You can now search for network threats from Suricata in TI Lookup. This latest addition to our Threat Intelligence Lookup will help you identify and analyze malicious network activity more accurately.
Let’s dive into the new features and see how you can use them (with examples).
What’s new
- New search fields for Suricata data
- Network threats tab with Suricata detections
- Ability to search within results
- Detailed threat information in search results
Let’s discuss each of these points in more detail:
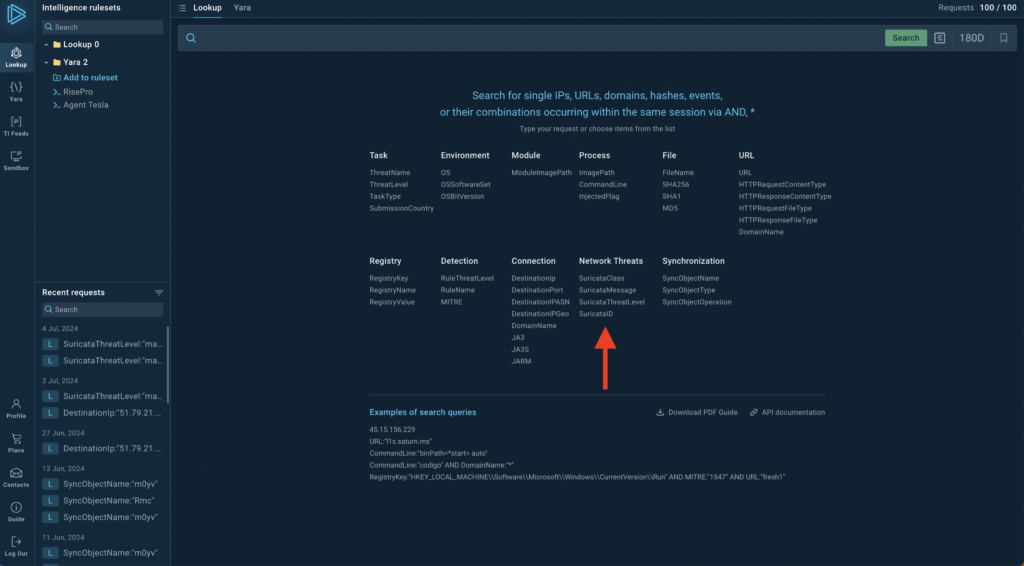
New Search Fields
We’ve added several new search fields to help you find specific network threats. These are:
- SuricataClass
- SuricataMessage
- Suricata ThreatLevel
- SuricataID
For example, you can use query SuricataThreatLevel:”malicious” to find all malicious network activities detected by Suricata.
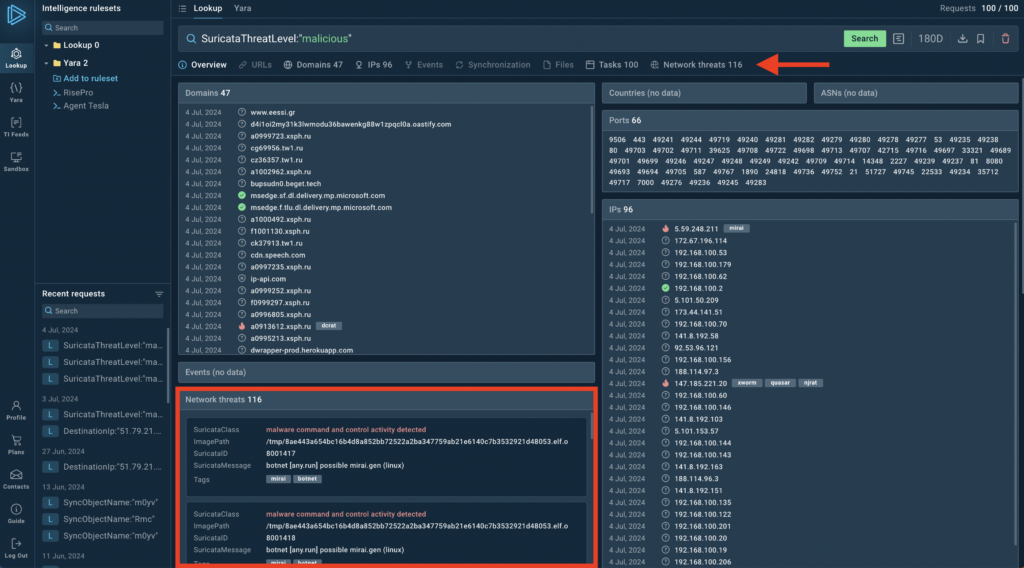
New network threats table and tab
The results page now includes detailed network threat information. For a more detailed breakdown, select the Network Threats tab.
The new Network threats tab displays Suricata detections, giving you a dedicated space to analyze network-based threats. This tab appears alongside existing tabs like URLs, Domains, and Files, providing a more comprehensive view of potential threats.
Search within results
After your initial search, you can further narrow down the results using the search bar in the Network threats tab. This feature allows you to quickly find specific threats among a large number of results.
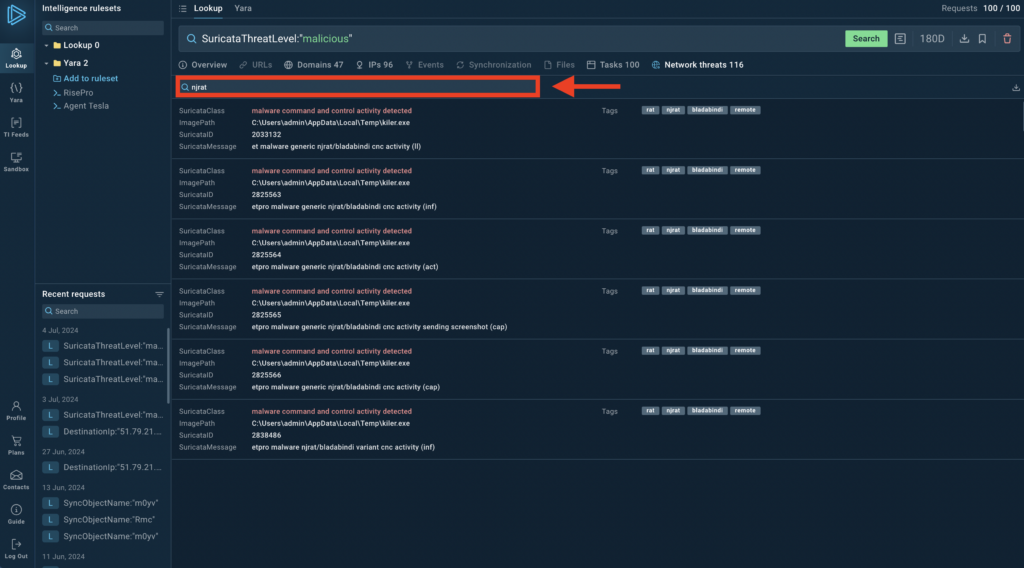
For instance, if you’re investigating NjRAT activity:
- Start with SuricataThreatLevel:”malicious.”
- In the Network threats tab, type “njrat” in the search bar.
- You’ll see only NjRAT-related entries, making your investigation more focused.
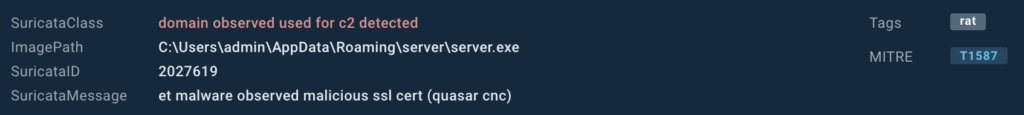
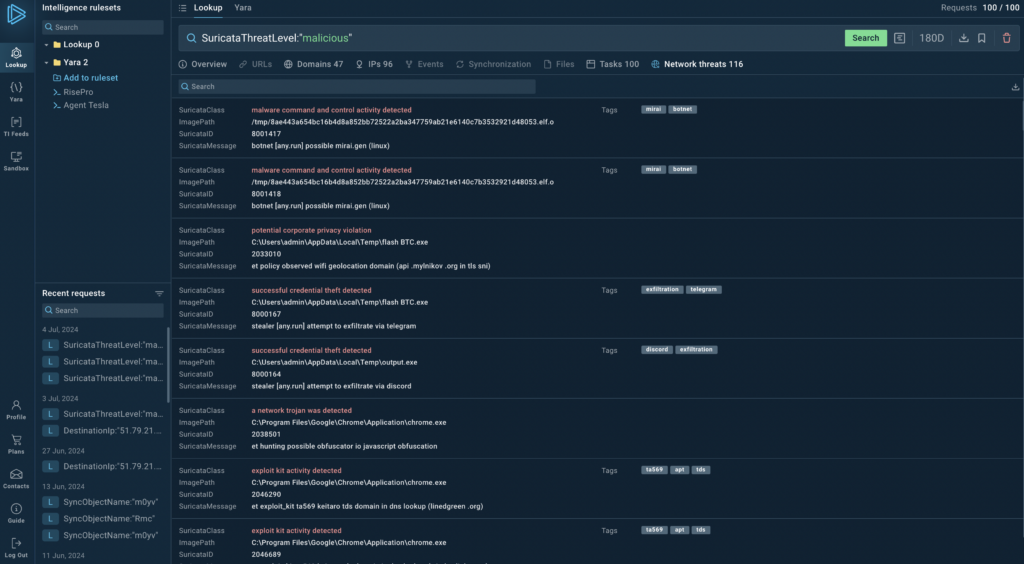
Detailed threat information
Each entry in the search results now includes:
- Suricata Class
- ImagePath
- Suricata ID
- Suricata Message
- Associated Tags
- MITRE TTP
This detailed information helps you quickly assess the nature and potential impact of each detected threat. Hower over an artifact and click on it to initiate a new TI Lookup search.
How to use Suricata search in TI Lookup
Let’s walk through a couple of practical examples.
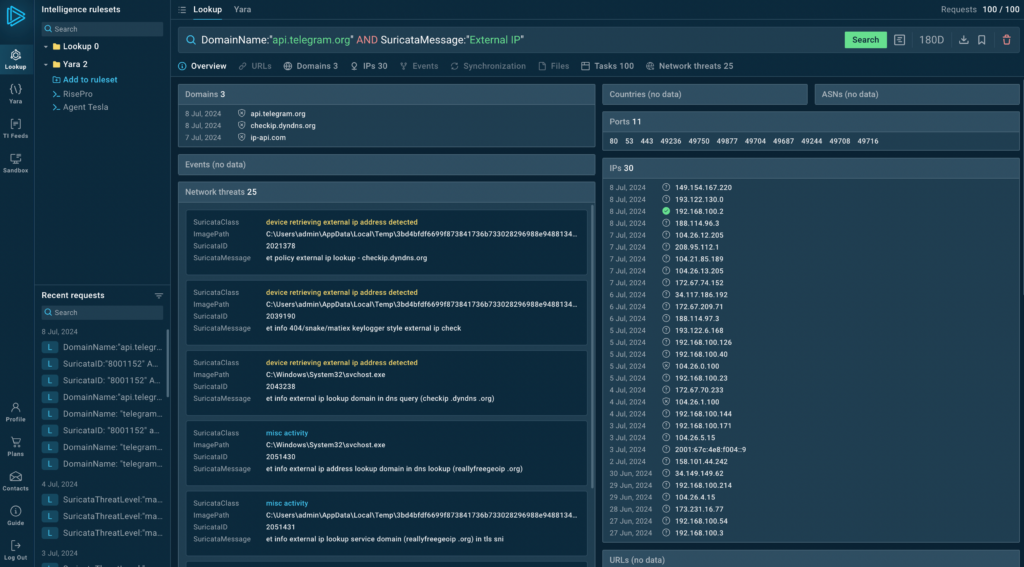
By obtaining the victim’s external IP address and connecting to Telegram’s API, you can capture a wide range of threats, including various stylers and some types of phishing.
Query example: DomainName:”api.telegram.org” AND SuricataMessage:”External IP”
And you can detect fake authentication attempts in Microsoft services using the following search query.
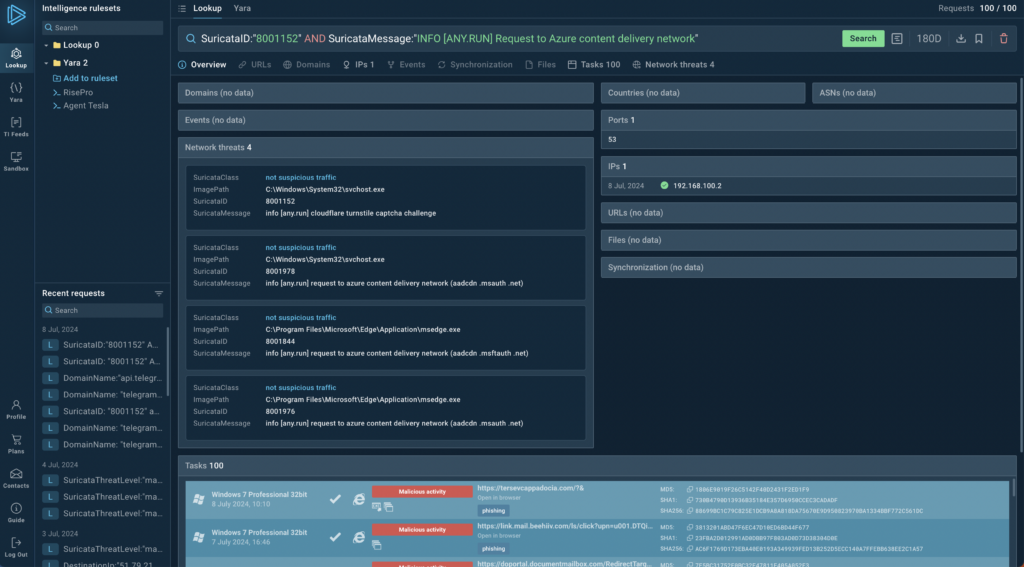
Query example: SuricataID:”8001152″ AND SuricataMessage:”INFO [ANY.RUN] Request to Azure content delivery network”
It works because Microsoft services do not use the free turnstile challenge from Cloudflare.
About ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Advantages of ANY.RUN
ANY.RUN helps you analyze threats faster while improving detection rates. The platform detects common malware families with YARA and Suricata rules and identifies malware behavior with signatures when detection by family is not possible.
With ANY.RUN you can:
- Detect malware in seconds.
- Interact with samples in real time.
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior.
- Collaborate with your team
- Scale as you need.








0 comments