Indicators of compromise (IOCs) are essential for proactive cybersecurity. They help you identify and respond to threats effectively. However, getting high-quality IOCs can be difficult, as the best source for this data is the malware’s code, analyzing which often requires hours of intensive work.
ANY.RUN sandbox users know that config-extracted indicators can be easily found in MalConf reports.
Now, these are also available through Threat Intelligence Lookup.
Quick Brief on TI Lookup
Threat Intelligence Lookup from ANY.RUN is a service with continuously updated threat data pulled from millions of sandbox analysis sessions.
It receives the latest information on phishing and malware samples uploaded to ANY.RUN’s Public submissions database by our international community of 400,000 security professionals.
Whether you are investigating an incident or hunting for emerging threats, TI Lookup allows you to:
- Search through the latest malware and phishing threat data
- Refine your searches using over 40 different parameters and combinations + wildcards
- Get results quickly, each with a corresponding sandbox session
- Use YARA Search with a built-in rule editor
- Integrate with your security systems using API
With TI Lookup, you can improve your cybersecurity efforts with precise and actionable IOCs. This not only helps in identifying current threats but also aids in predicting and preventing future attacks.
Access IOCs Extracted from Malware Configurations in TI Lookup
TI Lookup now includes indicators of compromise that our analyst team has manually extracted from malware configurations of reversed-engineered samples.
Currently, you can access config-extracted IOCs for 79 malware families. Each of these is labeled with the “malconf” tag, making them easy to identify.
Let’s explore a few use cases to show you how the new feature works.
Malnconf Use Cases in TI Lookup
Case 1: Finding C2 Domains of Remcos
With TI Lookup, you can find “malconf” indicators for a certain malware family. Use this combined search query to find C2 domains for Remcos:
The service lists over 250 domains found in sandbox sessions featuring Remcos.
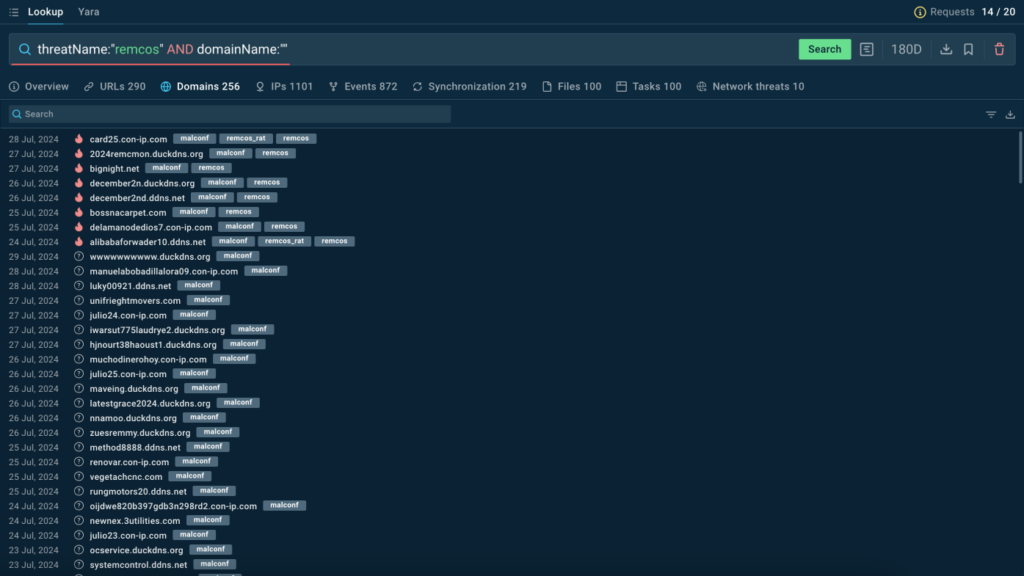
At the top, we can see domains labeled with the “malconf” tag.
Case 2: Discovering More AsyncRAT Indicators
We can also start with IOCs from a Config report provided by the sandbox.
Let’s say we want to investigate an IP address found in the configuration of an AsyncRAT sample.
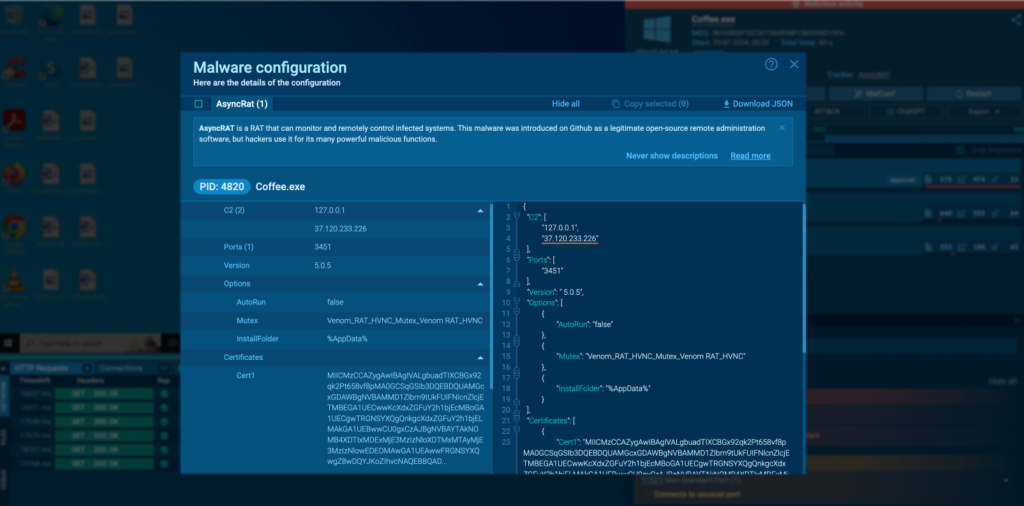
We can submit the following search query to TI Lookup:
The service returns events, files, destination ports, and sandbox sessions related to the indicator.
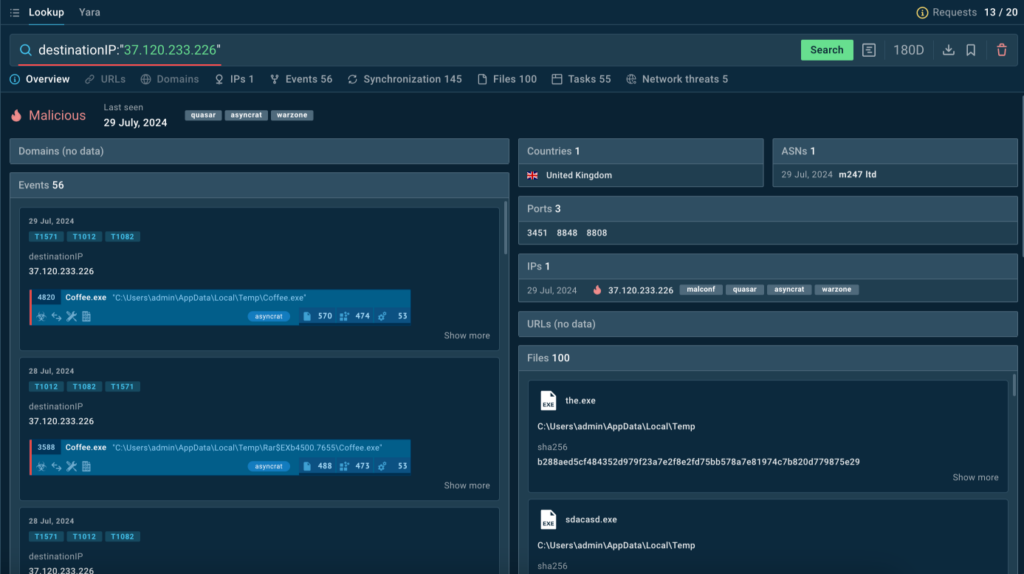
This can help us collect hash sums and other IOCs belonging to malware, as well as to find other malware families used by attackers.
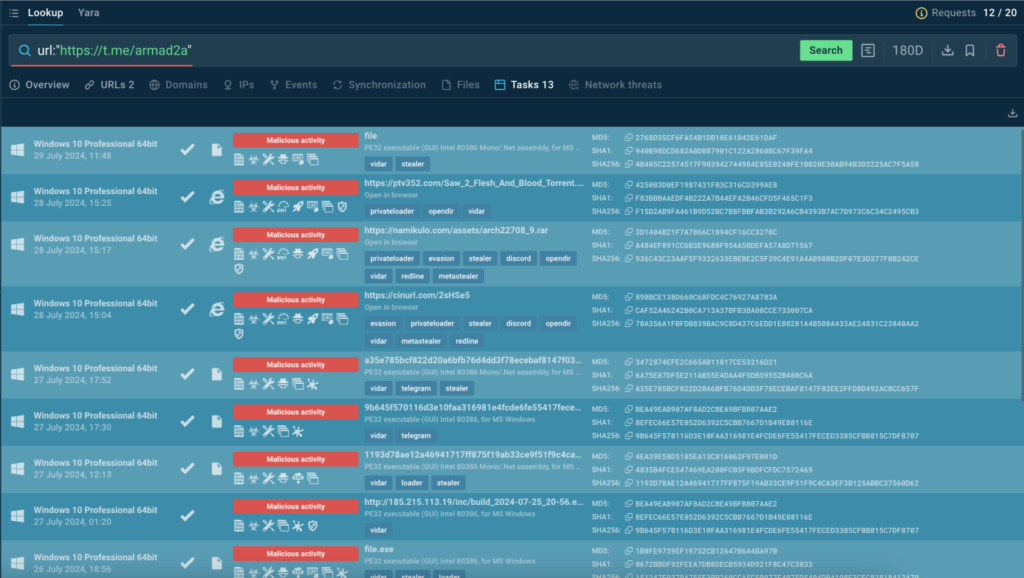
Case 3: Investigating a Vidar URL
URLs are another type of indicator we can get from a sandbox Config report to search for more threat information via TI Lookup.
Let’s pull a URL from a Vidar analysis session.
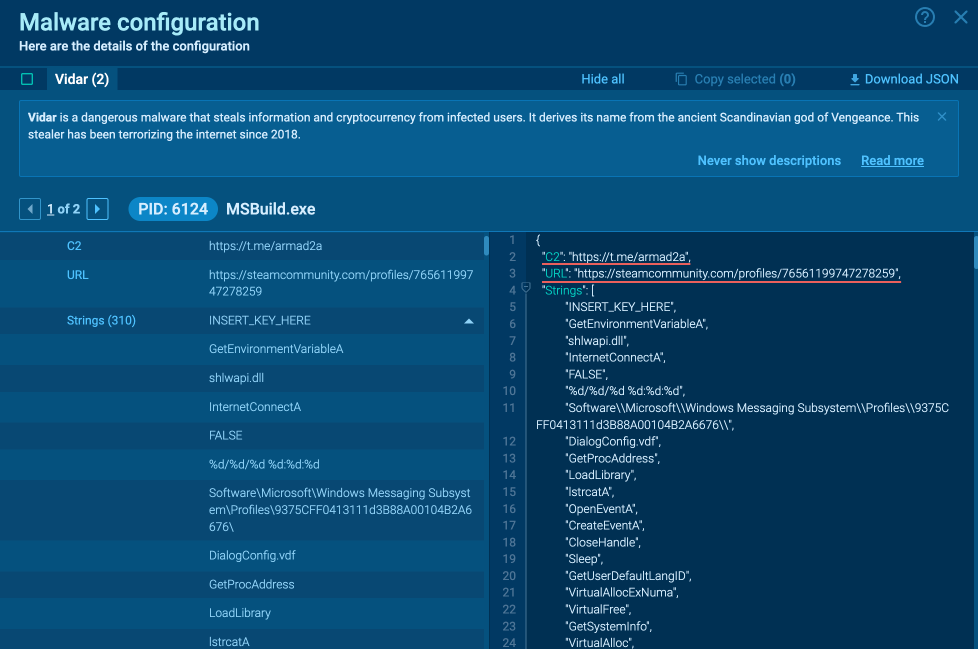
With it, we can create the following query:
Using TI Lookup, we can discover more samples with indicators and see that Vidar is often deployed through PrivateLoader.
About ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.







0 comments