Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


SalatStealer, also known as WEB_RAT or Salat Stealer, is a Go-based information-stealing malware targeting Windows systems. It operates as a Malware-as-a-Service (MaaS) focusing on harvesting browser credentials, cryptocurrency wallets, and session data from popular applications like Telegram and Steam.
|
Stealer
Type
:
|
Unknown
Origin
:
|
|
1 August, 2025
First seen
:
|
Unknown
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 August, 2025
First seen
:
|
Unknown
Last seen
:
|

 779
779
 0
0

 476
476
 0
0

 2720
2720
 0
0
destinationIP:"45.130.41.157".
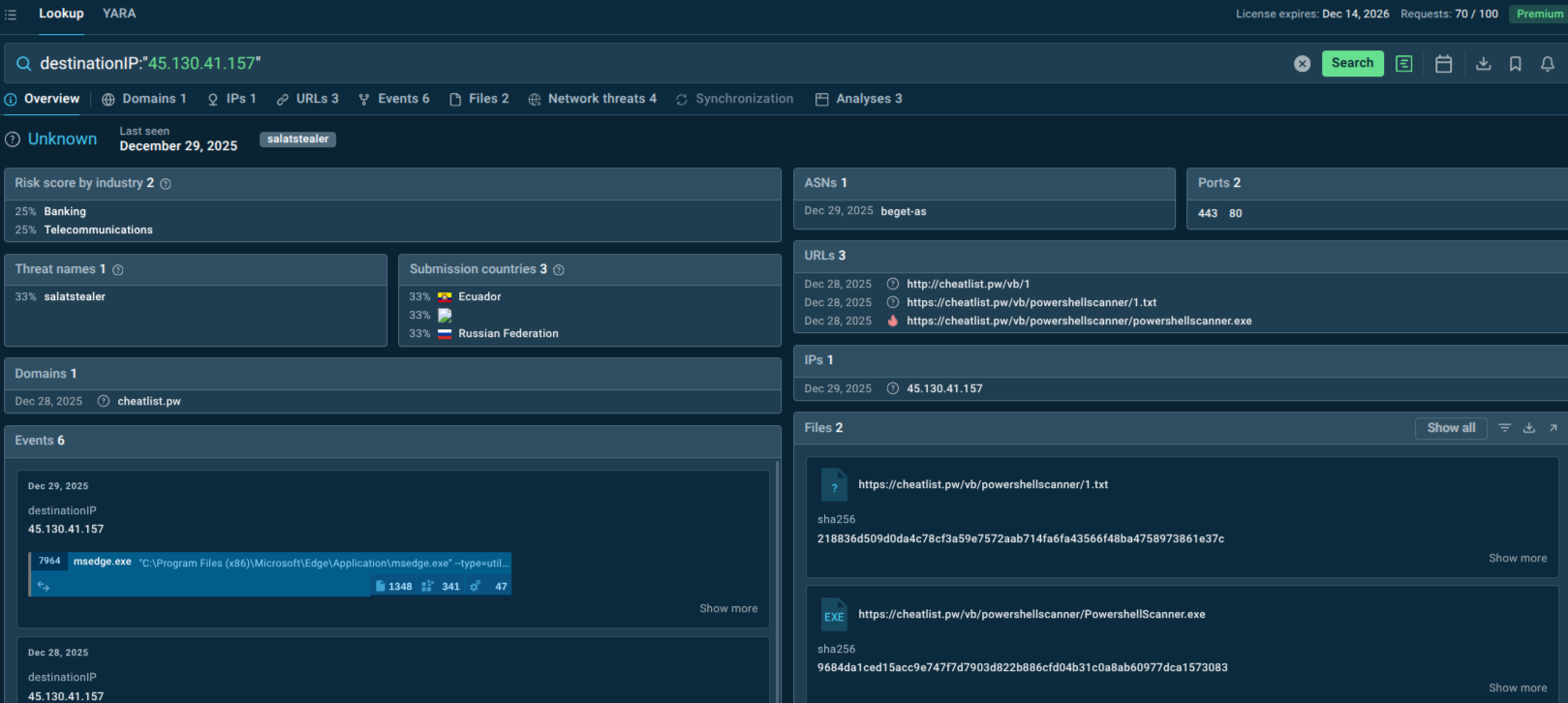 Suspicious IP detected as SalatStealer, plus targeted sectors
Suspicious IP detected as SalatStealer, plus targeted sectors
 SalatStealer detonated in ANY.RUN’s Sandbox
SalatStealer detonated in ANY.RUN’s Sandbox
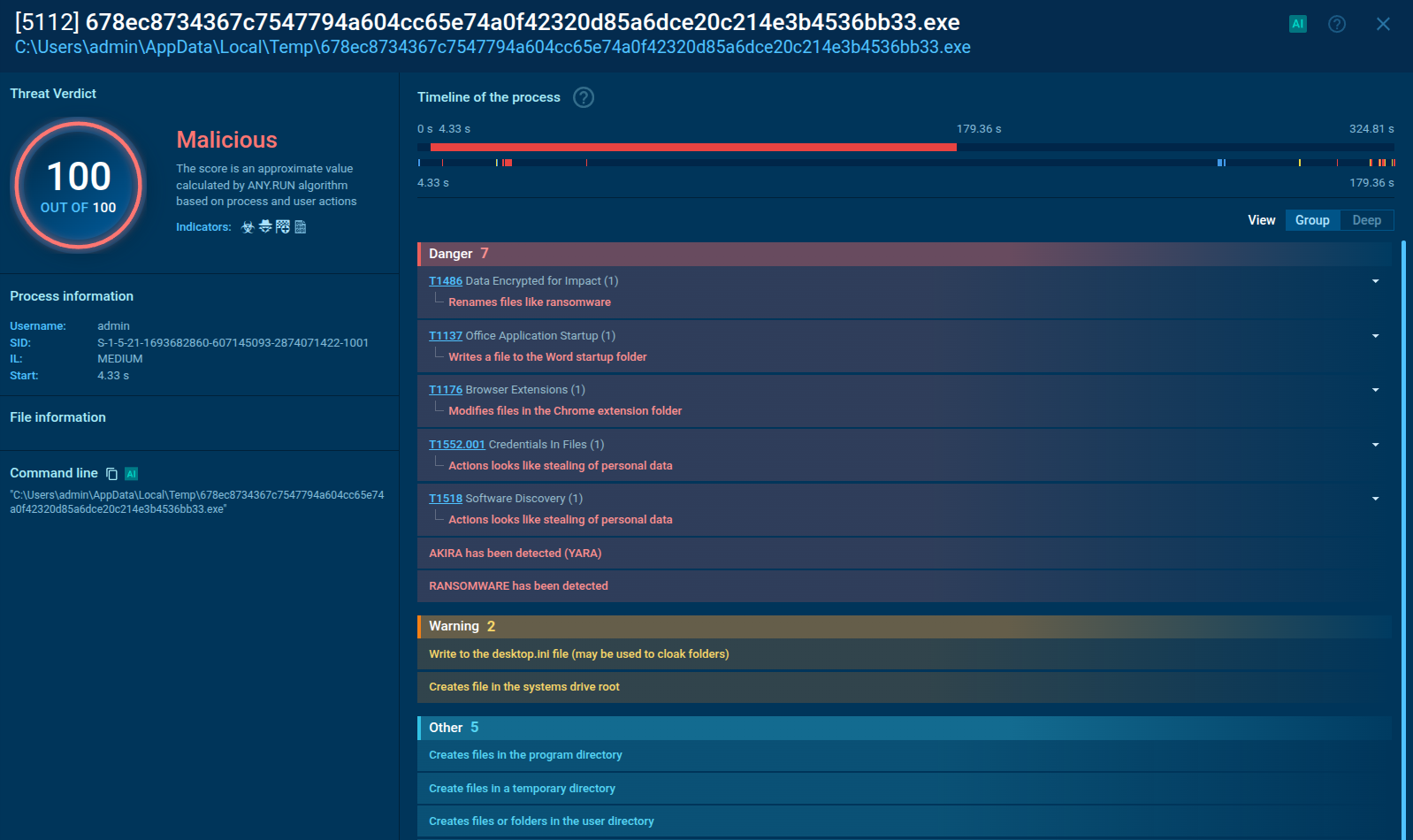
SalatStealer, also tracked as WEB_RAT, is a sophisticated information-stealing malware that targets Windows systems. First detected in August 2025, it has quickly established itself as a significant cybersecurity threat, combining extensive data theft capabilities with aggressive persistence mechanisms and real-time surveillance features.
What sets SalatStealer apart is its approach to data exfiltration. The malware doesn't just steal credentials. It harvests browser data, cryptocurrency wallets, messaging application sessions, system information, and even streams live video and audio from infected devices. Operating under a Malware-as-a-Service model, SalatStealer has become accessible to a broad range of cybercriminals, amplifying its reach and potential impact.
Written in Golang version 1.22.0, SalatStealer leverages the cross-platform capabilities and performance characteristics of the Go language. The developers have taken additional steps to hinder analysis by stripping all debugging symbols from the compiled binary, making reverse engineering significantly more challenging.
The malware employs multiple anti-analysis techniques, including virtual machine detection, mutex creation to prevent reinfection of the same device, and checks for debugging environments. These defensive measures help SalatStealer evade both automated sandbox analysis and manual reverse engineering attempts.
Upon execution, SalatStealer first checks if the infected system is connected to the internet by sending GET requests to specific URLs, automatically exiting if connectivity is not detected. This preliminary check ensures the malware operates only in environments where it can successfully communicate with its command-and-control infrastructure.
Often packed with UPX to increase entropy and hinder static analysis, the persistence mechanisms include registry run keys and scheduled tasks disguised as legitimate processes (e.g., Lightshot.exe or RuntimeBroker). It communicates with command-and-control (C2) servers via encrypted HTTPS channels and lightweight UDP beacons, using domains like salat[.]cn with multiple fallbacks for resilience. Operated through a web-based panel branded "WebRat," it is sold on underground forums for low subscription fees, making it accessible to a wide range of cybercriminals.
SalatStealer primarily targets opportunistic victims, such as individuals downloading pirated software, game cheats, or cracks from untrusted sources like YouTube links and file sharing sites. Its focus on cryptocurrency wallets and browser credentials suggests a strong interest in crypto enthusiasts and everyday users storing sensitive logins. While no specific geographic or sectoral targeting has been reported, the malware's broad capabilities make it a threat to both individual users and employees in organizations who fall for social engineering lures on personal devices.
SalatStealer poses significant risks to business environments:
Credential compromise leads to account takeovers and lateral movement.
Exfiltrated session tokens can bypass multifactor protections.
Corporate browser credential theft exposes enterprise SSO and internal portals.
Cryptocurrency asset theft impacts any organization handling digital assets.
Long-term persistence creates opportunities for further exploitation and deeper intrusion.
Malware can undermine endpoint defenses by creating exclusion rules and disabling protective tools.
Primary infection vectors include:
The malware sample is packed using UPX version 0.89 or higher, with all sections in the PE file compressed or encrypted to hide the real program instructions. Upon execution, the malware unpacks itself in memory, revealing its true functionality while avoiding disk-based detection.
Before proceeding with malicious activities, SalatStealer verifies internet connectivity to ensure it can communicate with its command-and-control servers.
Salat initiates multiple processes and attempts to evade detection by disguising itself as a legitimate application, creating several child processes named Lightshot.exe, which are dropped into directories that appear to belong to trusted software.
To maintain persistence on infected systems, the malware creates multiple Run key entries in the Windows Registry, registering itself under different names (Lightshot, Procmon, and RuntimeBroker) to further evade detection by mimicking legitimate system or third-party processes. It utilizes Windows Task Scheduler to create scheduled tasks under deceptive names, each configured with multiple triggers.
A "Defender Excluder" script module quietly adds critical directories to Windows Defender's exclusion list, ensuring that neither the main payload nor its auxiliary tools are scanned.
The malware systematically enumerates and harvests data from multiple sources. It accesses browser SQLite databases to extract credentials, scans specific directories for cryptocurrency wallet files and configurations, monitors active windows to identify sensitive applications, and captures screenshots and video streams when appropriate.
It compresses collected data and exfiltrates it to command-and-control servers over the Quick UDP Internet Connections (QUIC) protocol.
The platform includes real-time WebSocket communication, remote PowerShell execution capabilities, and predefined scripts for Windows Defender exclusion manipulation, UAC disabling, and recovery environment disabling.
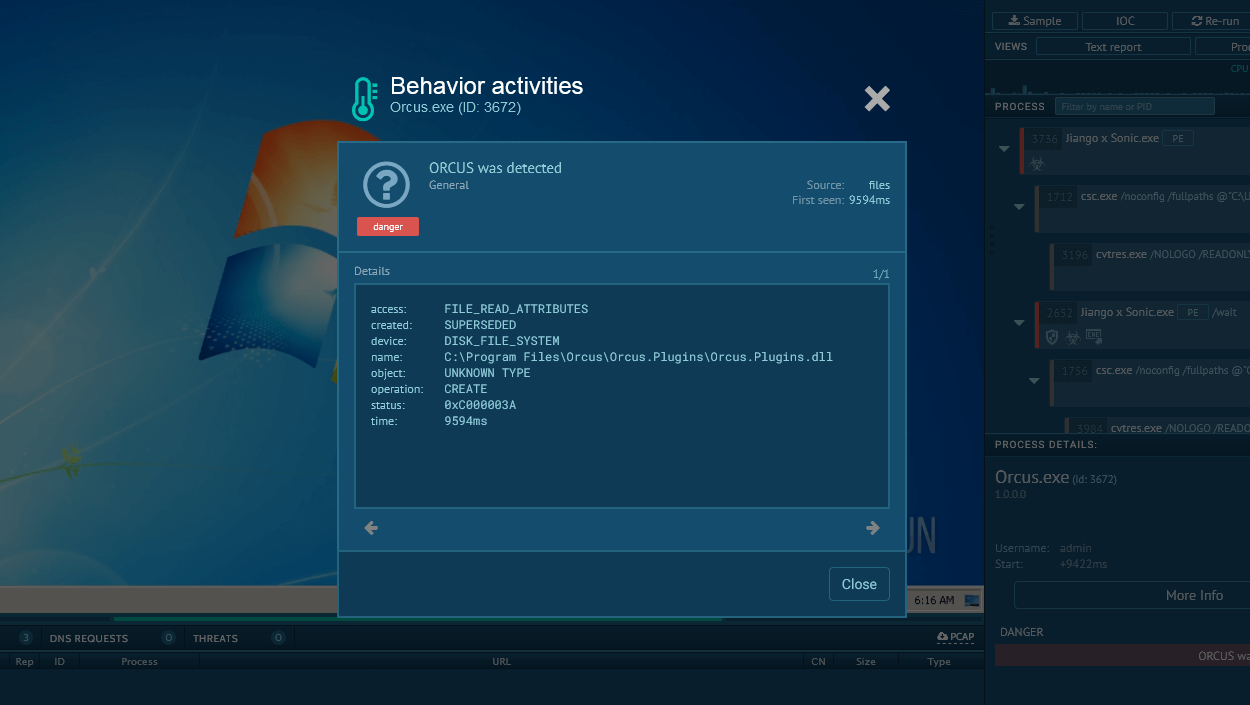
ANY.RUN’s Interactive Sandbox overcomes Salat’s ant-detection and sandbox-evasion mechanics, exposing the full attack chain. For SalatStealer, the Sandbox can reveal unpacking routines, persistence mechanisms, network communications, and data exfiltration attempts.
View a SalatStealer sample analysis
 SalatStealer detonated in the Interactive Sandbox
SalatStealer detonated in the Interactive Sandbox
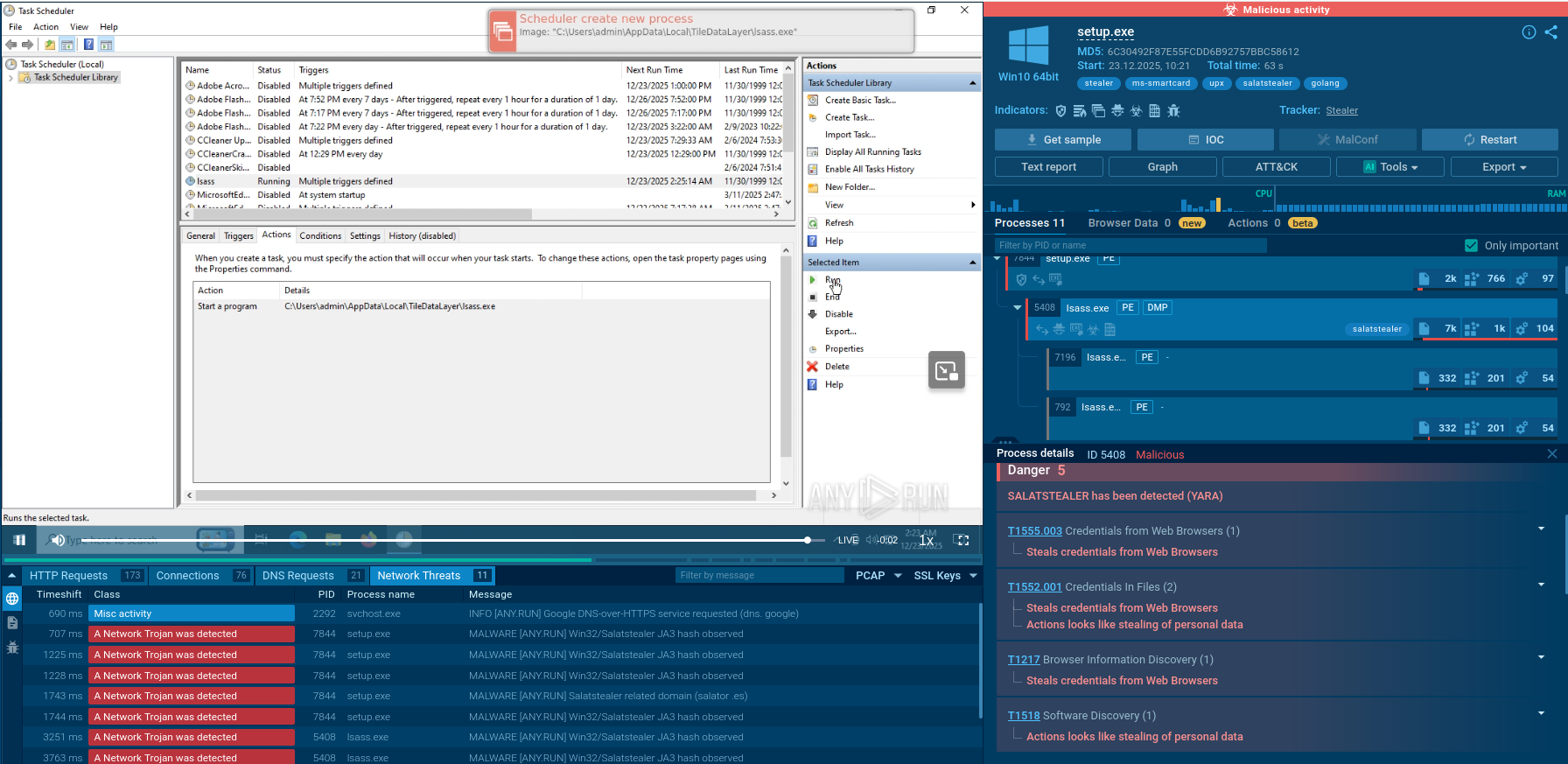
The main process spawns a child process lsass.exe. Domain resolution attempts for salat.cn were detected, but further network activity is absent due to the inactive C2 server.
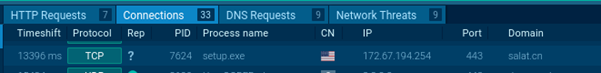 Domain connection attempt
Domain connection attempt
The sample is written in the Go language and packed with UPX which are detected by the Sandbox. It also reveals elliptic curves (YARA) that are used for encryption.
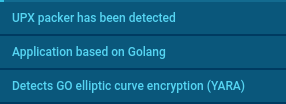 Malware features detected by the Sandbox
Malware features detected by the Sandbox
Registry queries extract basic data: computer name for victim identification, machine GUID for unique marking, and checking supported languages for locale adaptation. This forms a system profile, helping the malware select targets for data theft.
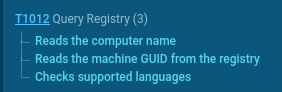 System data gathering
System data gathering
The sample drops itself into trusted directories and masquerades under system names, making the process resemble built-in Windows components.
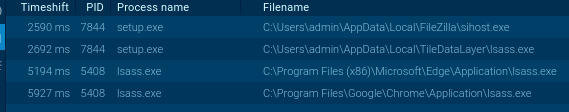 SalatStealer’s processes
SalatStealer’s processes
Signing in the Task Scheduler ensures automatic launch. The malware creates tasks with multiple triggers: at user logon and a one-time launch at a specific time.
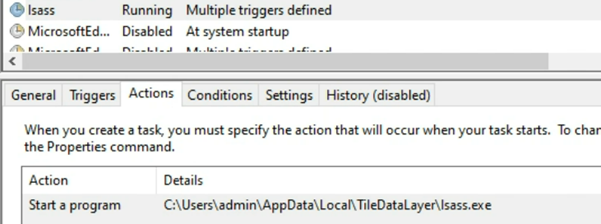 SalatStealer in Windows tasks
SalatStealer in Windows tasks
Browser data exfiltration focuses on passwords, cookies, and sessions stored in databases like SQLite. Wallet extension IDs were detected for potential theft of funds, and functionality for stealing messenger data is also observed.
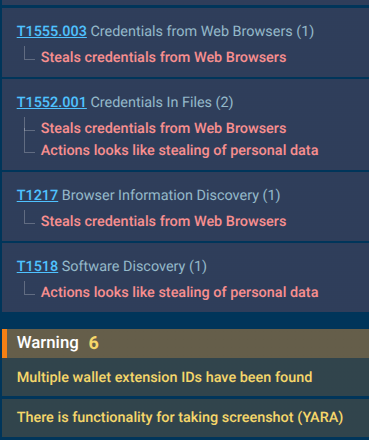 Credential harvesting and data theft
Credential harvesting and data theft
Threat intelligence services like ANY.RUN’s TI Lookup aggregate information about SalatStealer campaigns, including indicators of compromise, C2 infrastructure, file hashes, and tactics, techniques, and procedures. This intelligence enables proactive defense by allowing organizations to block known malicious infrastructure before infection attempts occur.
A threat name lookup can tell whether your business sector and geographical location are actively targeted by SalatStealer, deliver IOCs, and malware samples analyzed in the Sandbox:
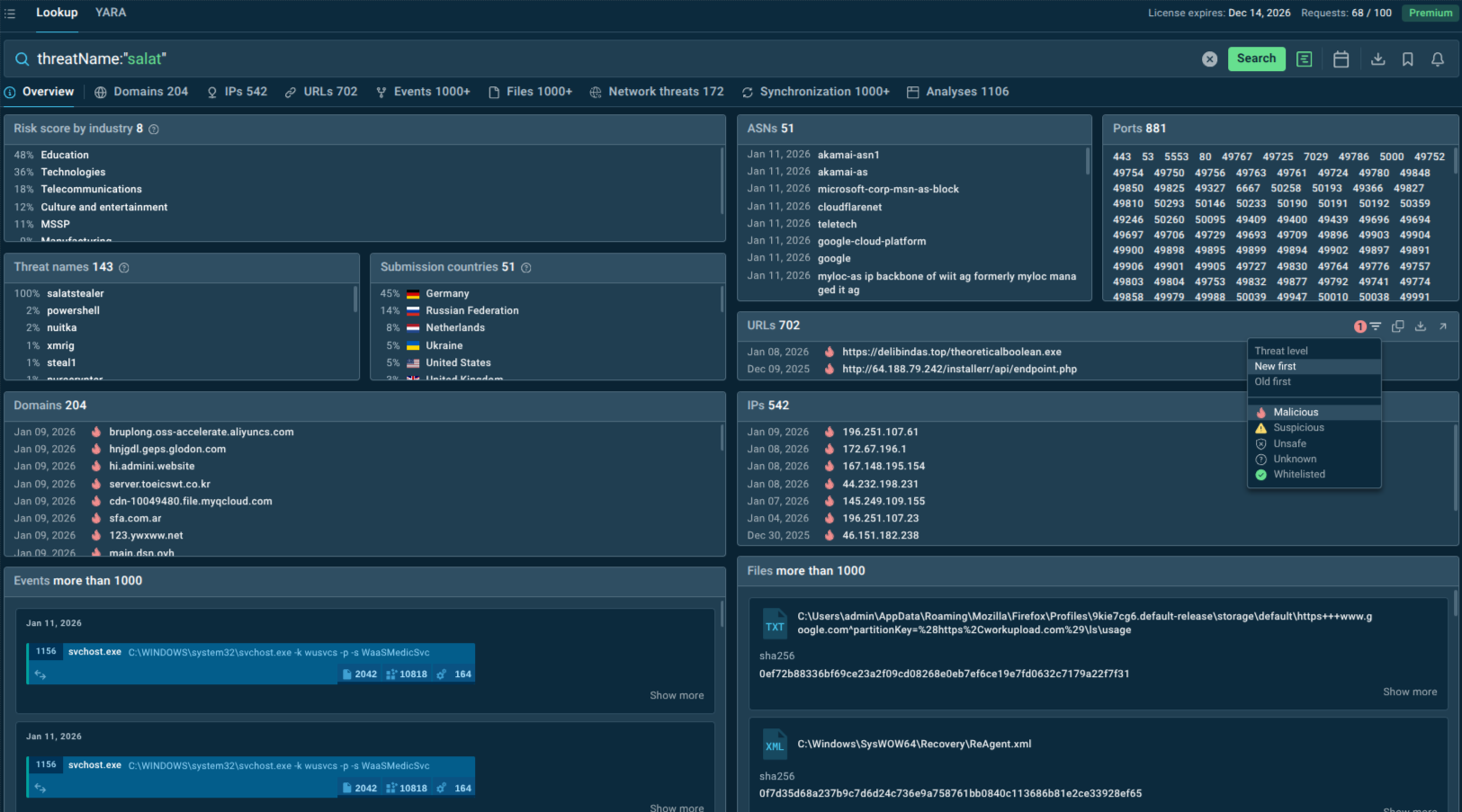 Use TI Lookup to gather Salat Stealer IOCs and view sandbox analyses
Use TI Lookup to gather Salat Stealer IOCs and view sandbox analyses
SalatStealer represents a serious evolution in infostealer malware: resilient, stealthy, and offered under a MaaS model that lowers the barrier to entry for attackers. Its ability to extract credentials, wallets, and sessions combined with evasion and persistence tactics make it a formidable threat at both the individual and enterprise level. Detection depends on robust modern security tooling and threat intelligence, while prevention hinges on user training, hygiene, and proactive defenses.
Trial TI Lookup to start gathering actionable threat intelligence on the malware that threatens your business sector and region: just sign up to ANY.RUN.