The growing dependence on digital technology of modern businesses makes them vulnerable to cyber threats. For three years in a row, manufacturing has stayed the sector most targeted by cyberattacks, IBM reports. Industrial companies suffered from more than 25% of security incidents recorded last year, the majority of them being ransomware attacks.
Investing in comprehensive cybersecurity infrastructure helps prevent substantial financial loss and reputation damage. But enforcing the perimeter is not enough: a proactive approach to threat management is essential.
What is Threat Intelligence
Cyber Threat Intelligence (CTI) is about gathering and analyzing data to spot, understand, and stop current and future threats. Even with strong security teams, just reacting to threats is not enough. Using current, detailed information from outside sources is key to responding effectively.
Cyber threat intelligence provides security teams with data about threats, attacks, and adversaries. It powers decision-making on all levels: operational, tactical, and strategic.
By analyzing threat indicators, tactics, techniques, and procedures of attackers, companies can anticipate attacks rather than just react to them. Vulnerabilities get identified before they can be exploited.
Why Companies Need Threat Intelligence
There are plenty of reasons why industrial enterprises and manufacturing companies may require threat intelligence. Mostly, these reasons relate to the critical role of such companies in the economy on one hand and their specific risks and vulnerabilities on the other:
- They are part of critical infrastructure
Many manufacturing companies are involved in critical infrastructure (e.g., energy, transportation, defense supply chains). Attacking these industries can disrupt essential services, exert political or economic pressure, or fulfill geopolitical goals.
- They are part of important supply chains
A successful attack can ripple across industries, causing widespread delays and impacting multiple organizations. In 2021, an attack on Colonial Pipeline disrupted fuel distribution, causing trouble to manufacturing and transportation sectors.
- They have high ransom potential
Companies rely on continuous operations and cannot afford prolonged downtime. Attacked by ransomware, they are often willing to pay to resume production quickly and avoid financial losses.
- They collect consumer data and possess intellectual property
A bunch of valuable data is an irresistible honeypot for hackers. Trade secrets, patents, blueprints, and proprietary technologies. Sensitive data about customers, employees, and supply chains. Stolen data can be sold, used for fraud, espionage, and other outlaw activities.
- They depend on legacy systems
Outdated systems and technologies are not designed with modern cybersecurity in mind. For example, older programmable logic controllers (PLCs) in factories often lack encryption or authentication, making them easy targets.
- They are in the midst of digitalization and IoT adoption
Manufacturing is embracing Industry 4.0, integrating IoT devices, cloud computing, and automation. More connected devices and networks introduce more vulnerabilities.
Time is Money, Downtime is No Money
A sadly large share of enterprise companies prioritizes operational efficiency over cybersecurity due to limited budgets, lack of expertise, and a focus on physical security. But it is a short-sighted approach.
Industrial companies have low tolerance for downtime: in the case of a ransomware attack they often prefer to pay adversaries than to permit a production halt. Research by Siemens in 2022 found that unplanned downtime costs Fortune Global 500 companies about US$1.5tn, which is 11% of their yearly turnover.

Learn to Track Emerging Cyber Threats
Check out expert guide to collecting intelligence on emerging threats with TI Lookup
Threat Intelligence Lookup at the Service of Enterprises
Threat Intelligence Lookup is a key tool in the cybersecurity stockpile. It is a special-purpose search engine that helps navigate and research threat data.
The data is extracted from malware samples uploaded via ANY.RUN’s Interactive Sandbox by over 500,000 security professionals.
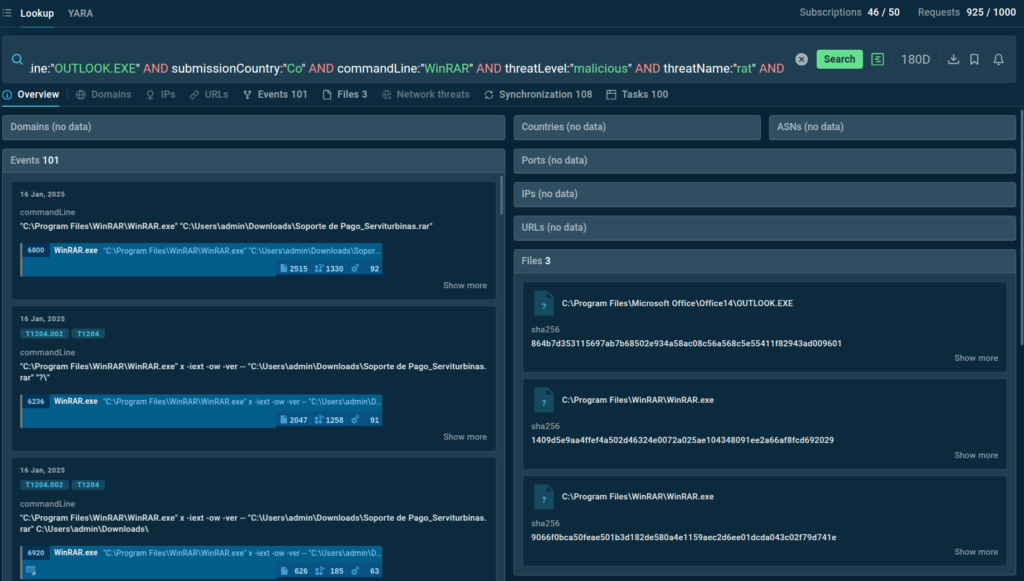
TI Lookup key features:
- Fast interactive search across over 40 different threat data types, including system events and indicators of compromise (IOCs), indicators of behavior (IOBs), and indicators of attack (IOAs).
- Continuously updated database with new indicators and samples.
- Customizable queries that support combining multiple indicators, wildcards, YARA and Suricata rules.
- Integration with sandbox to view sessions where particular indicators or events were discovered.
- Real-time updates on relevant threats and indicators to ensure ongoing monitoring.
TI Lookup in Action: A Recent Example
One of the latest and most dangerous malware campaigns that targeted the industrial sector unfolded this autumn. The attack was based on Lumma and Amadey malware.
Analysts in ANY.RUN explored the attack’s anatomy with the aid of the Interactive Sandbox found a number of IOCs associated with the malware. These IOCs can be used as TI Lookup search requests to analyze the attack further in pursuit of actionable insights for arming corporate security systems against it.
The following query consists of the name of the malware and the path to one of the malicious files used in the attack:
filePath:”dbghelp.dll” AND threatName:”lumma”
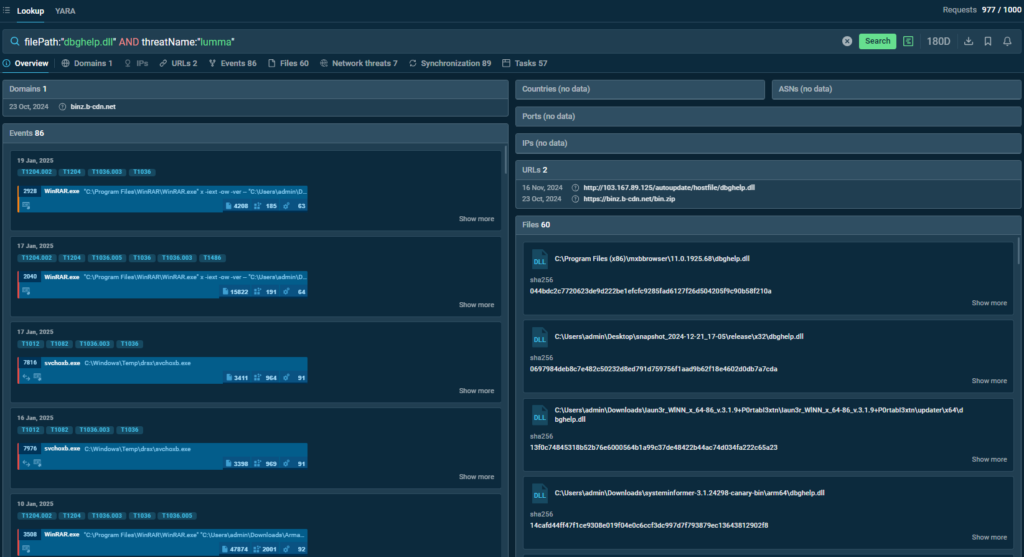
TI Lookup finds files associated with an attack and shows sandbox sessions featuring analysis of samples belonging to the same campaign.
TI Lookup provides a number of essential benefits for companies:
- Faster Access to Threat Information: Simplifies and speeds up the process of finding threat-related information, making it more convenient and efficient.
- Detailed Insights into Attacks: Provides detailed information on attacker methods, helping to determine the most effective response measures. Deep analysis makes the actions of analysts more precise and effective.
- Reduced Mean Time to Respond (MTTR): Offers quick access to key threat information, enabling analysts to make swift decisions.
- Increased Detection and Response Speed: Ensures data is up-to-date, helping businesses improve the speed of detecting and responding to new threats.
- Streamlined SOC Communication: Provides unified data that is easily interpreted and shared across different levels of the Security Operations Center (SOC).
How Threat Intel Research Helps Strengthen Enterprise Security
By investigating, collecting, and analyzing threat data with TI Lookup, security experts and management ensure:
Early detection and prevention of threats. By knowing what IOCs to look for, companies can set up systems to monitor these signs continuously. Early detection can lead to quicker response times before significant damage occurs.
Improved Incident Response. Security teams can more rapidly identify when an incident has occurred or is in progress. This speeds up the process of containment, eradication, and recovery.
Enhanced threat hunting. IOC research lets focus threat-hunting efforts by looking for signs of similar or related threats that might not have been detected by automated systems. It also helps to distinguish benign anomalies from actual threats and reduce the noise from false positives, which can overwhelm security teams.
Validation of security measures. Indicators can be used to test the effectiveness of current security controls by simulating or analyzing known threat patterns for fine-tuning security solutions.
Understanding of vulnerabilities and attack vectors. IOCs provide insights into the tactics, techniques, and procedures (TTPs) used by attackers, allowing companies to better understand where they are vulnerable and how adversaries operate.
Prioritization of security efforts and recourse management on the basis of understanding which threats are most likely to impact the organization.
Forensic Analysis. Post-incident analysis facilitates understanding the scope of the compromise, how the attack was executed, what was accessed, and how to prevent similar attacks in the future.
Training and awareness. Threat Intelligence Lookup can be used in training programs for educating staff to watch for suspicious activities or anomalies in system behavior.
Cyber Threat Intelligence and Business Performance
Threat intelligence objectives are closely connected with key business goals and metrics.
ROI and Cost Optimization
Significant cost savings can be achieved by preventing data breaches and minimizing mitigation efforts. By avoiding data losses and leaks, businesses can sidestep the expenses associated with incident response, legal fees, and regulatory fines.
Informed Decision-Making
Threat analysis by tools like ANY.RUN’s TI Lookup provides insights that allow to focus the resources and security efforts on the most relevant threats, critical areas, topical vulnerabilities.
Operational Viability
A pillar of enterprise efficiency, operational stability suffers immensely from even a brief downtime. Threat intelligence tools and methods like TI Lookup help automate threat detection, make it both wider and more accurate, and reduce downtime caused by breaches.
Compliance and Reporting
In manufacturing and industrial enterprises, regulatory compliance is critically important. Besides, such businesses often operate in multiple jurisdictions with varying rules and requirements. Plants and manufacturing facilities can be located in different countries with their own laws. Apart from improved threat detection, TI helps document incidents, enrich security reports, and meet requirements for frameworks like GDPR, HIPAA, and PCI.
Brand Reputation Defense
Customer and counterparty trust is one of the most valuable business assets in enterprise or elsewhere. Early detection of threats reduces the likelihood of incidents that could damage a company’s name and negatively impact shareholder value.
Conclusion
Cyber resilience must be a business priority for enterprise companies with their critical role in the economy, low tolerance for downtime and complex digital environments. Threat intelligence builds a basis for proactive threat management and informed decisions, helps allocate resources, and avoid ineffective costs. Professional solutions like ANY.RUN’s Threat Intelligence Lookup power security teams for meeting the demands of business security.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.








0 comments