We are facing a global threat. A threat of malware pandemics. News about cyber attacks on large companies is starting to surface almost every day. Too often do these attacks result in leaks of sensitive data.
And it is not just the attack frequency that is growing. Malware diversity is increasing as well. According to reports, in 2019 malware detections increased by 13 percent on Windows alone.
Keeping this in mind, as researchers we must thoroughly understand malware types. Or at least know the most common families out there.
Unfortunately, there is a lot of malware. So, to ensure that this article will indeed have an end, we are only going to explore viruses that affect PCs here. Mobile malware is a whole different and vast field, so let’s leave it for another time.
Amongst malware that affects PCs, these are the most popular families:
- Trojans
- Loaders
- Stealers
- Adware
- Ransomware
- Phishing
- RATs
- Bankers
- Exploits
- Malspams
- Spywares
- Information stealers
In this guide, we are going to focus specifically on the following six types of malware:
- Trojans
- RATs
- Banking Trojans
- Stealers
- Loaders
- Ransomware
They are the malware types that are responsible for the vast majority of cyberattacks. In ANY.RUN, we are getting reports about these families every day, which gives us an insight into how malware attacks are distributed among them:
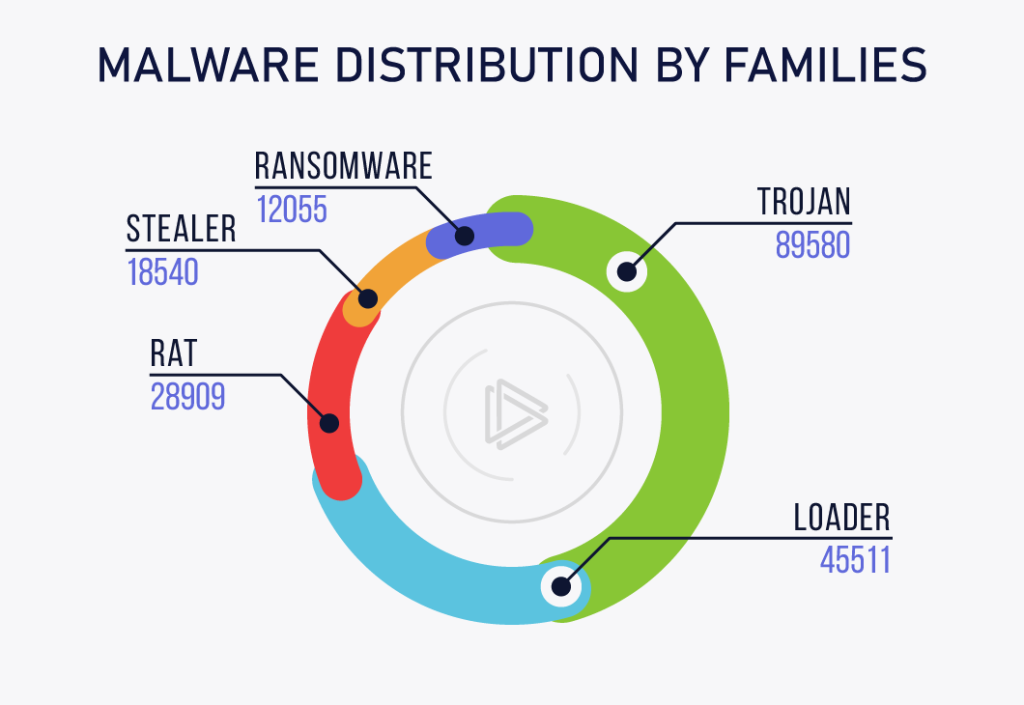
Now, it is important to understand the distinctions between families. But it is also important to keep in mind that these distinctions aren’t always concrete. A lot of modern malicious programs are starting to blur the borders between families, combining functionalities of different malware types. For example, some stealers are commonly known to drop other malware on infected systems.
You may have also noticed that two of the most widely known terms, “Computer virus” and “Worm” are missing from the list. That’s because today those two families can be considered extinct and they are very rarely used as standalone programs.
Lastly, before we jump into the guide we should note that several methodologies classify malware slightly differently. To make this article simpler, we are going to use the same system as in the main ANY.RUN service.
Without any further ado, let’s jump right into the classification
1. What is Trojan?
Trojans, sometimes also called Trojan horses are a family of malware that uses social engineering to trick users into installing and activating themselves. Just like the wooden horse from the legend of Troy after which the family is named, they pose harmless until the victim willingly installs the payload on their system. Trojans are generally categorized based on this infiltration behavior. They can perform various malicious tasks, with the most common being:
- Data tampering;
- Information stealing;
- Tampering with computers or computer network performance;
- Spying through the use of peripherals, such as webcams or mics;
- Cryptocurrency mining;
As we’ve already mentioned, many malware samples are borrowing functions from other families and Trojans are no exception. Over time the Trojan family has been expanding and some of its members eventually spawned whole new classes of malware. One example of this is RATs or Banking Trojans which we will cover later in the article.
The Trojan family includes some famous (though, the word infamous is more fitting here) malware samples such as the Zeus Trojan, which has managed to infect over 37,000 computers in the UK and steal over one million USD from various banking accounts throughout just a couple of months.
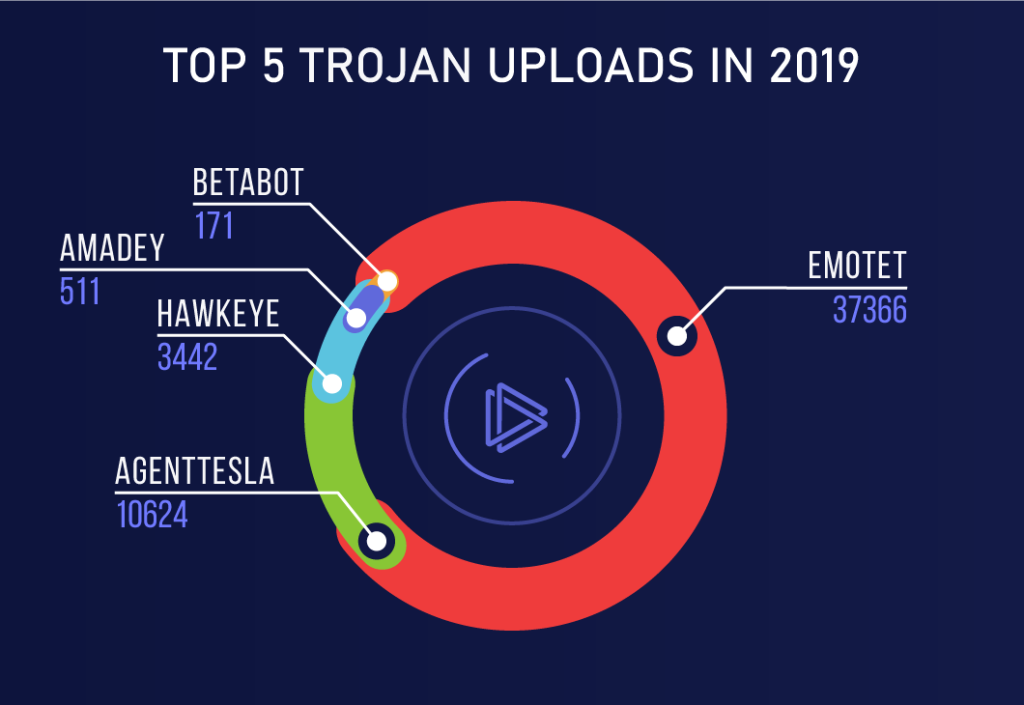
2. What is a RAT?
A RAT or Remote Access Trojan can be utilized to remotely control infected systems. Basically, it’s like TeamViewer software, except one that doesn’t ask for permission and operates illegally. RAT’s are typically designed to stay hidden from the victim for as long as possible and they often double as loaders. This means that they can install other malware samples.
It is easy to imagine just how much damage a RAT can do. While most families of malware have limited functions, a RAT gives the attacker total control of the infected machine, machine. This means that as long as the victim does not suspect that they got infected, hackers have unrestricted access to all personal information from the infected PC as well as all system and administrative functions. That’s a one, nasty malware family.
Common functions of RATs include:
- Remote control of infected machines;
- Information stealing and spying;
- Loading other malware on infected systems;
- Launch of botnets from infected endpoints;
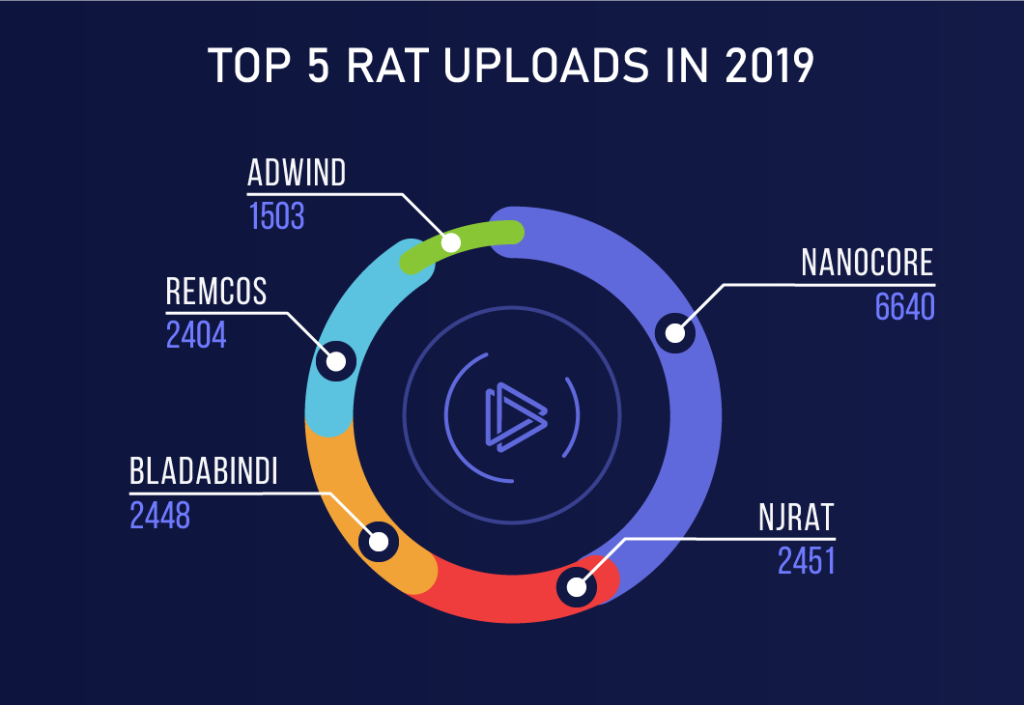
In ANY.RUN, we are processing a large number of malware samples that we receive from our users. Here is the data on the popularity of RATs in 2019:
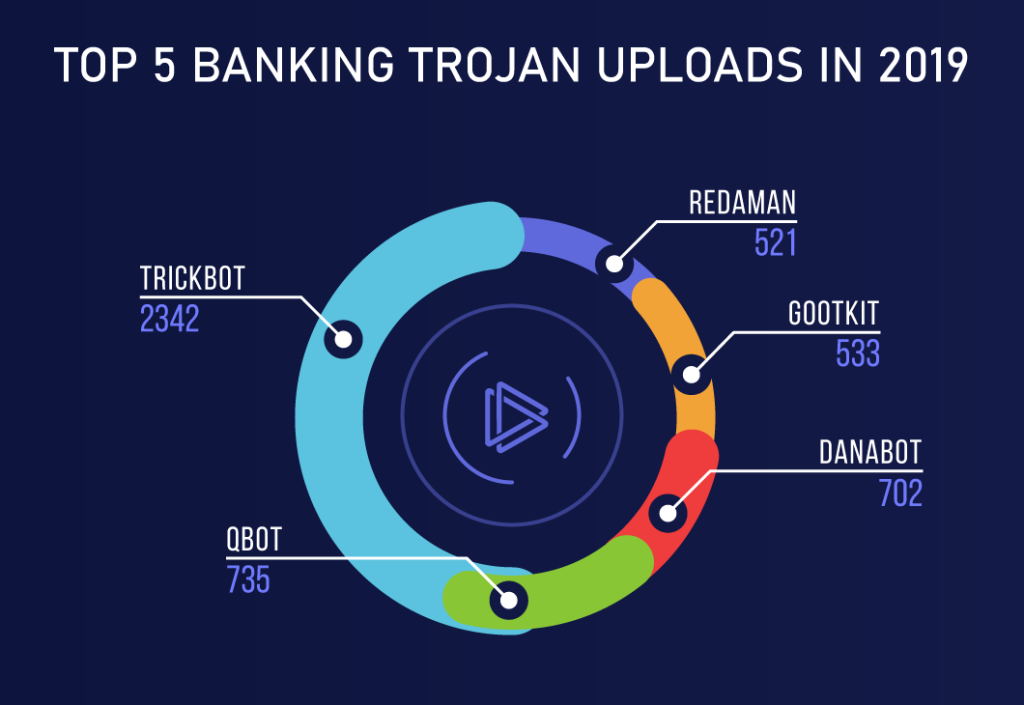
3. What is Trojan.Banker?
Trojan.Bankers or banking trojans can be considered a sub-family of Trojans, but we feel like they deserve their own spot in this classification. Simply put, Trojan.Bankers are Trojans that are designed very specifically to steal banking credentials. Just as classic Trojans, this family uses social engineering to infiltrate a system.
The common malicious functions of this family include:
- Stealing online banking credentials
- Stealing plastic card numbers
- Stealing of pretty much any data related to payments that the malware can find
- Installing other malware on infected systems
As you can see, banking trojans are also following the trend of mixing functions with other families. One of the most popular malware typically associated with banking trojans is Emotet. Despite the fact that according to more modern classification Emotet is not considered a banking Trojan anymore, it is still worth mentioning here, due to its massive popularity. This malware spreads mostly through email spam campaigns and while its main functionality revolves around credential theft, it also often drops the Dridex and TrickBot Trojan on infected systems.
4. What is Information Stealer?
Information stealers also called info stealers, or just stealers for short, are malware designed to collect and retrieve data from infected systems. Yeah, no surprise here, as the name suggests, they steal information. Their targets usually include:
- Passwords and logins for online banking;
- Login credentials for FTP servers;
- Login credentials for emails;
- Login credentials for social media websites;
One of the most popular info stealers right now is called the Raccoon malware. Like many other malware samples in this family, this stealer is offered as a Malware as a Service. This means that original creators sell the software to other criminals, who actually launch attacks. Raccoon can be had for as low as 75 USD a week. For this price, anybody, even without deep technical knowledge can use the malware to steal sensitive information, such as login credentials and cryptocurrency wallets, as well as basic system data.
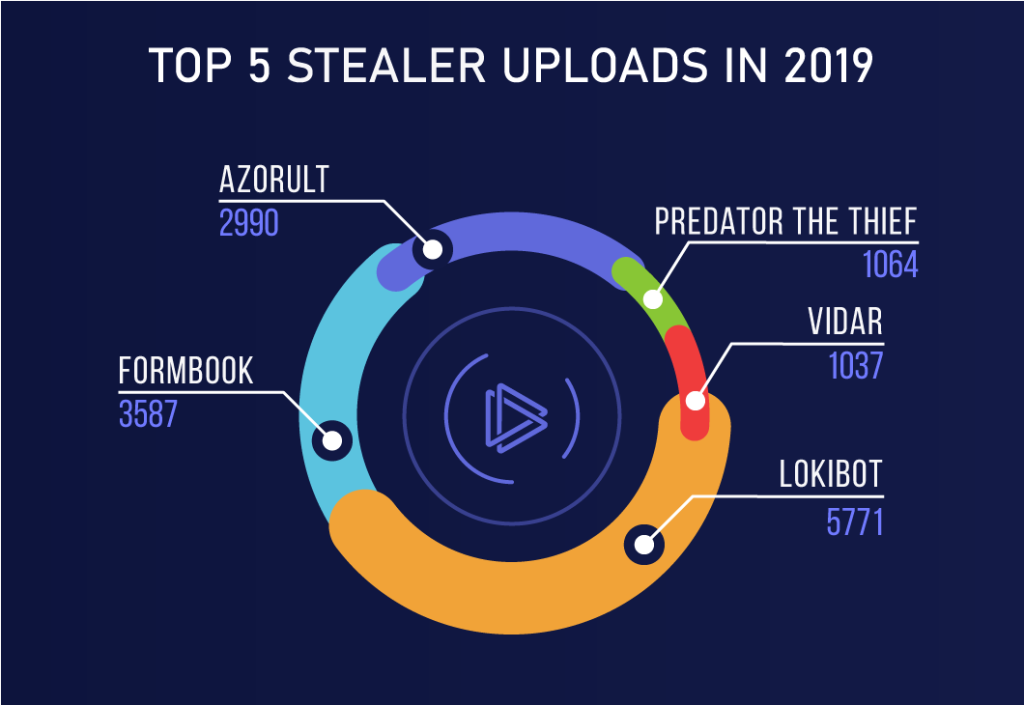
5. What is Trojan.Loader?
Trojan.Loaders, Droppers, or simply Loaders are viruses that aim to install other malware types on the infected system. So, members of this family usually do not tamper with information directly and do not perform malicious functions, other than dropping an infected payload. Their functions include:
- Loading and installation of another malware sample
- Sometimes information theft and spying
Loaders are categorized into two major groups — single-staged loaders are those that contain and end payload in the code, while two-staged loaders attempt to establish a connection with an outside resource on the web and download the target payload from there.
One of the most famous representatives of this family is a malware called Smoke Loader. It has been around since 2011 and continues to be active to this day. This particular malware is modular, meaning that attackers can equip Smoke with additional modules that expand its functionality from dropping payload to information stealing.
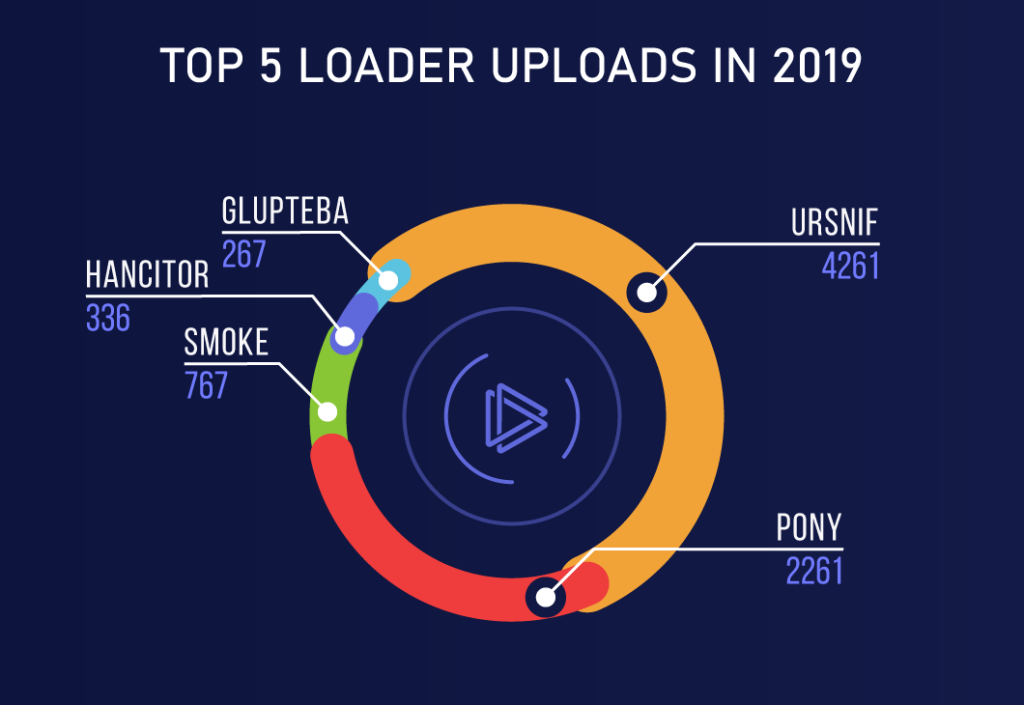
6. What is Ransomware?
Last but not least, Ransomware. Malware samples from this family demand users to pay a ransom, threatening to delete information or publically release sensitive data, unless the demands of attackers are not met. Some malware samples from this family encrypt files on infected PCs using cryptography, making decryption without a special key almost impossible. And the key can only be obtained from special websites if a ransom is paid, typically in a digital currency such as Bitcoin, which provides hackers with an anonymous payment address. Quite often, Ransomware attacks are carried out by initially infecting the system with a Trojan.
This malware family is particularly dangerous because attackers often distribute Ransomware in widespread email campaigns that can be directed not only at organizations but also at thousands of individuals.
An example of Ransomware is Dharma, which has yielded attackers over 25 million US dollars in ransom payments, making it one of the most devastating malicious programs of its type. Another good example is Ryuk, ransomware that is distributed in highly targeted campaigns to organizations. Ryuk has been featured in multiple successful attacks, some costing companies north of 100,000 US dollars.
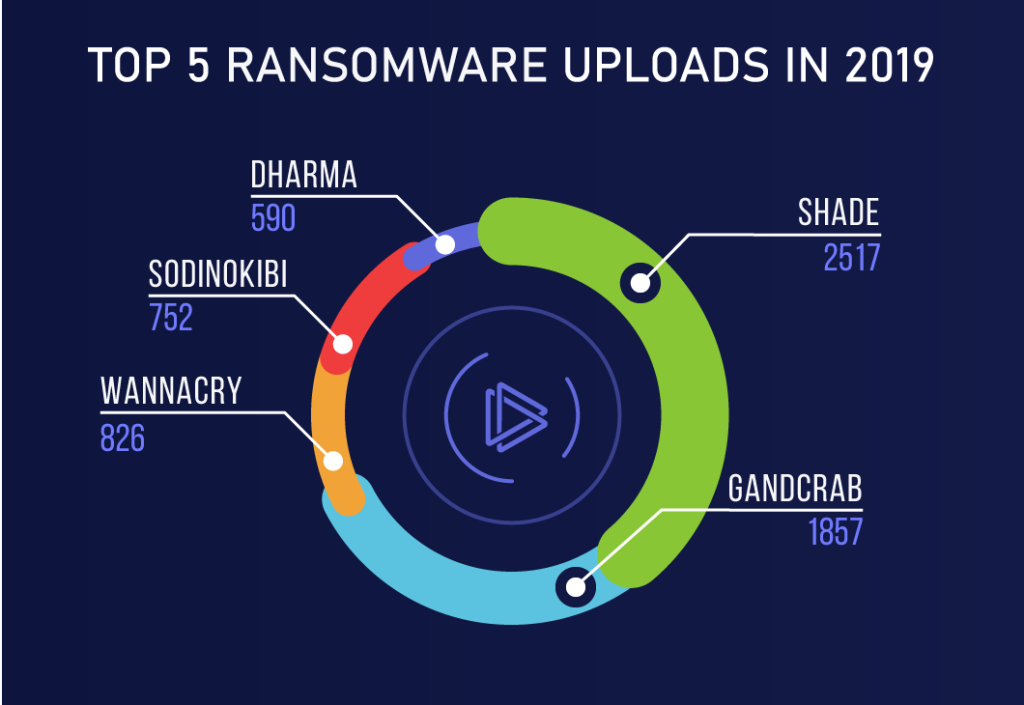
Conclusion
Know your enemy. That is the single best piece of advice that we can give to any aspiring security researcher. This classification is by no means comprehensive, but we do hope that it gives a solid starting point.
However, it is important to understand that malware is always evolving. Not so long ago Worms were our worst enemies. Fast forward a few years and apart from WannaCry, we would be hard-pressed to name samples that have worm-like functionality. Let alone active malware in this class.
Unfortunately, threat actors are an active bunch. They create new malware classes, upgrade the old ones… Generally do anything they can to stay on top of counter-measures developed by us, cybersecurity researchers.
This evolutionary race of malware has resulted in the borders between classes being blurred. The newest trend in malware are samples that combine functionality from multiple families. Like a swiss army knife, these viruses can do multiple things which makes them so much more dangerous.
And that is what we are facing. A global outbreak of potentially the most destructive malware yet created. That’s why getting familiar with the basics and general education in cybersecurity is especially important today. That’s why we reiterate — know your enemy.








0 comments