Think you can trust every email that comes from a business partner?
Unfortunately, that’s no longer guaranteed; attackers now slip into legitimate threads and send messages that look fully authentic.
That’s exactly what happened in a new case uncovered by ANY.RUN researchers; a trust takeover inside a real executive discussion about a document awaiting final approval.
By detonating the suspicious message, the investigation exposed the full execution chain and linked it to a broader phishing campaign already active since 2025.
Let’s find out how this attack worked, and how your team can detect similar threats faster, safely, and without disrupting business processes.
TL;DR
- Initial access: Likely compromise of a contractor mailbox already involved in the thread, enabling conversation hijacking inside a real C-suite approval flow.
- Attack chain: SCA phishing email → 7x forwards → phishing link → Cloudflare Turnstile antibot page → Turnstile-protected phishing page → EvilProxy AiTM for Microsoft credential theft.
- Evasion: Multi-step redirects + Turnstile mean the final phishing content is only exposed during real execution, not simple URL or static checks.
- Detection: Behavioral detonation is required to see the full chain and confirm intent; static analysis alone is unlikely to flag it reliably.
- Campaign context: Pivoting domains, URL paths (/bot, /robot), and patterns like loginmicrosoft* in TI Lookup maps this incident to a broader EvilProxy campaign, and supports hunting + detection engineering with both IOCs and IOBs.
New Phishing Attack Overview
This incident started as something that looked completely normal from the outside: a live email discussion about a document waiting for final approval. It didn’t contain any strange subject line or a cold intro. Just a reply that appeared to belong in the thread.
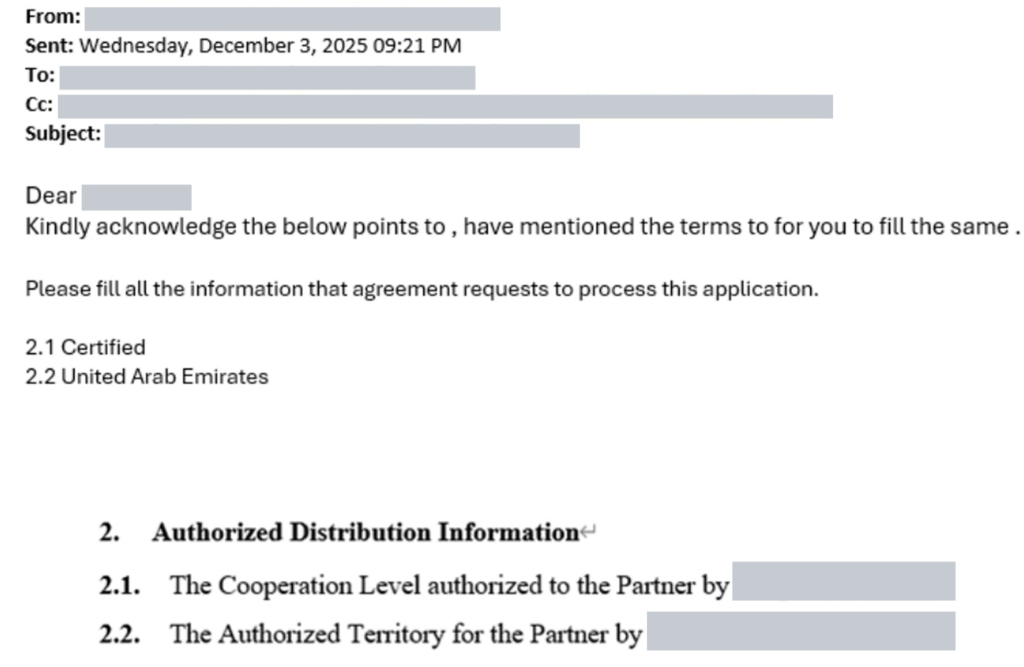
What made it dangerous was the access path. The attacker likely got into a supplier-side mailbox (a contractor’s sales manager account) and used that trusted identity to respond directly inside the active discussion among C-suite executives about a document pending final approval.
- Initial access (suspected): Compromised contractor account that was already involved in business correspondence.
- Delivery method: Conversation hijacking inside an existing C-suite thread.
- Goal: Steal Microsoft credentials through a fake authentication page.
- Protection evasion: Layered redirects and anti-bot gating designed to keep the content “clean” until a real user interacts.
- Campaign link: Indicators connected to a broader operation consistent with the EvilProxy phishkit, active since early December 2025, with primary targeting in the Middle East.
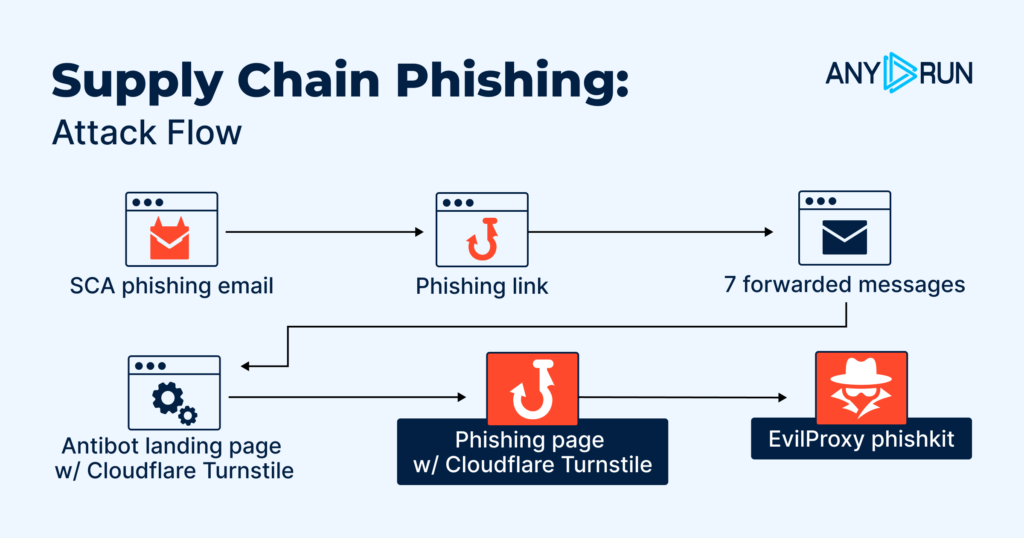
Execution Chain Observed Step-by-Step
SCA phishing email → 7 forwarded messages → phishing link → anti-bot landing page (Cloudflare Turnstile) → phishing page (Cloudflare Turnstile) → EvilProxy
1) SCA phishing email (initial entry into the supply chain)
The campaign begins with a message designed to look like routine business communication from the supply chain side (contractor/vendor context). The goal at this stage is simple: land the first message in an inbox that’s already part of real business workflows, so later steps inherit trust.
2) 7 forwarded messages (conversation momentum + legitimacy)
The attacker didn’t need to write a convincing pitch. The thread did that work for them. As the email was forwarded across stakeholders, it picked up real context, real names, and the natural “we’re already discussing this” signal that makes people drop their guard. By the time it landed with executives, the link looked like just another step in a legitimate approval flow, not a new request that needed to be questioned.
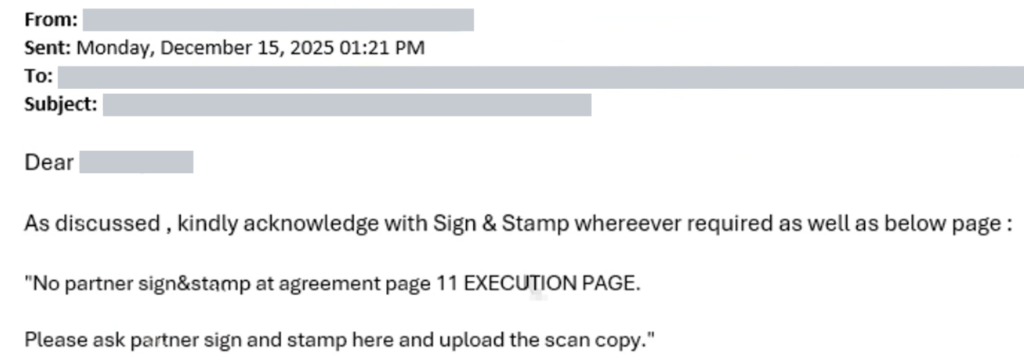
3) Phishing link (the moment of action)
The link is placed where it looks expected: tied to “review,” “final approval,” or “document access.” It’s not framed as suspicious or urgent in a classic way.
4) Anti-bot landing page with Cloudflare Turnstile (filtering for real users)
After clicking, the victim doesn’t land on the phishing form immediately. First, they hit an intermediary page protected by Cloudflare Turnstile. This step helps the attackers in two ways:
- It screens out automated scanners and some security crawlers.
- It delays exposure of the real phishing content until a human completes the check.
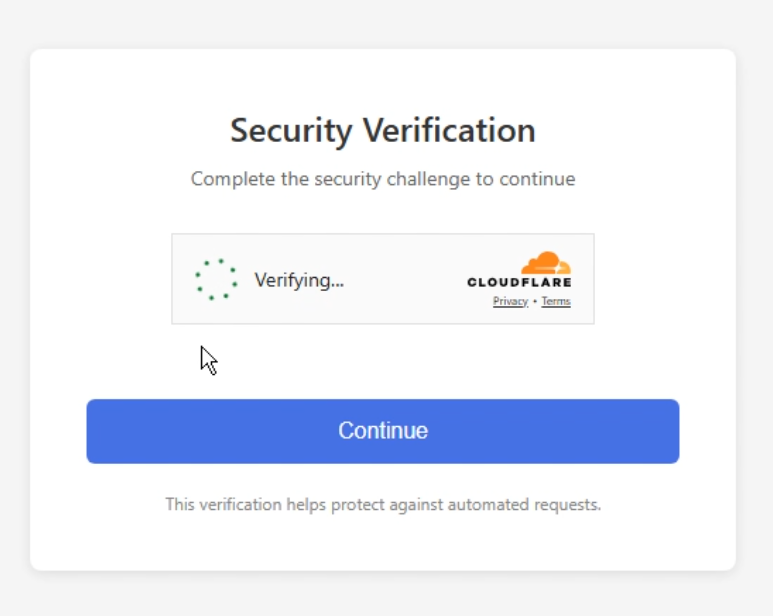
5) Phishing page with Cloudflare Turnstile (second gate before credential capture)
Once the user passes the first gate, they’re redirected to the phishing page; often with another Turnstile challenge. This extra layer reduces automated analysis success even more and increases the chance that the only “real” views of the credential page come from actual targets.

6) EvilProxy (credential theft via adversary-in-the-middle)
After passing the gates, the user is presented with a fake Microsoft authentication flow that’s built to steal credentials in a way that works even when users have strong security habits. The intent is to capture what the attacker needs to access the account and continue the intrusion, often by expanding access to other threads, mailboxes, and internal resources.
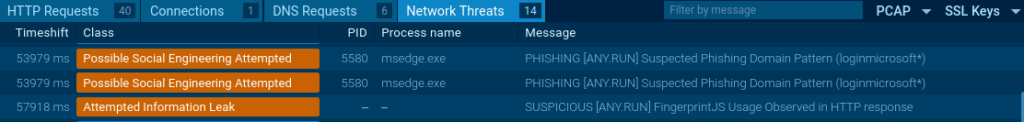
Why Thread-Hijack Phishing is a Different Class of Business Risk
Supply chain phishing has changed. Modern campaigns run like full operations, built to blend into real workflows and scale quietly across vendors and partners. The biggest shift is simple: these attacks exploit business trust, not technical vulnerabilities.
What makes this wave different:
- Layered social engineering: Targets are guided through multiple steps that feel normal in day-to-day work (review → approval → sign-in), so the “risk moment” gets buried inside routine actions.
- Real conversation hijacking: Attackers reply inside an existing email thread, borrowing the credibility of a live discussion instead of trying to create it from scratch.
- PhaaS-like infrastructure: Behind the scenes, the flow runs on multi-layer redirect chains, anti-bot gates, and rapidly changing domains; the kind of scale and setup that increasingly mirrors phishing-as-a-service platforms.
- Low-noise, high-impact execution: Fewer messages, more credibility, and a shorter window for defenders to catch it before credentials are handed over.
How SOC Teams Can Spot and Confirm These Attacks Faster
Thread-hijack phishing is built to pass “quick checks.” The only reliable way to beat it is to run a repeatable cycle that moves from early signals → proof → context → action → prevention. With ANY.RUN, teams can validate suspicious activity safely, uncover full campaigns, and strengthen detections in minutes, instead of hours.
Here’s how to do it step-by-step:
1. Reveal the True Intent Behind Suspicious Links and Files
Once a thread-hijack email lands in someone’s inbox, the biggest mistake teams make is relying on quick checks. These attacks are built to look clean until the moment a real person interacts. That’s why the first step is always safe detonation.
Running the link or file in ANY.RUN’s controlled environment exposes the real behavior of the attack, redirects, anti-bot gates, phishing pages, injected scripts, even the steps that remain hidden from static scans. In most cases, the full flow becomes visible in under 60 seconds.
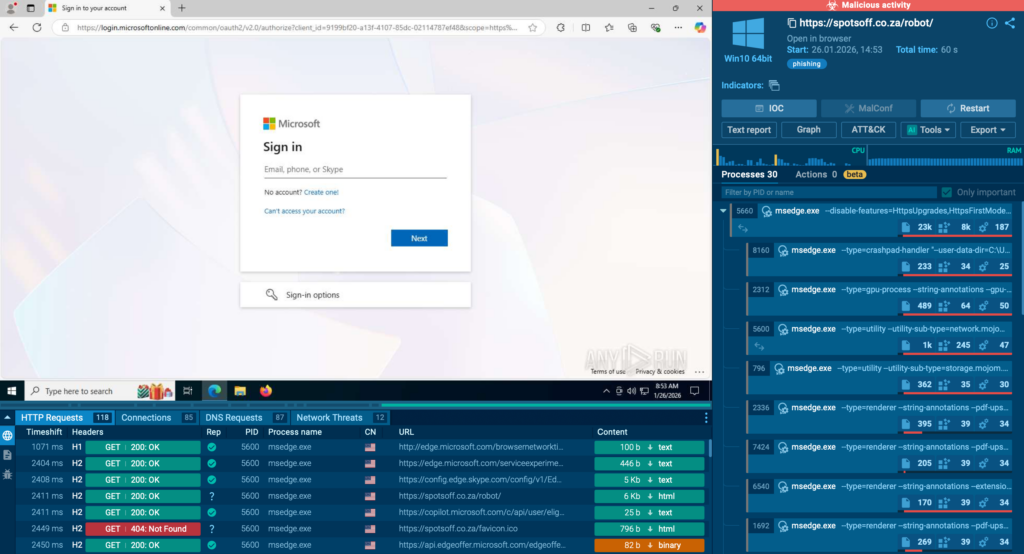
This is where teams get their first advantage:
- 94% report faster triage, because they are no longer guessing or waiting for confirmation.
- The verdict becomes evidence-based, not subjective.
- High-pressure approvals stop turning into high-risk blind spots.
Revealing intent early reduces workload for Tier-1 and prevents escalation loops that quietly drain SOC time and budget.
2. Investigate Deeper and Connect the Attack to the Bigger Picture
Modern supply chain phishing rarely comes as a one-off case. Behind a single malicious link usually hides an active campaign, a whole infrastructure layer, and hundreds of related samples circulating across industries.
The main advantage of ANY.RUN’s ecosystem is that a single sample is never isolated.
It lives inside a massive dataset enriched by 600,000+ analysts and telemetry from 15,000+ organizations.
This allows teams to immediately understand:
- Which domains and URLs belong to the same actor
- Whether similar attacks have been active in the past days or months
- How the infrastructure evolves
- Which TTPs define the campaign
- Whether the activity ties back to known kits (like EvilProxy)
This transforms one incident into a campaign-level view; crucial for prioritization, threat hunting, and strategic response planning.
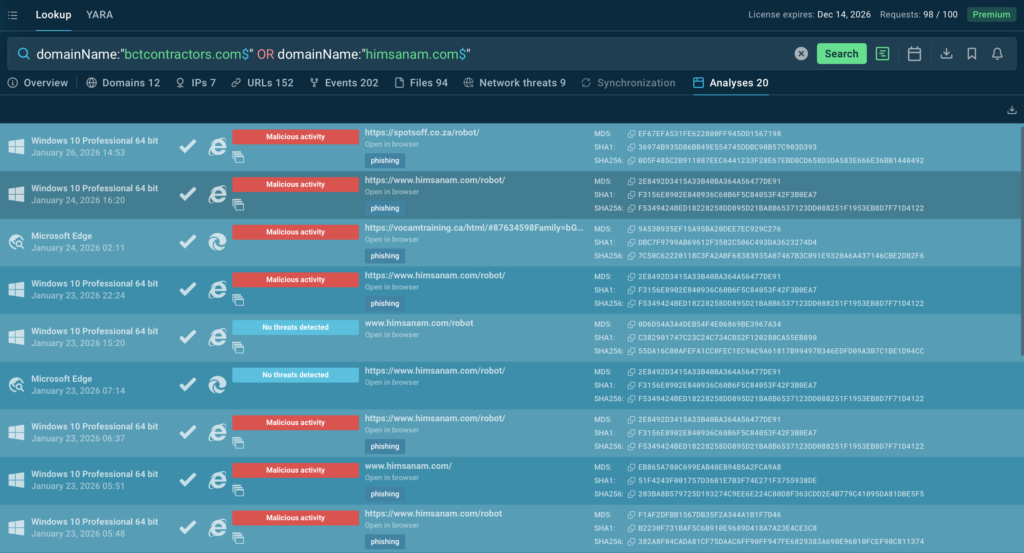
Use these TI Lookup search queries to find indicators and deeper campaign insights related to this phishing attack:
This level of visibility supports business needs too: clear audit trails, stronger reporting for leadership, and transparent decision-making during incidents.
3. Stay Ahead of the Campaign with Fresh Threat Data Inside Your Existing Platform
Once you link the attack to a broader operation, the next step is staying ahead of it. Thread-hijack campaigns shift domains and redirect paths constantly, so teams need threat data that updates just as fast.
Fresh indicators extracted from ongoing detonation sessions by TI Feeds can flow directly into the tools your team already uses, SIEM, SOAR, email security, and detection pipelines.
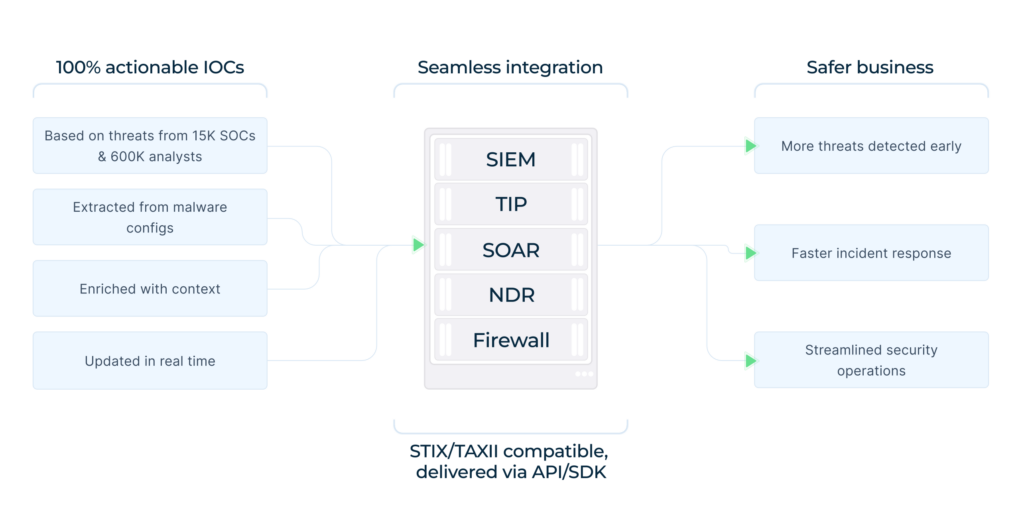
This gives defenders the ability to:
- See redirect and infrastructure changes early
- Strengthen correlation rules with fresh, high-confidence IOCs
- Validate threat-hunting ideas with real, recent telemetry
This ongoing flow transforms reactive detection into proactive monitoring, allowing teams to reduce the window between attack launch and discovery.
About ANY.RUN
ANY.RUN is a part of modern SOC workflows, easily integrating into existing processes and strengthening the entire operational cycle across Tier 1, Tier 2, and Tier 3.
It supports every stage of analysis; from exposing real behavior during detonation to enriching investigations with broader threat context and delivering continuous intelligence that helps teams move faster and make confident decisions.
Today, more than 600,000 specialists and 15,000 organizations rely on ANY.RUN to accelerate triage, reduce unnecessary escalations, and stay ahead of evolving phishing and malware campaigns.







0 comments