Welcome to ANY.RUN! This crash course will walk you through the basics of using our interactive sandbox to help you achieve your malware analysis goals.
Let’s get started!
About ANY.RUN’s Interactive Sandbox

ANY.RUN’s Interactive Sandbox enables security teams to rapidly analyze suspicious files and URLs to detect evasive malware and phishing threats early. The solution delivers measurable results that impact the speed and quality of SOC and MSSP operations, on average providing:
- 21-minute MTTR reduction thanks to real-time analysis and reporting that fuel fast response.
- 36% detection rate boost from live interactions with the malware that ensure full detonation of attacks missed by other solutions.
- 88% of threats revealed within 60 seconds of analysis thanks to advanced detection capabilities.
- 20% Tier 1 workload reduction via automation, streamlining routine tasks.
- 30% fewer Tier 1 to Tier 2 escalations by equipping junior staff with actionable insights that let them make decisions on their own with more confidence.
Now, let’s dive into the sandbox’s interface.
Setting up your account
Step 1: Sign up

Get started with ANY.RUN
Analyze malware with no limit inside fully interactive Windows VMs to collect fresh IOCs.
Use your business email to register.
For non-business email users, use the #verification channel on our Discord server to request a free ANY.RUN account.
Step 2: Choose your subscription plan
After logging in to your account, you will be greeted by the dashboard page. From there, you can go to your Profile settings to choose your subscription plan.
We offer a free Community plan that provides you with a basic set of tools for investigations. For an advanced level of malware analysis and privacy, individual researchers can utilize the Hunter plan.
For use in a real SOC setting, we offer Enterprise plan that delivers maximum capabilities of the sandbox, including teamwork features, for boosting business security.
Learn more about ANY.RUN’s plans
With your account all set-up and firing on all cylinders, it is time you get started with your first analysis.
Setting up a virtual machine for malware analysis
In order to set up a virtual machine (VM) for malware analysis in ANY.RUN, you need to create a new analysis session.
Access an interactive tutorial by visiting the FAQ page‘s Tutorials tab and clicking the “How to analyze threats” button.
In case you prefer written instructions, continue reading this article and follow these steps:
Step 1: Open the new analysis window
Click the New analysis button on the left sidebar to open the analysis window.
Step 2: Choose an analysis mode
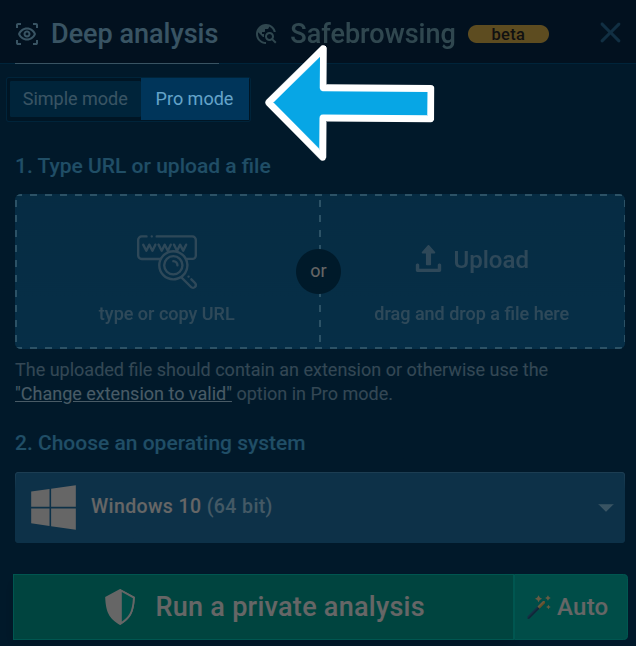
The newly opened analysis window will be set to the User Mode by default, which lets you quickly analyze your file or link but limits your VM settings to only choosing an OS version:
- Windows from 7 through 11 — 32-bit or 64-bit versions.
- Linux — Ubuntu 22.04.2 & Debian 12.2 (ARM, 64-bit).
- Android 14 (ARM, 64-bit).
To open the rest of the VM customization features, enable the Pro mode by pressing the respective button on top of the analysis window.
Step 3: Configure the VM
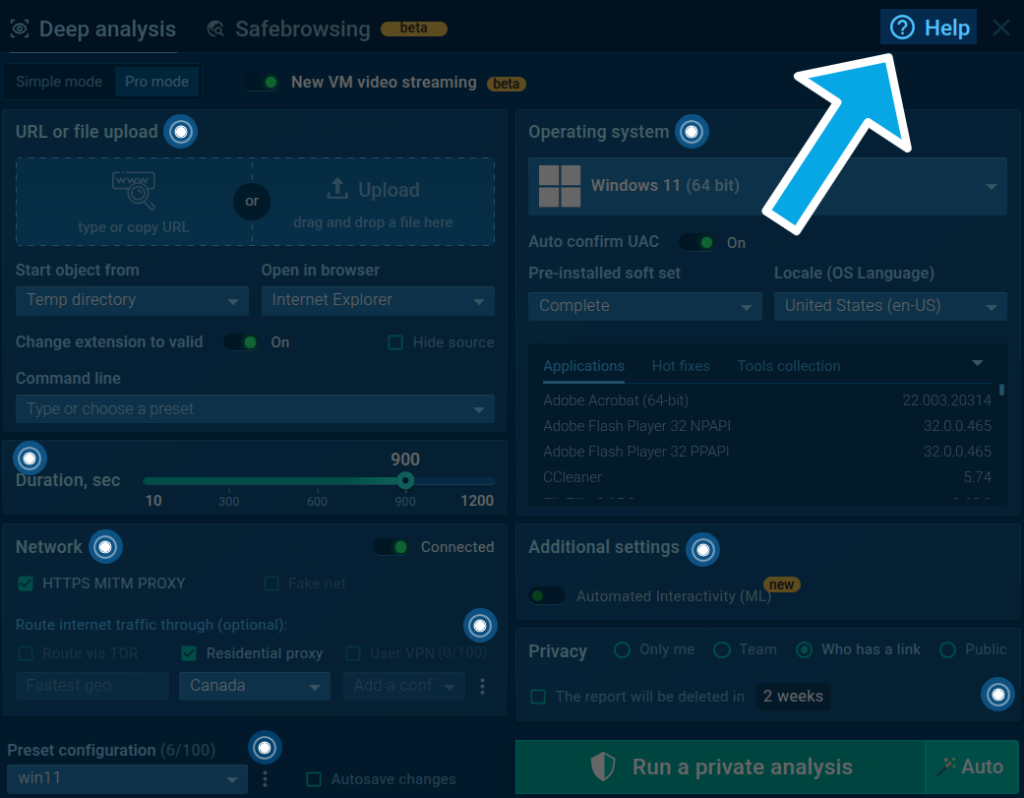
In the Pro mode, you can fine-tune your analysis environment. Click on the question mark icon in the top right corner to access tooltips with detailed explanations of each setting.
After completing the VM setup, begin your analysis by pressing the Run a private/public analysis button.
Learn more: Guide to Creating a new analysis in ANY.RUN
Analyzing malware
Once your analysis is launched, you will be taken to a page where you will be able to analyze your sample in real time and, once it is done, review the findings of the investigation.
Here are the things you can perform as part of your analysis:
Interact with the sample
ANY.RUN enables you to manually interact with your sample in a VM environment like you would on a normal computer.
You can run programs, open tabs in a browser, and even restart the system without delay.
Learn more: Interactive Malware Analysis
Track network activity
The Network section monitors and records network activity as it is occurring and provides the following information:
- HTTP Requests: Displays details of connection requests, including URL connection response and content
- Connections: Shows other protocols that were not mentioned in HTTP Requests
- DNS Requests: Indicates the correlation between a domain name and IP address
- Threats: Detects intrusion using Suricata rules (Detection with Suricata IDS)
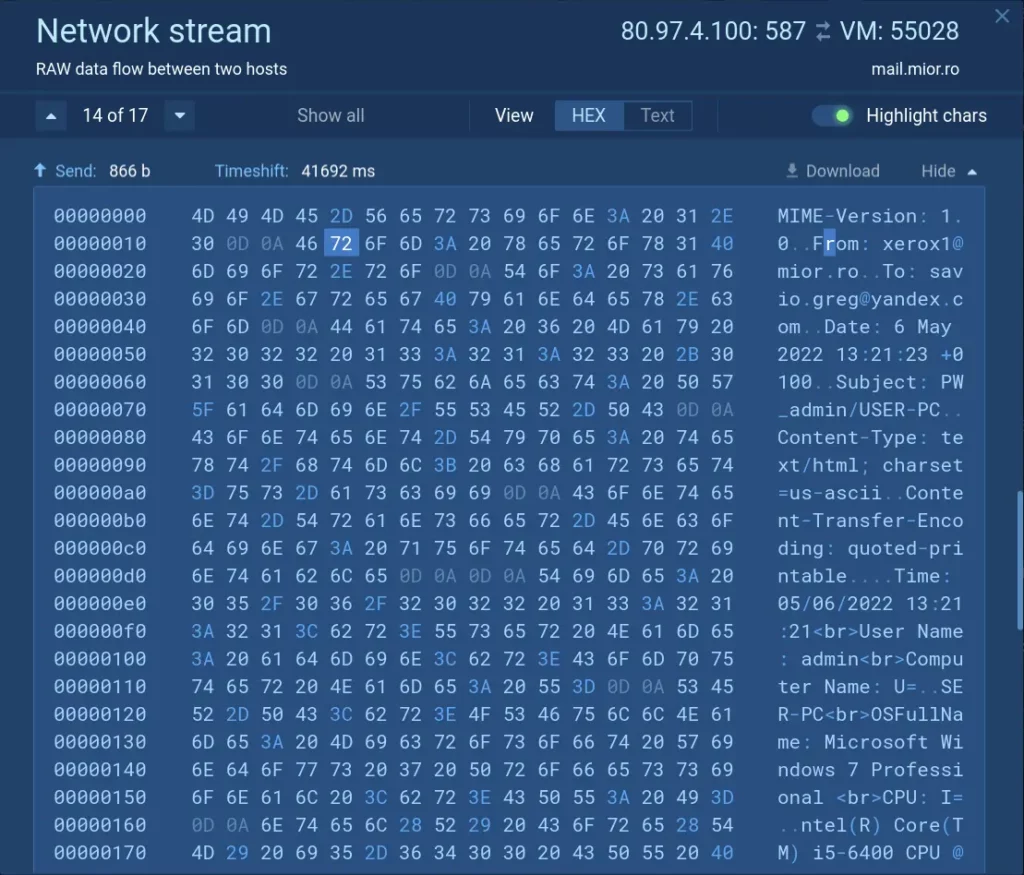
You can examine traffic packet by packet using the Network stream feature, enabling you to identify unusual patterns or connections, stolen data, C2 addresses, proxies, and downloaded files.
Learn more: Analyzing the Network Stream
Let us show you how ANY.RUN can help your SOC team – book a call with us ⬇️
Review modified files
The Files Modification section lists all files used during the analysis. Click on each file’s content to access downloadable Static discovering data.
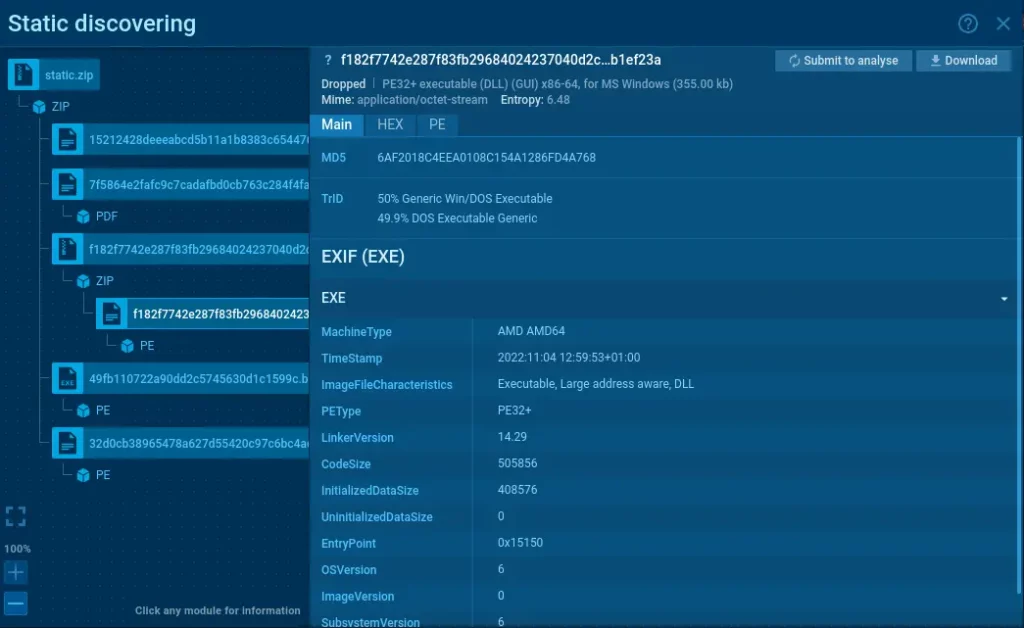
ANY.RUN’s Static discovering feature is modular, letting you analyze a wide range of file types including PDF, LNK, ZIP, RAR, Office documents, and others.
Learn more: Static Analysis for Various File Types
Utilize debugging
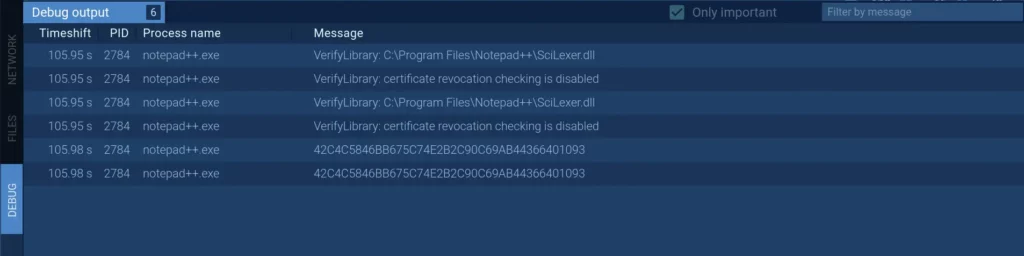
The Debug section displays information on how to debug the program afterward. If you happen to encounter malware like Dridex, debug output messages will be helpful in your investigation.
Inspect processes
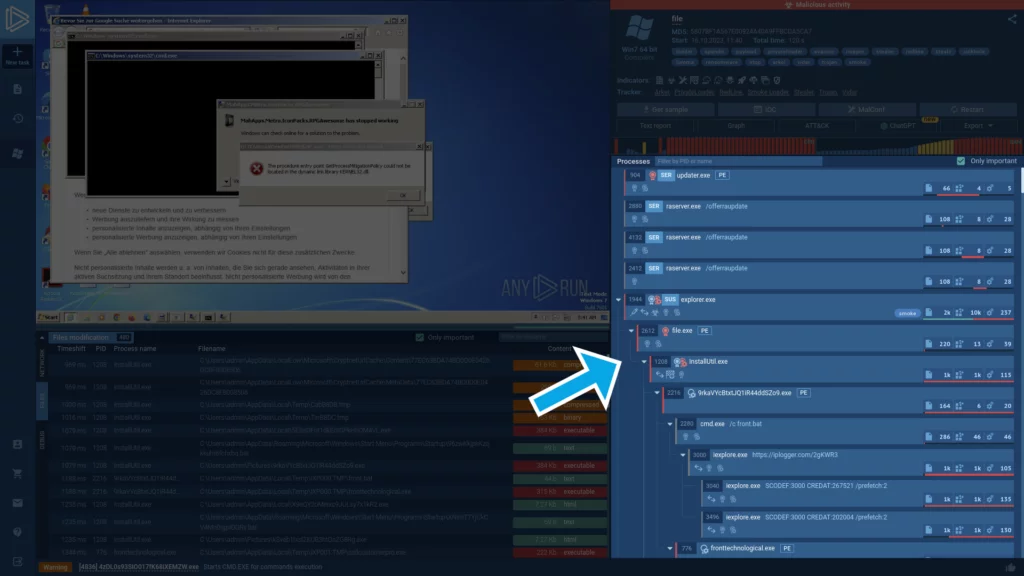
The Processes section lays out a hierarchical view of all processes, accompanied by corresponding indicators.
Learn more: Indicators and Tags Used in ANY.RUN
To investigate a specific process, simply click on it. This will bring up the Process details window, from which you can navigate to the Advanced details by pressing the More info button.
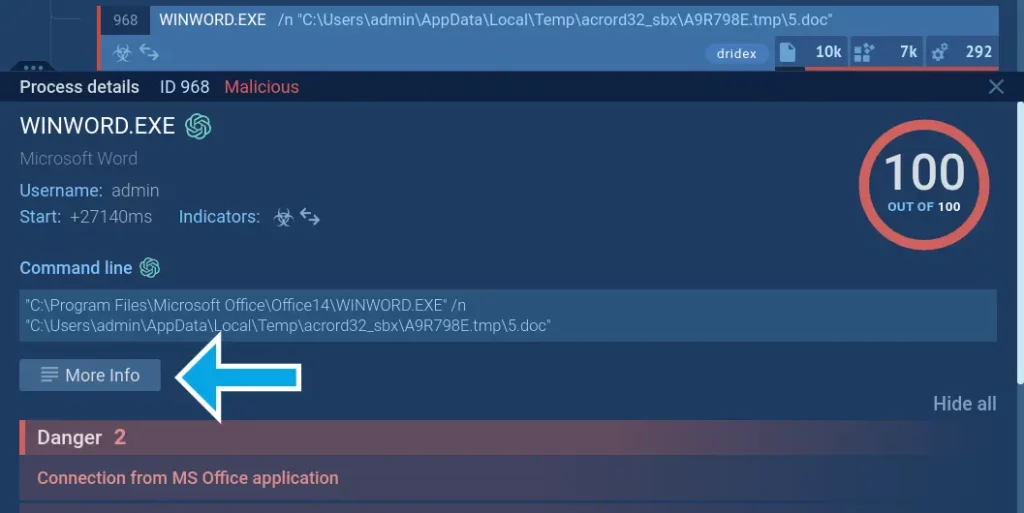
The Advanced details menu can help you track the timeline of any process.
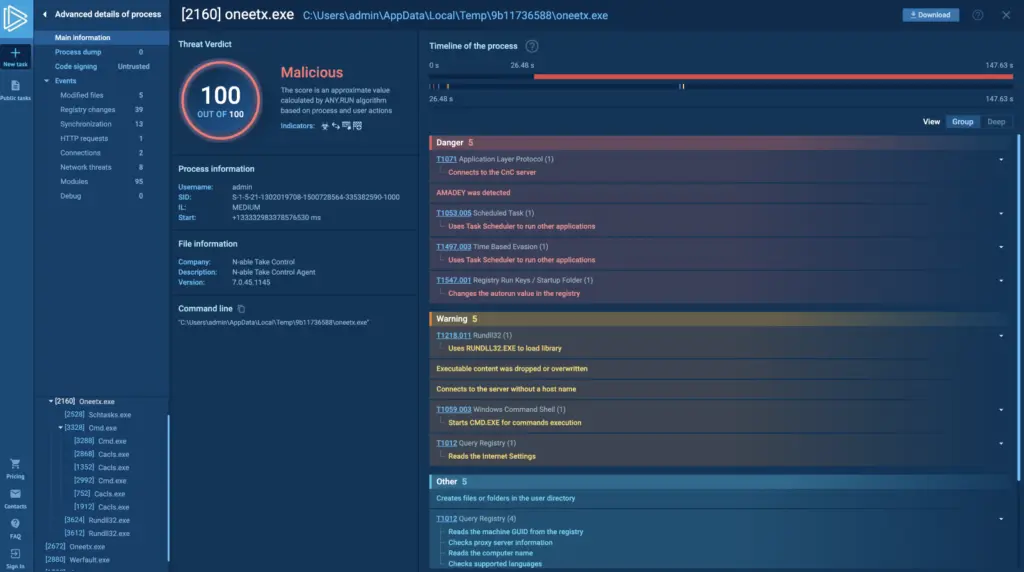
Additionally, here you can download process dumps. The complete list of process details includes:
- Modified files / Files in a raw view;
- Registry changes / Registry keys;
- Synchronization;
- HTTP Requests;
- Connections;
- Network threats;
- Modules;
- Debug.
Learn more: Fast and Simple Access to Malware Details
Access malware analysis reports
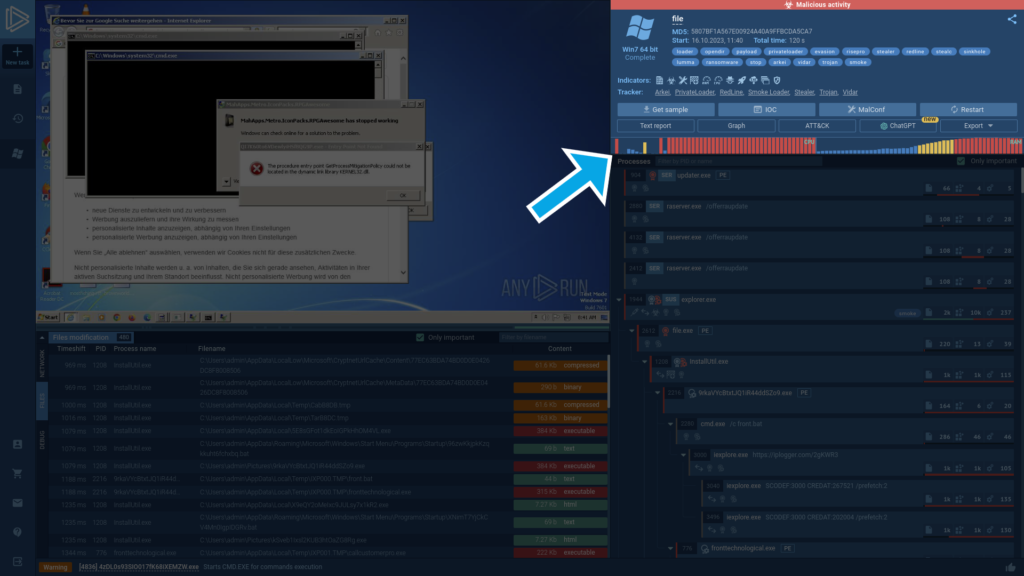
In the top right corner, you can view the key threat information generated as part of the analysis, including:
Indicators of compromise (IOCs)
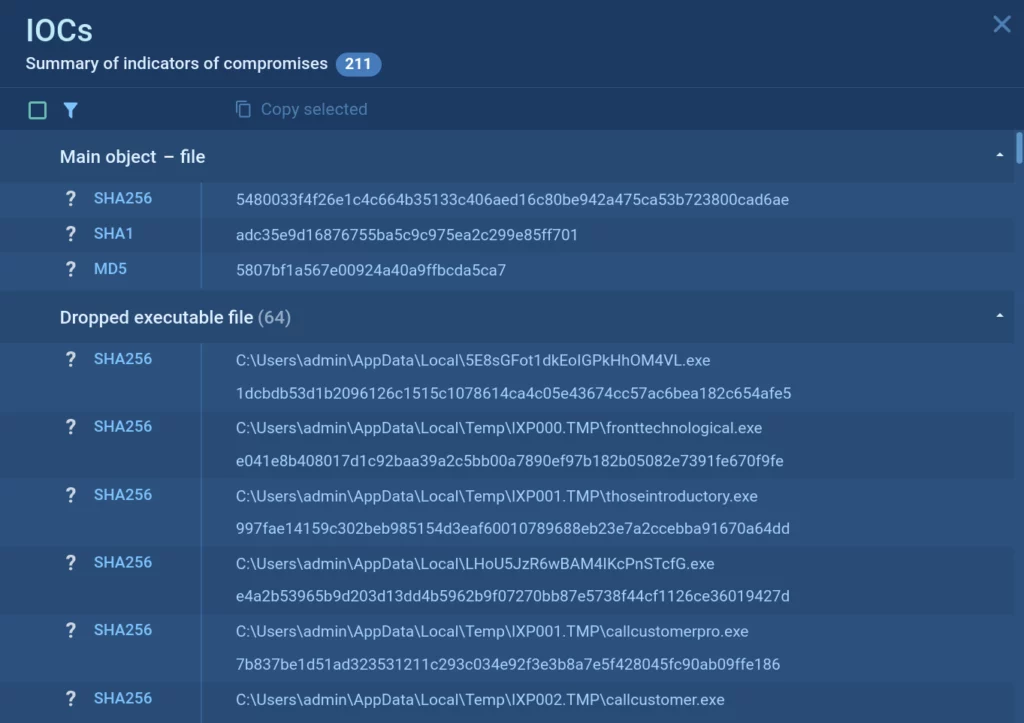
Indicators of compromise are an essential piece of information that you can use for timely detection of malware.
Learn more: Indicators of Compromise
Malware’s configuration
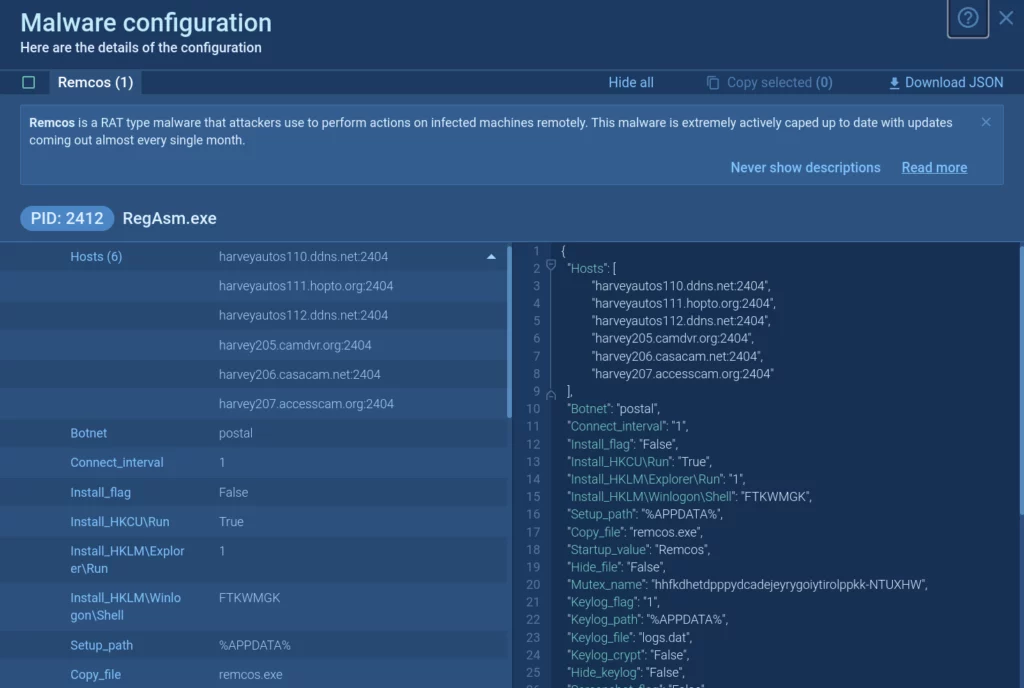
Malware configurations can include a variety of information, such as IP addresses and ports of C2 servers, malware family name, type, and version, encryption keys, anti-debugging, anti-sandbox, and other evasion methods, and much more.
Learn more: Dive into Analysis with Malware Configuration
MITRE ATT&CK Matrix
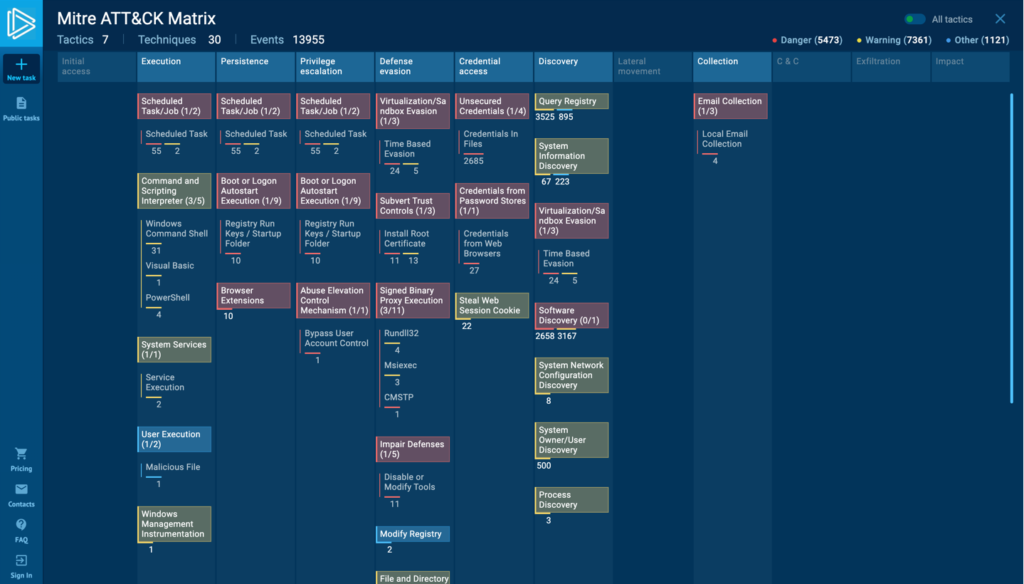
The built-in MITRE ATT&CK Matrix allows you to view the techniques utilized by the malware with action mapping and explore each of them.
Learn more: MITRE ATT&CK Matrix
Private AI Assistant for Malware Analysis in ANY.RUN Sandbox
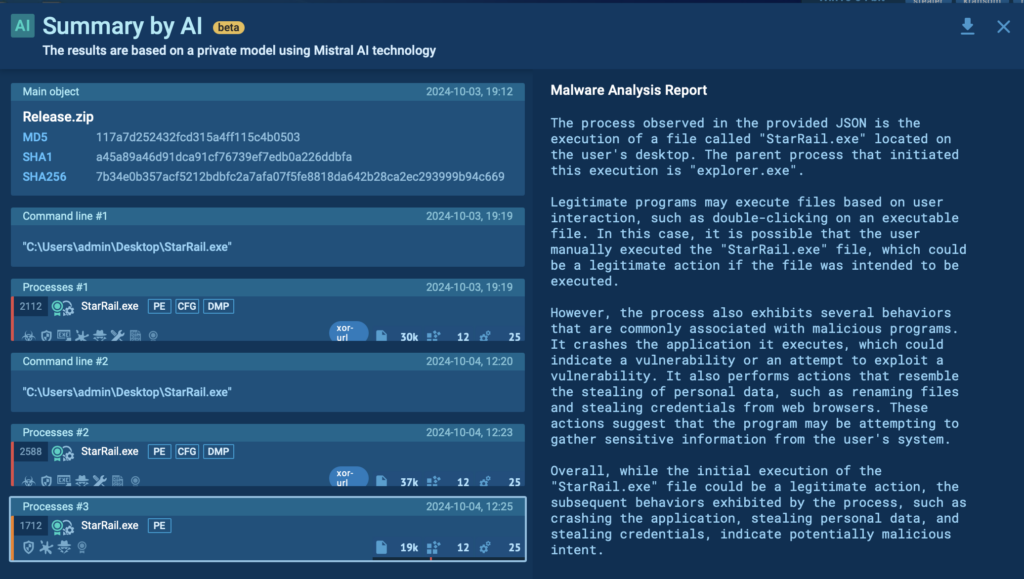
This feature provides you with a deeper understanding of malware’s behavior by providing AI-powered explanations of important elements, such as processes, rules, and connections.
To use this feature, simply click on the AI button next to any important element in your report.
Learn more: Private AI assistant for malware analysis
Malware analysis text report
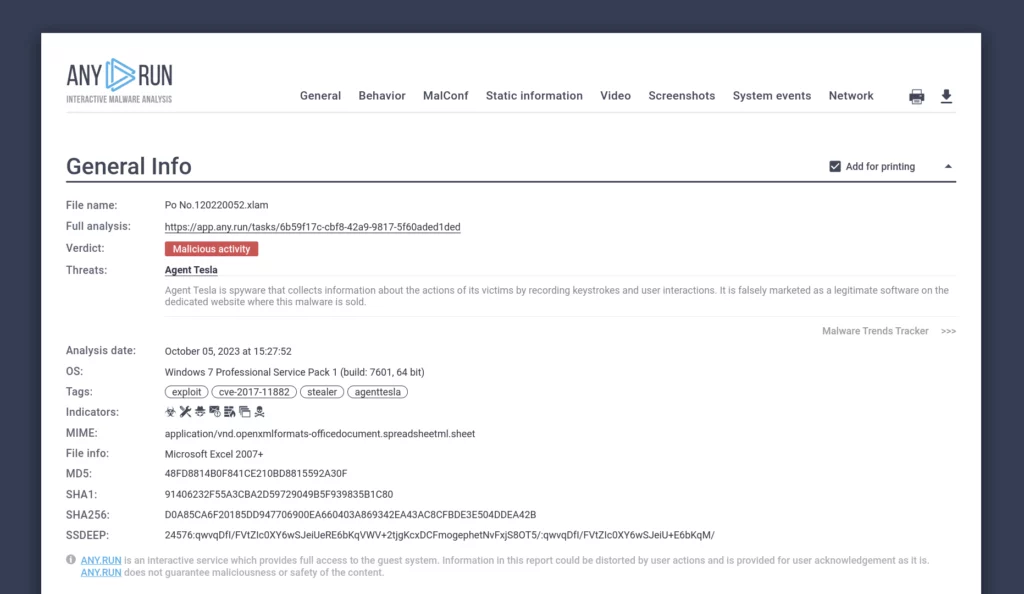
The sandbox generates a comprehensive report for each file and URL you analyze. It includes all of the details we mentioned earlier.
The report can be exported in your preferred format, including JSON and HTML.
Learn more: Malware Analysis Report in One Click
Restart the analysis
You can always restart any analysis with different VM settings to test a sample in a new environment.
Working with public malware samples
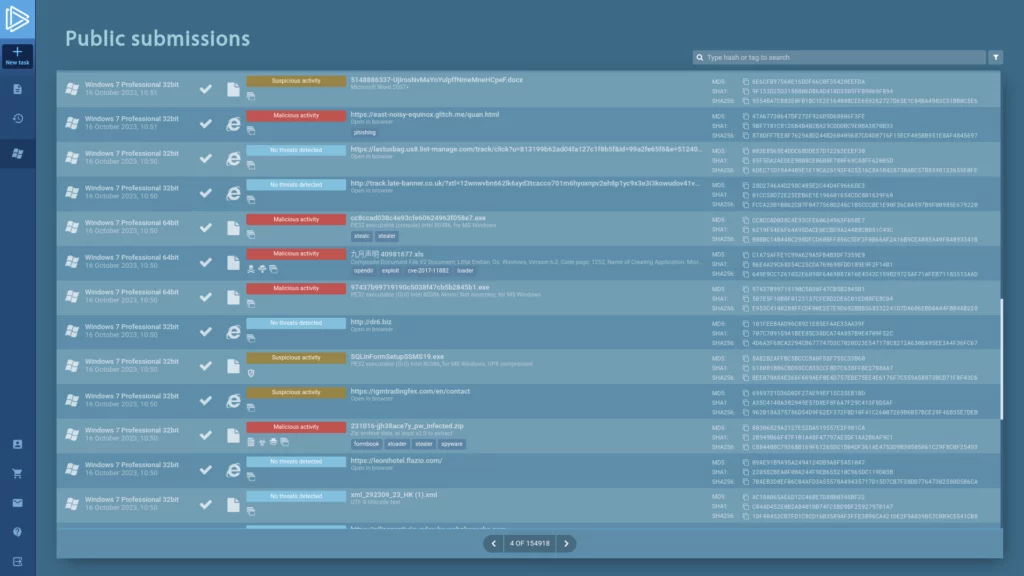
In addition to analyzing your own samples, you can access ANY.RUN’s database of over 6 million malware samples submitted by users from around the world.
Learn more: How to Get Free Malware Samples and Reports
Managing a team
All Enterprise-plan users can take advantage of the Teamwork feature that allows analysts to work together on different samples in real time.
It makes it easy to monitor your team’s activities and train junior analysts. It is also a great way to track productivity and manage large, dynamic teams.
Here are some of its benefits:
- Real-time collaboration: Analysts can join their forces, saving time and improving accuracy.
- Common analysis history: Team history can be configured to show all analyses, only the leader’s analyses, or only links to the leader’s analyses.
- Employee activity tracking: Team leaders can view employee activity, which can help them identify areas where training or extra resources are needed.
- Subscription management: Team leaders can manage subscriptions and assign licenses to team members.
Learn more: Teamwork
Using Live Attack Data from 15K SOCs in Threat Intelligence Lookup
Threat Intelligence Lookup is ANY.RUN’s key solution for working with threat intelligence. It simplifies and accelerates different stages of malware investigations, from proactive monitoring to gaining insights for incident response. As a result, you get to ensure a better defense against cyber threats for your company.
In practice, this means that TI Lookup provides you with Indicators of Compromise (IOCs), Attack (IOAs), and Behavior (IOBs). It not only links each indicator to an attack or sample but also showcases its behavior inside the sandbox.
The source of indicators is unique: all data comes from millions of malware analysis sessions done in ANY.RUN’s Interactive Sandbox. TI Lookup allows you to tap into it to gain invaluable insights into real threats targeting 15,000 companies in finance, manufacturing, transportation, government, and other industries right now.
Conclusion
ANY.RUN’s Interactive Sandbox is your best solution for both static and dynamic malware analysis.
Run an unlimited number of analyses, explore millions of reports and malware samples, and collect valuable data by studying the ins and outs of malicious programs and links.
With our cloud-based sandbox, your threat investigations will become a walk in the park.
About ANY.RUN
Over 500,000 cybersecurity professionals and 15,000+ companies in finance, manufacturing, healthcare, and other sectors rely on ANY.RUN. Our services streamline malware and phishing investigations for organizations worldwide.
- Speed up triage and response: Detonate suspicious files using ANY.RUN’s Interactive Sandbox to observe malicious behavior in real time and collect insights for faster and more confident security decisions.
- Improve threat detection: ANY.RUN’s Threat Intelligence Lookup and TI Feeds provide actionable insights into cyber attacks, improving detection and deepening understanding of evolving threats.
Request trial of ANY.RUN’s services to see how they can boost your SOC workflows








0 comments