Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


Crocodilus is a highly sophisticated Android banking Trojan that emerged in March 2025, designed for full device takeover. Disguised as legitimate apps, it steals banking credentials, cryptocurrency wallet data, and enables remote control, rapidly evolving into a global threat targeting financial users across Europe, South America, and Asia.
|
Trojan
Type
:
|
Unknown
Origin
:
|
|
1 March, 2025
First seen
:
|
22 October, 2025
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 March, 2025
First seen
:
|
22 October, 2025
Last seen
:
|

 807
807
 0
0

 488
488
 0
0

 2743
2743
 0
0
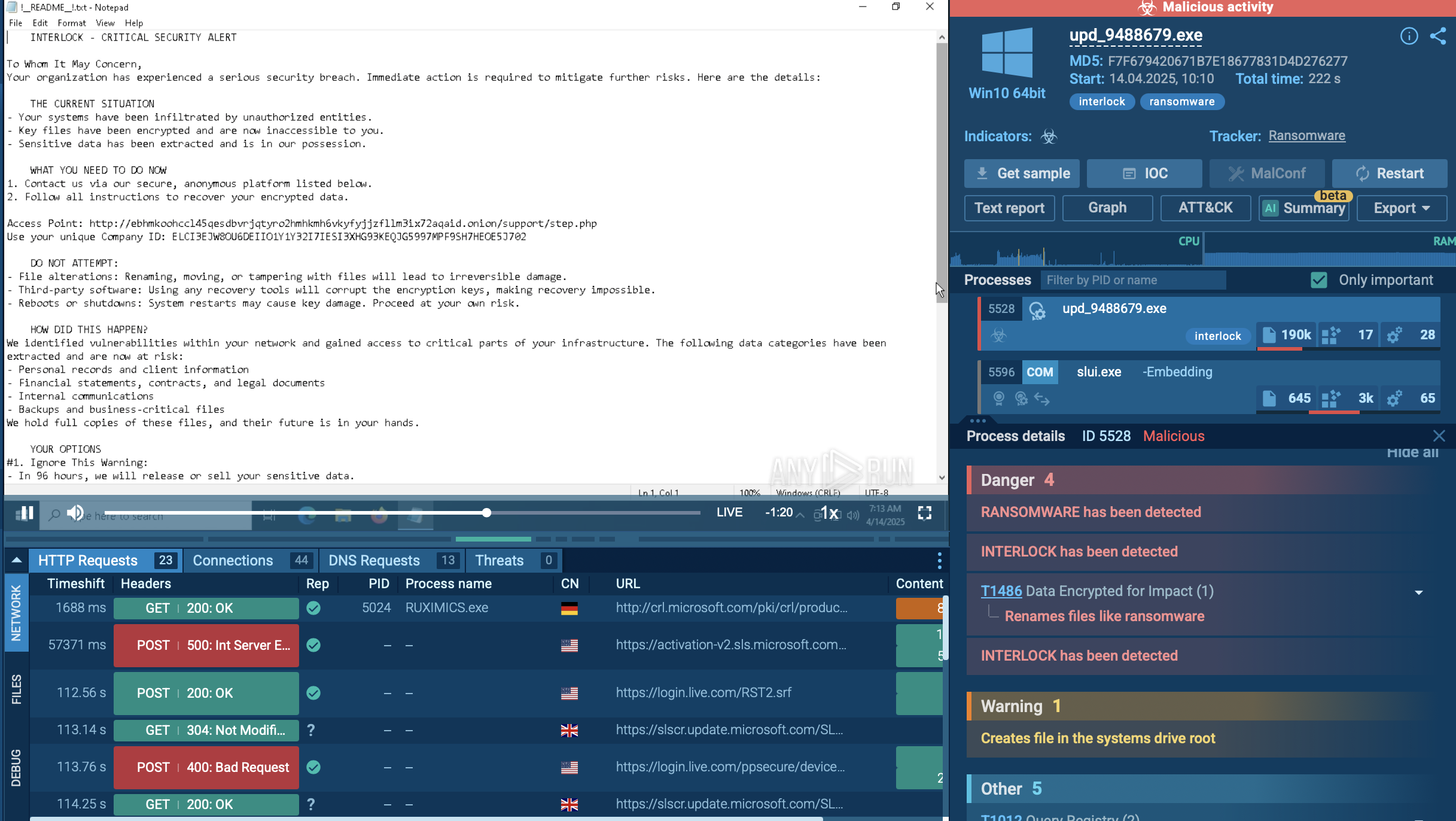
View Crocodilus detonations in ANY.RUN’s Interactive Sandbox to see malicious processes and network connections and understand how the malware acts:
 Crocodilus processes detected in the sandbox analysis
Crocodilus processes detected in the sandbox analysis
Social engineering remains the critical vulnerability: despite technical sophistication, Crocodilus succeeds primarily through convincing social engineering: fake ads, urgent warnings, and trusted caller ID spoofing. Security awareness training focused on mobile-specific threats is essential for both individuals and organizations.
Crocodilus is a sophisticated Android banking Trojan that emerged in early 2025, representing a new generation of mobile device-takeover malware. Unlike simpler malicious apps, Crocodilus arrives fully equipped with advanced capabilities including overlay attacks, keylogging, remote access, and hidden remote control features.
It specifically targets banking applications and cryptocurrency wallets, using social engineering tactics to deceive victims into surrendering their most sensitive credentials. Since its discovery, Crocodilus has rapidly evolved and expanded globally.
The malware employs a multi-layered approach to compromise devices, beginning with a proprietary dropper that bypasses Android 13+ security restrictions. Once installed, it requests Accessibility Service permissions, which grants it extensive control over the device.
The malware operates by continuously monitoring app launches and displaying fake overlays to intercept credentials when victims attempt to access legitimate banking or cryptocurrency applications. What distinguishes Crocodilus is its "Accessibility Logger" feature, which goes beyond traditional keylogging by capturing all accessibility events and screen elements, effectively recording everything displayed on the victim's device.
Crocodilus includes remote access trojan (RAT) capabilities that allow attackers to take complete control of infected devices. The malware can display black screen overlays during fraudulent activities, effectively hiding actions from victims while muting device sounds to prevent detection. The malware communicates with command-and-control (C2) servers to receive instructions, download target lists, and exfiltrate stolen data.
Recent variants have introduced even more sophisticated features, including the ability to modify contact lists by adding fake entries that appear as legitimate bank support numbers, and automated seed phrase collectors that use regular expressions to extract cryptocurrency wallet credentials directly from the screen content.
Crocodilus infiltrates via social engineering-driven droppers distributed through:
Spread relies on C2 orchestration for global campaigns, with no peer-to-peer replication observed. Evolution includes 17+ dropper families for broader compatibility.
Crocodilus primarily preys on Android users engaged in financial activities, with campaigns tailored to specific demographics and regions. Initial attacks focused on Spain and Turkey, targeting users of major banks like BBVA and Garanti BBVA, as well as cryptocurrency wallets. By June 2025, its reach expanded to Poland (via ads targeting users over 35), South America (Argentina and Brazil), and broader Europe, including digital banks in the US, Indonesia, and India.
Notable campaigns:
Crocodilus operates through a multi-stage infection and control process: Stage 1: Initial Installation The malware uses a proprietary dropper application designed to bypass Android 13+ security restrictions. This dropper disguises itself as a legitimate application, often mimicking banking apps, browsers, cryptocurrency tools, or utility applications.
Stage 2: Permission Acquisition Upon installation, Crocodilus immediately requests Accessibility Service permissions. These permissions grant the malware extensive control over the device's user interface and ability to interact with other applications. The malware uses deceptive messaging to convince users to grant these dangerous permissions.
Stage 3: Command and Control Establishment Once permissions are granted, the malware connects to its C2 server to receive operational instructions. This includes downloading lists of target applications (banks and cryptocurrency wallets to monitor) and the corresponding fake overlay screens to deploy.
Stage 4: Continuous Monitoring Crocodilus runs persistently in the background, monitoring which applications the user launches. When a target application is opened, the malware springs into action.
Stage 5: Credential Interception When victims attempt to log into targeted banking or cryptocurrency applications, Crocodilus displays a fake overlay screen that perfectly mimics the legitimate login interface. Users unknowingly enter their credentials into the malicious overlay, which immediately transmits this data to attackers.
Stage 6: Data Exfiltration The malware's accessibility logger captures all screen content, including sensitive information like account balances, transaction details, two-factor authentication codes from Google Authenticator, and cryptocurrency wallet data. For cryptocurrency wallets specifically, the malware employs social engineering to trick users into revealing their seed phrases.
Stage 7: Remote Control Attackers can initiate remote control sessions, taking direct control of the infected device. During these sessions, the malware can display black screen overlays and mute sounds, hiding fraudulent activities from the victim while attackers execute unauthorized transactions, transfer funds, or steal additional information.
Stage 8: Advanced Manipulation Recent variants add fake contacts to the victim's contact list, enabling attackers to call victims while appearing as legitimate bank support or trusted entities. This facilitates additional social engineering attacks and helps bypass fraud prevention systems that flag calls from unknown numbers.
ANY.RUN’s Interactive Sandbox supports the detonation and analysis of mobile malware and lets observe its behavior on an actual Android device. Just select an OS in the VM settings on the analysis launch:
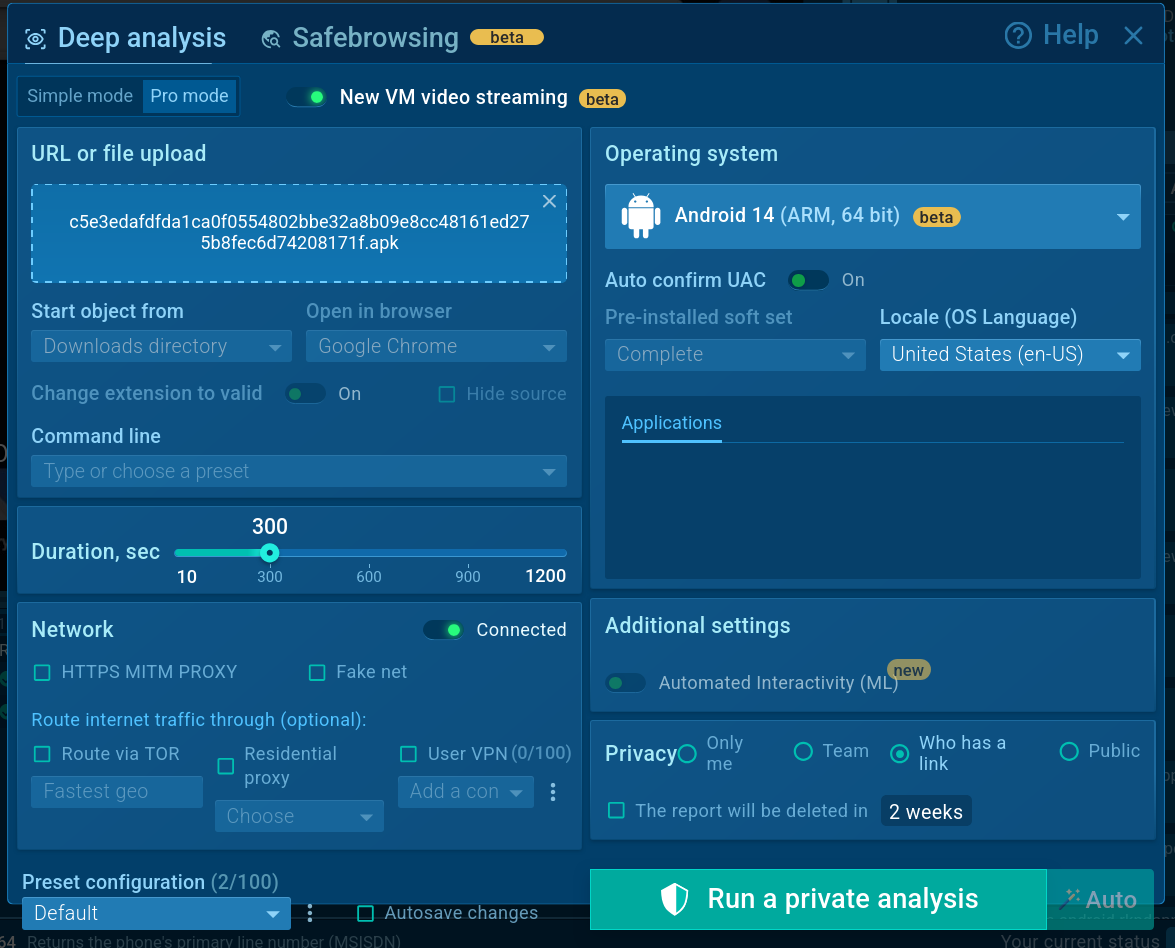 Set up virtual environment selecting an Android OS
Set up virtual environment selecting an Android OS
A Crocodilus sample sandbox analysis demonstrates its signature TTPs like network discovery, evasion, and encryption.
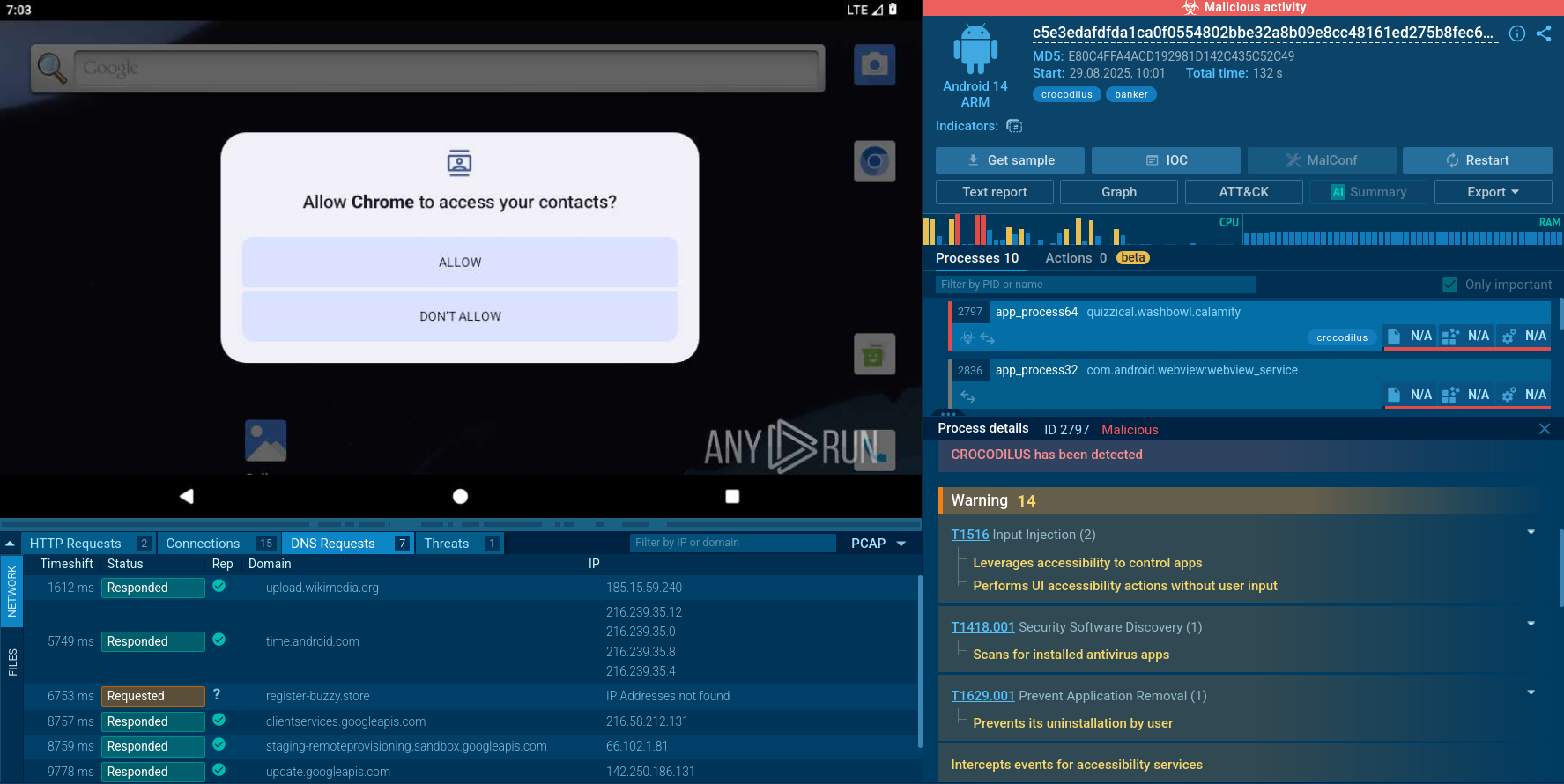 Crocodilus in action in the safe Interactive Sandbox environment
Crocodilus in action in the safe Interactive Sandbox environment
The malware performs network reconnaissance, extracting the phone number and the name of the current network operator, which allows it to adapt attacks to a specific user and region.
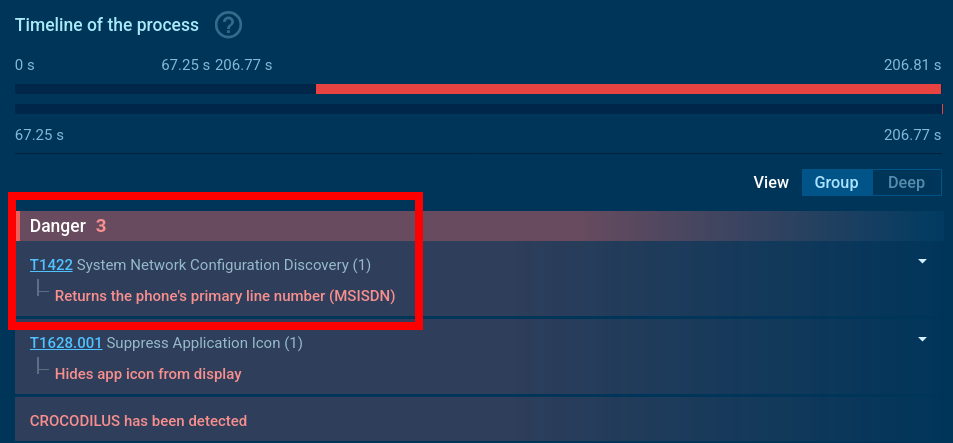 Crocodilus explores network configuration
Crocodilus explores network configuration
The analysis shows the use of cryptographic APIs for data encryption, which helps protect transmitted commands and stolen information from interception.
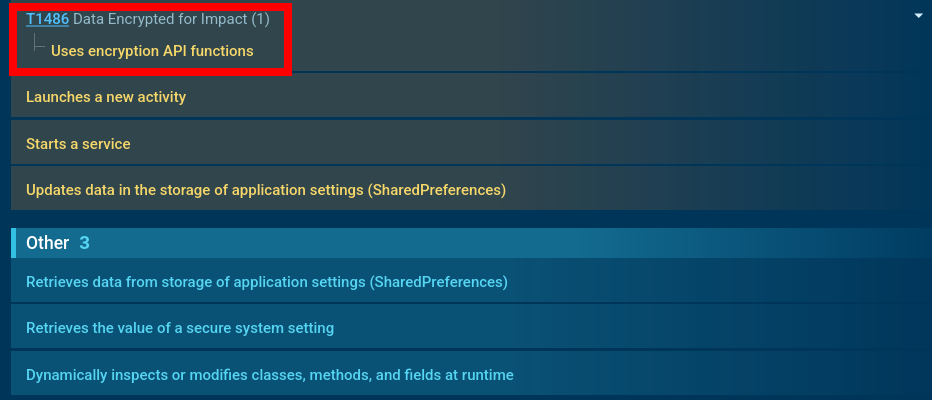 Crocodilus encrypts stolen data
Crocodilus encrypts stolen data
Crocodilus stores its configuration in the SharedPreferences system storage in XML format, where parameters such as the URL of the command server determine the behavior of the malware.
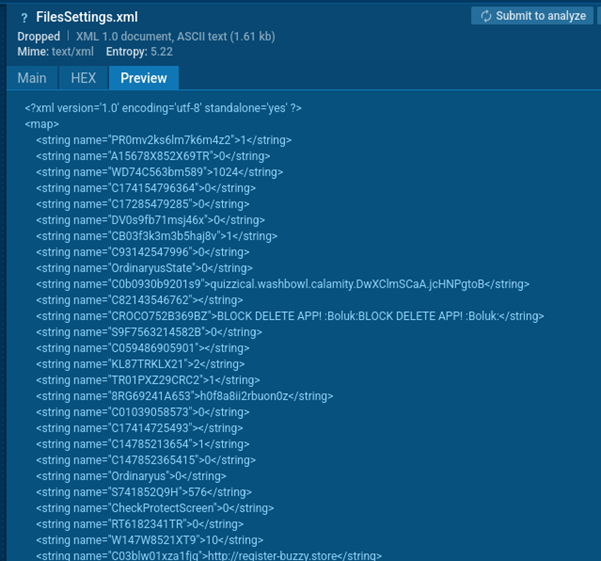 Crocodilus’ configuration file
Crocodilus’ configuration file
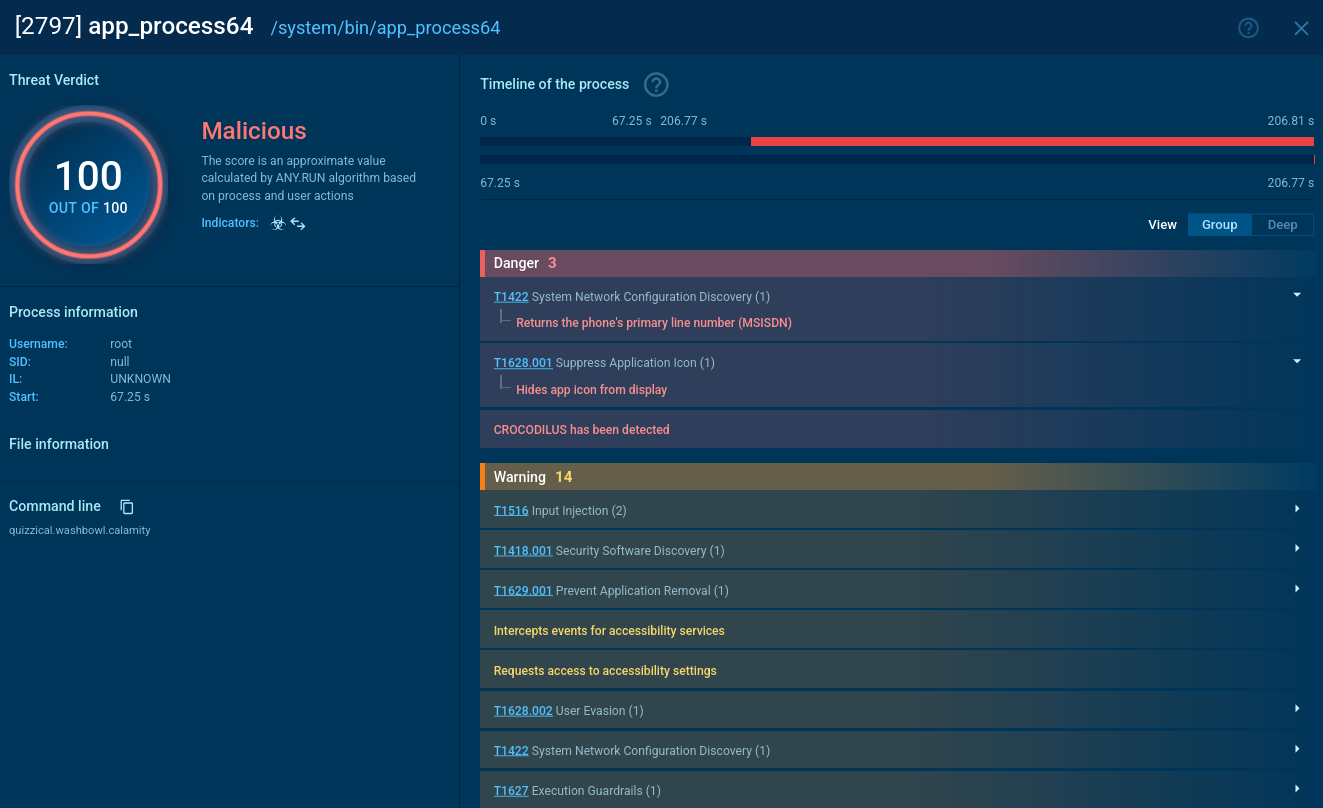
To remain stealthy, Crocodilus hides the application icon from the screen and blocks deletion attempts by intercepting events in Android settings. Besides, it requests access to accessibility services and intercepts their events, allowing interface manipulation without user input. The malware uses accessibility to control applications, automatically performing actions such as button taps, for privilege escalation and overlay attacks.
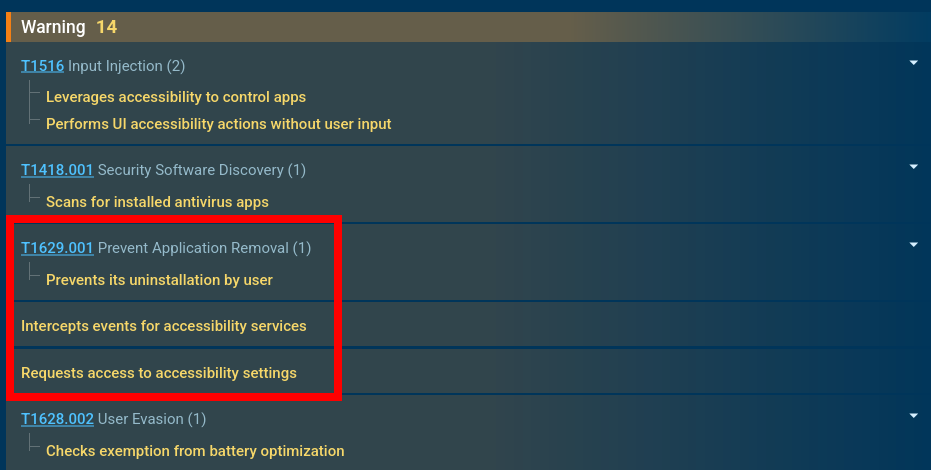 Crocodilus develops its persistence and privileges
Crocodilus develops its persistence and privileges
Keylogging through screen capture is implemented as an Accessibility Logger. The malware monitors all accessibility events, capturing elements displayed on the screen, including user’s text input. This allows recording not only keystrokes but also dynamic content, such as one-time passwords from applications like Google Authenticator.
Overlay attacks are the main tool for stealing credentials. When a user launches a target application, such as a banking or crypto wallet, the malware overlays a fake screen on top of the real one, imitating the login interface to capture logins and passwords.
While Crocodilus primarily targets individual users, its impact extends significantly to businesses and organizations through multiple attack vectors:
Bring Your Own Device (BYOD) Risks: If an employee's infected device accesses company banking applications, financial systems, or corporate accounts, the malware can compromise business financial assets.
Financial Fraud and Direct Losses: Organizations that conduct mobile banking or maintain cryptocurrency treasuries face direct financial theft.
Data Breach and Compliance Violations: Crocodilus captures sensitive business communications, credentials, and financial data. For organizations subject to regulations like GDPR, PCI DSS, or financial services regulations, such breaches can result in substantial fines, legal liabilities, and mandatory breach notifications.
Business Email Compromise (BEC) Enablement: By accessing business communications and contact lists on infected devices, attackers gain intelligence for BEC attacks. They can impersonate executives, understand business relationships, and craft convincing fraud attempts targeting other employees or business partners.
Reputational Damage: Organizations that fall victim to Crocodilus-enabled fraud may suffer significant reputational harm, especially if customer data or funds are compromised.
Supply Chain Threats: Infected devices used by vendors, contractors, or partners can serve as entry points into broader business ecosystems, potentially compromising multiple organizations through a single infection.
Threat intelligence provides specific technical indicators including file hashes, C2 server domains, malicious package names, and behavioral signatures. Security teams can integrate these IOCs into security tools, endpoint protection platforms, and network security devices to identify and block Crocodilus-related activity.
Start from querying Threat Intelligence Lookup with the threat name to find Crocodilus samples that ANY.RUN’s community of 500K professionals and 15K SOC teams has already analyzed. Study TTPs and gather IOCs:
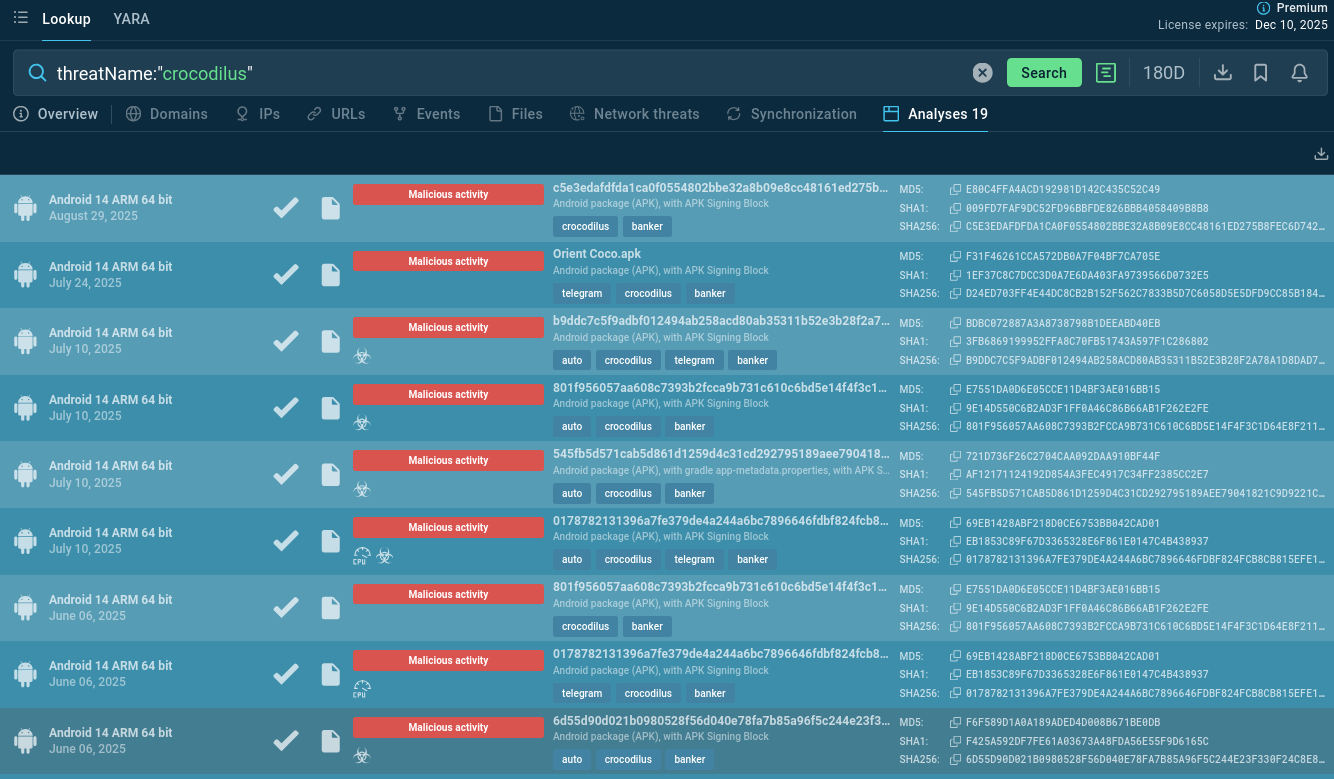 Crocodilus sandbox analyses found via TI Lookup
Crocodilus sandbox analyses found via TI Lookup
Add a country code to the request to see how actively Crocodilus samples has been recently analyzed by the Sandbox users from this country and suggest whether the region is heavily targeted right now. In this example, German does not seem to be under fire yet, which means local companies and users still have some time to prepare:
threatName:"crocodilus" AND submissionCountry:"de"
 Crocodilus samples submitted to the Sandbox from Germany
Crocodilus samples submitted to the Sandbox from Germany
Crocodilus exemplifies the accelerating arms race in mobile malware, blending RAT sophistication with global scalability to erode trust in digital finance. From its Turkish roots to worldwide bites, it demands a unified response: vigilant users, fortified apps, and shared intelligence. As Android's dominance grows, ignoring such threats risks financial chaos—but armed with awareness, we can clamp down before it snaps again.
Start gathering actionable threat intelligence on Crocodilus by signing up to ANY.RUN’s TI Lookup: protect your business with timely detection and response.