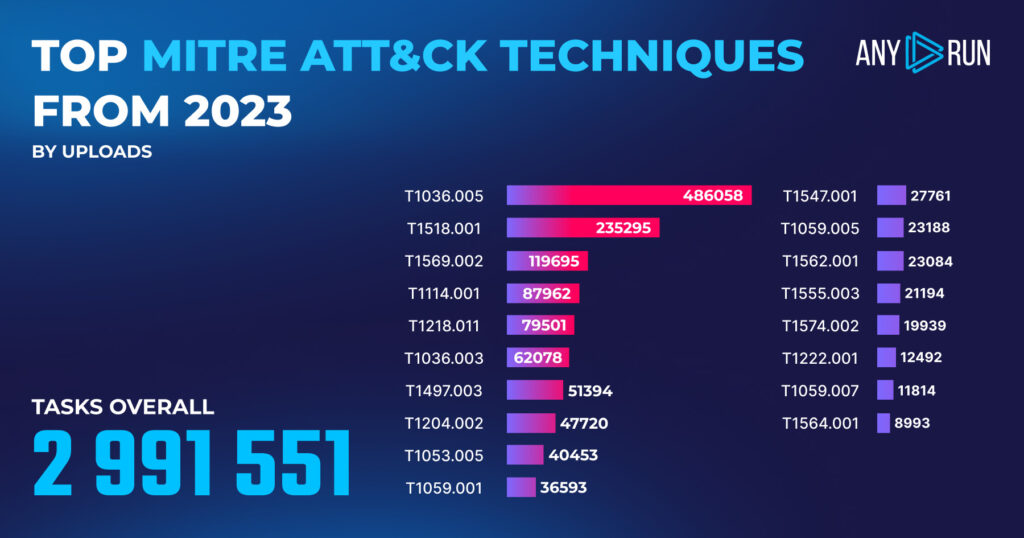
ANY.RUN has a MITRE ATT&CK report that matches malware actions to specific techniques. In 2023, we made over 1.2 million matches, allowing us to put together this spreadsheet of TTPs adversaries employed most frequently in 2023:
| MITRE ATT&CK Technique | Count |
|---|---|
| T1036.005 Masquerading: Match Legitimate Name or Location | 486,058 |
| T1518.001 Software Discovery: Security Software Discovery | 235,295 |
| T1569.002 System Services: Service Execution | 119,695 |
| T1114.001 Email Collection: Local Email Collection | 87,962 |
| T1218.011 System Binary Proxy Execution: Rundll32 | 79,501 |
| T1059.003 Command and Scripting Interpreter: Windows Command Shell | 75,300 |
| T1036.003 Masquerading: Rename System Utilities | 62,078 |
| T1497.003 Virtualization/Sandbox Evasion: Time Based Evasion | 51,394 |
| T1204.002 User Execution: Malicious File | 47,720 |
| T1053.005 Scheduled Task/Job: Scheduled Task | 40,453 |
| T1059.001 Command and Scripting Interpreter: PowerShell | 36,593 |
| T1547.001 Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | 27,761 |
| T1059.005 Command and Scripting Interpreter: Visual Basic | 23,188 |
| T1562.001 Impair Defenses: Disable or Modify Tools | 23,084 |
| T1555.003 Credentials from Password Stores: Credentials from Web Browsers | 21,194 |
| T1574.002 Hijack Execution Flow: DLL Side-Loading | 19,939 |
| T1222.001 File and Directory Permissions Modification: Windows File and Directory Permissions Modification | 12,492 |
| T1059.007 Command and Scripting Interpreter: JavaScript | 11,814 |
| T1564.001 Hide Artifacts: Hidden Files and Directories | 8,993 |
Top TTPs: highlights:
- Masquerading Techniques (T1036.005): There’s a notable prelevance of Masquerading: Match Legitimate Name or Location technique. This indicates how common obfuscation via deceptive filenames and paths has been in 2023. This technique employs mimicry tactics to bypass heuristic detection. Effective countermeasures include behavioral analysis, focusing on anomaly detection in process tree execution and scrutinizing file path irregularities.
- Security Software Discovery (T1518.001): Software Discovery: Security Software Discovery is indicative of sophisticated adversaries targeting security mechanisms. This method is a hallmark of APTs and targeted ransomware campaigns.
- Increased Use of System Services for Execution (T1569.002): We’re seeing a lot of malware use system services to stay hidden and live of the land. This is a common technique in rootkits and sophisticated malware. This approach exploits system services to execute code at elevated privileges.
- Email Collection: Local Email Collection (T1114.001): This technique takes place with malware that focuses on stealing sensitive information from emails, specifically from local email files such as cache or Outlook files.
Report methodology
In our report, we analyzed data from 2,991,551 tasks sent to our public threat database. This information is from researchers in our community who helped by running tasks in ANY.RUN.
About ANY.RUN
ANY.RUN is a cloud malware sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams. Every day, 300,000 professionals use our platform to investigate incidents and streamline threat analysis.
Request a demo today and enjoy 14 days of free access to our Enterprise plan.








0 comments