Every security alert represents a decision point. Act too slowly, and a threat becomes a breach. Act without context, and analysts drown in noise. At the center of both failure modes is a single, often underestimated process: alert enrichment.
Key Takeaways
- Alert enrichment is the operational multiplier. Its quality determines the effectiveness of every other SOC investment — detection tools, SIEM rules, and analyst headcount all underperform when enrichment is slow or fragmented.
- Manual enrichment is a structural problem, not a skills problem. Even experienced analysts lose 20–30 minutes per alert to fragmented, multi-platform investigations.
- Static intelligence and live behavioral analysis cover different failure modes. Threat Intelligence Lookup handles known indicators at speed. The Interactive Sandbox handles the unknown with depth.
- Enrichment improvements are directly measurable in business terms. MTTD, MTTR, false positive rate, and analyst retention are all affected by enrichment quality.
The Seconds That Define a Breach
Alert enrichment is the practice of layering contextual intelligence onto raw security alerts (IP reputation, domain history, file behavior, attacker TTPs) so that analysts can make fast, accurate decisions. It sounds operational. But its downstream effects are deeply strategic: mean time to respond, analyst capacity, false-positive rates, and ultimately, whether the security function is perceived as a cost center or a competitive asset.
For the business, the difference is simple: enriched alerts lead to faster containment and fewer incidents. Poorly enriched alerts lead to delays, escalations, and avoidable losses.
From Raw Alerts to Actionable Decisions
Alert enrichment sits at the crossroads of detection, analysis, and response. It connects telemetry from SIEM, EDR, email security, and network controls with external and internal context such as indicators, attacker behavior, infrastructure, and historical activity.
When enrichment works well:
- Tier 1 analysts understand what they are seeing;
- Tier 2 can quickly validate intent and scope;
- Tier 3 focuses on root cause and prevention, not data gathering.
Considering business objectives, effective enrichment directly affects:
- Mean time to triage and respond,
- Incident escalation rates,
- Analyst productivity and burnout,
- Cost of incidents and downtime,
- Confidence in SOC reporting.
In short, alert enrichment defines how efficiently security investments translate into risk reduction.
Leadership increasingly demands that security spend be justified in operational terms. Alert enrichment is one of the most concrete levers available. It is measurable, improvable, and its effects cascade through the entire security operation. Organizations that treat it as a background task, rather than a core process deserving investment and optimization, consistently underperform on every metric that matters.
Where SOCs Go Wrong with Alert Enrichment
Many SOCs struggle because enrichment is:
- Fragmented across multiple disconnected sources;
- Manual and time-consuming;
- Focused only on static indicator reputation;
- Performed too late in the escalation chain;
- Lacking behavioral validation;
- Without behavioral evidence, analysts often guess severity.
The business consequences of poor enrichment practices compound over time. The most direct impact is an extended breach window. Organizations with slow enrichment workflows consistently show longer dwell times before threat detection and containment.
Beyond breach economics, there are workforce consequences. Analyst teams experiencing enrichment bottlenecks burn out faster, make more errors under time pressure, and escalate inappropriately.
Finally, poor enrichment undermines executive reporting. When MTTR and false positive rates are poor, security teams struggle to demonstrate value to the board. This erodes confidence in the function and creates pressure for headcount reductions at precisely the moment when operational capacity is already strained.
Transforming Alert Enrichment into a Business-Aligned Efficiency Driver
The path from dysfunctional enrichment to a streamlined, high-performance process runs through threat intelligence. High-performing SOCs enrich alerts with two types of validation:
- Historical attack data,
- Live behavioral analysis.
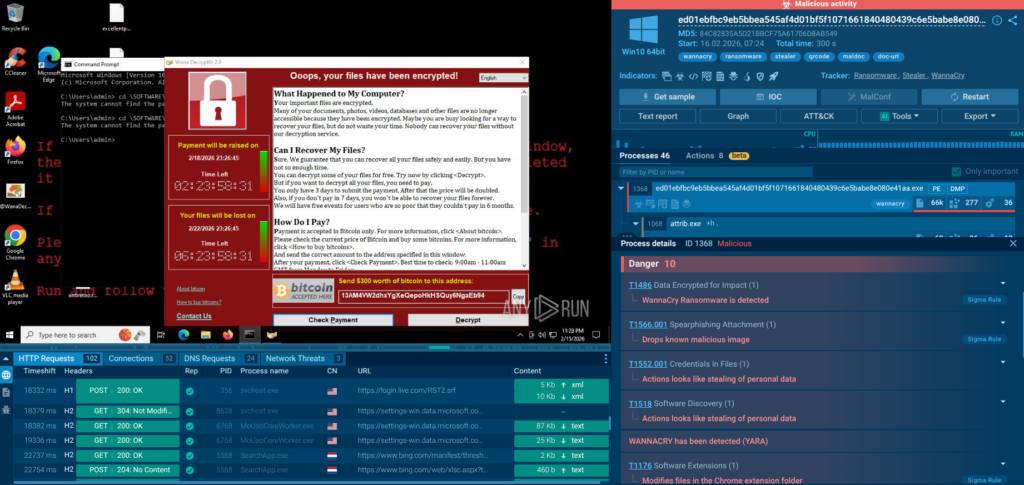
ANY.RUN offers two distinct but deeply complementary capabilities that, together, cover the full spectrum of SOC enrichment needs: the Interactive Sandbox for live behavioral analysis of unknown threats, and Threat Intelligence Lookup for instant, structured context on known indicators.
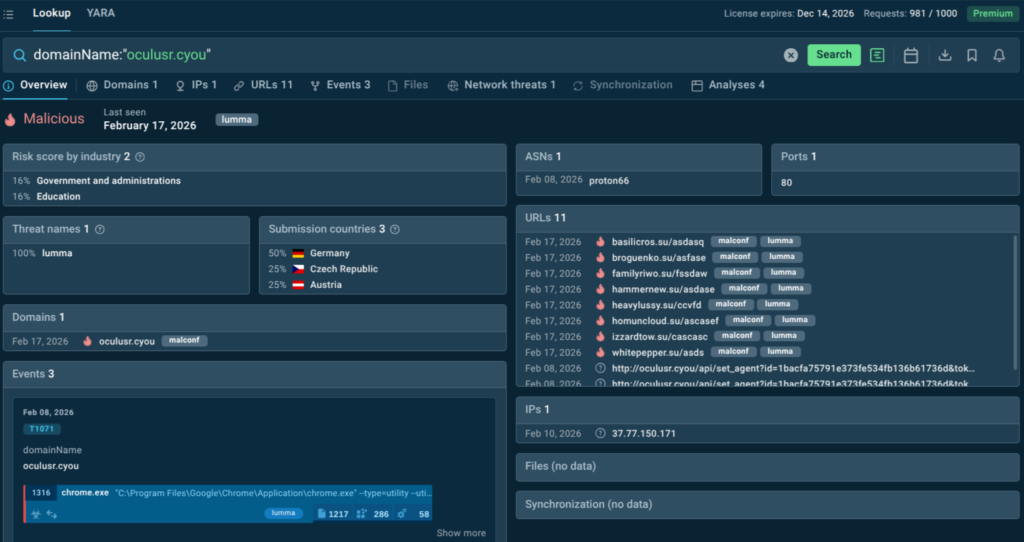
Understanding each one, and how they interconnect, is key to applying them effectively across SOC tiers. With intelligence-backed and behavior-validated enrichment:
- Tier 1 gains confidence in decision-making;
- Tier 2 reduces investigation time;
- Tier 3 identifies patterns faster;
- Automation rules become safer;
- Executive stakeholders receive clearer risk assessments.
The SOC shifts from reactive investigation to structured decision-making.
Interactive Sandbox: Live Analysis When Intelligence Doesn’t Exist Yet
The ANY.RUN Interactive Sandbox is a cloud-based malware analysis environment that executes suspicious files and URLs and captures every aspect of their behavior in real time. It allows analysts to interact with the execution clicking through installer dialogs, entering credentials on a phishing page, following multi-stage execution chains.
Check a real-world case inside sandbox
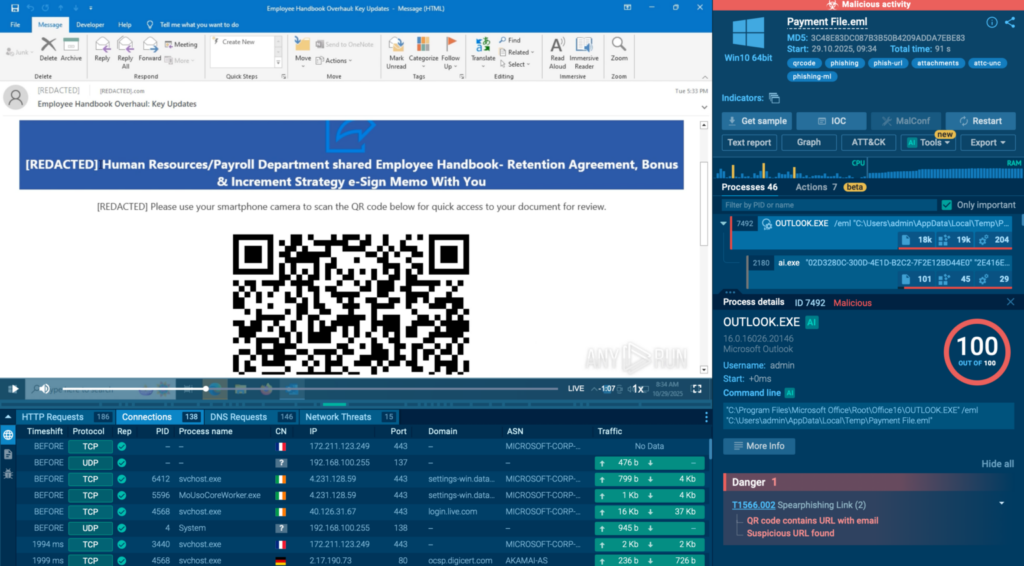
In this sample, a QR code hidden in a phishing email leads to a CAPTCHA-protected page and then to a fake Microsoft 365 login designed to steal credentials. The sandbox detonates the full chain, reveals the phishing infrastructure, and confirms credential theft behavior in seconds.
A sandbox session generates a rich analytical output that invests in alert enrichment and aligns with business objectives:
- Faster mean time to respond (MTTR), minimizing breach dwell time and data loss;
- Reduced false positives by 35-60%, lowering analyst fatigue and operational costs;
- Cost savings from prevented incidents and long-term ROI through proactive defense.
When one analyst runs a new sample, the resulting data immediately becomes available to the entire community and feeds directly into TI Lookup’s dataset.
The Interactive Sandbox is accessible via API, allowing orchestration platforms to trigger sandbox submissions automatically when incoming files or URLs meet defined criteria and to attach the resulting behavioral analysis directly to the incident ticket.
ANY.RUN Threat Intelligence Lookup: Structured Context at Investigation Speed
Threat Intelligence Lookup is a search-driven intelligence platform built specifically to support the investigative and enrichment needs of SOC analysts. It centralizes structured, current intelligence in a single queryable interface.
The platform aggregates data from ANY.RUN’s Sandbox. Analysts can query by over 40 parameters including IP address, domain, URL, file hash, YARA rule, or MITRE ATT&CK technique and receive structured, actionable results in seconds.
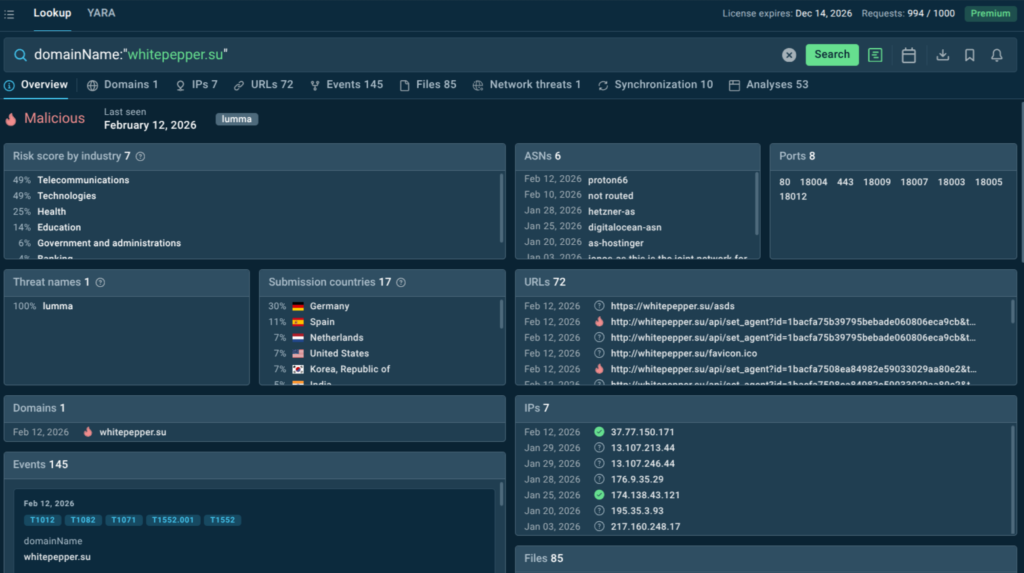
Here we can see an actionable verdict on a domain that triggered alerts: it’s malicious, associated with Lumma stealer, spotted in the very recent attacks that mostly target telecom, IT, and healthcare sectors across Europe.
TI Lookup answers the question: have we (or has anyone in the security community) seen this indicator before, and what do we know about it? The Interactive Sandbox answers the question: what does this artifact do when it runs, right now, in a real environment?
Just switch to the “Analyses” tab in TI Lookup results to see a selection of fresh malware samples featuring the artifact in question and to view analyses for full attack chains, IOCs and TTPs.
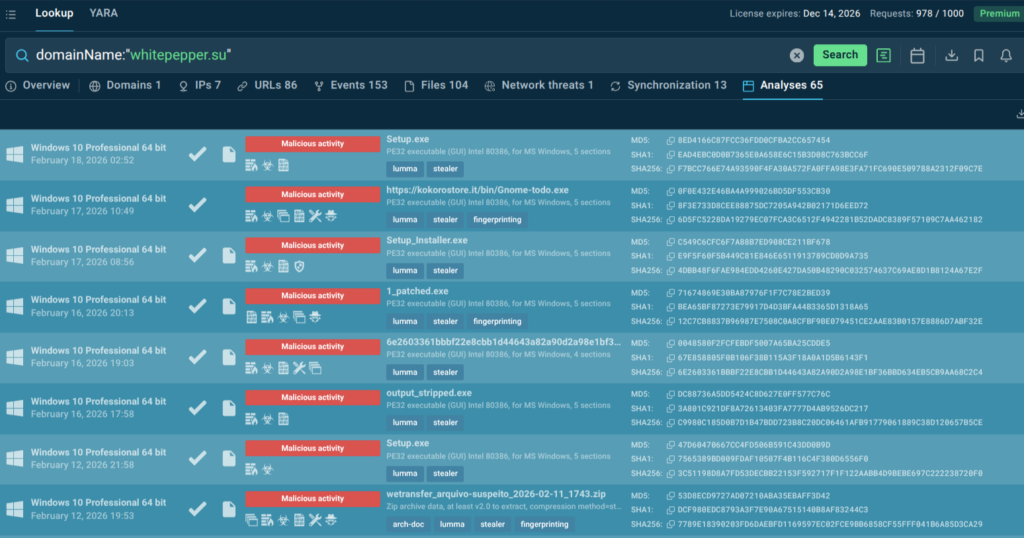
Both capabilities are designed for operational integration. TI Lookup is accessible via a web interface for direct analyst use and via API for integration into SIEM, SOAR, and ticketing platforms, enabling automated pre-enrichment of alerts before they reach a human reviewer.
- Enhances detection accuracy and reduces false positives;
- Cuts investigation time and effort, boosting SOC productivity and minimizing breach impacts;
- Supports compliance and employee training with rich, pre-processed data on malware behaviors and trends.
| TI Lookup | Interactive Sandbox | Synergy Effect & Measured Impact |
|---|---|---|
| Real-world attack artifacts linked to known campaigns | Safe detonation of suspicious files and URLs | Historical evidence + live validation → reduces false positive escalations |
| Mapping of indicators to malware families and attacker techniques | Real-time execution chain and process visibility | Faster malicious intent confirmation → cuts triage time |
| Infrastructure clustering and IOC relationship analysis | Network traffic monitoring and C2 detection | Stronger prioritization logic → improves alert severity accuracy |
| Behavioral context from prior attack executions | Extraction of dropped files and secondary payloads | Earlier full-chain visibility → shortens incident lifecycle |
| Indicator reuse and prevalence insights | Automatic IOC extraction from dynamic analysis | Better-informed automation → reduces manual review workload |
| Cross-campaign artifact correlation for enrichment | Interactive analyst-driven investigation | Higher Tier 1 resolution rate and fewer unnecessary Tier 2 escalations |
One Process, Organization-Wide Impact
Alert enrichment is not an isolated activity that affects only the analyst who performs it. It sits at the center of the SOC’s operational cycle, and its efficiency (or inefficiency) propagates through every tier and every metric. When enrichment is slow, fragmented, or dependent on stale intelligence, every downstream process suffers: triage is less accurate, investigation takes longer, containment is slower, and leadership receives metrics that tell a story of organizational underperformance.
By integrating TI Lookup and the Interactive Sandbox into the enrichment workflow, organizations address the root cause of this underperformance. Together, these capabilities cover the full surface area of enrichment need: instant structured context for known indicators, and live behavioral evidence for the unknown. The former get handled at speed, and the latter are exposed in depth. Neither replaces a professional’s judgment: both elevate it while being integrated into the analyst’s existing workflows.
| SOC Tier | Operational Gain | Business Metric Affected |
|---|---|---|
| Tier 1 — Triage | Faster indicator triage via TI Lookup; Sandbox confirmation for ambiguous indicators; Fewer incorrect escalations; Lower alert fatigue | False positive rate, analyst retention, MTTD |
| Tier 2 — Investigation | Pre-assembled context from TI Lookup; Live behavioral analysis from Interactive Sandbox; TTP mapping accelerates incident scoping | MTTR, incident response cost, breach scope |
| Tier 3 — Threat Hunting | Current campaign intelligence from TI Lookup; Real-time sandbox execution for new variants; Hypothesis-driven, evidence-based hunting | Proactive detection rate, detection rule quality, executive confidence in SOC maturity |
When enrichment velocity increases, the key metrics that define SOC value to the business improve in tandem: MTTD drops because contextual data enables faster threat recognition; MTTR drops because analysts spend less time on data collection and more time on decision-making; false positive rates fall because richer context enables more accurate triage; and analyst capacity increases because the same team can handle greater alert volume without compromising quality.
Conclusion: Enrichment as the Multiplier
Alert enrichment defines whether a SOC operates reactively or strategically. When alerts are supported by real attack intelligence and validated through dynamic analysis, analysts stop guessing and start deciding.
ANY.RUN’s Threat Intelligence Lookup and Interactive Sandbox together provide both precedent and proof. And when enrichment is grounded in both, security becomes faster, clearer, and more aligned with business objectives.
About ANY.RUN
ANY.RUN is part of modern SOC workflows, integrating easily into existing processes and strengthening the entire operational cycle across Tier 1, Tier 2, and Tier 3.
It supports every stage of investigation, from exposing real behavior during safe detonation, to enriching analysis with broader threat context, and delivering continuous intelligence that helps teams move faster and make confident decisions.
Today, more than 600,000 security professionals and 15,000 organizations rely on ANY.RUN to accelerate triage, reduce unnecessary escalations, and stay ahead of evolving phishing and malware campaigns.
To stay informed about newly discovered threats and real-world attack analysis, follow ANY.RUN’s team on LinkedIn and X, where weekly updates highlight the latest research, detections, and investigation insights.
FAQ
Alert enrichment is the process of adding contextual and behavioral information to security alerts to enable accurate prioritization and faster response.
Because it affects response time, escalation rates, analyst workload, and ultimately the cost and impact of security incidents.
It provides real-world attack context, linking indicators to malware families, techniques, and infrastructure observed in live campaigns.
It allows analysts to safely detonate suspicious artifacts and observe real-time execution behavior, reducing uncertainty and guesswork.
Lookup provides historical evidence. Sandbox provides live behavioral proof. Together, they reduce false positives, accelerate investigations, and improve SOC-wide efficiency.







0 comments