If you have been using our malware hunting service for a while, you have probably seen tags and indicators that appear during the analysis. Usually, these interface elements are quite self-explanatory, however, some of them might not be immediately obvious.
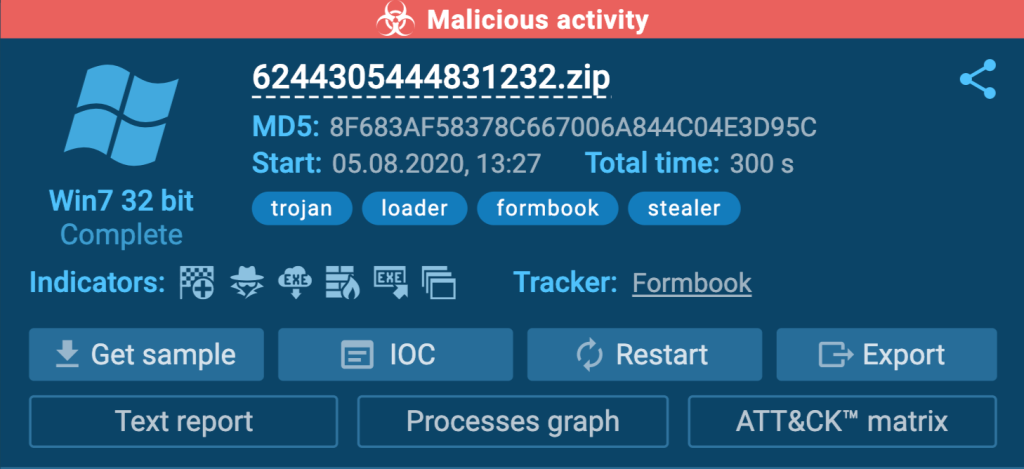
Every tag and indicator that appears on the screen carries important information, that’s why it is crucial to understand each one. Let’s go over the most commonly used tags and indicators that researchers come across during studies.
Tags in ANY.RUN
We use tags to highlight malware types and software features. Tags can also be used to search in public submissions to find similar samples are analyses. Let’s divide tags into multiple groups to add a little structure and make memorizing them a little easier.
Malware and Malware Family Tags
These are the most obvious tags that you should already be familiar with at this point. They highlight to which family a malware sample belongs, or point at the malware name.
Here are some examples of malware family tags:
- trojan
- stealer
- keylogger
- loader
- ransomware
- installer
- and others
And here are some examples of malware name tags that you will see when working with ANY.RUN:
- azorult
- bladabindi
- dharma
- dreambot
- emotet
- gandcrab
- and more
We are not going to list every tag here, because there are over 400 of them. However, keep in mind that when an analysis or a sample is marked with a tag from this group, this is a clear and certain indication that you are dealing with a malicious program.
Macros Tags
While tags from the previous group are a definite indication that a program is malicious, some tag groups show that you should approach a sample with suspicion. One such group is macros tags:
- macros
- macros-on-close
- macros-on-open
A macro is a user-defined rule or action algorithm. Macros are typically used to perform routine actions in Microsoft Office files. When launching a macro, the user starts a predefined chain of actions within the program. This could be interactions with the menus, mouse clicks, and virtual keyboard presses.
A macro on itself is completely legitimate and could be harmless. In fact, it probably won’t be an overstatement to say that all advanced users of programs like Microsoft Office use macros daily. However, for a security researcher, a macro is a clear red flag. It is no secret that hackers have been using macros to secretly install malware on targeted machines for years.
Note, that the macros-on-close tag indicates that the macro executes when the user closes the document, while macros-on-open executes when the user opens the file.
The OLE Tag
A similar tag to macros is the ole-embedded tag.
Object Linking & Embedding or OLE is a proprietary technology developed by Microsoft. OLE enables users to create embedded links to documents or objects in a file. The technology works similarly to macros and can also be used with malicious intent.
Potentially Unwanted Programs (PUP) Tags
Potentially unwanted programs are those that the user wilfully installs, disregarding that the program is of no use. An example of a PUP is adware or other spam-related software that comes bundled with a program which the user actually wants.
Software like this can be used to gain remote control over a system or simply show ads. However, these tags are also important for malware analysis.
This group includes the following tags:
- lavasoft
- pup
- teamviewer
- unwanted
- pua
Maldoc Tags
A Maldoc is a short term for a malicious document. Hackers have been using infected documents to spread malware for a while now. However, cybercriminals are constantly changing and improving their lures.
In ANY.RUN, we have created around 50 maldocs and classified them by similarity. Different malicious docs are known to spread specified malware samples, however, since threat actors constantly modify their attack vectors maldocs rarely stay the same for long.
When you encounter the maldoc tag, you can be one hundred percent certain that you are dealing with a malicious document. Some of the most commonly encountered maldoc tags are:
- maldoc-21
- maldoc-47
- emotet-doc
- ta505
The Emotet-doc tag indicates a file that spreads the Emotet Trojan, while the ta505 tag points at maldocs that are used by the та505 cybergang, who spread Dridex, Flawedammyy, and Trickbot malware.
Phishing Tags
These are the tags that indicate documents and websites that can mislead users by their appearance and thus steal personal information. Some commons examples of tags from this group are:
- phish-pdf
- phish-microsoft
- phish-onedrive
- phish-outlook
CVE Tags
CVE or Common Vulnerabilities and Exposures is a term that describes a record format for known vulnerabilities in a public database. Each CVE entry contains a number, description, and a set of links to references and useful resources. In ANY.RUN, CVE tags are added to malware that can utilize the corresponding vulnerabilities. Some examples of common tags in this category are:
- CVE-2017-11882
- CVE-2018-4878
The Obfuscated Tag
Code obfuscation is a practice of deliberately creating code that is hardly readable by humans intending to hide the true intent of the program or code logic. As such, the obfuscated tag points at programs that employ this practice.
By itself, code obfuscation is not illegal and sometimes it is even used for security purposes. However, since it is also commonly used by threat actors any sample marked with this tag is suspicious at the least.
The Exploit Tag
An exploit is a code that uses a known vulnerability or a weak spot in the cyber defense. Exploits are usually created with malicious intent, however, they can also be written by cybersecurity professionals for penetration testing.
Exploits can be utilized to infiltrate a network, gain elevated access, or drop malware onto infected machines.
The Generated-doc Tag
This tag indicates documents that were generated by a program. A common trait of such documents is that timestamps for file creation, editing, and adding information are identical, which would be completely impossible if the file was created by a human. After all, we can only perform these actions consequently. A lot of malware samples create files and directories, which means that security researchers should pay additional attention to automatically-generated files.
The Opendir Tag
Many websites today contain directories that are open by mistake or by design. Unfortunately, open directories often become compromised by criminals. Threat actors use them to spread malicious content or store stolen data.
Tasks that are marked with this tag may contain a malicious document. Additional, it can be a good idea to search open directories for signs of malware or analyze their content to determine what kind of data a certain malware sample may be stealing.
Indicators in ANY.RUN
Along with tags, ANY.RUN also uses a set of visual indicators. These are icons that provide important information during analysis. Indicators can show events, execution stages, and processes. Here is a full list of indicators that the service uses:
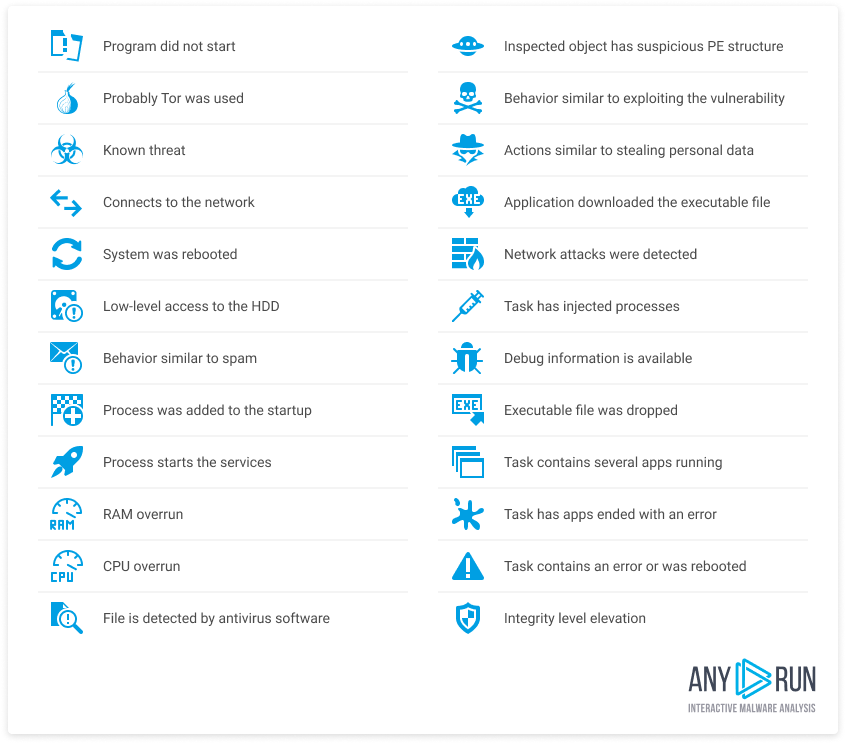
Conclusion
Memorizing the tags and indicators listed in this article will help to streamline the workflow and make malware analysis with ANY.RUN even faster. Since ANY.RUN has to use hundreds of tags to list every known malware family and strain there is a lot to keep in mind.
That’s why if you still feel uncertain about a certain tag or icon, don’t hesitate to contact our support team or message us through our social media pages and we will be happy to explain everything in detail.
3 comments








Good write-up, I am regular visitor of one’s website, maintain up the nice operate, and It’s going to be a regular visitor for a lengthy time.
Ok with the presentation of the tags but how can I add tags by myself ?
Hi there! You can add a custom tag to any of your own finished tasks. Look for the “add tags” button in the top right corner menu right next to the existing tags.