Recently, DFIR consultant & content creator/educator Steven from the YouTube channel MyDFIR released a new video showing how DFIR professionals can leverage the ANY.RUN Sandbox to efficiently analyze malware and extract actionable intelligence.
The video provides a step-by-step guide on investigating real-world threats, including how to quickly identify and analyze Indicators of Compromise (IOCs) and uncover key behavioral insights.
If you’re looking to improve your investigation workflows and see practical examples of malware analysis in action, we highly recommend watching the video to follow along with the expert’s process.
Here’s our overview of the key highlights covered in the video.
About ANY.RUN Sandbox
The ANY.RUN Sandbox is an interactive malware analysis platform that enables security professionals to analyze malicious files in a live, user-driven environment. It allows DFIR professionals to:
- Uncover the behaviors and tactics of malware.
- Quickly gather critical Indicators of Compromise (IOCs).
- Explore malware configurations and identify threats in real time.
By providing detailed insights through features like process trees, network monitoring, and integrated ATT&CK mapping, ANY.RUN helps analysts stay ahead of emerging threats and streamline investigations.
Use Case 1: Investigating Formbook Infostealer
Formbook is a widespread infostealer that targets credentials, cookies, and other sensitive data. Here’s how DFIR professionals can use ANY.RUN to analyze it.
Imagine you have received the following alert: malware detected and quarantined.
The alert also provides details such as:
- Hostname: SALESPC-01
- User: Bobby
- Filename: suchost.exe
- Current Directory: C:\Users\Bobby\Downloads
- SHA256: 472a703381c8fe89f83b0fe4d7960b0942c5694054ba94dd85c249c4c702e0cd
Use this information to initiate your investigation.
Check Previous Analyses
The first thing you should do is check if ANY.RUN analyzed this file previously. Navigate to ANY.RUN’s Reports section, located on the left-hand side.
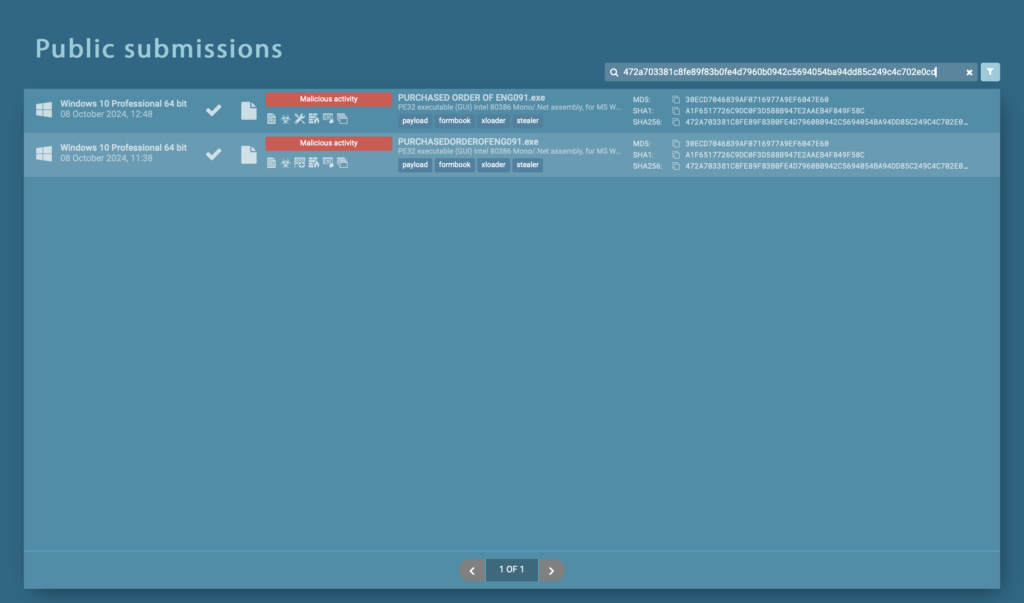
Search for the hash of the flagged file. If the file has already been analyzed, review the existing reports. Otherwise, upload the file to initiate a fresh analysis.
In our case, there are 2 analysis sessions found from October 2024. Let’s choose the first report and look closer at what’s inside.
After clicking on the existing entry, you’ll be redirected to the ANY.RUN sandbox presented with a lot of useful information.
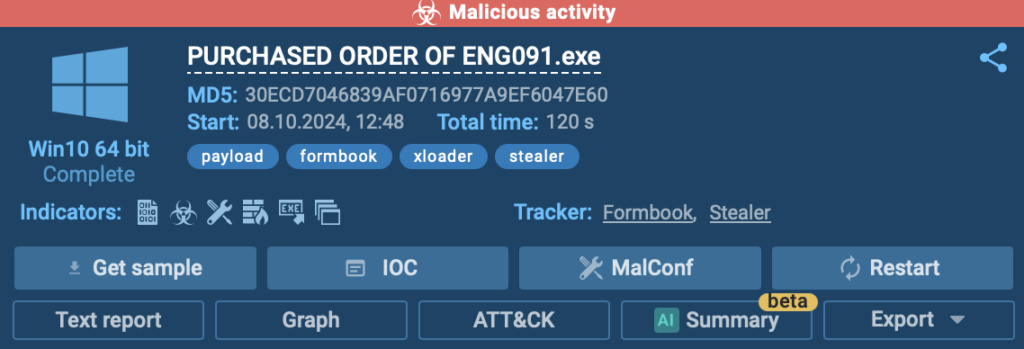
Let’s use this analysis to see how the sandbox can help us.
Examine Initial Results
ANY.RUN provides an overview of the analysis, including malicious activity indicators, the operating system used for analysis (e.g., Windows 10 64-bit), and a suite of options, such as:
- Get Sample: Download the file for deeper analysis.
- IOC Tab: View all related IOCs.
- MalConf: Explore indicators extracted from the malware’s configuration.
- Restart: Re-run the analysis if needed.
- Text Report: Get a detailed overview of findings.
- Graph: Visualize the process tree and events.
- ATT&CK Tab: Review associated tactics, techniques, and procedures (TTPs).
- AI Summary: Summarize key findings.
- Export Options: Save results in various formats like STIX or MISP JSON.
Analyze the Process Tree
Study the parent-child relationship in the process tree to understand how the file behaves.
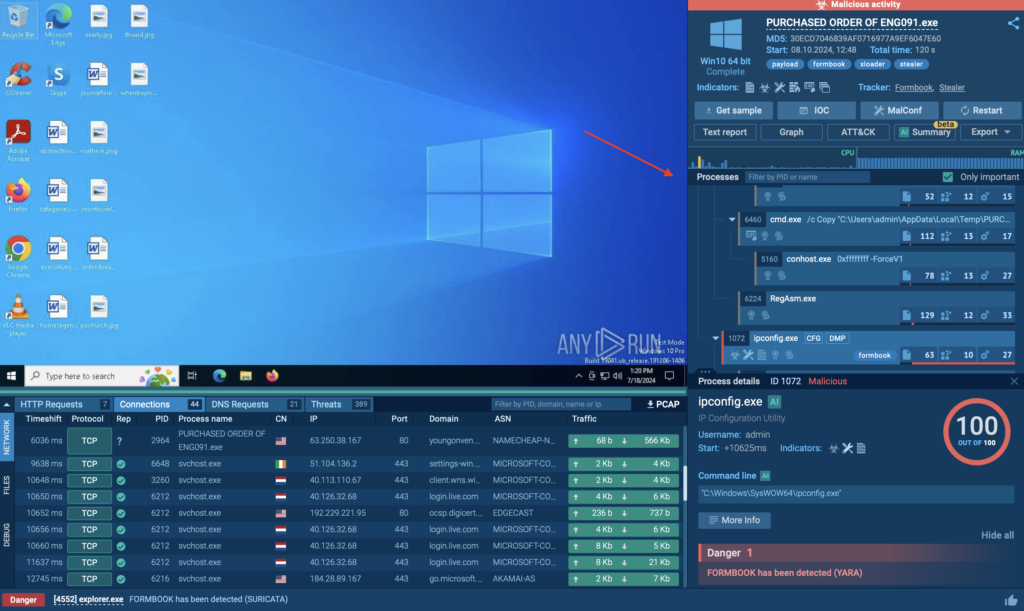
For example, Formbook may create a registry key to establish persistence. By clicking on the process, you can view command-line details and trace the registry key creation and file execution paths.
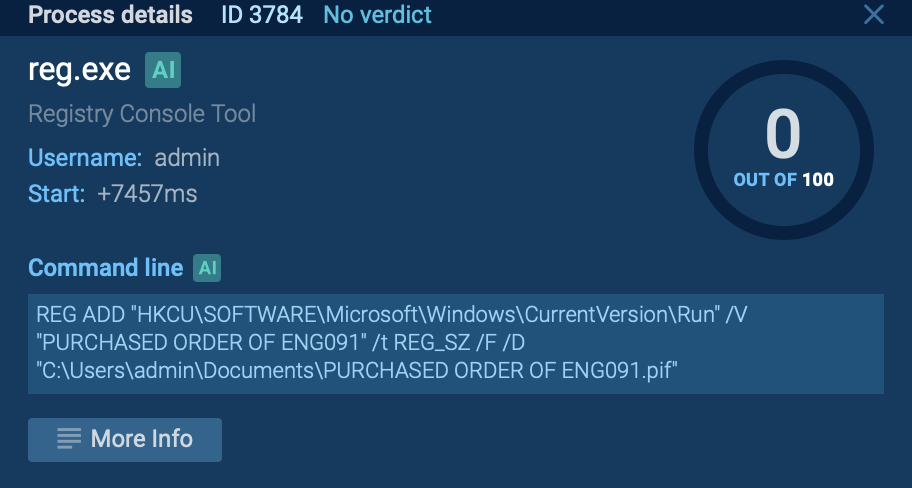
Investigate Network Activity
Use the network-related tabs to track events like HTTP requests and connections. ANY.RUN simplifies this by flagging requests with reputation icons:
- Green checkmark: Known and safe.
- Question mark: Unknown.
- Fire icon: Malicious. Document any flagged IOCs, such as suspicious IP addresses or domains, and cross-check them within your environment.
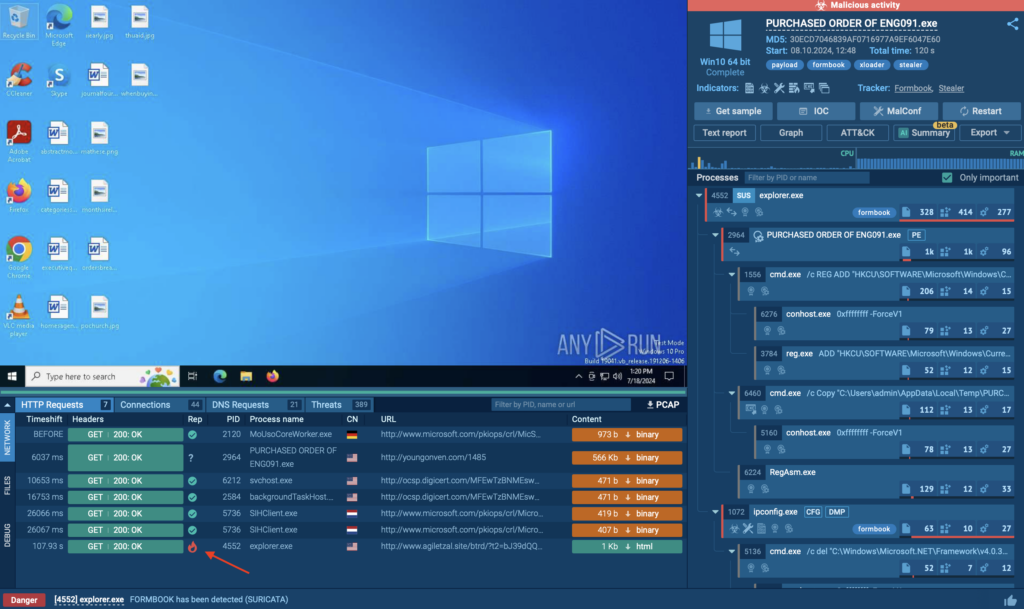
Leverage Threat Hunting Features
Utilize tabs like MalConf and ATT&CK to uncover additional insights. For instance, MalConf may reveal hardcoded strings or configurations that can aid in threat hunting.
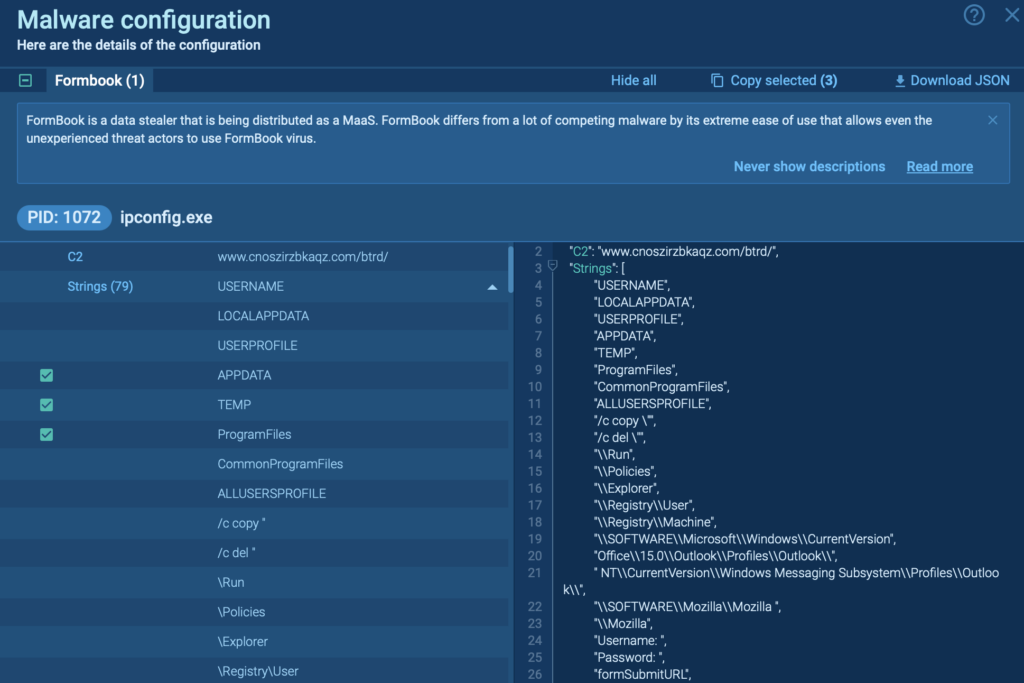
The ATT&CK tab provides a breakdown of associated TTPs, helping analysts understand how the malware evades detection or escalates privileges.
In the current analysis session, these are the TTPs the sandbox identified:
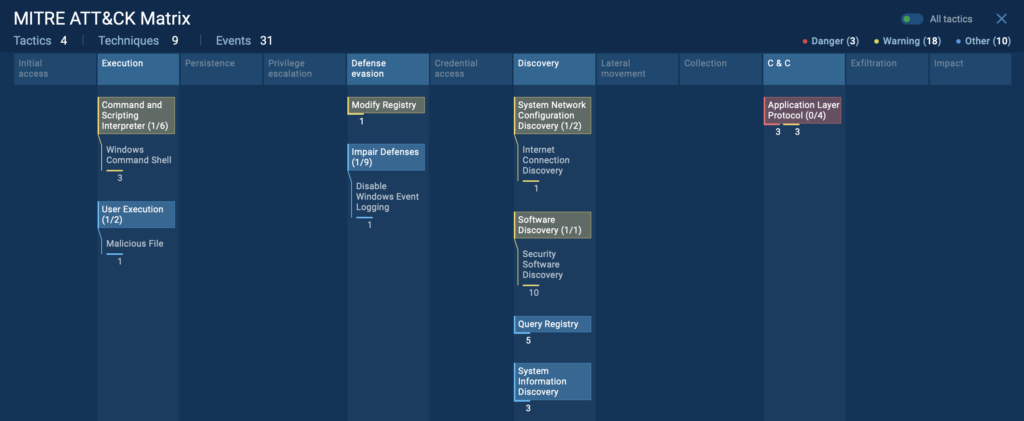
AI Summary
The AI-powered summary distills the technical findings into easy-to-understand insights. This is particularly beneficial for:
- Quickly understanding the file’s behavior without diving into the technical minutiae.
- Assisting junior analysts or teams new to malware analysis by providing clear explanations of what the file is doing.
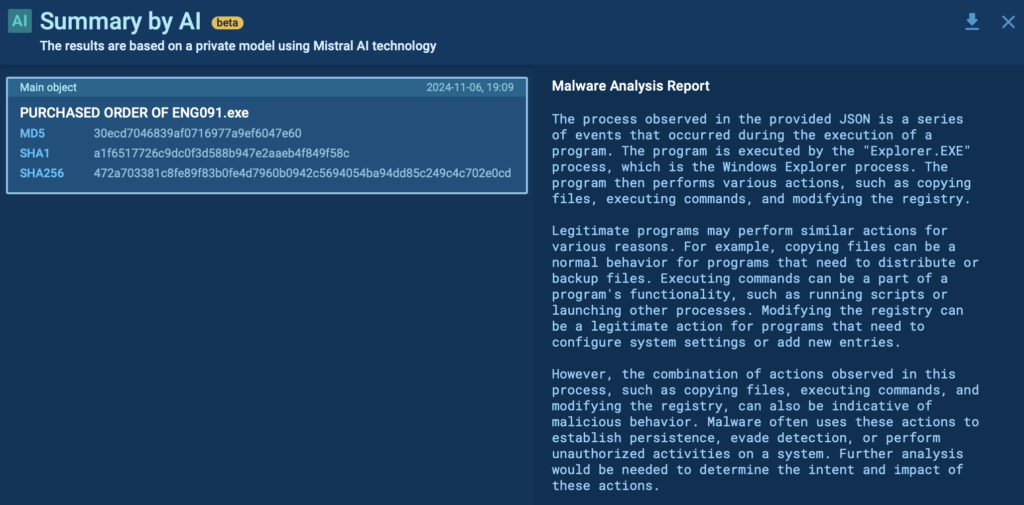
By leveraging these features, DFIR professionals can perform detailed, thorough, and efficient malware analysis, tailoring their investigations to the specific needs of their organization.

Learn to analyze cyber threats
See a detailed guide to using ANY.RUN’s Interactive Sandbox for malware and phishing analysis
Use Case 2: Analyzing Lumma Stealer with Advanced Features
The next use case focuses on analyzing a file using the ANY.RUN sandbox, specifically targeting a different infostealer called Luma Stealer. The latter is another malware aimed at exfiltrating data.
For this demonstration, the free plan is used, but comparisons to the paid plan capabilities will also be highlighted.
Uploading a File to ANY.RUN
To analyze a file in ANY.RUN, start by selecting Submit File option from the available 3 options.
When uploading a file, keep in mind that as a free user Analysis will be public, meaning anyone can view it. Avoid uploading sensitive data. Always consult with your team if unsure.
The free plan, however, offers privacy options to restrict access to your analysis.
After selecting the file, you’ll see two key options:
- Deep analysis: Ideal for file-based malware investigations.
- Safebrowsing: Suitable for URL-based fast analysis.
For this case, we’re performing Deep Analysis on the Luma Stealer sample.
Explore the entire analysis session
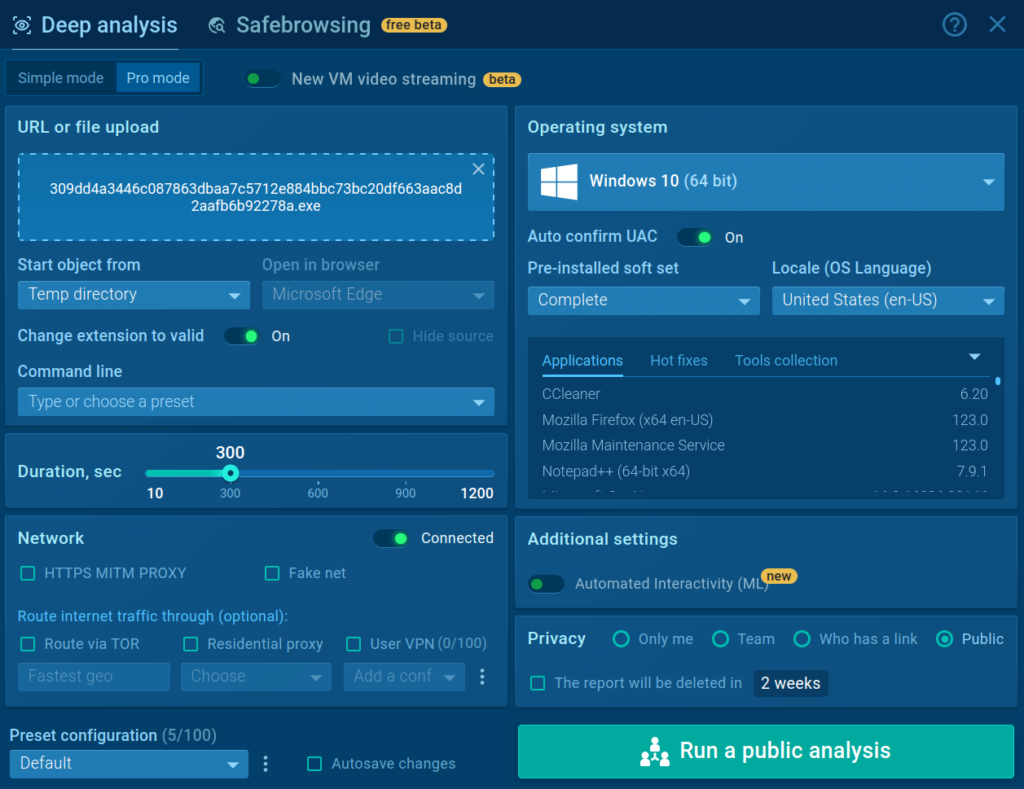
Configuration Options
ANY.RUN allows you to customize execution and environment settings to simulate real-world scenarios. For instance, you can specify custom command-line arguments to trigger specific malware behaviors.
- The free plan offers 60 seconds of analysis.
- With the paid plan, you can extend to 10+ minutes for deeper analysis.
You can also choose where you want to execute the file, for instance, temp directory, desktop, downloads directory, AppData, and more.
For the network traffic the following options are available:
- FakeNet: Simulates network traffic.
- TOR Routing: Routes traffic through Tor for anonymity.
- Residential Proxy: Assigns a residential IP to your VM.
Then, choose the operating system, such as Windows 7 (32-bit), Windows 10 (64-bit), and Ubuntu 22.04. The paid plan also offers Windows 11.
Running the Analysis
Once configurations are set, click Run Analysis. If you decide to go with the Public mode, a warning will remind you that the analysis data will be publicly accessible. To make your analysis private, you will need to get a Hunter or Enterprise plan subscription.
The sandbox begins dynamic analysis, executing the file and recording all processes, behaviors, and network activities.
A timer (top-right) shows the remaining analysis duration. You can add time to capture extended malware behaviors.
Observing Results in Real Time
Once the analysis begins, you can interact with the sandbox environment. Have a look at the parent-child relationships of processes generated by the malware.
On the right corner you can already see the sandbox identifies the processes as Lumma malware and possible phishing.
Besides, we can note that the sandbox also detected a domain used for C2 connection:
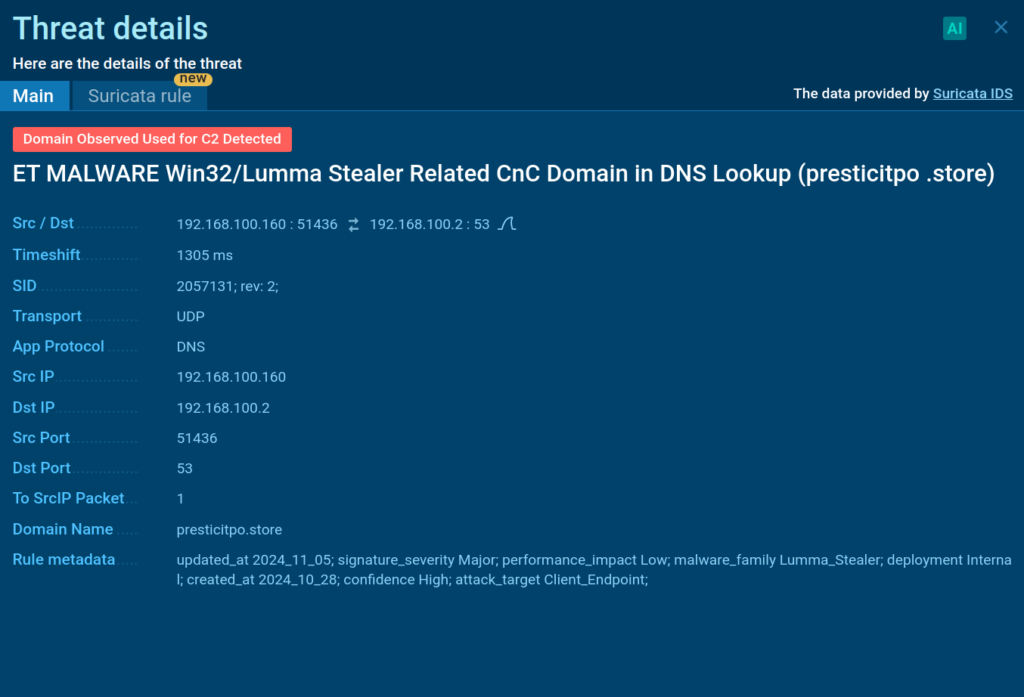
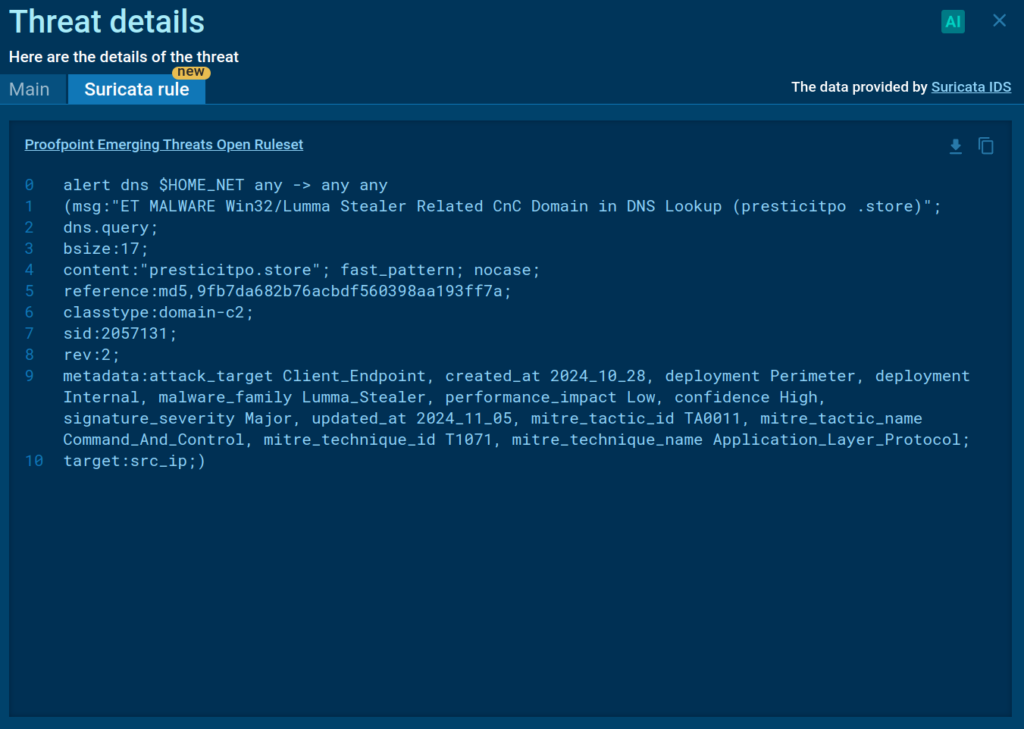
With the paid plan you can also see how this particular Suricata rule was generated:
Extracting IOCs and Key Artifacts
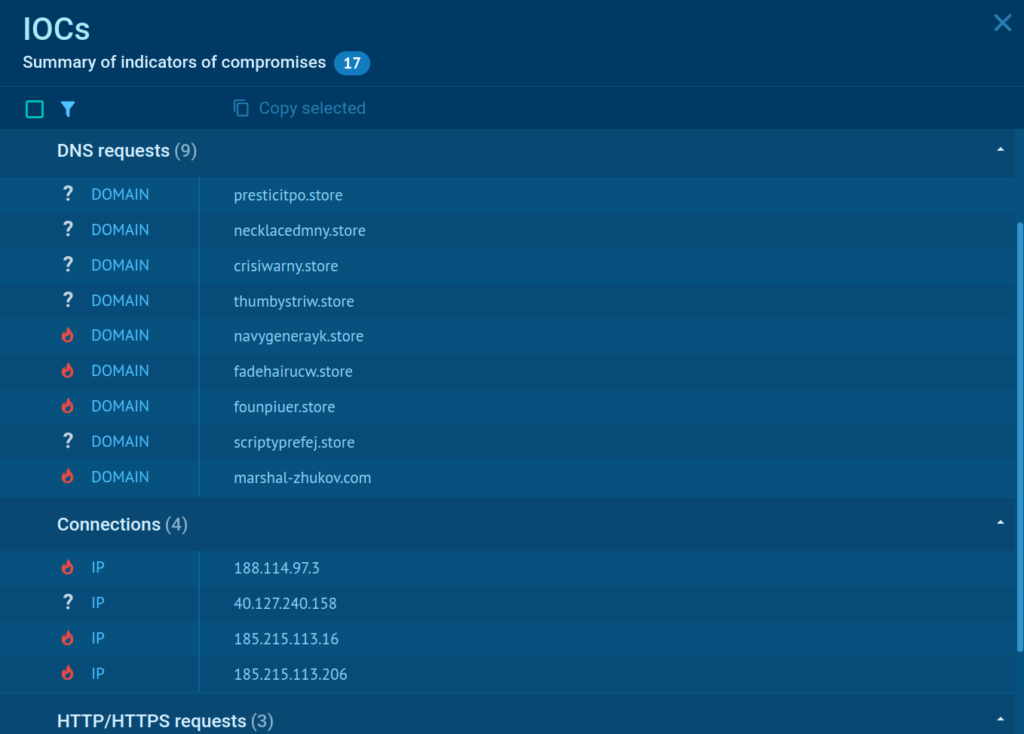
Once the analysis completes, go to the IOC tab to extract key indicators, including:
- IP addresses
- Domains
- File hashes
- URLs
Why DFIR Professionals Rely on ANY.RUN
ANY.RUN’s real-time, interactive capabilities make it a favorite among DFIR experts. Here’s why:
- Speed: Analyze malware behavior and extract IOCs faster than ever.
- Ease of use: Its intuitive interface works for both seasoned analysts and newcomers.
- Flexibility: From free plans to enterprise solutions, ANY.RUN fits teams of all sizes.
- Threat intelligence integration: Enrich your investigations with additional context to ensure thorough results.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
With ANY.RUN you can:
- Detect malware in seconds
- Interact with samples in real time
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior
- Collaborate with your team
- Scale as you need







0 comments