Global threat intelligence refers to information about emerging and persistent cybersecurity threats from around the world.
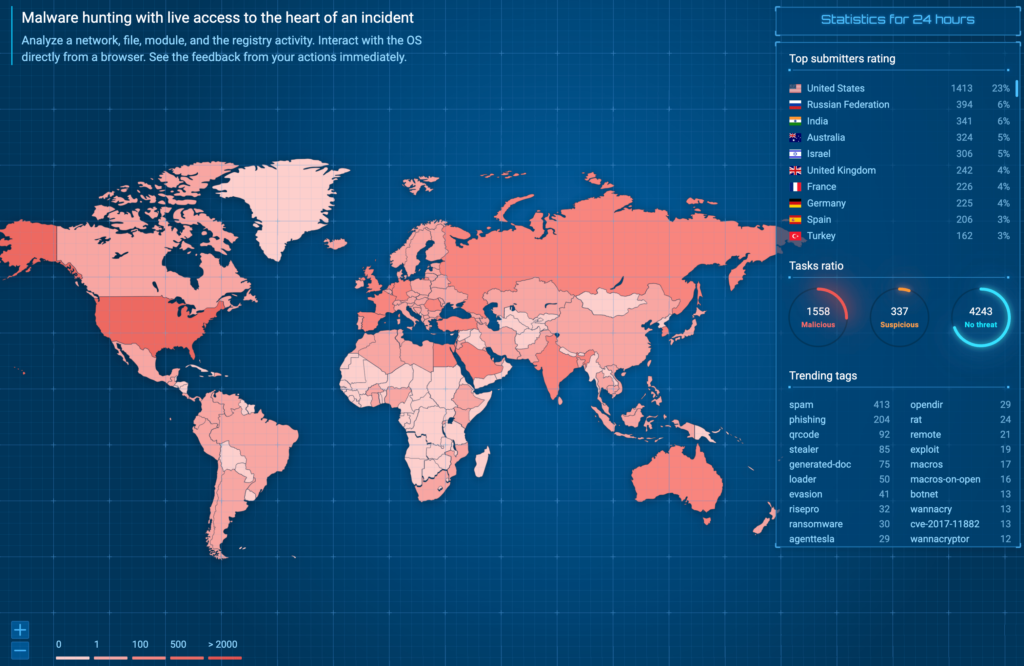
Cybersecurity threats can originate from anywhere globally, and each region has its own unique characteristics. For instance, North Korean APTs are notorious for targeted attacks against government infrastructure and critical services, while groups in former Soviet Union territories often run ransomware-as-a-service (RaaS) campaigns like LockBit.
Read about how the LockBit operation was disrupted but later resurfaced.
To gain a comprehensive understanding of the threat landscape, it’s crucial to monitor threat intelligence not just from your local region but from around the globe. This requires access to specialized data sources.
What is Considered Global Threat Intelligence?
In the table below we’ve listed the aspects that a truly global threat intelligence source should include:
| Comprehensive data sources | Global threat intelligence relies on collecting data from sources around the world, and the more international organizations from different countries and regions contribute to the data source the more holistic picture it will be able to provide. |
| Global monitoring | It involves monitoring cyber threats, malware campaigns, and other malicious activities that transcend geographical boundaries and have the potential to impact organizations worldwide. |
| Global IOCs and event fields | The data source should provide access to artifacts or patterns that indicate a system has been compromised or is under attack, like IP addresses, domain names, file hashes, patterns of network traffic, or CMD to PowerShell commands associated with known malware. |
Global Threat Intelligence in ANY.RUN
Threat Intelligence is a vast field with different levels: strategic (who might attack us and why?), operational (how could they carry out the attack, and what techniques are we exposed to?), tactical (what specific malware could they use?), and technical (what indicators of compromise should we monitor?).
Each level requires its own tools and techniques, and it’s impossible to cover them all in one article. ANY.RUN’s solutions can help you with technical, tactical, and operational threat intelligence on a global scale. Here’s what makes our data source truly global.
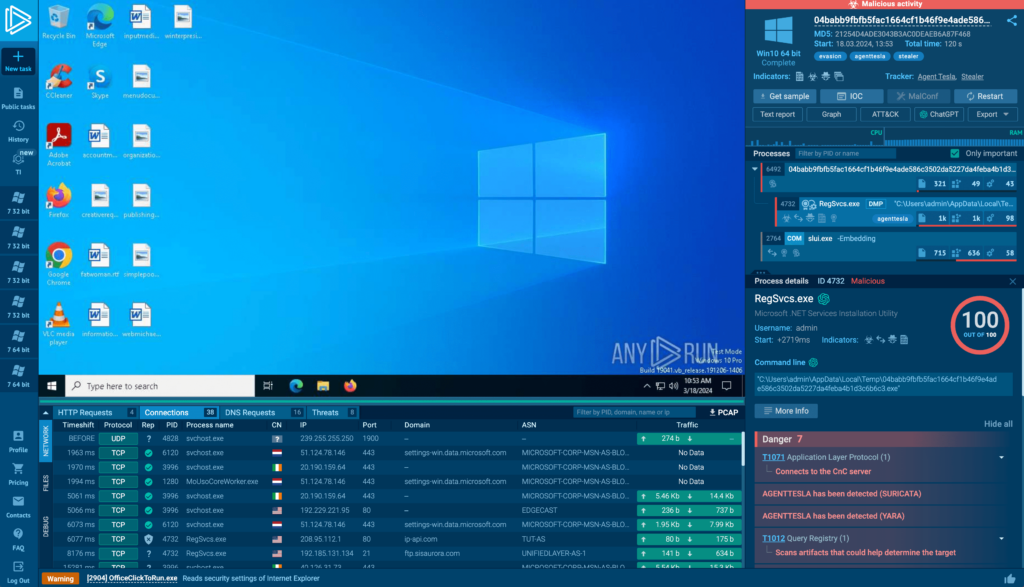
It all starts with the ANY.RUN interactive sandbox. Roughly 400,000 malware researchers worldwide (from 190 countries) use our sandbox to quickly set up malware analysis environments in the cloud and analyze samples they encounter. Many choose to share the results publicly. Every day, we process nearly 15,000 of these public submissions.
Read how we pre-process IOCs and Events Fields for our TI products.
Our sandbox is designed for speed, enabling analysts to quickly upload and analyze newly encountered malware samples. During each analysis session, we record not just indicators of compromise (IOCs), but also related data: file and registry events, mutexes, loaded modules, script traces, malware configurations, command lines, processes, and their connections to specific malware families. We then save all of this data in our database.
You can leverage this global data for threat intelligence in two ways:
- Subscribe to ANY.RUN’s Threat Intelligence Feeds. Keep your SIEM or threat intelligence platform updated with fresh global IOCs delivered in STIX format in real time.
- Use our Lookup Portal to find connected indicators. Because our threat intelligence database maintains the linkages between events in each sandbox analysis, you can search for an isolated event like a suspicious Command Line and quickly identify which malware it may be associated with. This provides incident responders with valuable context often unavailable from open sources.
Our recording of IOCs and related telemetry data provides a powerful global data source for technical, tactical, and operational threat intelligence.
Example of Global Threat Intelligence in ANY.RUN
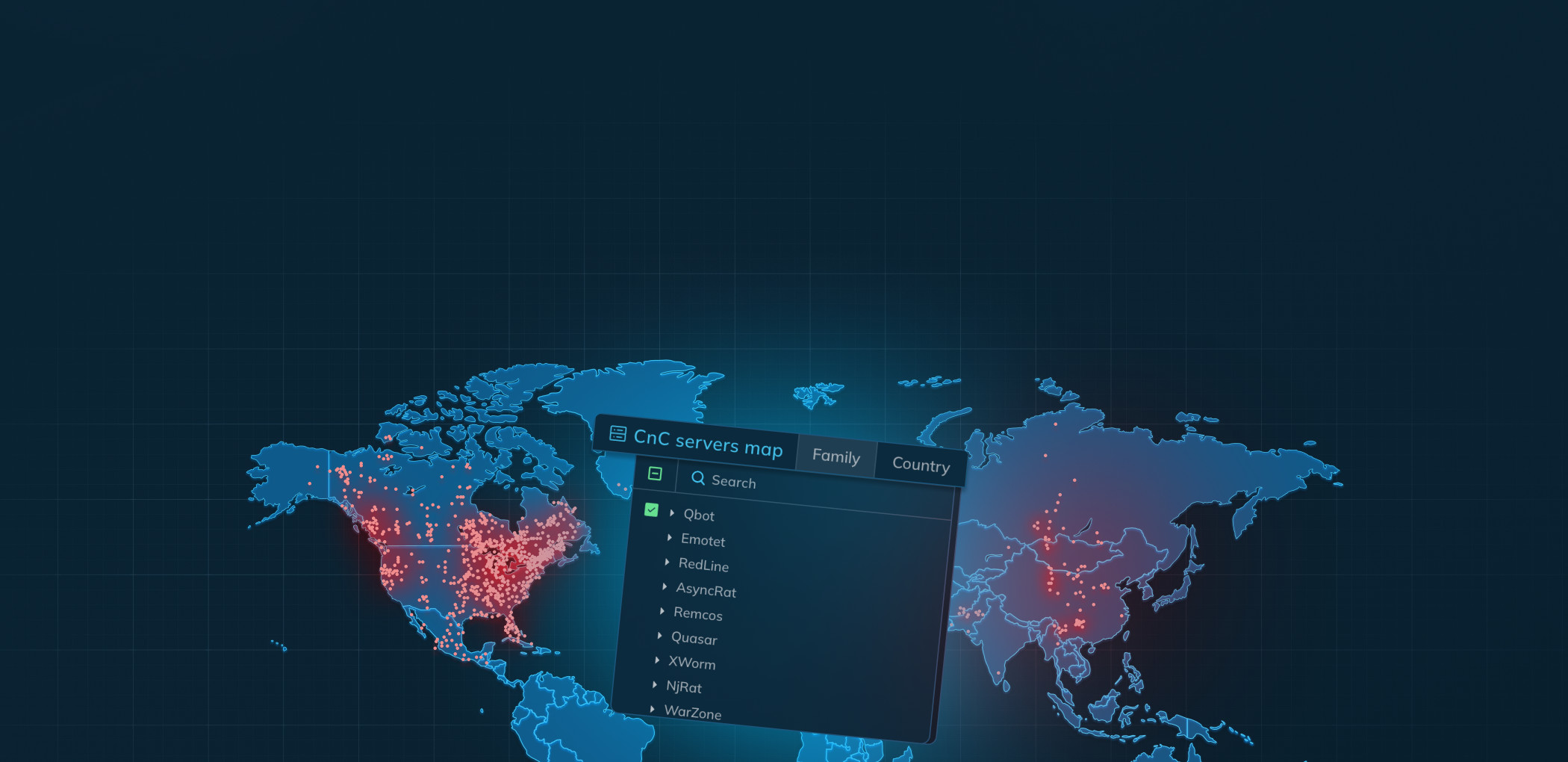
Let’s look at an example of how ANY.RUN enables global threat intelligence. Because we extract C2 server locations from malware configurations and network traffic, we can map them on a global view accessible through the ANY.RUN Threat Intelligence Lookup portal:
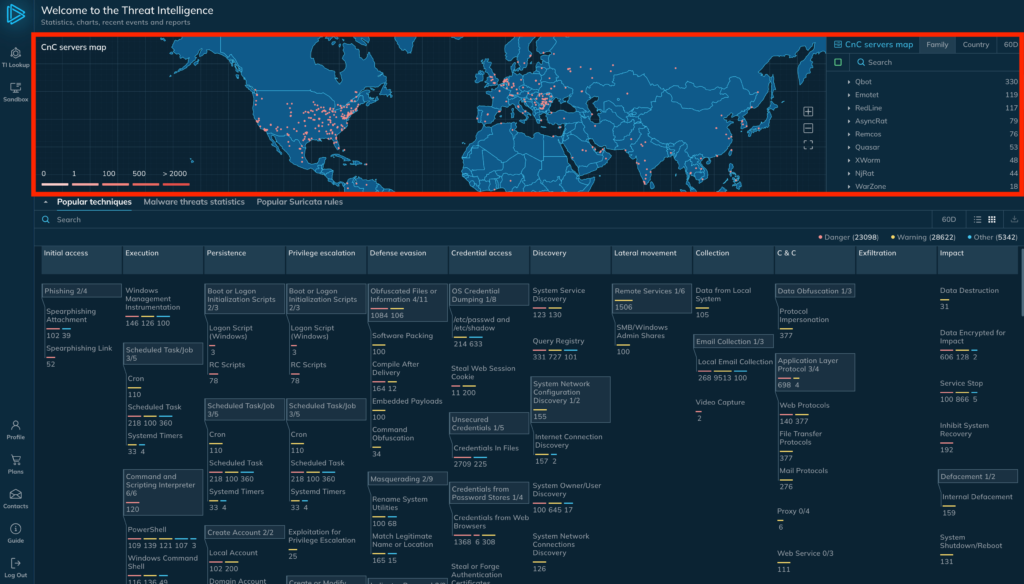
You can filter threats by country or family to see where different malware families were spotted communicating over time, as well as their commonly associated MITRE tactics and techniques.
This geographic visualization provides valuable operational threat intelligence.
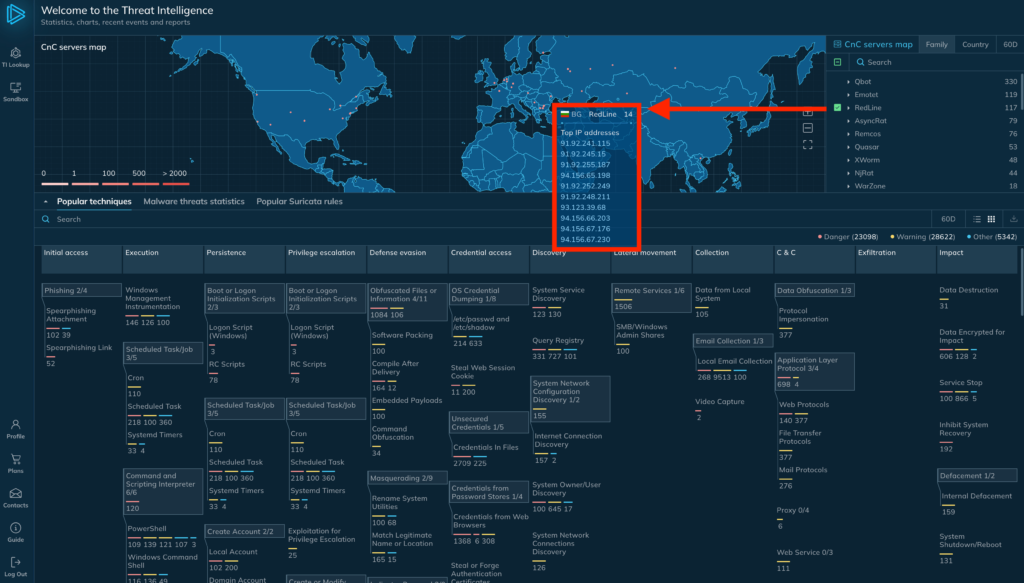
Hover over any location, and you’ll see a list of the specific IP addresses associated with that threat in that region. This granular IP information can help you configure web application firewalls or other controls to guard against targeted threats. Or, if you log traffic to one of those IPs, you can automatically enrich incident tickets with the corresponding threat identifiers in your threat intel platform.
What is ANY.RUN?
ANY.RUN’s flagship product is an interactive malware sandbox that helps security teams efficiently analyze malware. Every day, 400,000 professionals use our cloud-based platform to investigate incidents and streamline threat analysis on Windows and Linux virtual machines.
Key advantages of ANY.RUN for businesses:
- Real-time detection: Within roughly 40 seconds of uploading a file, ANY.RUN can detect malware and automatically identify many malware families using YARA and Suricata rules.
- Interactive analysis: Unlike fully automated solutions, ANY.RUN allows you to play with the the sample in a VM directly through your browser. This way you can detect zero-day exploits and sophisticated malware that can evade signature-based detection.
- Cost-effective: As a cloud-based solution, ANY.RUN translates into cost savings by eliminating setup and maintenance efforts for your DevOps team.
- Streamlined onboarding: ANY.RUN’s intuitive interface enables even junior SOC analysts to quickly learn malware analysis and indicator of compromise extraction.
If these capabilities sound beneficial for you or your team, give ANY.RUN a try. The best part is — we offer a completely free starter plan.







0 comments