In February, The FBI and international law enforcement allies claimed a big victory. They’ve seized the operations of LockBit, got hold of the gang’s source code, and took over their website:
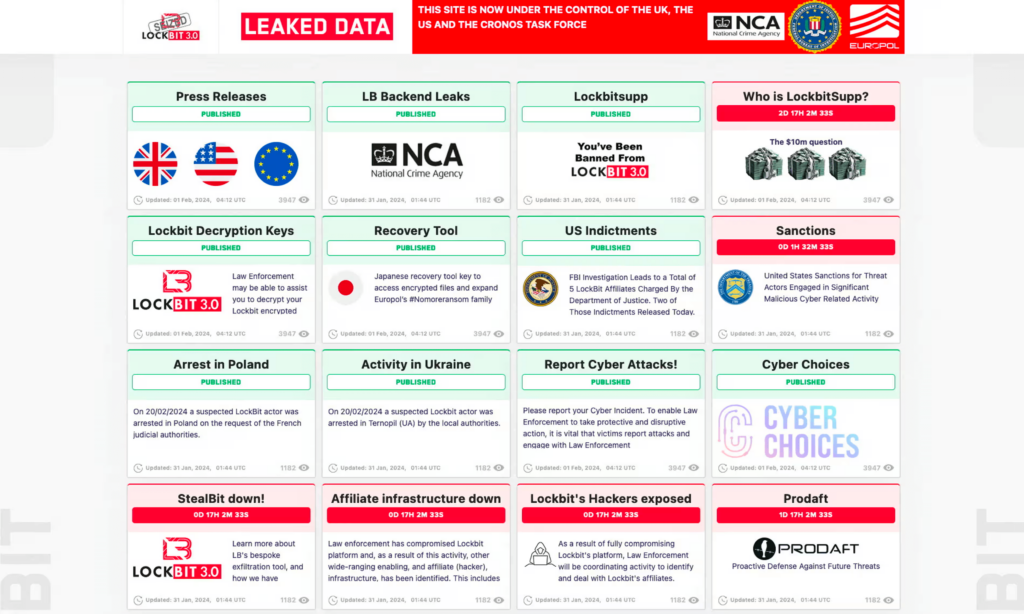
Unfortunately, it seems the win was only temporary. The core members of the gang weren’t arrested, and the takedown by Operation Cronos was short-lived, as the gang recovered within days.
At ANY.RUN, we noted a period of inactivity followed by a spike, as LockBit detections in our sandbox reached 0 and then began to grow, starting a few days after the takedown.
The LockBit ransomware gang has resumed its attacks, then. Now they’re employing updated encryptors and ransom notes that lead to new servers.
Rather than rebranding, LockBit gang promised to return with enhanced infrastructure and updated security measures to prevent the law enforcement from accessing their descriptors again.
We’ve seen this pattern before. Shortly after GandCrab was taken down in June 2019, REvil — also known as Sodinokibi — ransomware emerged, and it was based on GandCrab’s source code at least partially. Security researchers who took the opportunity to study GandCrab’s code during the quiet period were better prepared to deal with REvil when it appeared.
History repeats iself. Read about the rise and fall of REvil
What is LockBit?
LockBit is both a ransomware and an APT group with the same name. The group has claimed responsibility for many high-profile attacks. LockBit has extorted over $120 million from 2,000 victims.
LockBit ransomware primarily targets Windows systems, but it’s also capable of encrypting files on Linux and MacOS. The group operates using a Ransomware-as-a-Service (RaaS) model, wherein the core members develop the ransomware and then sell it to affiliates who carry out the actual attacks.
Analyzing LockBit in ANY.RUN
Similar to the story of GandCrab’s demise and resurrection as REvil, it’s likely that LockBit creators will modify the code of this threat. Even if they don’t, ransomware activity as a whole has been climbing since 2023, and LockBit is one of the most widely deployed strains you’re likely to encounter.
That’s why it’s important to study its behavioral patterns, TTPs, and collect Lockbit IOCs to set up your TIP and SIEM systems. With ANY.RUN, you can run extensive LockBit ransomware analysis in seconds and just with a couple of clicks. This way, you can detect and isolate an intrusion before LockBit encrypts your files and causes damage to your infrastructure.
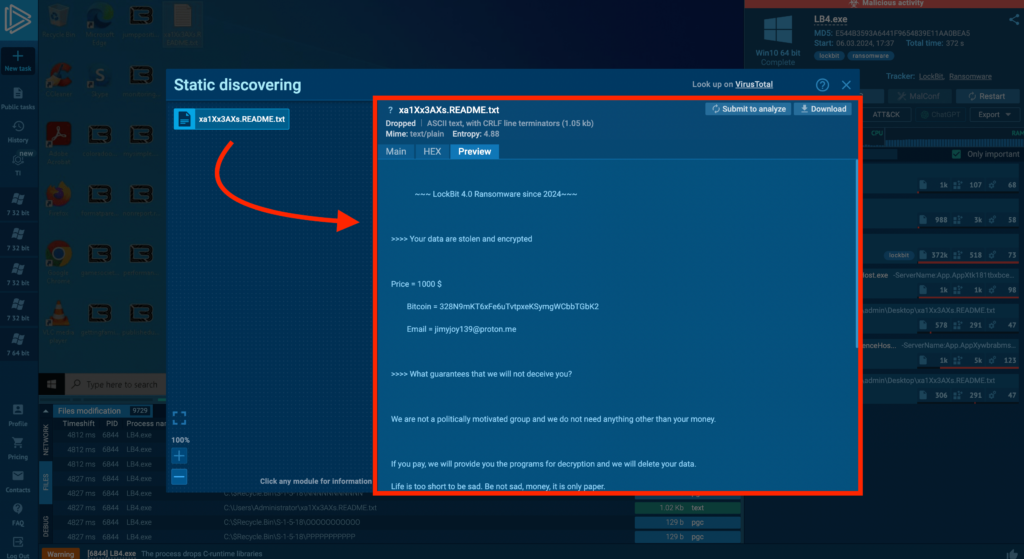
The primary function of this ransomware is still the same: it encrypts files and deposits a ransom note with contact information and instructions — like we see in this task.
The latest version is LockBit 4.0, and it’s a bit different from the previous 3.0 version. In 4.0, it doesn’t change the wallpaper anymore, and it takes a lot longer to decrypt all the files on the infected system. Unlike 3.0 which deleted itself after encrypting, version 4.0 doesn’t do that.
Wrapping up
- LockBit has bounced back from the takedown: the gang resumed its operations with updated encryptors, and infrastructure.
- LockBit overview: LockBit targets primarily Windows systems but also capable of affecting Linux and MacOS. With over $120 million extorted from 2,000 victims, LockBit is perhaps the most infamous ransomware.
- Preparation is Key: Understanding LockBit’s behavioral patterns, tactics, techniques, and TTPs, and collecting IOCs can help you set up security systems appropriately.
What is ANY.RUN?
ANY.RUN is a cloud malware sandbox that handles the heavy lifting of security teams. Every day, 400,000 professionals use our platform to investigate incidents and streamline threat analysis on Windows and Linux cloud VMs.
Advantages of ANY.RUN
- Real-time detection: Within roughly 40 seconds of uploading a file, ANY.RUN can detect malware and automatically identify many malware families using YARA and Suricata rules.
- Interactive analysis: Unlike many automated solutions, ANY.RUN allows you to interactively engage with the virtual machine directly through your browser. This interactive capability helps prevent zero-day exploits and sophisticated malware that can evade signature-based detection.
- Cost-Effective: For businesses, ANY.RUN’s cloud nature translates into a cost-effective solution, as it doesn’t require any setup or maintenance effort from your DevOps team.
- Great for onboarding new security team members: ANY.RUN’s intuitive interface allows even junior SOC analysts to quickly learn how to analyze malware and extract indicators of compromise IOCs.
If these capabilities sound beneficial for you or your team, give ANY.RUN a try. The best part is — we offer a completely free starter plan and a personalized demo for your team.








0 comments