TTPs stands for Tactics, Techniques, and Procedures, a concept commonly used in cybersecurity to describe the behavior patterns of threat actors or adversaries.
What are TTPs?
TTPs refer to the specific methods and patterns that adversaries use to carry out their objectives. Understanding TTPs is crucial for defenders to anticipate, detect, and respond to threats effectively. By analyzing TTPs, security professionals can develop better strategies to protect against and mitigate potential attacks.
Let’s break down each component:
Tactics
Tactics represent the high-level game plan or overall approach an adversary takes to achieve their goals. It’s the “why” behind their actions. Tactics describe the adversary’s intended effect or outcome, such as initial access, privilege escalation, or data exfiltration.
How to detect tactics
Tactics are typically identified through broader behavioral analysis and understanding the overall goals of the malware.
This often involves observing the malware’s actions in a controlled environment — like ANY.RUN sandbox — analyzing its network traffic, and studying its interactions with the system.
For example, if you notice the malware attempting to establish persistence, elevate privileges, and exfiltrate data, you can infer that its tactics align with long-term espionage or data theft. Uncovering tactics often requires looking at the bigger picture and piecing together various observed behaviors to understand the malware’s strategic objectives.
Techniques
Techniques are the specific methods or actions an adversary uses to execute their tactics. These are the “how” of their operations. Techniques can include various activities like phishing, exploiting vulnerabilities, or using malware. They are more detailed than tactics but still general enough to apply across different scenarios.
How to detect techniques
Techniques are more specific and can be detected through a combination of static and dynamic analysis.
Static analysis involves examining the malware’s code or binary structure without executing it. You might look for specific API calls, strings, or code patterns that indicate particular techniques.
For instance, the presence of certain Windows API calls could indicate an attempt to inject code into another process. Dynamic analysis, where you run the malware in a controlled environment, allows you to observe these techniques in action.
Use tools like process monitors, network analyzers, and sandboxes. You’d look for specific actions like registry modifications, file creations, or network connections that correspond to known malicious techniques.
Procedures
Procedures are the precise, step-by-step processes an adversary follows to implement their techniques. This is the most granular level of the TTP framework, describing the exact tools, malware variants, or specific exploits used in an attack. Procedures represent the unique “fingerprint” of an adversary’s operations.
How to detect procedures
Procedures are the most granular and specific aspect of malware behavior. Uncovering these often requires deep dive analysis and reverse engineering.
This involves disassembling the malware to understand its exact implementation of a technique. For example, you might analyze the specific encryption algorithm used for data exfiltration, the exact method used for process injection, or the particular command and control protocol.
Identifying procedures often requires debuggers and disassemblers, and a strong understanding of low-level system operations. You’d look for unique identifiers like specific file names, registry keys, mutex names, or network indicators that are particular to a specific malware family or threat actor.
In summary, understanding TTPs helps security professionals to:
- Identify patterns in adversary behavior.
- Attribute attacks to specific threat actors.
- Develop more effective defensive strategies.
- Improve threat intelligence and information sharing.
How TTPs Help Cyber Security Professionals
TTPs serve as a framework for analyzing and predicting adversary behavior in cybersecurity. By studying the consistent patterns in how threat actors operate, security teams can develop more effective defensive strategies and response plans.
Detecting novel malware or attack vectors
One key benefit of understanding TTPs is the ability to detect threats even when faced with novel malware or attack vectors. For instance, while a new strain of ransomware might evade signature-based detection, the techniques used to deploy it – such as exploiting unpatched vulnerabilities or using stolen credentials — often remain consistent.
This allows defenders to focus on identifying and mitigating these common attack paths rather than playing an endless game of catch-up with each new malware variant.
Threat attribution
TTPs also play a crucial role in threat attribution. Different nation-state actors, cybercriminal groups, and hacktivist organizations often have distinct operational patterns. By cataloging these patterns, security analysts can often identify the likely culprit behind an attack, even without direct evidence linking the attack to a specific group.
This attribution is valuable not just for law enforcement purposes, but also for understanding the motivations and capabilities of the attacker, which in turn informs risk assessments and defensive priorities.
Incident response
In incident response, TTP analysis helps prioritize actions and allocate resources effectively. If an intrusion is detected and the TTPs match those of a known advanced persistent threat (APT) group, the response team knows to prepare for a potentially long-term, sophisticated campaign rather than a one-off opportunistic attack.
This insight allows for more appropriate scaling of the response effort and guides decisions about whether to involve law enforcement or other external parties.
Strategic security planning
Understanding TTPs also informs better security architecture decisions. By knowing the common techniques used by attackers to move laterally within networks, for example, security architects can implement more effective network segmentation and access control policies. This approach of “thinking like the attacker” to inform defensive strategies is a cornerstone of modern cybersecurity practices.
TTPs and MITRE ATT&CK framework
The concept of TTPs has led to the development of standardized frameworks like MITRE ATT&CK, which provides a common taxonomy for describing adversary behaviors.
This shared language facilitates better communication within and between organizations, enabling more effective threat intelligence sharing and collaborative defense efforts across the industry.
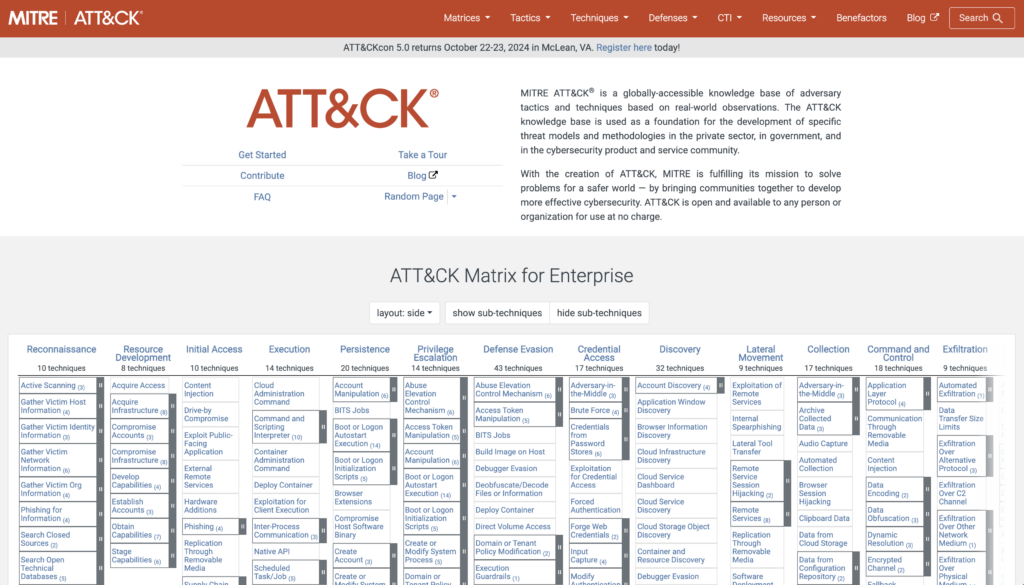
MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) is a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations. It’s essentially a comprehensive matrix that maps out the steps an attacker might take to compromise and operate within a network.
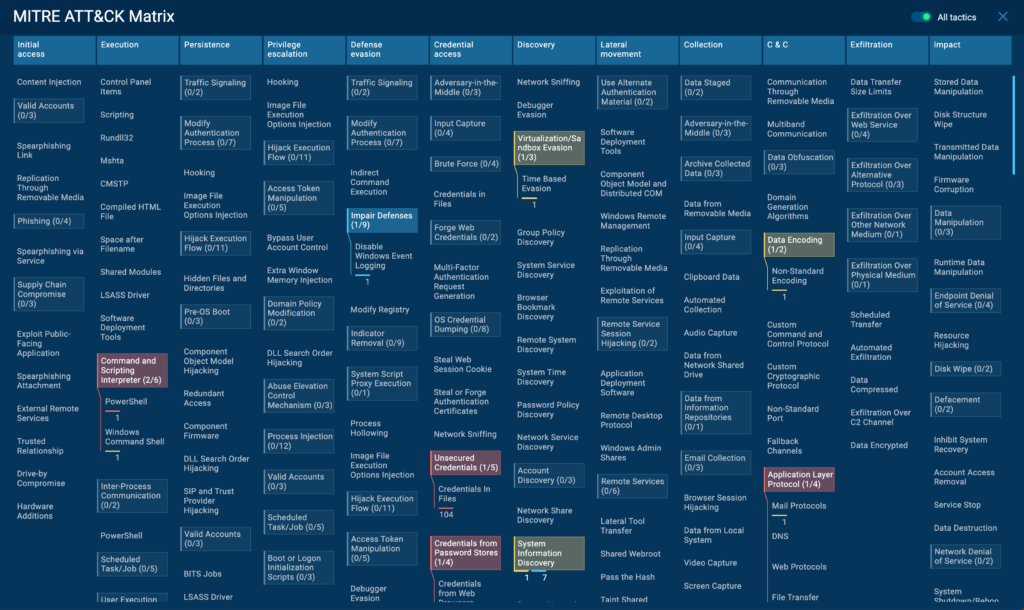
The ATT&CK matrix is organized into several tactical categories, each representing a different stage of an attack lifecycle. These categories include Initial Access, Execution, Persistence, Privilege Escalation, Defense Evasion, Credential Access, Discovery, Lateral Movement, Collection, Exfiltration, and Command and Control. Under each of these tactics, you’ll find numerous techniques and sub-techniques that adversaries might employ.
What makes the ATT&CK matrix particularly valuable is its granularity and specificity.
For each technique, MITRE provides detailed information including a description of how it works, examples of its use in the wild, potential mitigations, and detection strategies. This level of detail allows security teams to develop highly targeted defenses and detection methods.
Many organizations use the ATT&CK matrix as a framework for assessing their security posture.
They might map their existing security controls against the techniques in the matrix to identify gaps in their defenses. Similarly, red teams often use the matrix to plan and document their simulated attacks, ensuring they’re testing a comprehensive range of realistic adversary behaviors.
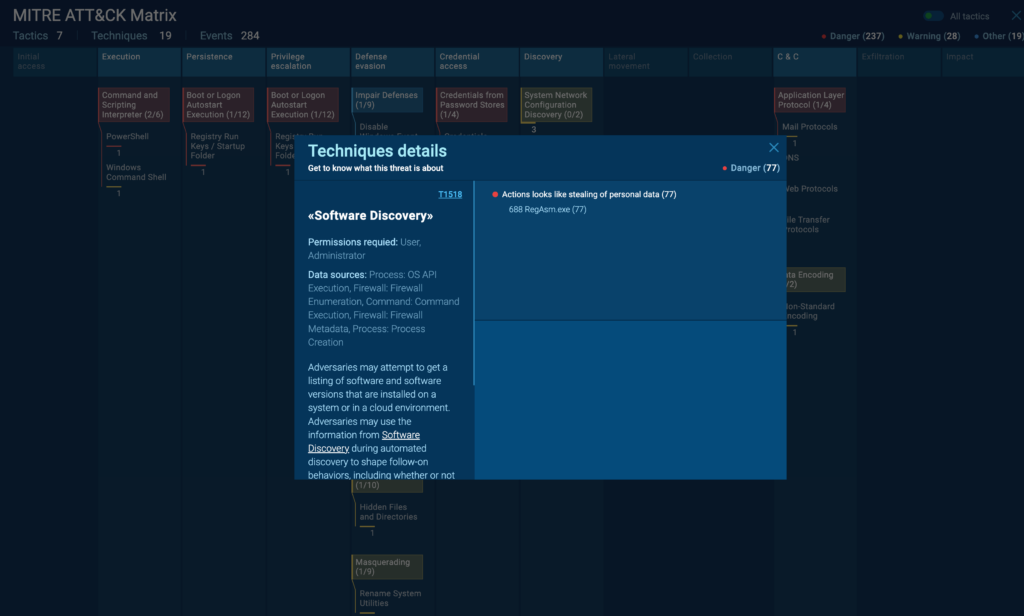
Using the MITRE ATT&CK Matrix in ANY.RUN to learn about TTPs
The TTP Matrix report in ANY.RUN is a powerful feature that maps observed malware behaviors to the MITRE ATT&CK framework.
It provides a visual representation of the tactics and techniques used by the analyzed sample, allowing for quick assessment of its capabilities and potential impact. Here’s how to effectively use this report:
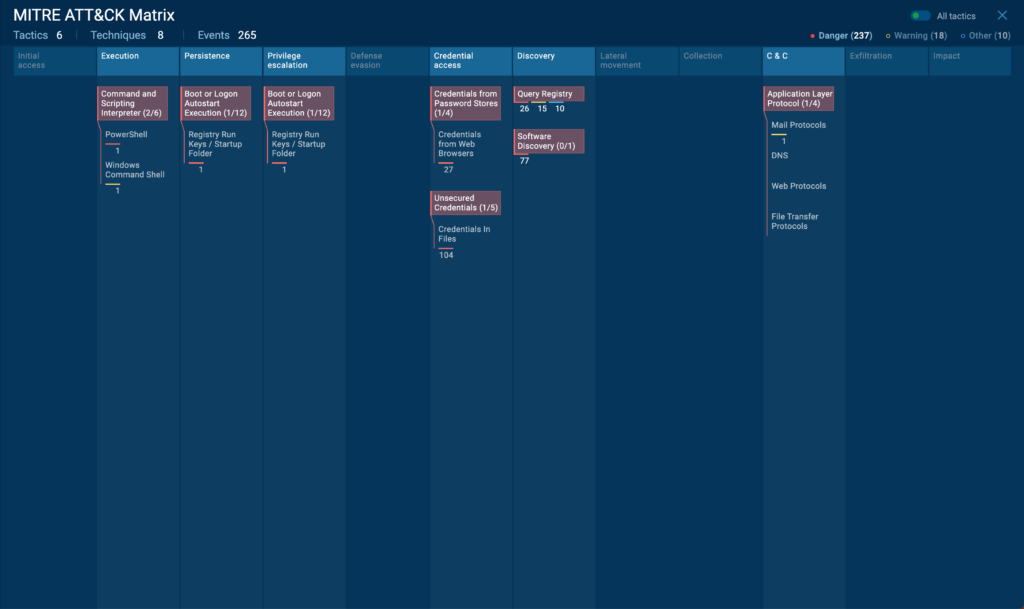
How does this report work?
When you run a sample in ANY.RUN, the TTP Matrix report is automatically generated as part of the analysis results. You’ll find it in the “TTP Matrix” tab of the analysis interface.
To interpret the report, start by looking at the tactics (columns) to get an overview of the malware’s general behavior patterns. For instance, if you see multiple techniques highlighted under “Defense Evasion” and “Persistence”, it suggests the malware is designed for long-term stealth operation.
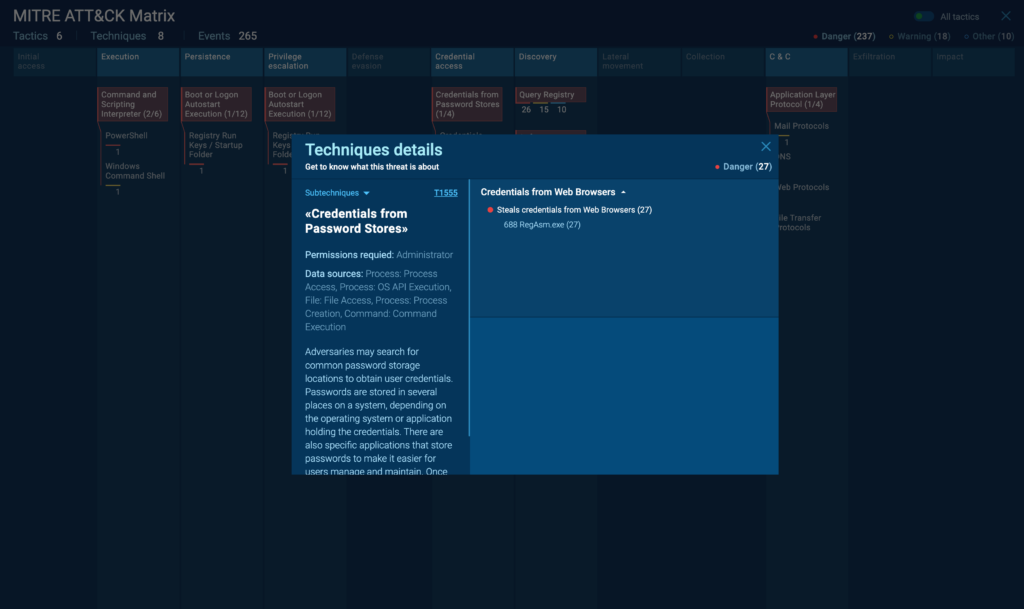
Click on individual cells in the matrix to view details about each observed technique. ANY.RUN provides a description of the technique and specific examples of how the malware implemented it. This information is crucial for understanding the malware’s exact capabilities and potential impact.
How to apply the TTP matrix report in ANY.RUN
Use the matrix to guide your further investigation. If you see a technique you’re unfamiliar with, you can research it further using the MITRE ATT&CK ID provided. This helps in expanding your knowledge of malware behaviors and improving your analysis skills over time.
The TTP Matrix report is also valuable for comparing different malware samples. By looking at the patterns of techniques used, you can identify similarities that might indicate related malware families or threat actors. This can be particularly useful when dealing with potential variants of known malware.
Lastly, use the report to inform your defensive strategies. If you consistently see certain techniques being used across multiple samples, it may indicate areas where you need to strengthen your defenses or improve your detection capabilities.
While the TTP Matrix provides valuable insights, it should be used in conjunction with other analysis results in ANY.RUN for a comprehensive understanding of the malware’s behavior.
Driving your cybersecurity strategy with TTPs
TTPs can serve as a powerful foundation for shaping your cybersecurity strategy. By aligning your defenses with known adversary behaviors, you can create a more proactive and effective security posture.
This approach allows you to prioritize your efforts based on real-world threats, rather than hypothetical scenarios or outdated assumptions. Here are several ways to leverage TTPs in driving your cybersecurity strategy:
Prioritize defense investments based on prevalent tactics. For example, if analysis shows that initial access is frequently gained through phishing, allocate more resources to email security, user training, and multi-factor authentication.
Enhance detection capabilities by focusing on common techniques. Implement logging and monitoring specifically tailored to detect behaviors associated with frequently used techniques, such as PowerShell abuse or credential dumping.
Develop incident response playbooks around specific procedures. Create detailed response plans for handling the exact methods used by threat actors, like a specific ransomware variant’s encryption process or a nation-state APT’s preferred exfiltration method.
Streamline threat hunting by focusing on indicators associated with known TTPs. Develop hunting hypotheses based on the techniques favored by threat actors who are likely to target your organization.
Optimize security tool configurations to address specific techniques. Tune your firewalls, intrusion detection systems, and endpoint protection platforms to detect and prevent the exact methods used in common attack chains.
Guide security architecture decisions based on adversary movement patterns. Design network segmentation and access controls to disrupt the lateral movement techniques frequently employed by sophisticated threat actors.
Prioritize vulnerability management by considering the techniques that exploit specific vulnerabilities. Focus patching efforts on vulnerabilities that align with the TTPs of threat actors targeting your sector.
Develop custom analytics to detect procedure-specific indicators. Create specialized detection rules or machine learning models designed to identify the unique artifacts or patterns associated with specific adversary procedures.
About ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
With ANY.RUN you can:
- Detect malware in seconds.
- Interact with samples in real time.
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior.
- Collaborate with your team
- Scale as you need.









0 comments