Editor’s note: The current article was originally published on March 29, 2022, and updated on January 3, 2024.
Memory dump extraction and YARA matching are powerful detection methods for known malware families. What’s more, they can reveal detailed information about malware injected into the memory of system processes.
But extracting malware configuration is not easy. Unless you do it with ANY.RUN.
How memory dumps improve detection rate
One of ANY.RUN’s main advantages lie in its simplicity, interactivity, and speed. Any user can analyze even complex malware nearly instantly. Simply loading a sample and hitting the “run” button already gives you structured data with little manual work.
But there are cases when you need to dive into a deeper analysis of samples.
One of such tasks is malware’s memory analysis. Extracting malware configuration from memory in itself requires a wide set of skills. Our goal is to streamline this process and help you retrieve and decrypt data on the fly, improving your productivity.
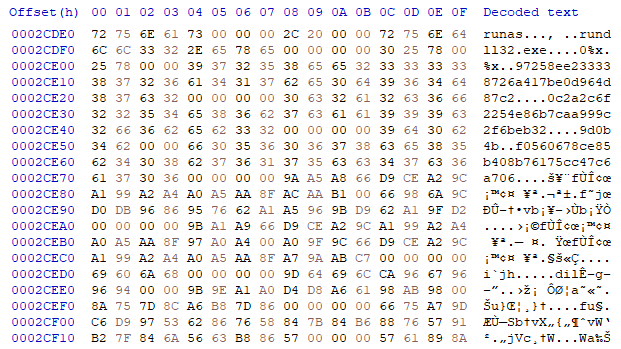
A part of the memory dump with the beginning of Amadey’s version 2.50 encoded config
- Memory analysis is carried out with the help of dump extractions from specific regions of executed files.
- After that, we detect a malicious program using a set of the YARA rules.
- Then, we employ algorithms designed for its analysis and configuration extraction if known malware is identified.
Memory dumps extracted by ANY.RUN and our YARA scanner effectively detect various anomalies such as encrypted strings, packers, anti-debug, and anti-sandbox techniques, etc.
Why extract malware configs?
Malware configurations are crucial for identifying all types of Indicators of Compromise (IOCs), which are then used for detection purposes. They also aid in understanding how malware is configured to execute and its functional capabilities.
Configuration feature: the key to the endless internal malware features
In cybersecurity, understanding typical behaviors of malware families is essential. Each family typically adheres to a pattern established by its creator, with individual files following this blueprint. The behavior of these malware instances varies based on the settings defined in the initial build. For instance, a malicious object might send data to an email, a server, use messengers, or a combination of these, all contingent upon its configuration settings.
That said, modern malware, such as Arkei, has evolved to exhibit a modular nature.
This allows the addition of new components — like keyloggers, banking modules, or miners — to the initial build, altering the malware’s behavior. The configurations of these modules, which store all customization options, play a crucial role. When extracted, they enable cybersecurity specialists to predict and understand the behavior of malicious objects, possibly even before they initiate harmful activities or after their command servers become inaccessible.
Consider this Remcos sample that no longer connects to its C2 server. Despite this disconnection, its configuration can still be analyzed.
Configurations also help you catch details that would have been missed otherwise. For example, in a malware with ten C&C servers, if the first server responds, the subsequent ones might remain undiscovered, as often seen with Emotet. This malware typically transmits data to the first IP address, obscuring the others when monitoring network traffic. Configuration extractors are invaluable in such scenarios, revealing hidden details without requiring active malware engagement.
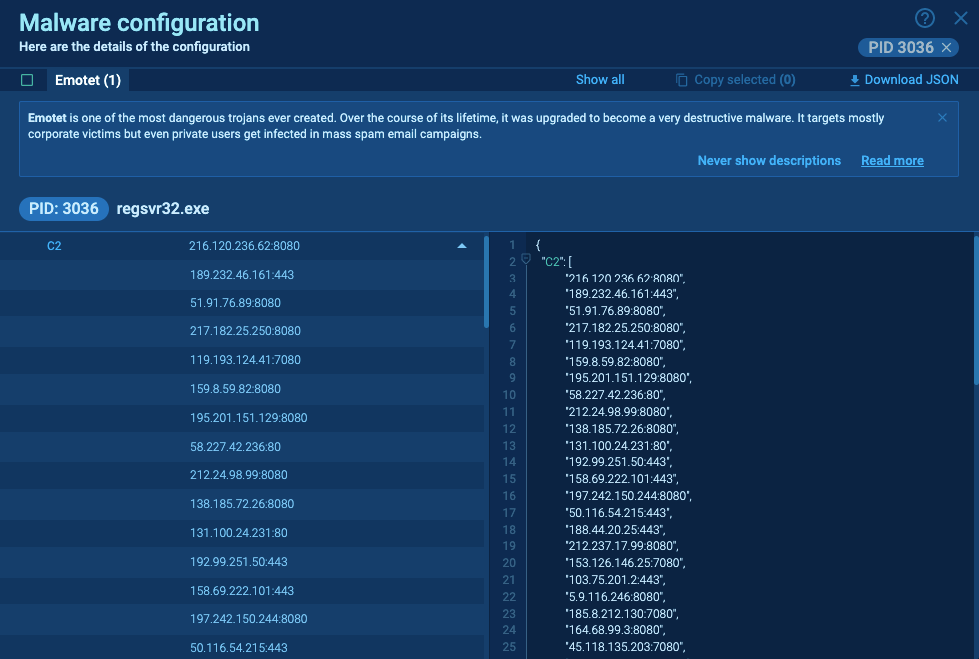
Take Trickbot as another example. It employs delay tactics, like lengthy mathematical calculations, to postpone its activity. While Trickbot may only start network activities, such as connecting to a C2 server, after a 300-second delay, tools like ANY.RUN can detect and extract its configurations in as little as 100 seconds.
Given the multitude of malware families, our strategic approach focuses on the most prevalent ones, as per distribution statistics. According to our Malware Trends Tracker, there are roughly 50 widespread families. This helps us monitor more targeted APTs and popular MaaS operations which you’re most likely to encounter as a security specialist.
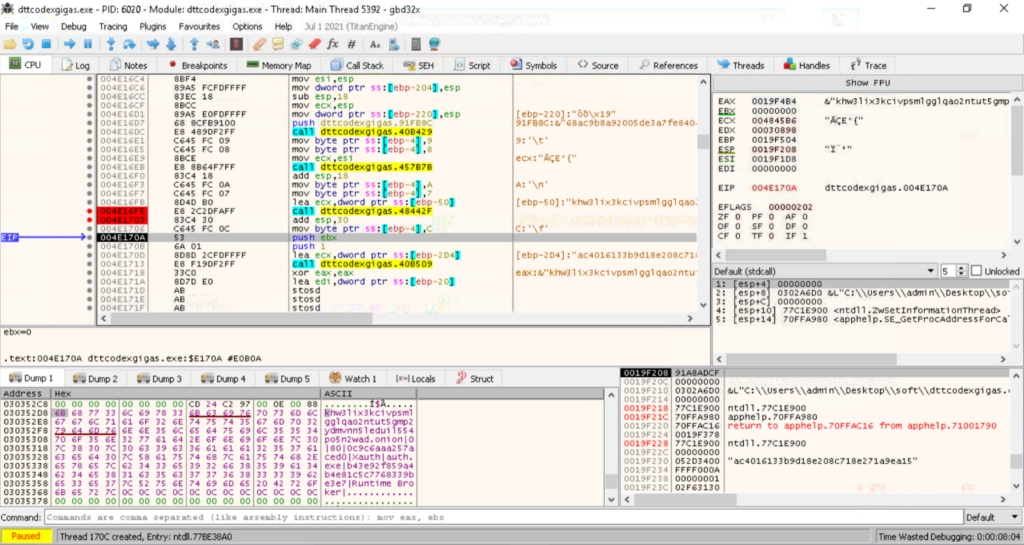
Malware analysis often involves delving into a sample’s memory dump, reversing, and debugging it. This process, especially for complex codes like those in Emotet, can be time-consuming. However, understanding and extracting malware configurations streamline this task, offering quicker and more efficient insights into the malware’s potential behavior and impact.
Automating malware config extraction with ANY.RUN
Extracting malware configurations is a repetitive but crucial task for researchers. It involves delving into the memory dump of a malware sample, then reversing and debugging it to understand its behavior and structure. This can be particularly time-consuming with complex malware like Emotet, known for its bloated code.
Good news is that in many cases you don’t need to do it manually. ANY.RUN can extract configs for 90% of the most well-known malware.
For instance, today alone, there have been numerous AgentTesla uploads, and configurations for all active samples are already available.
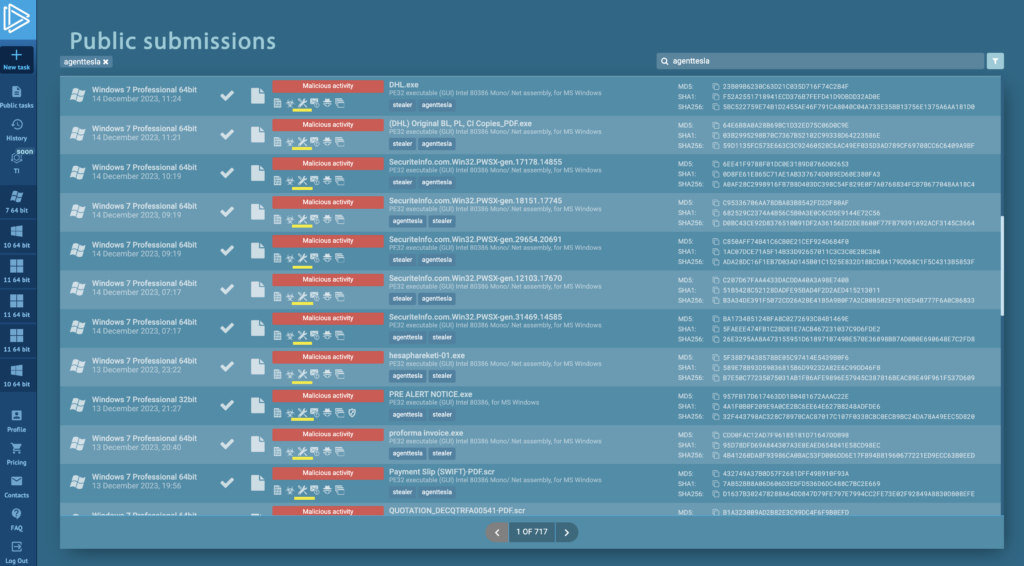
These can be accessed in our public submissions under “Emotet samples with configurations.” As of this writing ANY.RUN offers over 50 extractors. Here are some of the highlights:
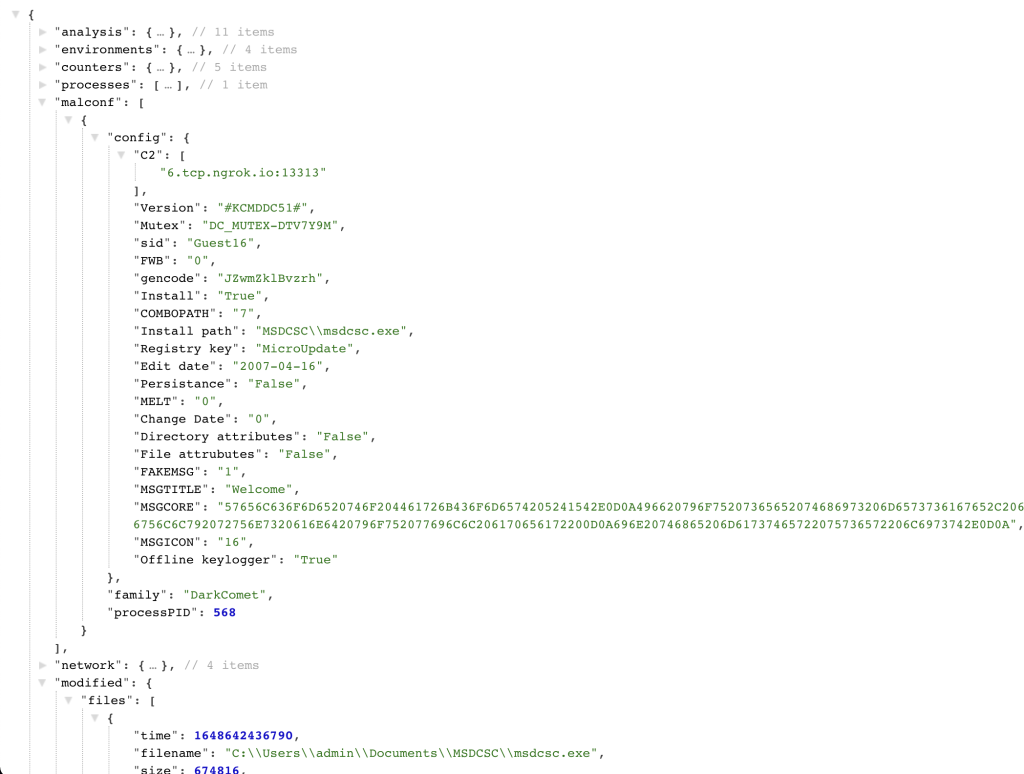
The system displays the following malware configurations:
- An IP address and a port to connect to a C2 server
- The current sample name
- A malware family name, type, and version
- A campaign ID
- Encryption keys
- Number and types of sub-modules
- Anti-debugging, anti-sandbox, and other anti-evasion methods
- Mutex
- DGA seeds
- The targeted OS version
- Domain names and URL lists
- Other options
But keep in mind that different malware families will show various sets of characteristics. Sometimes it can only be the IP addresses of the C2 server with the port, login, and password for the connection.
Guide to using ANY.RUN’s Malware Configuration interface
Let’s delve into the specifics of ANY.RUN’s malware configuration reports.
The interface is divided into three functional areas:
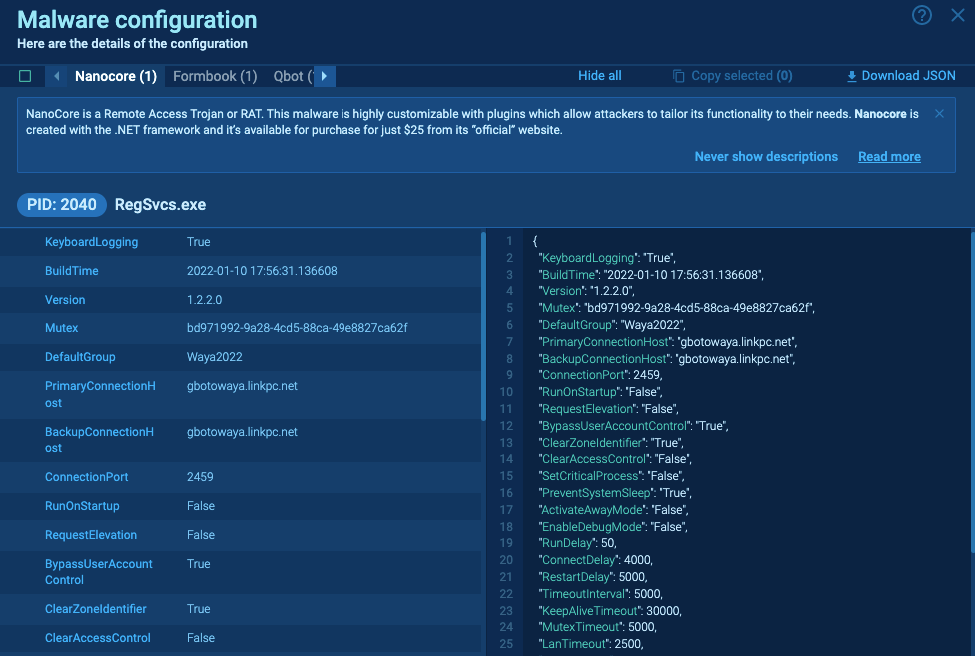
- Process Navigation: Located at the top, this section lists detected malware families within the sample. It includes all variants, even if there are several builds of the same family. A concise description of the malware is displayed here, with options to visit Malware Tracker for more details and the latest IOCs.
- Information Panel: This is split into two parts. On the left, there’s a list where you can select and copy the necessary data. The right side caters to specialists requiring data export in JSON format. A tooltip guide for further information is available and can be accessed by clicking the question mark.
- Malware Configuration Access: You can find the malware configuration in the info panel either after the task is completed or in real-time. The CFG tag next to the process allows you to work with IOCs immediately, without having to stop the analysis or wait until the end of the task.
Malware configuration can be found on the info panel after the task is finished or in real-time by the CFG tag next to the process, which is quite convenient.
Using ANY.RUN’s API to quickly get IOCs
The API feature in ANY.RUN provides a quick way to gather IOCs. This is particularly useful when you have to deal with a large number of files, like receiving hundreds in a spam campaign. You have two main options for analysis:

It takes 15 seconds from the moment of sending the executable file till the final results with IOCs. 15 seconds for everything!
Conclusion
Help us expand our threat coverage even more. Here’s how you can contribute:
- Let us know which malware families you encounter often, and We’ll consider adding them.
- If you spot any issues with our extractors, please tell us.
- Need specific data for your work? Feel free to share your requirements in the comments below.
Also, if you discover a new malware version that isn’t in our database yet, email us at [email protected].
A few words about ANY.RUN
ANY.RUN is a cloud malware sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams. Every day, 300,000 professionals use our platform to investigate incidents and streamline threat analysis.
Request a demo today and enjoy 14 days of free access to our Enterprise plan.
1 comments










Very nice features!