Cyber attacks are becoming more complex and frequent, targeting organizations of all sizes. To counter these threats effectively, organizations need insights into their adversaries’ methods and capabilities.
This is where threat intelligence comes in.
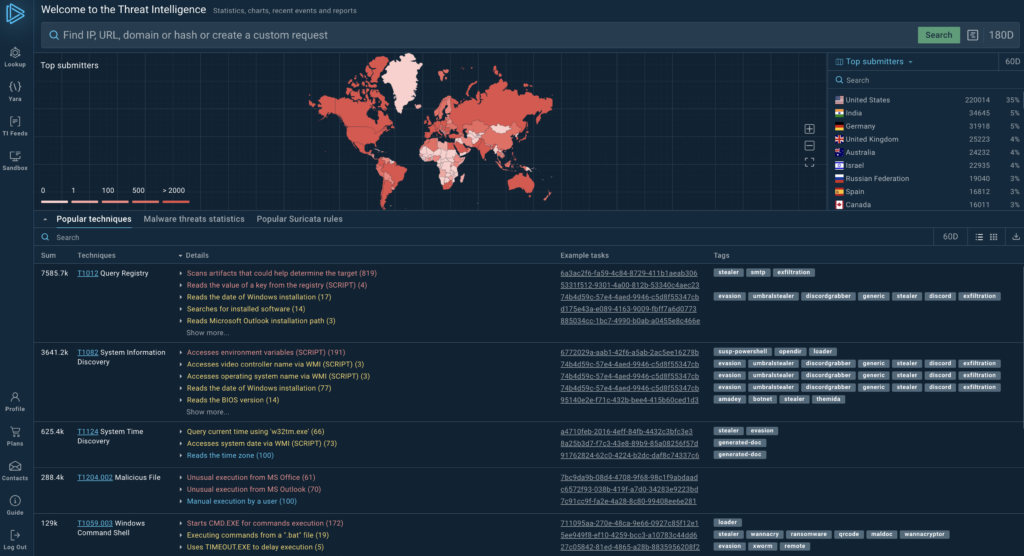
Threat intelligence involves analyzing data about potential or current attacks to understand and defend against adversaries more effectively. It’s not just about collecting information – it’s about extracting useful insights to guide security decisions.
Key elements of threat intelligence include:
- Gathering data from various sources
- Analyzing patterns and trends
- Putting threats in context
- Sharing relevant information with security teams
- Integrating intelligence into security tools and processes
By using threat intelligence, organizations can spot and address risks before they turn into full-scale attacks. This proactive approach helps strengthen overall security and makes better use of resources.
The Importance of Cyber Threat Intelligence
Threat intelligence plays a crucial role in modern cybersecurity for these key reasons:
- Proactive Defense: It helps organizations anticipate and prepare for potential attacks, rather than just reacting to incidents after they occur.
- Resource Optimization: With a clearer picture of the threat landscape, security teams can focus their efforts on the most relevant risks to their specific environment.
- Faster Incident Response: When an attack happens, having context about the adversary and its methods allows for quicker containment and recovery.
- Improved Decision-Making: Threat intelligence provides valuable input for both tactical and strategic security decisions, from updating firewall rules to planning long-term security investments.
- Regulatory Compliance: Many industries require organizations to stay informed about potential threats as part of their compliance obligations.
Who Benefits from Threat Intelligence?
Organizations of all sizes and across various industries can leverage TI to enhance their cybersecurity posture.
At the forefront, security analysts and SOC teams use threat intelligence daily. It helps them investigate incidents more effectively, identify potential threats before they materialize, and fine-tune detection capabilities. With better intelligence, these professionals can prioritize alerts more accurately, reducing false positives and improving response times.
For CISOs and other security leaders, threat intelligence serves as a strategic tool. It guides decisions on security investments, shapes policy development, and provides crucial information for board-level risk discussions. This high-level perspective allows leaders to align security strategies with overall business objectives.
But the value of threat intelligence extends beyond the technical teams:
- Risk management teams use it to assess and mitigate organizational risk more accurately.
- Executives gain a clearer understanding of the security landscape, enabling more informed decision-making.
- DevOps teams incorporate threat intelligence into the development process, addressing potential vulnerabilities early in the software lifecycle.
Even smaller organizations without dedicated security personnel can benefit. By tapping into threat intelligence services, they stay informed about relevant threats and can take appropriate precautions.
The Value of Comprehensive Cyber Threat Intelligence
Comprehensive cyber threat intelligence provides a holistic view of the global threat landscape, drawing from diverse sources to paint a complete picture.
This approach combines data from open web sources, dark web monitoring, malware analysis, and industry-specific feeds.
The real power of comprehensive threat intelligence lies in its ability to connect the dots between seemingly unrelated pieces of information. By analyzing data from multiple angles, security teams can uncover hidden patterns and relationships that might otherwise go unnoticed. This deeper understanding allows organizations to anticipate potential threats and take preemptive action.
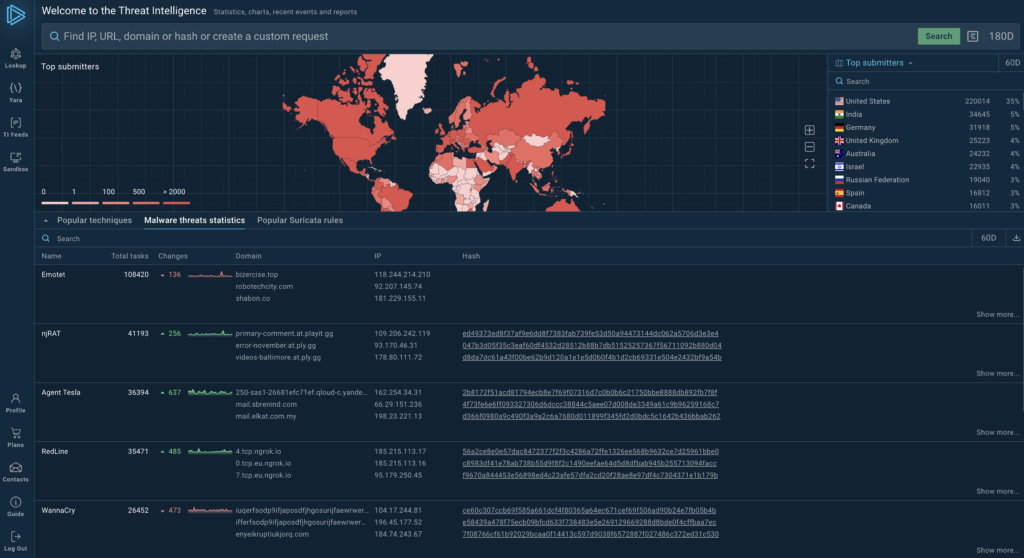
One key benefit of comprehensive threat intelligence is its ability to provide context. Raw data about threats is of limited use without proper context. Comprehensive intelligence adds layers of meaning by considering factors such as:
- The attacker’s motivations and capabilities
- The targeted industry or organization type
- The broader geopolitical or economic context
This contextualization turns mere information into actionable insights, enabling more informed decision-making at all levels of an organization.
Another advantage of a comprehensive approach is its adaptability. Cyber threats evolve rapidly, and a narrow focus on a single type of intelligence can leave blind spots. By drawing from a wide range of sources, comprehensive threat intelligence helps organizations stay agile and responsive to new and emerging threats.
Three Ways To Deliver Threat Intelligence
Threat intelligence comes in 3 main forms, and each serves a different need within an organization.
Strategic Intelligence
Strategic intelligence provides a big-picture view of the threat landscape. It focuses on broad trends, emerging threats, and long-term patterns that could impact an organization’s security posture.
This type of intelligence typically takes the form of comprehensive reports or briefings. It might cover topics like the rise of certain types of attacks in a particular industry, or the emergence of new threat actors targeting specific regions.
Security leaders and executives use strategic intelligence to inform high-level decision-making. It helps shape overall security strategy, guide resource allocation, and align security initiatives with broader business objectives.
Tactical Intelligence
Tactical intelligence operates on a shorter time scale, supporting day-to-day security operations. It provides practical, actionable information that security teams can use to detect and respond to immediate threats.
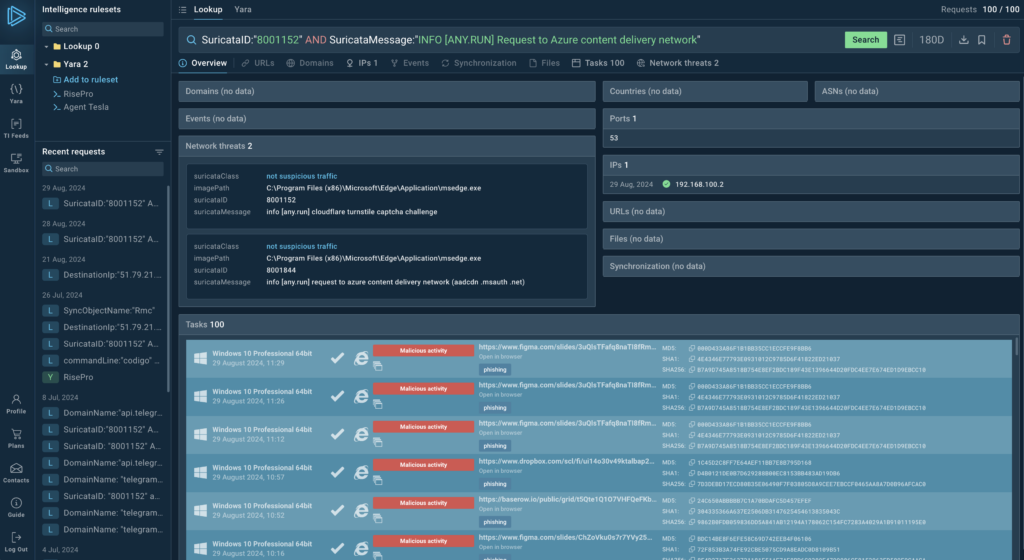
Tools like ANY.RUN’s Threat Intelligence Lookup and YARA Search fall into this category. They allow analysts to quickly assess potential threats by providing detailed information about specific indicators of compromise, malware samples, or suspicious activities.
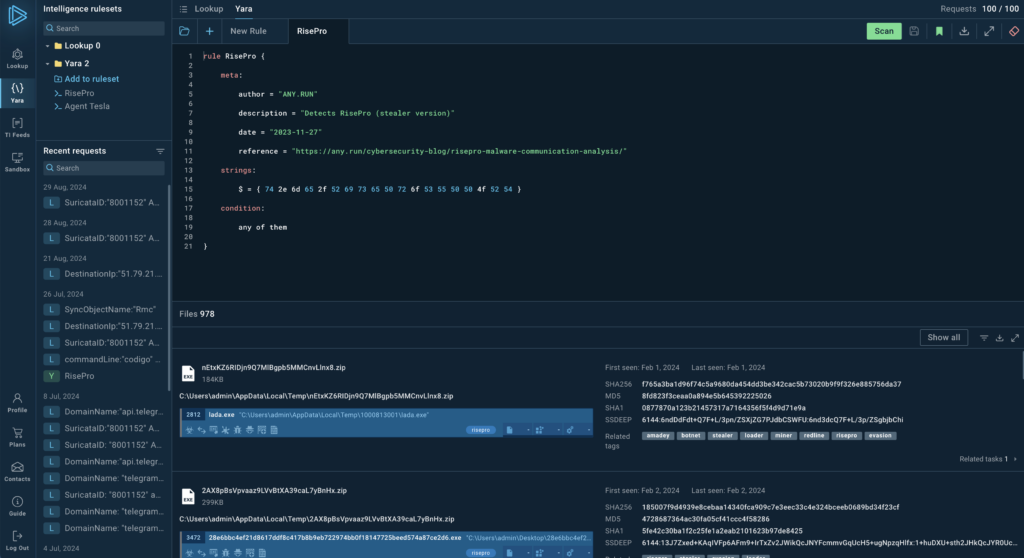
Tactical intelligence helps security teams prioritize their efforts, investigate incidents more effectively, and make informed decisions about immediate security measures. It bridges the gap between high-level strategy and technical implementation.
Technical Intelligence
Technical intelligence is the most granular form of threat intelligence. It consists of specific technical indicators that can be directly integrated into security systems for automated detection and blocking of malicious activity.
This often takes the form of threat data feeds, which provide real-time streams of information about known malicious IP addresses, domains, file hashes, and other technical indicators. These feeds can be ingested by security information and event management (SIEM) systems, intrusion detection systems (IDS), and other security tools.
By leveraging technical intelligence, organizations can automate much of their threat detection and response processes. This not only improves the speed and efficiency of security operations but also frees up human analysts to focus on more complex tasks that require deeper investigation and analysis.
Wrapping up: The Impact of Threat Intelligence
Threat intelligence has become a cornerstone of modern cybersecurity strategies. As cyber threats continue to evolve in complexity and frequency, organizations that effectively leverage threat intelligence will be better positioned to protect their assets and respond to incidents.
Key points to remember:
- Threat intelligence enables a shift from reactive to proactive cybersecurity.
- It benefits various roles across an organization, from analysts to executives.
- Comprehensive intelligence provides a fuller picture of the threat landscape.
- Three main delivery methods: strategic, tactical, and technical intelligence.
- TI is valuable for organizations of all sizes, including those without dedicated. security teams.
About ANY.RUN
If you’re part of the ANY.RUN community or a current user, you know we focus on cloud-based interactive sandboxing. With over 16,000 submissions daily—most of which are new malware samples—our community is on pace to collect more than 50 million unique IOCs every quarter in 2024.
We are harnessing this vast amount of data to help organizations boost their proactive security through our Threat Intelligence offerings:
If you’re interested in ANY.RUN’s Threat Intelligence solutions, don’t hesitate to contact our sales team. They can provide pricing details and answer any questions you have about the product.










0 comments