Threat hunting is widely recognized as one of the most important capabilities of a mature SOC. It uncovers stealthy attackers early, reduces dwell time, and prevents security incidents from impacting the business. Yet, in practice, many organizations find that their threat hunting efforts don’t consistently deliver these outcomes.
Let’s take a look at how high-performing security teams make threat hunting more repeatable, measurable, and effective.
Why Threat Hunting Programs Often Fail Before They Start
Most threat hunting teams are doing many things right. They understand attacker techniques, follow threat intelligence reports, and rely on established frameworks. Even so, translating this knowledge into reliable detections can be harder than expected.
The challenge is rarely about analyst skill or methodology. More often, it comes down to the lack of rich, current, behavior-driven intelligence that makes hunts actionable at scale.
Most teams operate with fragmented and incomplete inputs:
- Teams know attacker techniques but don’t see them in action: Without real execution data such as processes, files, registry and network behavior, TTP hunts stay theoretical and detections remain generic, leaving real business exposure undiscovered.
- Indicators come without context: IOCs alone don’t explain how attacks unfold, what happens next, or which assets are at risk, leading to late detection and higher incident impact for the business.
- Third-part threat reports cost more effort than they deliver value: Being outdated, fragmented, and too high-level, they slow down hunting and detection engineering, increasing the likelihood of incidents and response costs.
The result is predictable. Threat hunting consumes significant analyst time while delivering low ROI. Hunts take weeks, detections are rolled out with low confidence, and leadership struggles to see a clear business outcome.
What Ineffective Threat Hunting Means for the Business
When threat hunting fails, the security risks and expenses for companies start to grow, leading to:
- Later detection of active threats: Attacks are identified after user interaction, credential abuse, or persistence, expanding impact and recovery effort.
- Higher and less predictable incident costs: Delayed visibility forces broader containment, longer investigations, and extended recovery timelines.
- Unclear risk posture at the executive level: Leadership lacks evidence that proactive security efforts are reducing exposure, limiting informed decision-making.
- Inefficient use of security resources: Analyst time is spent on activities that do not measurably reduce incident likelihood or impact.
How to Make Threat Hunting Work in Your SOC or MSSP
Effective and scalable threat hunting starts with real attacker behavior, not theory. Teams build hunting ideas around how attacks actually happen today and continuously adjust them based on what they observe in real investigations.
This keeps threat hunting practical, repeatable, and aligned with what is actually happening in the threat landscape, rather than relying on abstract models or outdated intelligence.

This is where ANY.RUN’s Threat Intelligence Lookup proves to be essential for hundreds of SOC teams in companies across finance and transportation to technology and MSSPs in healthcare.
How TI Lookup Transforms Your Hunts for Maximum Business Impact
TI Lookup supports instant search across a vast database of threats and indicators. It is built on real-time attack investigations from ANY.RUN’s Interactive Sandbox, where 15,000+ SOC teams and 600,000+ analysts manually analyze live malware and phishing every day. Each investigation immediately feeds fresh data into TI Lookup.
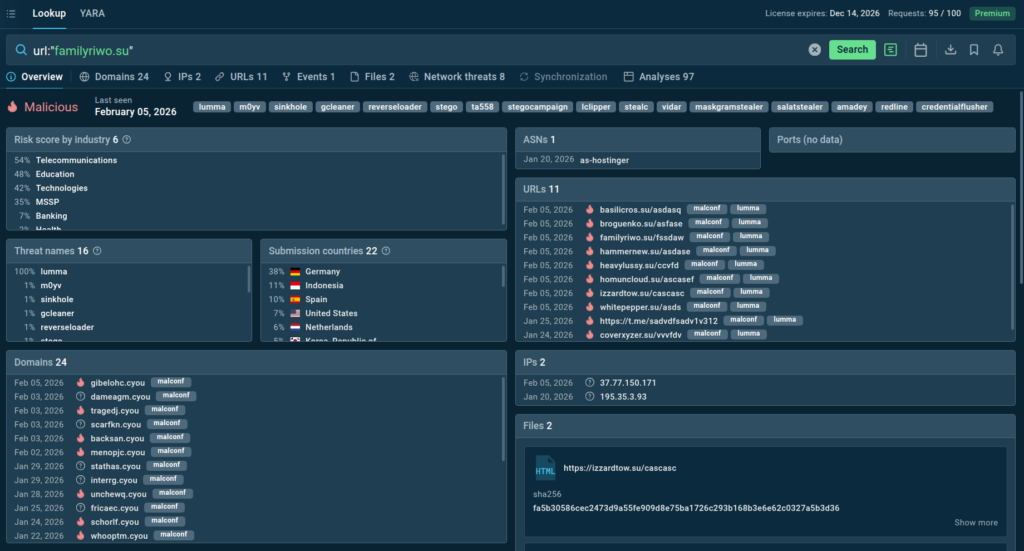
While most threat intelligence on the market is recycled from other sources, TI Lookup delivers original intelligence derived from live attack activity.
As a result, TI Lookup acts as a powerful starting point for hunters, giving them access to:
- Massive attack volume for broader threat coverage: Millions of real executions across industries, regions, and campaigns, expanding your SOC’s visibility and reducing blind spots.
- Near real-time freshness for faster business risk awareness: Intelligence appears hours after attacks are observed, not days or weeks later, enabling earlier risk assessment and response.
- 40+ types of indicators for higher detection rate: Rich telemetry, spanning IOCs, IOBs, and IOAs (from IPs and domains to registry keys and TTPs) is searchable and available to hunters in 2 seconds, reducing the chance of missed threats.
- Behavior-first context for quick prioritization: Every indicator is tied to an actual malware or phishing attack, helping teams quickly separate business-critical risk from low-impact noise.
- Integration with SOC tools for scalability: Thanks to ready-made connectors and API/SDK support, TI Lookup works seamlessly with SIEM/SOAR/TIP and other types of solutions.
By giving hunters direct access to real attacker behavior, TI Lookup turns threat hunting into a process that delivers measurable outcomes.
| Threat Hunting Stage | Without TI Lookup | With TI Lookup | Business Outcome |
|---|---|---|---|
| Hypothesis generation | Theoretical assumptions based on reports | Hypotheses validated against real attack executions from 15,000+ SOC teams | Up to 58% more threats detected through earlier and broader visibility into real attack activity |
| Indicator analysis | Isolated IOCs with limited context | Indicators enriched with behavioral and historical context from fresh malware and phishing | 36% higher detection rate with fewer false positives and faster analyst decisions |
| Technique exploration | Abstract MITRE techniques | Techniques observed in live attacks with full execution context | Improved coverage of evasive and low-noise attacks, reducing undetected exposure |
| Prioritization | Intuition-driven, hard to justify | Prioritized by active targeting by industry and geography | Security effort focused on threats that actually impact the business, not theoretical risk |
| Validation | Limited or post-deployment | Pre-deployment validation on real attack data, including large-scale YARA testing | 21-minute reduction in MTTR per case and lower incident and recovery costs |
By giving hunters direct access to real attack behavior from millions of sandbox sessions, TI Lookup turns threat hunting into a process that delivers measurable value for SOC performance and business risk reduction.
- SOC effort shifts from research to risk reduction: TI Lookup helps teams concentrate on threats that are actively used in real attacks, instead of spending time on low-impact hypotheses.
- Hunting turns into visible results: Instead of producing observations, threat hunting leads to clear decisions: what to investigate, block, monitor, or escalate.
- Threat hunting becomes a repeatable SOC process: With consistent context and validation, hunting no longer depends on individual expertise and produces predictable outcomes across teams and shifts.
- Business relevance is built into every hunt: Hunts are aligned with real attack targets and objectives, making their value clear for both SOC management and leadership.
- Threat hunting delivers measurable security impact: Earlier discovery of hidden threats reduces incident probability and justifies threat hunting as a cost-effective risk control.
TI Lookup enables SOC teams to validate and refine hunting patterns, understand which malware families and campaigns they truly correlate with, and prioritize threats based on real activity levels, affected industries, and geographic spread.
As a result, threat hunting becomes faster, more precise, and firmly grounded in observed attacker behavior rather than assumptions or isolated IOCs.
Earlier detection and better prioritization reduce incident likelihood, minimize response costs, protect critical assets, and allow security teams to focus resources on threats that pose real, measurable risk to the organization.
5 Use Cases for Intelligence-Driven Threat Hunting in Your SOC
Use Case 1: Turn MITRE Techniques into Detectable Attacks
Hunting problem
Teams know which MITRE techniques matter, but lack concrete data to build high-quality hunts.
How hunters usually struggle
They write generic detections based on technique descriptions, leading to noisy alerts and weak coverage.
How TI Lookup helps
Hunters can search directly by MITRE technique, for example T1036.003, one of the top techniques in 2025 according to ANY.RUN’s research. TI Lookup returns dozens of real attack executions, including processes, file artifacts, registry changes, and network activity.
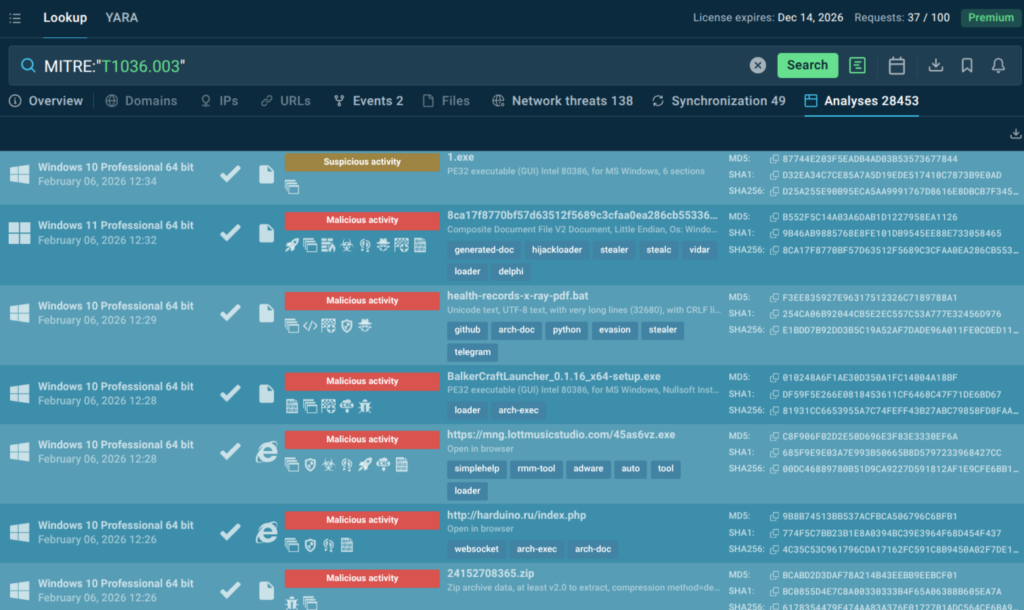
Click any of the links to view an analysis session, observe a malware’s detonation, and watch the technique you explore in action.
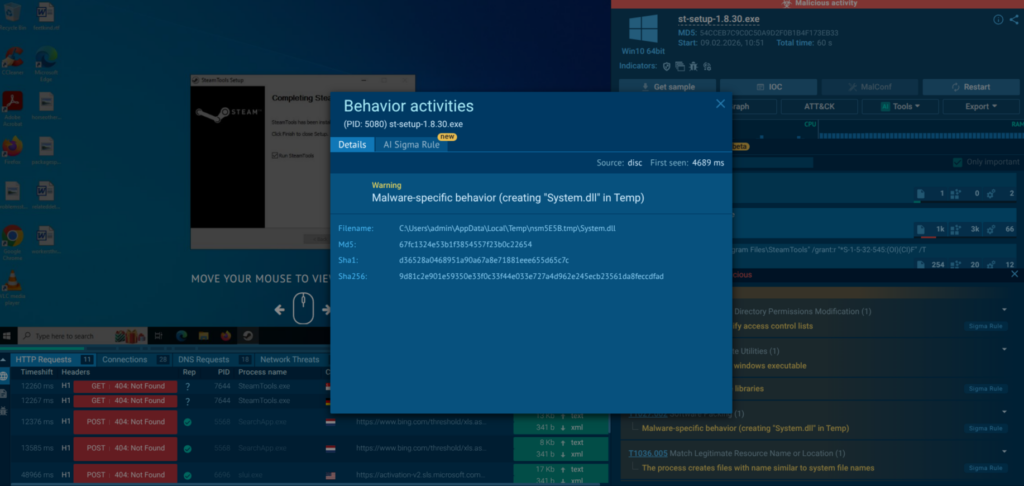
Instead of guessing how a technique might look, hunters see how it actually behaves in live attacks.
SOC / Business impact:
- More precise hunts based on observed adversary behavior;
- Fewer false positives due to less generic detection logic;
- Faster time-to-detection for new implementations of known techniques.
Use Case 2: Catch Relevant Threats while They’re Still Active
Hunting problem
Most security incidents escalate because detections lag behind fast-moving attack campaigns. By the time indicators are deployed, the campaign has already evolved and the business is exposed.
How hunters usually struggle
Teams rely on vendor reports and shared IOCs that arrive too late. By the time blocking rules are deployed, attackers have already rotated domains or delivery methods.
How TI Lookup helps
Hunters can validate campaign patterns against real, recent sandbox data.
For example, when tracking enterprise email phishing using fake Microsoft login pages, hunters can search for domain patterns to identify the latest malicious domains. Sandbox sessions reveal full attack chains and associated artifacts.
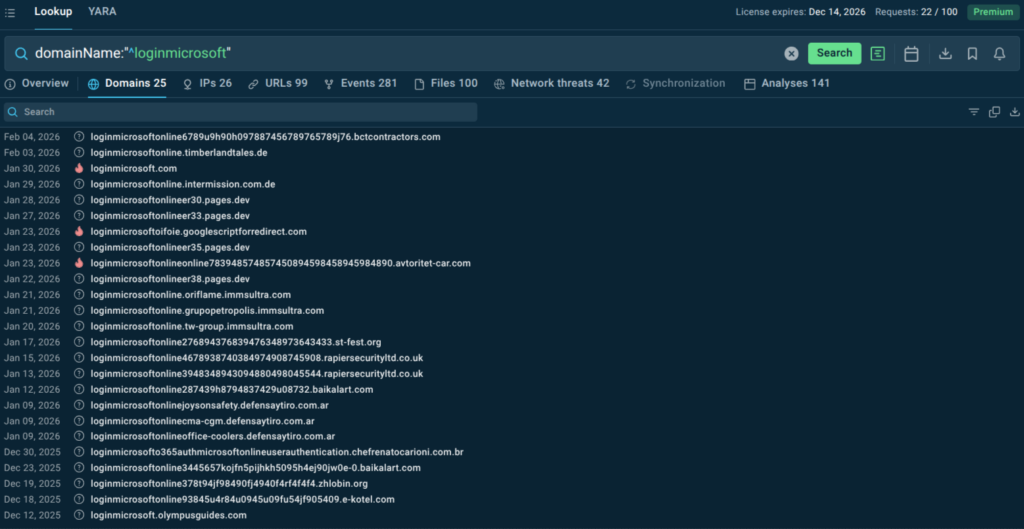
Correlation with malware families such as EvilProxy provides additional context. Collected data is immediately usable for detection updates.
SOC / Business impact:
- Earlier disruption of active campaigns;
- Higher confidence in detection updates with less post-deployment noise;
- Reduced risk of compromise thanks to timely blocking.
Use Case 3: Test YARA Rules Before They Flood Your SOC With False Positives
Hunting problem
YARA rules are powerful, but deploying them without proper validation often creates noise, blind spots, or both, directly impacting business security.
How hunters usually struggle
Rules are tested on limited sample sets, increasing the risk of false positives.
How TI Lookup helps
Test your YARA rule against millions of real malware samples before deployment and immediately see which samples it matches.
Examine the matched files to understand precisely what your rule detects. You can identify false positives early, refine your rule to be more specific, or broaden it to catch additional variants. This validation happens in minutes rather than weeks, and in a controlled environment rather than production.
See how it works on an example of an AgentTesla rule available in TI Lookup.
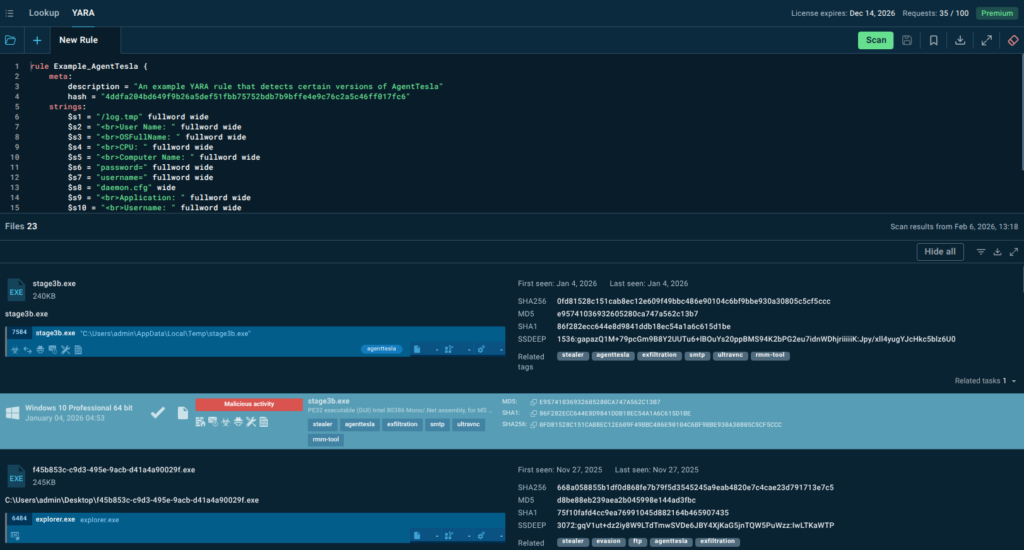
The rule targets the strings that Agent Tesla typically uses when building and sending stolen data reports (via email/SMTP, HTTP, Telegram bots, etc.). These strings come from the formatted logs or HTML-like reports the malware creates.
SOC / Business impact:
- Higher true positive rates for file-based detections;
- Reduced false positives that would otherwise waste analyst time;
- Confidence in detection coverage before production deployment.
Use Case 4: Hunt What Actually Threatens Your Business
Hunting problem
Your team has a backlog of potential hunting hypotheses, but limited time and resources. You need to prioritize based on what’s actually threatening your organization right now.
How hunters usually struggle
They rely on intuition or outdated threat reports, wasting time on low-impact scenarios.
How TI Lookup helps
TI Lookup allows teams to focus hunts using real, recent attack data, filtered by industry, geography, and timeframe.
Hunters can immediately see which malware families, campaigns, and techniques are actively targeting organizations like theirs right now.
Let’s try to search for attack data relevant to financial organizations based in the United States.
submissionCountry:”US” and industry:”finance”
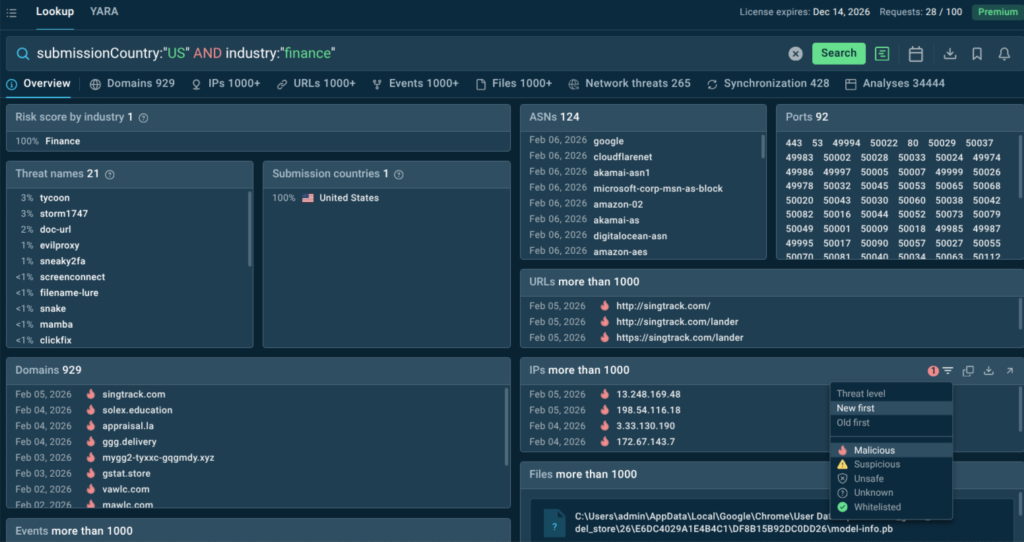
Contextual filtering reveals which malware families, attack techniques, and delivery methods are currently active against organizations like yours.
- EvilProxy is linked to multiple campaigns in 2023-2025 specifically targeted senior executives in US banking and financial services (FinCEN).
- As of early 2025, Tycoon is the most widespread phishing kit threatening the financial sector (Invenio IT).
You can prioritize hunting efforts based on actual observed threats rather than general industry chatter.
SOC / Business impact
- Focus on real business risk rather than theoretical threats;
- Less wasted hunting time on irrelevant attack patterns;
- Better alignment between security operations and business priorities.
Use Case 5: Turn TI Reports into Actionable Hunts
Hunting problem
By the time threat intelligence reports are published, many of the described attack patterns are already outdated or no longer active.
How hunters usually struggle
SOC teams invest effort into reports that no longer reflect active threats, resulting in delayed detections and wasted hunting time.
How TI Lookup helps
ANY.RUN’s Threat Intelligence Reports are created by analysts based on the freshest sandbox investigation data and come with ready-to-use TI Lookup queries.
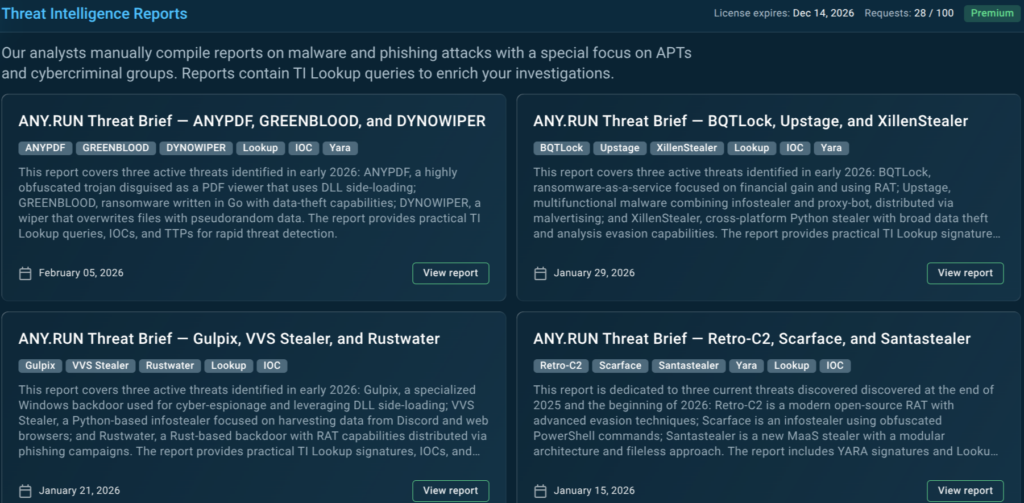
Instead of manually extracting indicators, teams can immediately test report findings against current, real attack data, verify whether the described patterns are still active, and collect fresh indicators for detections.
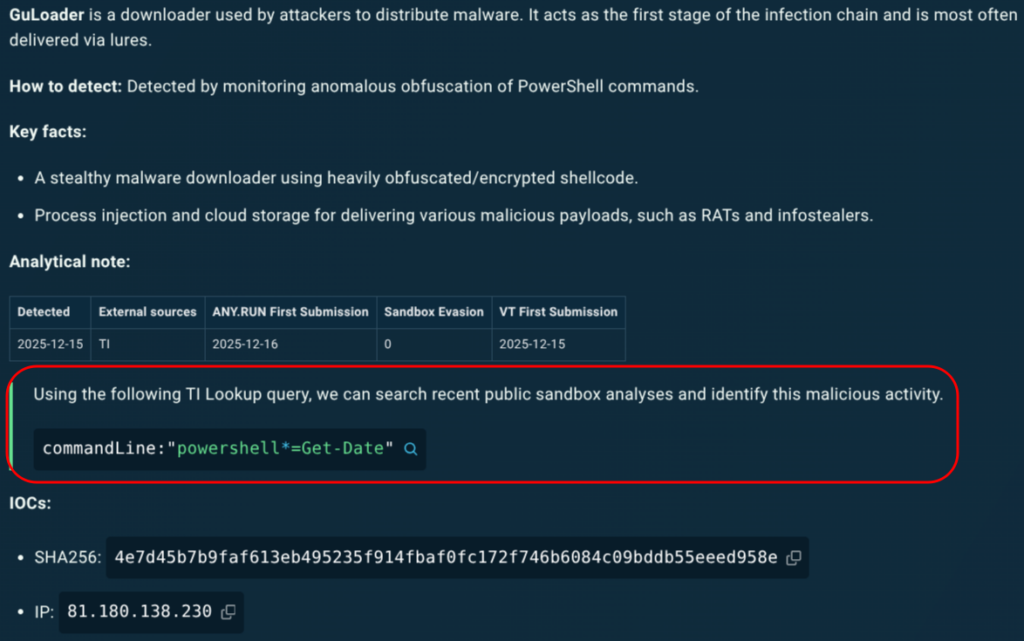
Intelligence moves directly from the report to a hunt, enabling SOC teams to quickly gather additional details for enriching the company’s proactive defense.
commandLine:”powershell*=Get-Date”
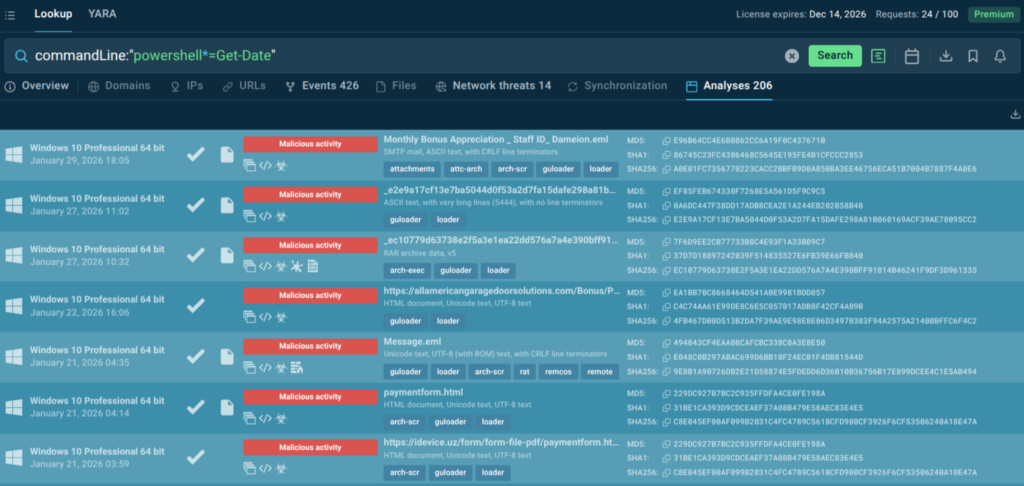
By tying indicators from the reports to sandbox sessions, threat hunting teams get to observe the entire attack execution and use the evidence to build effective detection rules.
SOC / Business impact
- Faster hunt cycles from intelligence to detection;
- Better ROI from threat intelligence research and subscriptions;
- Continuous learning loop between intelligence and operations.
What SOCs Gain, and Why the Business Cares
For SOC teams:
- Faster hunt planning: Reduce the research phase of threat hunting from hours to minutes. Access real attack examples immediately rather than piecing together information from multiple sources.
- Better detection quality: Build detection rules based on actual attack behavior, not assumptions. Test and validate detections against real malware before production deployment, reducing both false positives and false negatives.
- Less manual research: Eliminate the tedious work of correlating IOCs, searching through OSINT repositories, and extracting technical details from reports. Focus analyst time on analysis and decision-making rather than data collection.
For businesses:
- Earlier risk exposure: Identify threats proactively before they impact operations. Detect active campaigns targeting your industry while they’re still developing, not after damage occurs.
- Fewer missed attacks: Close detection gaps by building comprehensive coverage of current attack techniques. Reduce the window between attack and detection through intelligence-driven hunting.
- Higher ROI from existing security stack: Maximize the value of your current tools by feeding them better detection logic. Improve the signal-to-noise ratio across your security infrastructure, making every tool more effective.
Your Move: From Reactive Defense to Proactive Discovery
Threat hunting is only as effective as the intelligence that drives it. Without access to current, contextual attack data, even skilled analysts struggle to build detections that protect the business.
TI Lookup and YARA Search change this equation by providing direct access to millions of real attack sessions. This intelligence-first approach, starting with observable attack behavior rather than isolated indicators, enables SOC teams to hunt more effectively and demonstrate clear business value.
About ANY.RUN
ANY.RUN develops advanced solutions for malware analysis and threat hunting, trusted by 600,000+ cybersecurity professionals worldwide.
Its interactive malware analysis sandbox enables hands-on investigation of threats targeting Windows, Linux, and Android environments. ANY.RUN’s Threat Intelligence Lookup and Threat Intelligence Feeds help security teams quickly identify indicators of compromise, enrich alerts with context, and investigate incidents early. Together, the solutions empowers analysts to strengthen overall security posture at enterprises.
Request ANY.RUN access for your company
Because it reflects how attackers actually operate, not how they are assumed to operate.
No. It complements feeds by adding depth, context, and validation using real attacks.
TI Lookup includes both fresh and historical sandbox sessions, enabling real-time and retrospective analysis.
Yes. It reduces manual research effort and accelerates hunt development.
By tying hunts directly to real attacks, measurable detections, and reduced business risk.
Yes. YARA rules can be validated against real malware samples at scale.
In many cases, within hours instead of weeks.








0 comments