Researchers report about a new campaign that’s delivering a variety of malware, by exploiting GitHub, FileZilla and potentially other legitimate services.
What’s happening?
Adversaries are impersonating 1Password, Bartender 5, Pixelmator Pro, and other software on GitHub and FileZilla to deliver multiple threats in a massive campaign.
The campaign uses multiple stealers, allowing it to target Windows, MacOS, and Android users. Researchers believe that hackers are centrally controlling these families from a shared C2.
The following table shows which malware families affect which systems:
Vidar and Lumma are both modern info-stealers.
Vidar, a Malware-as-a-Service (MaaS), first appeared in the wild in 2018. Lumma is even newer — experts have known about it since late 2022 or early 2023.
Breaking down the attack chain
Malvertising and SEO poisoning drives victims to fake repositories made to look like legitimate software. But in reality, the repositories contain malware-infected software.
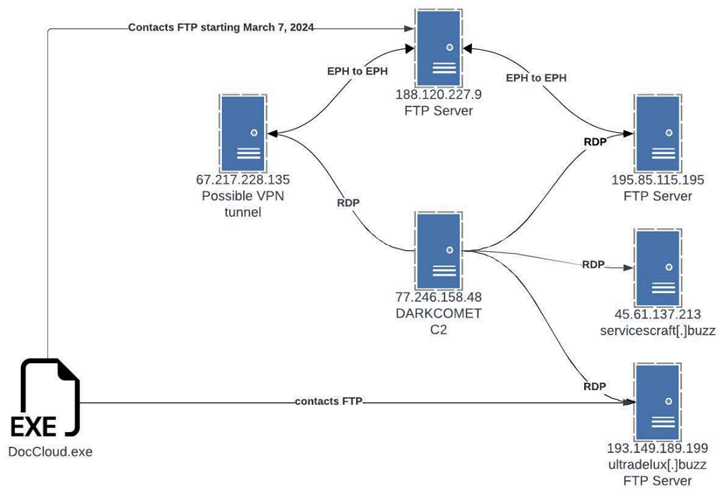
Another case of GitHub abuse
This campaign shows that hackers can exploit services users already trust. The tactic has been gaining popularity recently. Read about a new version of Redline being distributed via GitHub, and how STRRAT and VCRAT used GitHub for distribution.
The same group behind this campaign also distributes Rhadamanthys malware. The infection process is similar: victims are lured to fake websites that then redirect them to malicious hosts on Bitbucket and Dropbox, where the hackers have uploaded the malware.
Vidar — a popular threat
Vidar has been gaining popularity as of late, according to our threat data:
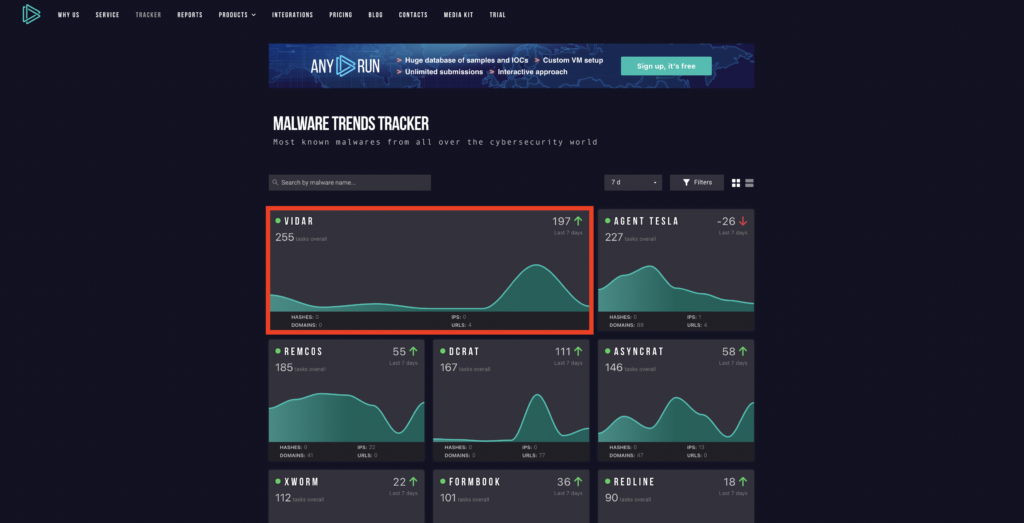
The ANY.RUN Malware Trends Tracker shows the popularity of malware families from the data that 400,000 researchers submit to our sandbox for analysis. It shows that at the time of writing Vidar’s detections have spiked.
Analyzing Lumma in ANY.RUN
In this anlysis session in ANY.RUN, we can see that a program called Lazesoft Recover My Password Professional Edition Setup immediately begins its malicious activities upon starting.
It injects into the system process BitLockerToGo to evade process-based defenses and potentially elevate privileges.
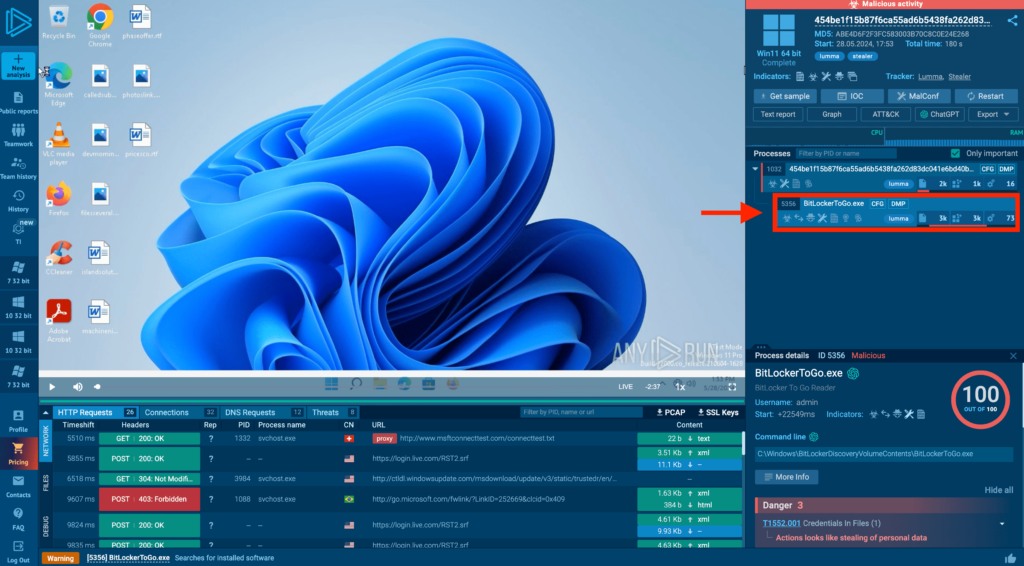
BitLockerToGo is a feature of Microsoft’s BitLocker full-disk encryption software that specifically targets removable drives, such as USB flash drives and external hard drives.
The malware was detected by both Yara and Suricata rules.
About ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Advantages of ANY.RUN
ANY.RUN helps you analyze threats faster while improving detection rates. The platform detects common malware families with YARA and Suricata rules and identifies malware behavior with signatures when detection by family is not possible.
With ANY.RUN you can:
- Detect malware in under 40s.
- Interact with samples in real time.
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior.
- Collaborate with your team
- Scale as you need.
Try the full power of ANY.RUN for free










0 comments