Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases
Tycoon 2FA is a phishing-as-a-service (PhaaS) platform designed to bypass multi-factor authentication (MFA) protections, particularly targeting Microsoft 365 and Gmail accounts. Its advanced evasion techniques and modular architecture make it a significant threat to organizations relying on MFA for security.
|
Phishingkit
Type
:
|
Unknown
Origin
:
|
|
1 August, 2023
First seen
:
|
27 February, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 August, 2023
First seen
:
|
27 February, 2026
Last seen
:
|

 793
793
 0
0

 482
482
 0
0

 2730
2730
 0
0
This Adversary-in-the-Middle (AiTM) phishing kit became known in 2023, with significant updates observed through 2025. The PhaaS model allows even low-skilled attackers to deploy sophisticated phishing campaigns
Tycoon 2FA can intercept user credentials and session cookies to bypass MFA, enabling unauthorized access to accounts even with additional security measures. Organizations using cloud services are at the most risk.
The kit is distributed via Telegram channels starting at $120 for 10 days, with prices varying by domain extension (.com, .net, .org, etc.).
Tycoon 2FA has a multi-stage attack process through social engineering and compromised infrastructure, including phishing emails and QR codes; redirects to fake login pages; exploitation of legitimate services (e.g., Milanote for project collaboration).
Read detailed breakdown of Tycoon2FA’s defense evasion techniques
Victims are directed to a counterfeit login page mimicking Microsoft 365 or Gmail, where they unknowingly enter their credentials. A custom CAPTCHA (previously Cloudflare Turnstile, now HTML5 canvas-based) filters out automated bots and security tools, ensuring only human users proceed.
If MFA is enabled, Tycoon 2FA acts as a man-in-the-middle, relaying MFA prompts and capturing session cookies in real time upon successful authentication. These cookies grant attackers unauthorized access to the victim's account without needing further credentials. Attackers reuse session cookies to bypass security controls and access accounts even if credentials are reset.
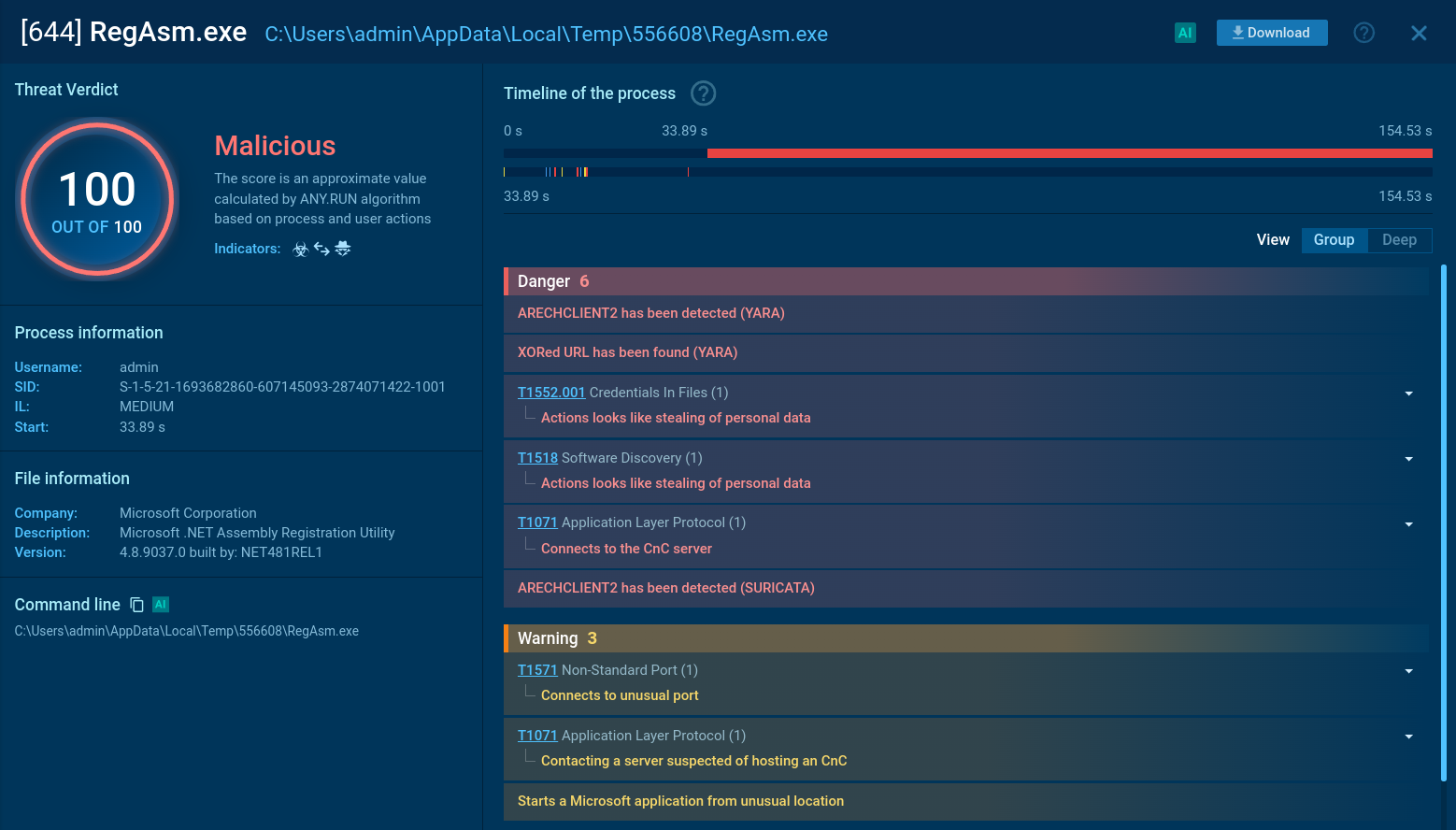
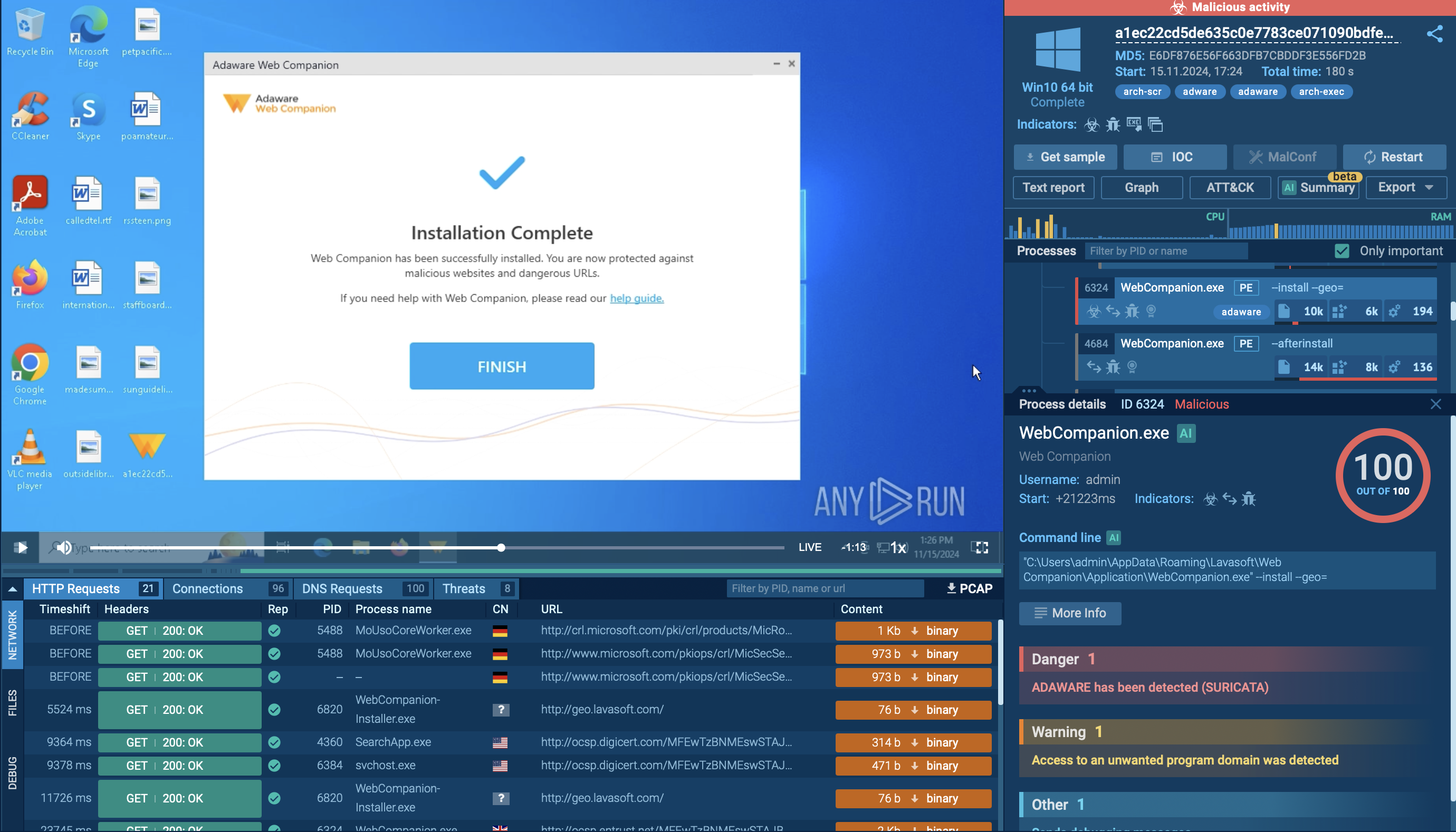
ANY.RUN’s Interactive Sandbox, trusted by over 500,000 threat analysts and 15,000 SOC teams, contains an impressive collection of malware samples featuring Tycoon 2FA attacks. Let’s scrutinize the phish kit’s strategy and tactics on an illustrative analysis session.
View the analysis and gather actionable data.
 Tycoon 2FA sample in ANY.RUN's Interactive Sandbox
Tycoon 2FA sample in ANY.RUN's Interactive Sandbox
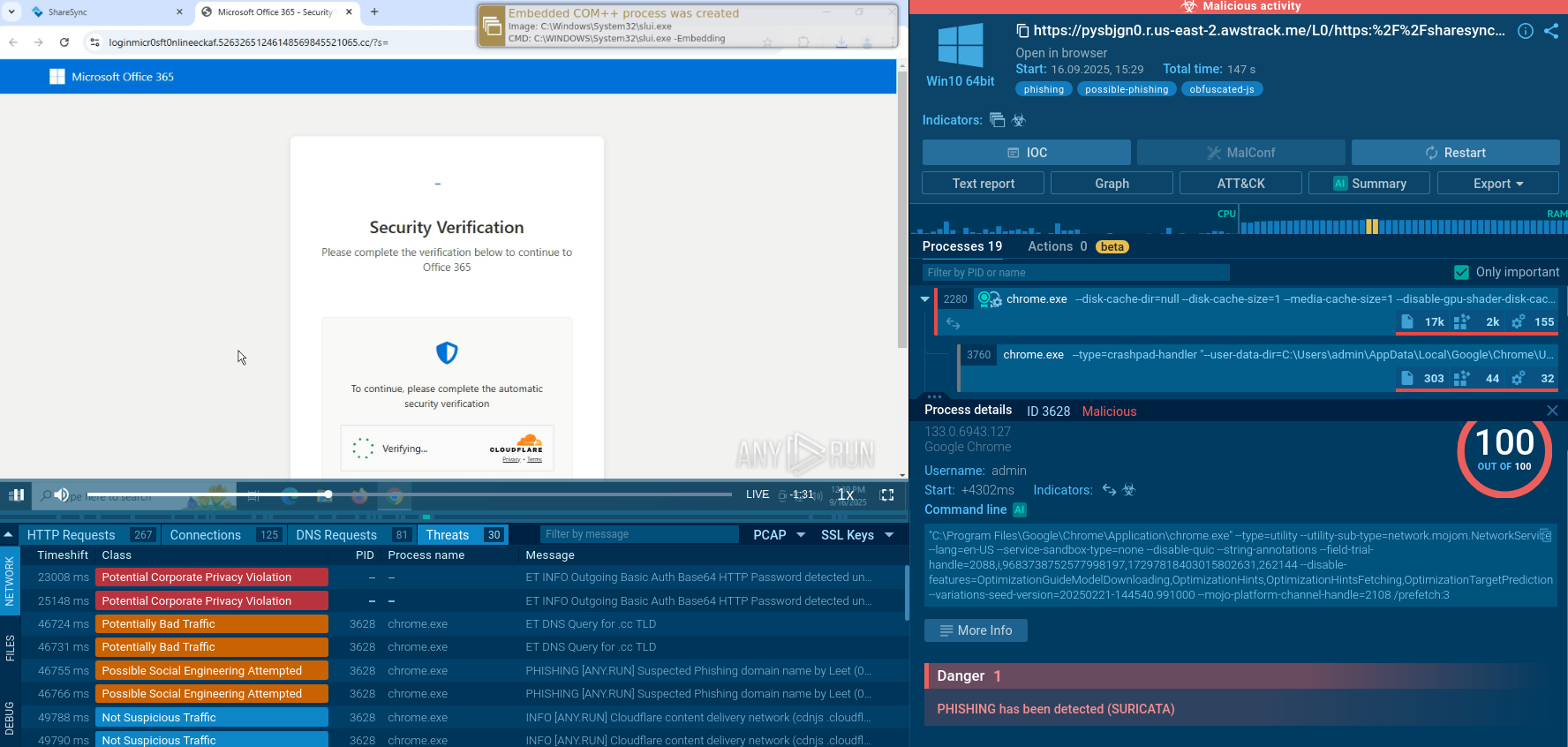
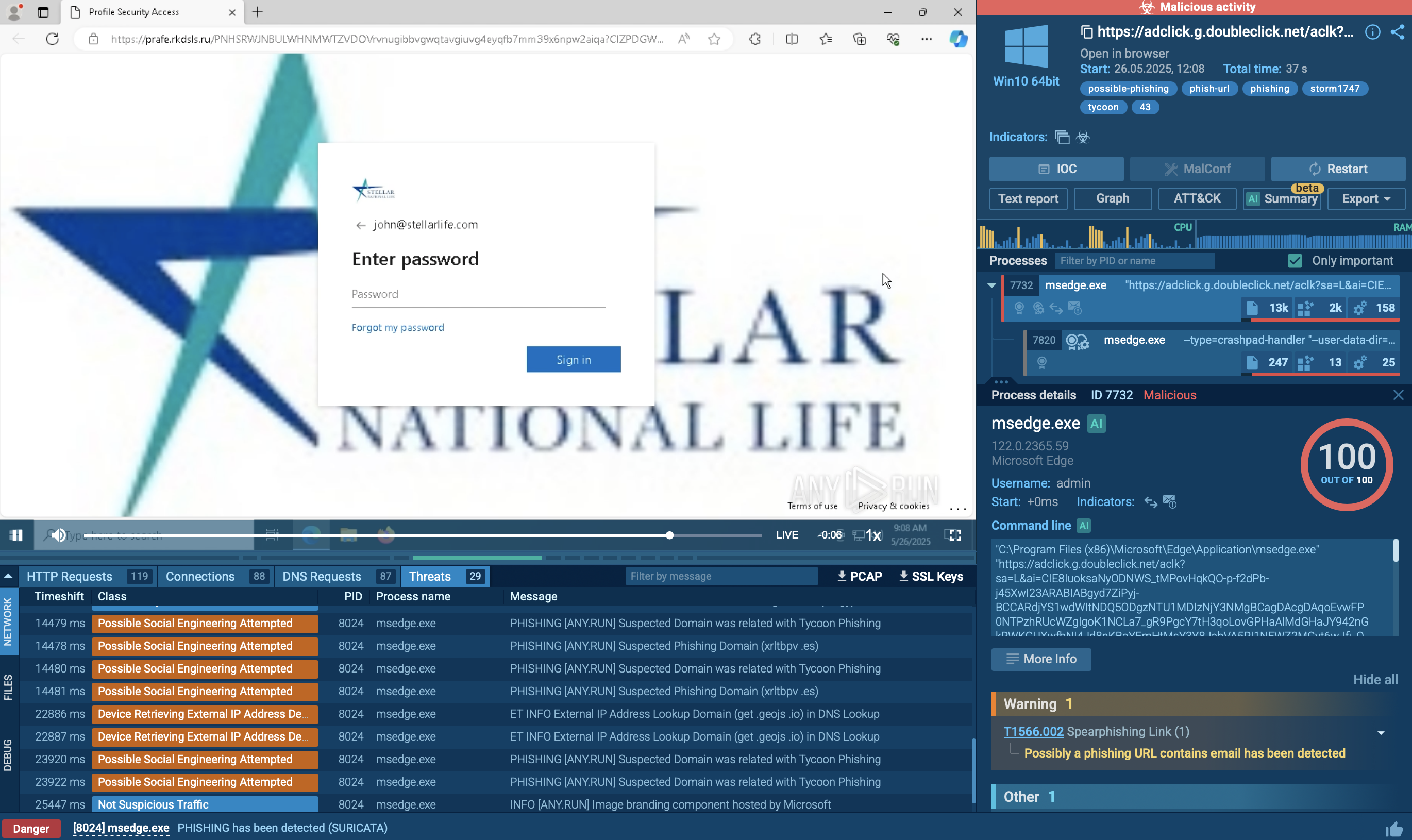
The execution chain typically begins with phishing emails or QR codes that direct victims to malicious URLs. These messages often impersonate trusted services and may be sent via legitimate platforms to enhance credibility. When a victim clicks the link, they are redirected through several intermediate pages, including CAPTCHA challenges such as reCAPTCHA or Cloudflare CAPTCHA, which are used to block bots and avoid automated detection systems.
ANY.RUN supports Automated Interactivity (ML) capable of handling such challenges in submitted tasks, including those sent via API. These CAPTCHA steps also help attackers evade sandbox detection by filtering out non-human traffic. During this redirection process, the kit performs environment checks by analyzing IP addresses, user agents, and browser fingerprints to identify security researchers or automated tools. These detections are ineffective against ANY.RUN, which uses residential proxies to simulate legitimate user traffic. If suspicious activity is detected, the visitor is redirected to a benign website to avoid raising alarms.
After passing the environment checks, the victim is taken to a fake login page that closely imitates Microsoft 365 or Gmail authentication portals. These pages are tailored to match the victim’s organization by modifying branding elements using legitimate services. Built with obfuscated and randomized JavaScript and HTML, these pages are designed to evade detection by signature-based security tools.
When the victim submits their credentials and, if prompted, an MFA code, the phishing kit captures the information in real time and forwards it to the legitimate Microsoft or Gmail servers via a reverse proxy. This enables the attackers to intercept valid session cookies, effectively bypassing MFA. With these session tokens, attackers gain persistent, unauthorized access without needing to reauthenticate.
To complicate analysis, payloads and exfiltrated data are often encrypted using AES, while URLs are randomized and malicious resources are delayed until after CAPTCHA completion to avoid detection by automated scanners.
To counter Tycoon 2FA, organizations should adopt a proactive, multi-layered defense strategy informed by threat intelligence. Solutions like ANY.RUN’s Threat Intelligence Lookup help to detect and block known Tycoon 2FA infrastructure like domains and IPs at the network edge.
Make an easy entrance to Tycoon 2FA investigation by searching the threat by the name via TI Lookup. View any analysis session to get acquainted with the phish kit operators’ TTPs and gather indicators of compromise to set up alerts and defenses.
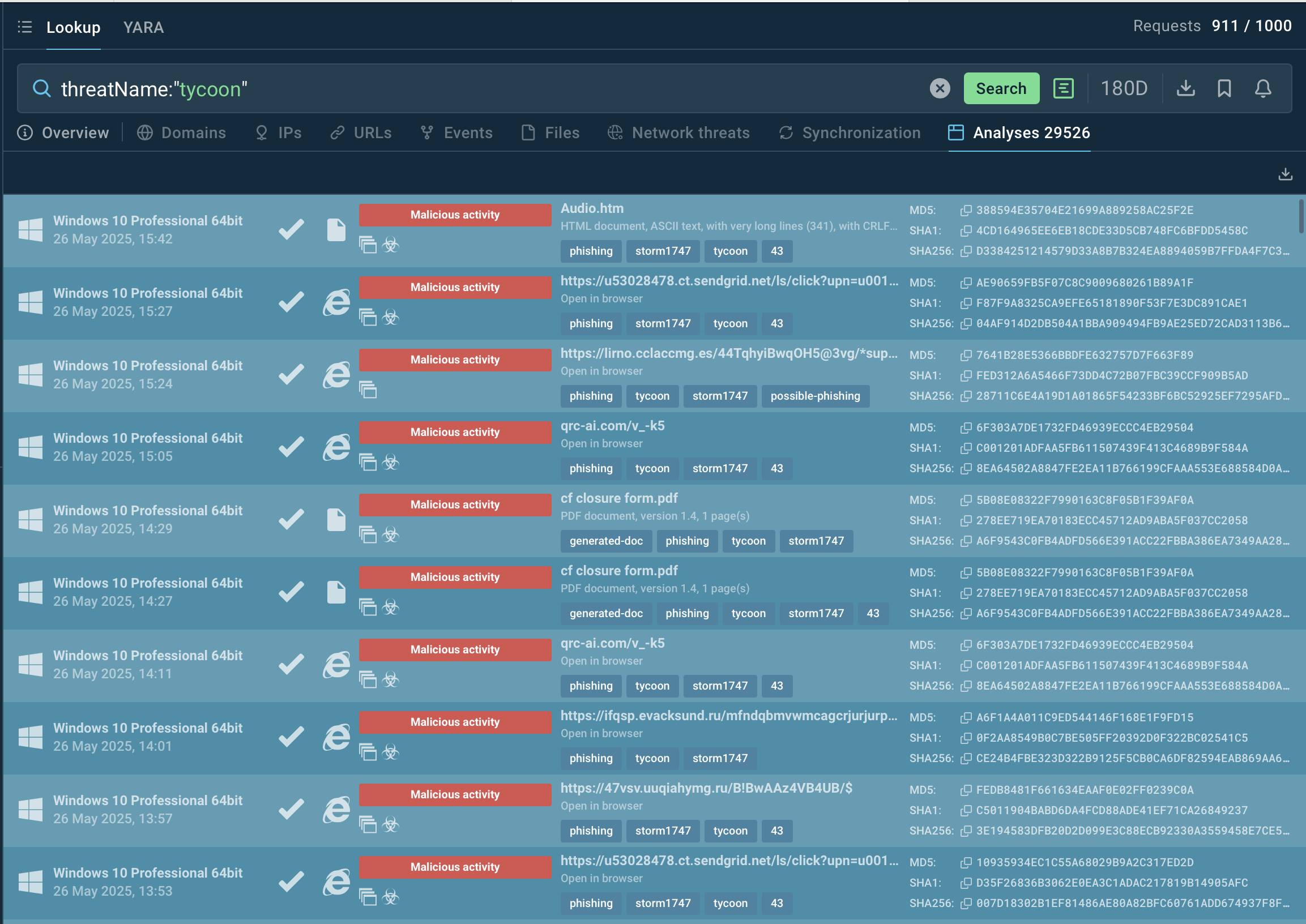 Sandbox malware analyses featuring Tycoon 2FA
Sandbox malware analyses featuring Tycoon 2FA
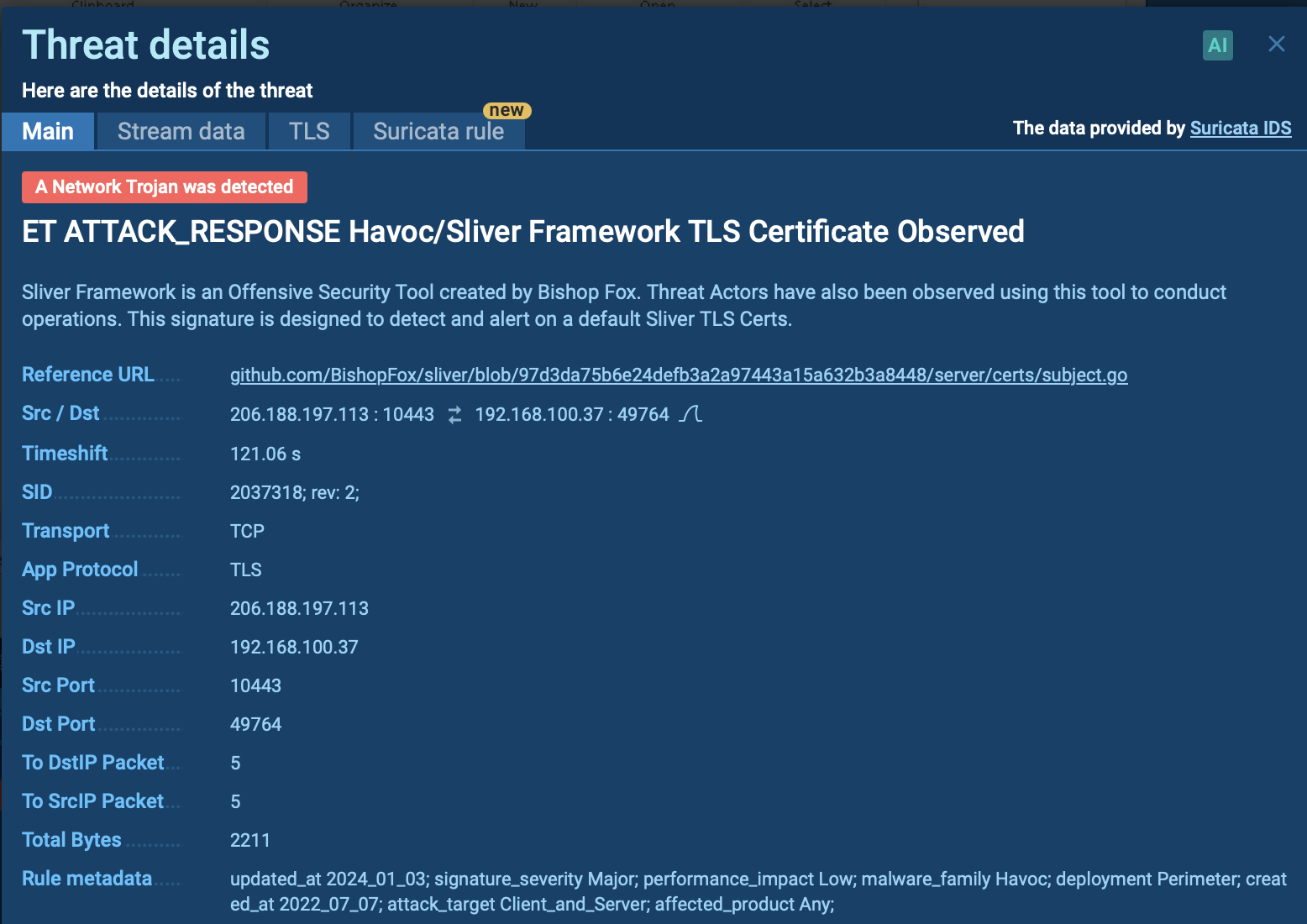
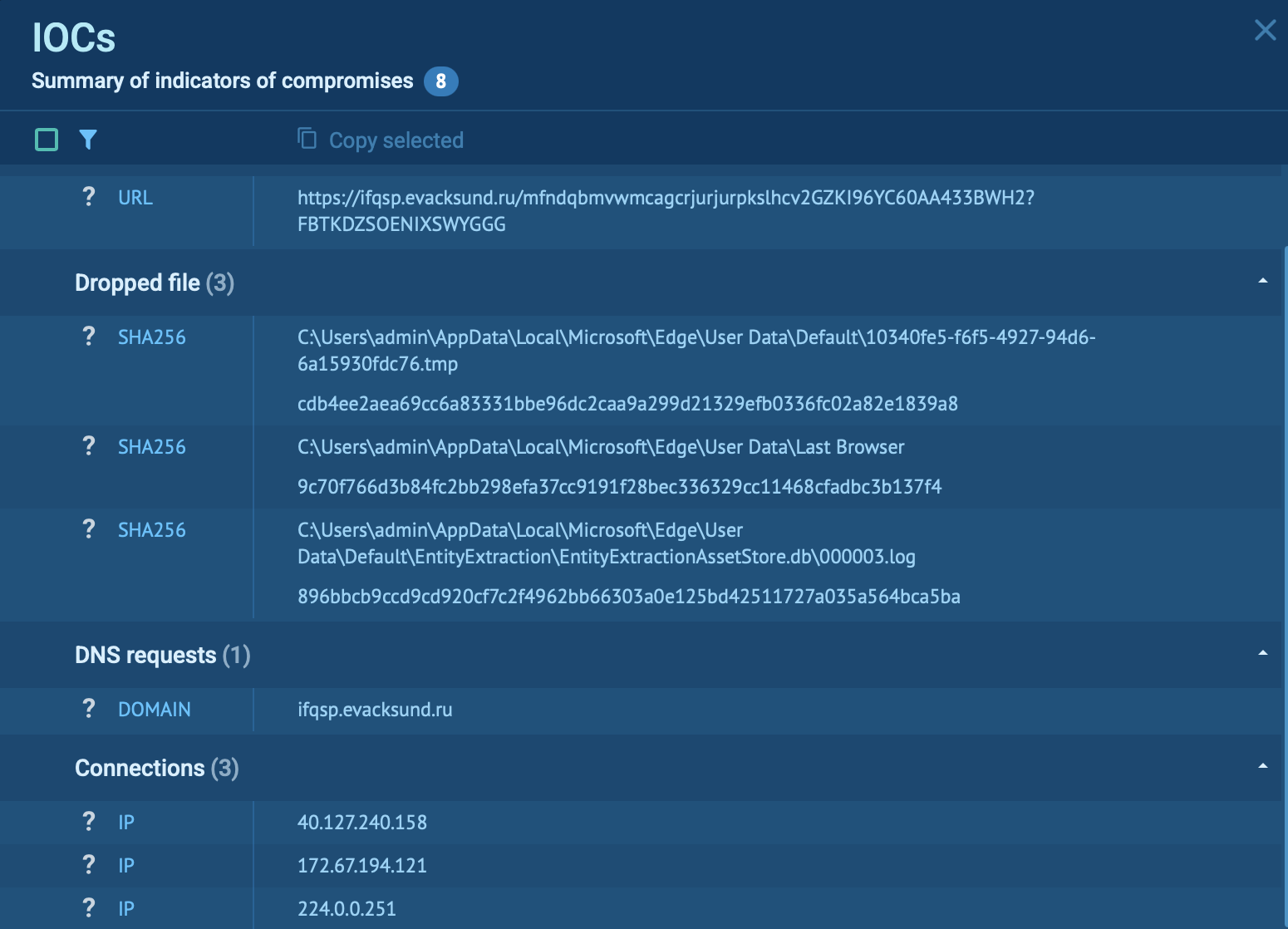 Tycoon 2FA IOCs extracted from a malware sample
Tycoon 2FA IOCs extracted from a malware sample
Tycoon 2FA is an evolved phishing kit that poses a significant threat due to its ability to bypass MFA, leverage legitimate infrastructure, and employ advanced evasion techniques like invisible Unicode obfuscation, custom CAPTCHAs, and anti-debugging scripts. Its ease of use and scalability make it accessible to a wide range of cybercriminals, amplifying its impact.
Detection and counteraction require a combination of behavioral monitoring, advanced threat intelligence, phish-resistant MFA, and user awareness.
Use Threat Intelligence Lookup to shoot Tycoon 2FA on approach: start with 50 trial searches.