There’s a new version of Hijack Loader active in the wild, and it received updated anti-evasion capabilities.
What’s happening?
Security researchers found a new version of Hijack Loader, which decrypts and parses a PNG image to load its second stage payload.
This second stage features a modular architecture, with its primary aim being the injection of the main instrumentation module.
To enhance stealth, the malware:
- Avoids inline API hooking, a common technique used by security software to detect threats.
- Adds an exclusion for Windows Defender antivirus.
- Bypasses User Account Control (UAC).
- Uses process hollowing.
In all, security researchers spotted seven new modules in March and April 2024.
What is HijackLoader
Hijack Loader, also known as IDAT Loader, appeared in September 2023. It’s been growing in popularity ever since. Today, Hijack is one of the most widely used loaders.
This malware currently ranks 6th most detected in the ANY.RUN Trends Tracker. We calculate this ranking by analyzing public sandbox submissions.
The card below shows payloads Hijack Loader delivers:
- Amadey
- Lumma Stealer
- Meta Stealer
- Raccoon Stealer V2
- Remcos RAT
- Rhadamanthys
(Read our Raccoon Stealer 2.0 technical analysis)
Detecting Hijack Loader in ANY.RUN
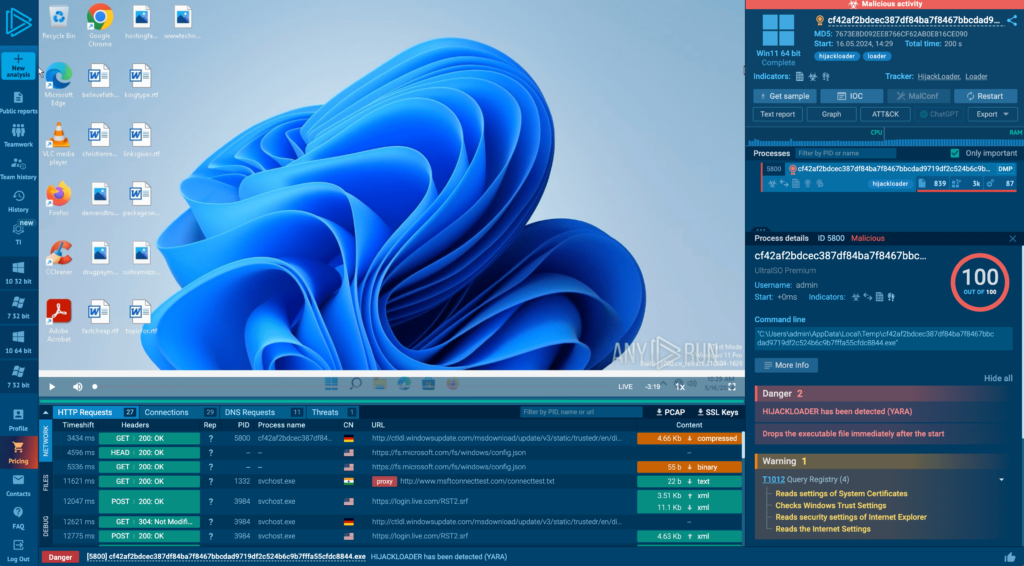
ANY.RUN sandbox can detect HijackLoader by YARA. The screenshot below shows an analysis session of the new Hijack Loader version.
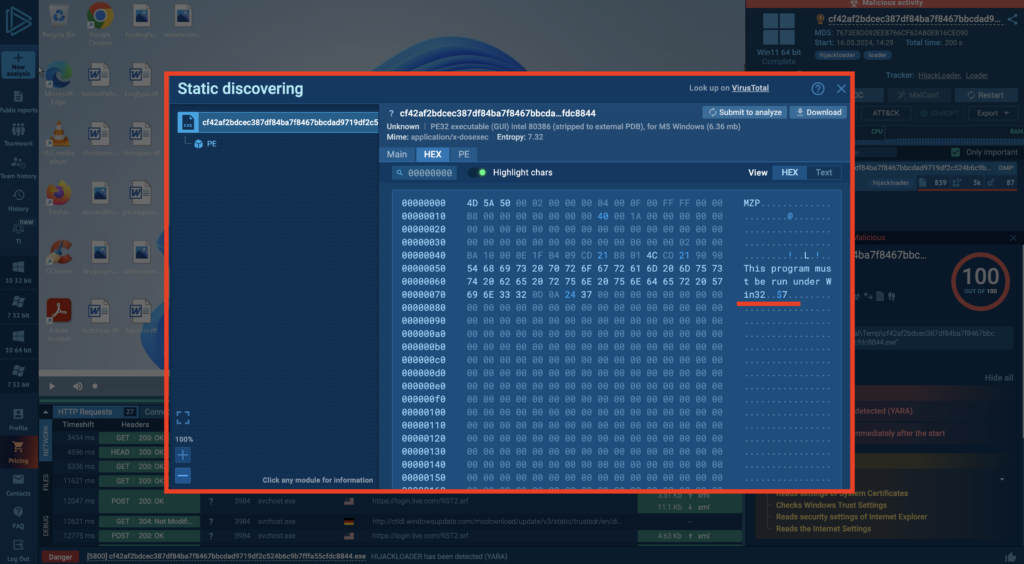
By analyzing the static file content, we can see that this sample targets both 32- and 64-bit versions of Windows:
In this particular example, the second stage payload did not download because the C2 was already dead.
Lates Hijack Loader IOCs
We’ve collected the latest Hijack Loader IOCs from the Malware Trends Tracker.
More artifacts can be found here. They’re dynamically updated when someone creates a new public analysis session and uploads this malware to ANY.RUN.
| IPs: |
185.215.113.67 193.233.132.139 185.172.128.76 |
| Hashes: |
86BCCBACD8E9FDE23FF236155EE47F866DD7DD51C6129ED340034810A10705B3 0AE58BE8D7058E40926FDB51B76043D109B96B91AA9FA2950DBB8A3626185E0F A38DA72082FC2DC1F60B3B245E1F2382D5F8C1D08EBC397DD0D81CC9F74EBBE6 |
| URLs: |
mail.zoomfilms-cz[.]com discussiowardder[.]website wxt82[.]xyz |
About ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Advantages of ANY.RUN
ANY.RUN helps you analyze threats faster while improving detection rates. The platform detects common malware families with YARA and Suricata rules and identifies malware behavior with signatures when detection by family is not possible.
With ANY.RUN you can:
- Detect malware in under 40s: ANY.RUN detects malware within about 40 seconds of a file upload. It identifies prevalent malware families using YARA and Suricata rules and uses behavioral signatures to detect malicious actions when you encounter a new threat.
- Interact with samples in real time: ANY.RUN is an interactive cloud sandbox powered by VNC, which means that you can do everything you could on a real system: browse webpages, click through installers, open password-protected archives.
- Save time and money on sandbox setup and maintenance: ANY.RUN’s cloud-based nature eliminates the need for setup or maintenance by your DevOps team, making it a cost-effective solution for businesses.
- Record and study all aspects of malware behavior: ANY.RUN provides a detailed analysis of malware behavior, including network traffic, system calls, and file system changes.
- Collaborate with your team: easily share analysis results, or, as a senior team member, check work of junior analysts by viewing recordings of their analysis sessions.
- Scale as you need: as a cloud service, you can easily scale your team, simply by adding more licenses.
We’ll show you in an interactive presentation how ANY.RUN can help your security team.








0 comments