Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


Pulsar RAT is a derivative of Quasar RAT with extensive functionality including keylogging, cryptocurrency wallet clipping, credential theft, file management, remote shell execution, and data exfiltration capabilities. As a modular, open-source remote administration tool designed for Windows systems, Pulsar introduces significant enhancements over its predecessor.
|
RAT
Type
:
|
Unknown
Origin
:
|
|
1 April, 2025
First seen
:
|
27 February, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 April, 2025
First seen
:
|
27 February, 2026
Last seen
:
|

 793
793
 0
0

 482
482
 0
0

 2730
2730
 0
0
 Suspicious IP detected as Pulsar IOC, plus most targeted sectors and regions
Suspicious IP detected as Pulsar IOC, plus most targeted sectors and regions
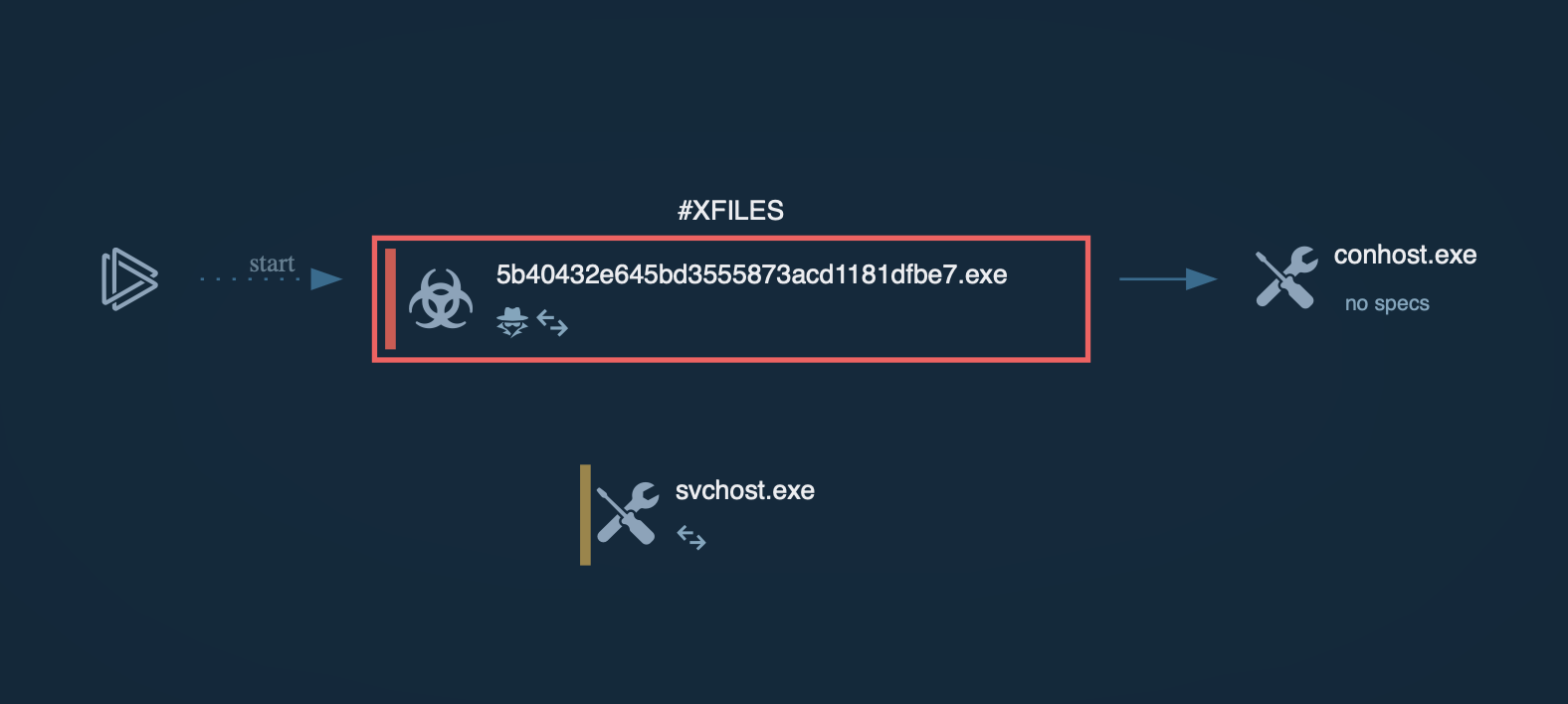
 Pulsar RAT attack chain in ANY.RUN’s Sandbox
Pulsar RAT attack chain in ANY.RUN’s Sandbox
Pulsar RAT represents an evolved fork of the popular open-source Quasar RAT, enhancing its predecessor with additional features and improved stealth. Developed as a modular .NET-based tool, it offers comprehensive remote administration capabilities that can be legitimately used for IT management but are frequently abused by cybercriminals for unauthorized access, espionage, and data theft.
Key enhancements include TLS-encrypted communications, hidden virtual network computing (HVNC) for stealthy remote desktop access, reverse proxy support, and a plugin system for customization. It incorporates specialized modules for credential harvesting (known as Kematian Grabber), cryptocurrency clipboard hijacking, and even "FunStuff" features like screen distortions or fake BSOD triggers.
Pulsar stands out for its robust anti-analysis techniques, making it challenging for security tools to detect and analyze. The malware employs robust anti-virtualization and anti-debugging techniques, code injection capabilities, and built-in obfuscation and packing mechanisms specifically designed to evade detection by security solutions. Its modular design allows for seamless plugin additions, enabling operators to customize functionality for specific campaign objectives.
The tool even includes creative modules labeled "FunStuff" that enable operations like GDI effects, blue screen of death triggers, mouse swapping, and taskbar hiding, showcasing versatility that extends beyond conventional remote administration applications.
First observed in the wild around 2025, Pulsar has been deployed in targeted campaigns, including supply chain attacks, demonstrating its adaptability in the hands of threat actors.
Pulsar RAT primarily targets Windows users and organizations across various sectors. Known incidents, such as the malicious npm package campaign, suggest a focus on software developers and tech-savvy individuals who install third-party libraries. However, as a versatile RAT, it can affect businesses of all sizes, particularly those with remote workforces or weak endpoint security.
Victims often include small-to-medium enterprises lacking advanced EDR solutions, as well as individual users exposed through phishing or malicious downloads. There is no strong evidence of nation-state targeting, but its data theft features make it appealing for financially motivated attackers seeking credentials, cryptocurrencies, or sensitive corporate data.
This RAT is relatively new, so large-scale campaigns are limited, but notable incidents include:
2025 npm Supply Chain Attack: Malicious packages "solders" and "@mediawave/lib" (published by "codewizguru") used extreme obfuscation and steganography to infect developers installing the libraries, achieving hundreds of weekly downloads before detection.
Multi-RAT Deployments: Samples linked to open directories dropping Pulsar alongside Quasar, NjRAT, and XWorm, indicating opportunistic or targeted infections.
No massive breaches publicly attributed yet, but its features suggest potential use in credential theft or precursor to ransomware.
Initial access typically occurs through social engineering or supply chain compromises:
Once inside, it persists via startup entries or scheduled tasks but focuses on stealth rather than worm-like spreading. Lateral movement relies on attacker commands (e.g., via proxy).
Pulsar operates via a client-server model. The client (stub) on the victim machine connects to the attacker's C2 server using encrypted channels (TLS).
The malware retrieves C2 configuration from public paste sites like Pastebin, decrypts the configuration using embedded keys to obtain the C2 server IP or domain, then establishes a BCrypt-encrypted connection using the MessagePack binary protocol for command transmission.
The MessagePack binary protocol enables efficient command serialization and deserialization, allowing attackers to send complex instructions and receive detailed responses about system state.
The malware incorporates multiple evasion techniques to avoid detection during security analysis. Anti-virtualization checks inspect disk labels for strings common in virtual machines like "QEMU HARDDISK." If such indicators are present, execution stops immediately, ensuring the payload avoids sandbox analysis tools.
Code injection capabilities allow the malware to execute within legitimate processes, making detection based on process names ineffective.
Advanced deployment methods load the payload directly into memory via .NET reflection without writing files to disk. This fileless approach bypasses disk-based security monitoring and reduces forensic visibility, making incident response significantly more challenging.
The plugin-based design allows operators to load additional functionality without recompiling the core malware. Modules can be added or removed based on specific campaign requirements, target environments, or evolving attacker objectives.
ANY.RUN’s Interactive Sandbox overcomes Pulsar’s ant-detection and sandbox-evasion mechanics, exposing the full attack chain. For this RAT, the Sandbox can reveal unpacking routines, persistence mechanisms, network communications, and data exfiltration attempts.
View a Pulsar RAT sample analysis
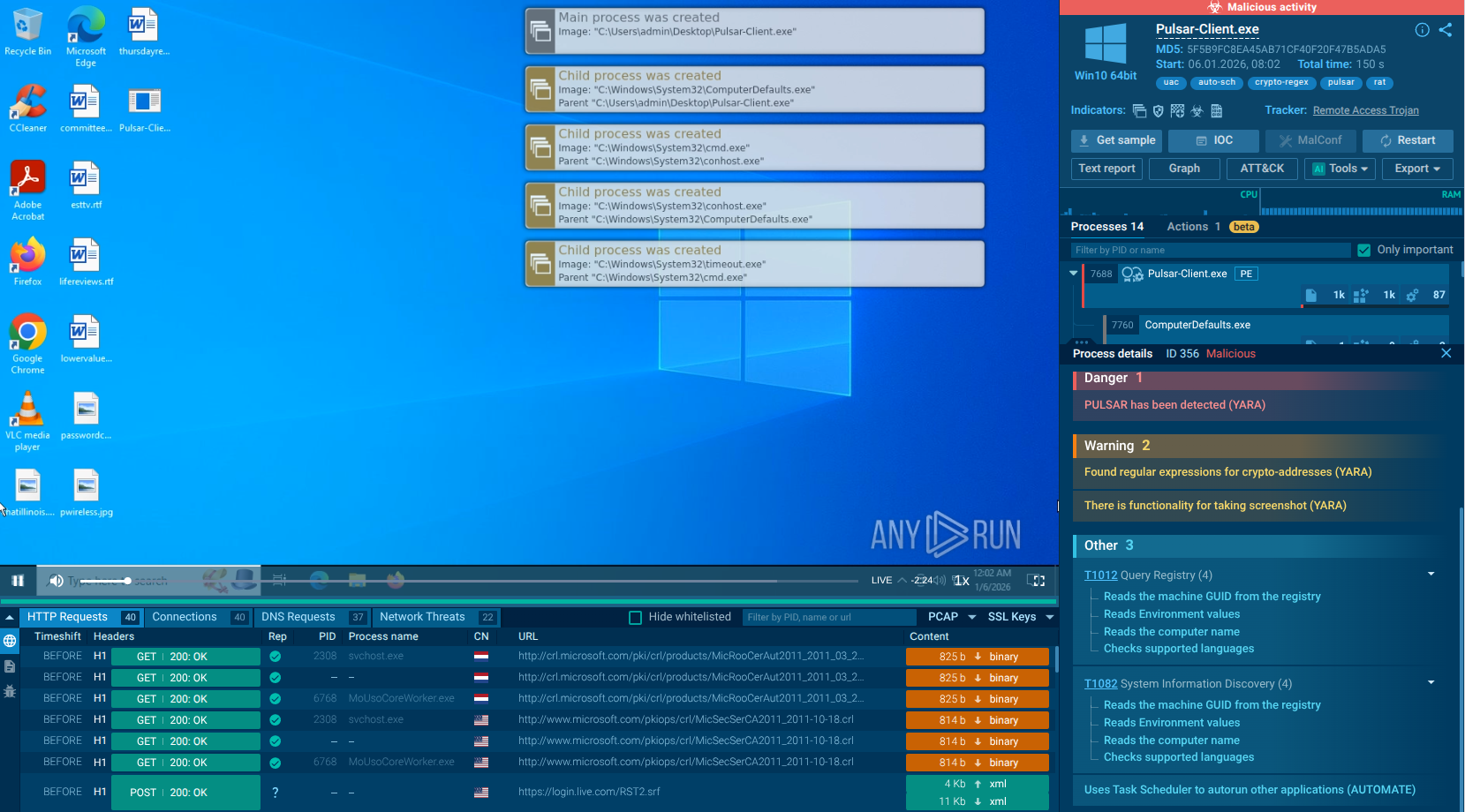
 Pulsar RAT detonated in the Interactive Sandbox
Pulsar RAT detonated in the Interactive Sandbox
In this sample, a quite simple BAT file is created (C:\Users\admin\AppData\Local\Temp\28c726a0.bat):
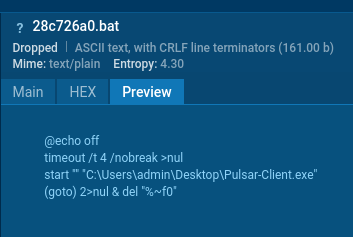 BAT file created at the start of the attack
BAT file created at the start of the attack
This file is used for UAC bypassing at the next step. The mechanism works as follows:
First, the DelegateExecute value is cleared in the registry key HKEY_CLASSES_ROOT\ms-settings\Shell\Open\command. This is necessary so that when ms-settings is opened, the system does not use the COM handler specified in the DelegateExecute value. In this case, the handler is taken directly from the (Default) value.
Therefore, the next step writes a malicious command into the (Default) value: this command launches a BAT file and then runs the legitimate program computerdefaults.exe.
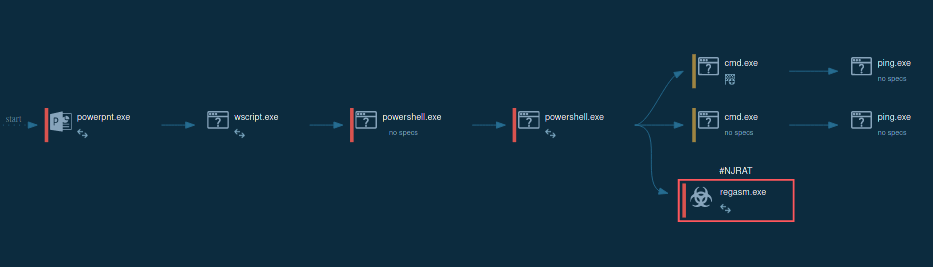
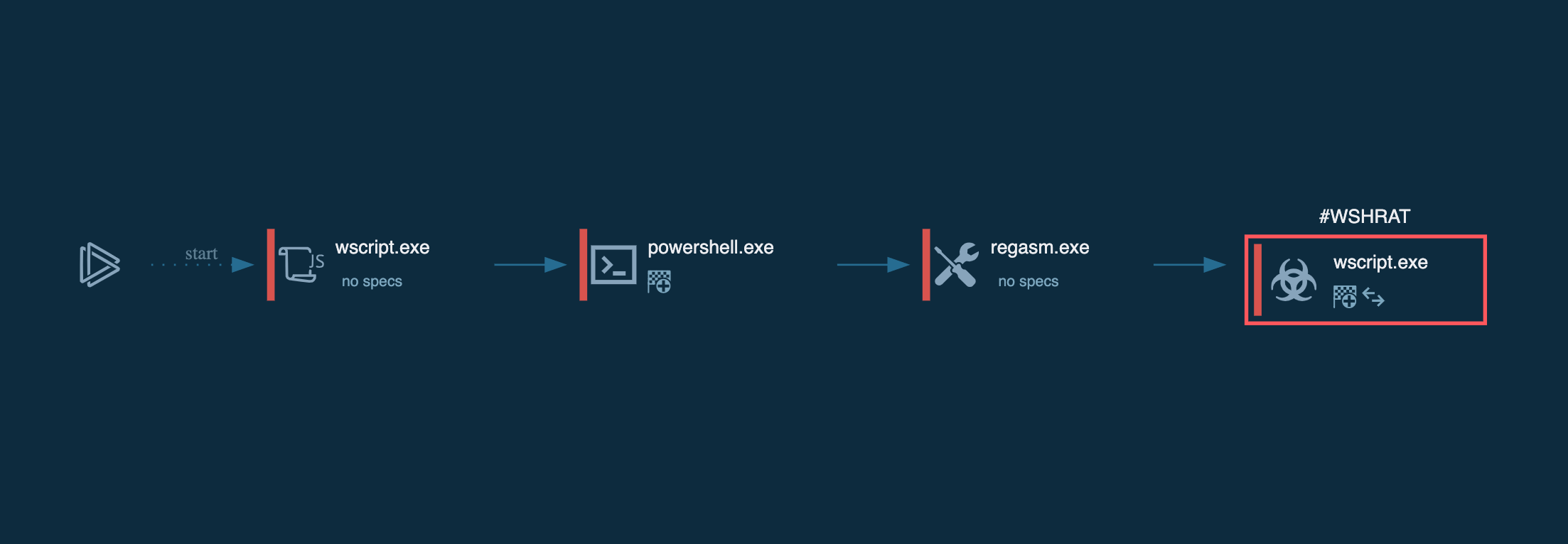
The full attack chain proceeds as follows:
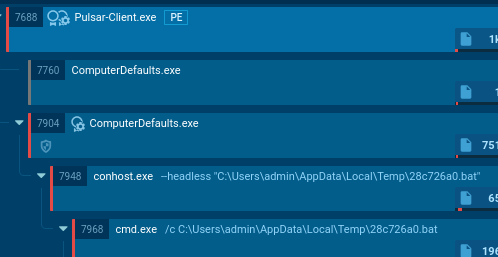 Pulsar process succession
Pulsar process succession
After the attack executes, the modified registry values are cleared to cover tracks.
The BAT file then launches the executable with elevated privileges. This executable, in turn, creates a scheduled task in Task Scheduler. The task is configured to run at every user logon with HIGHEST privileges.
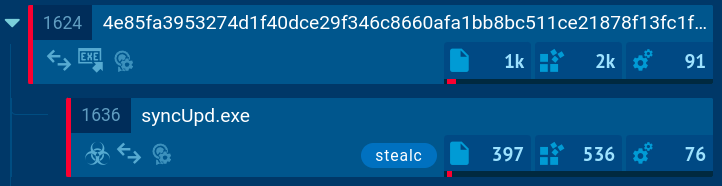
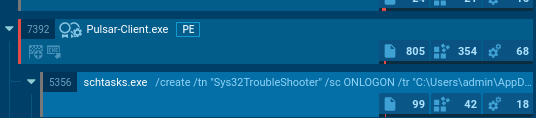 Malicious file disguised as svchost.exe
Malicious file disguised as svchost.exe
This file is a disguised Pulsar RAT, as confirmed by a YARA rule trigger.
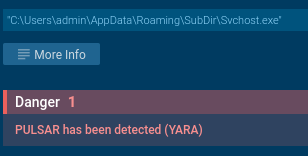 Pulsar detected by YARA rule
Pulsar detected by YARA rule
After Pulsar finished collecting system information, execution stopped.
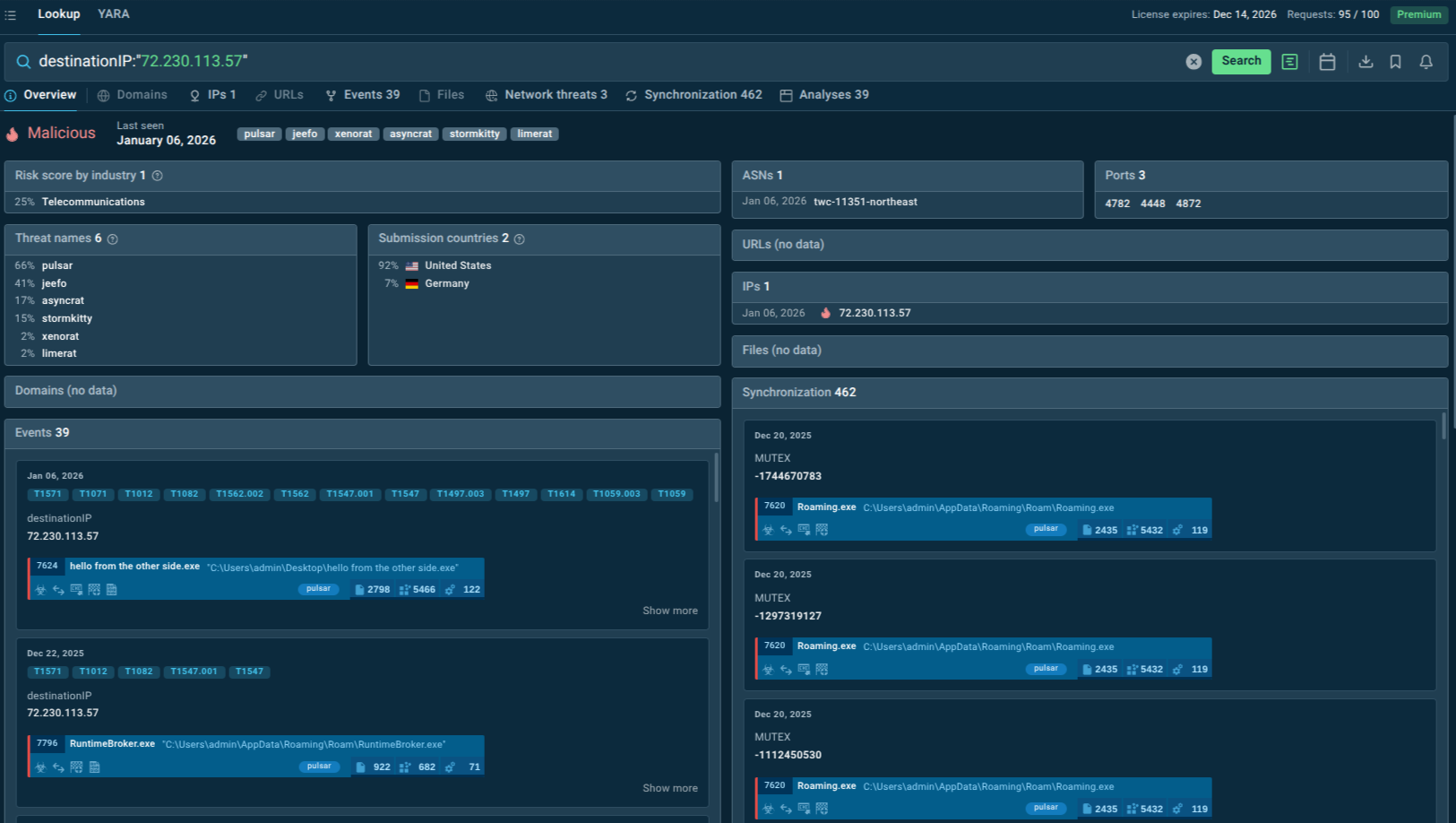
By searching for known Pulsar RAT indicators, security teams retrieve comprehensive intelligence including sample analysis results, network connections, related infrastructure, and historical campaign data. This accelerates investigations by providing immediate context without requiring manual sample collection and analysis.
Start by querying the threat’s name in ANY.RUN’s Threat Intelligence Lookup.
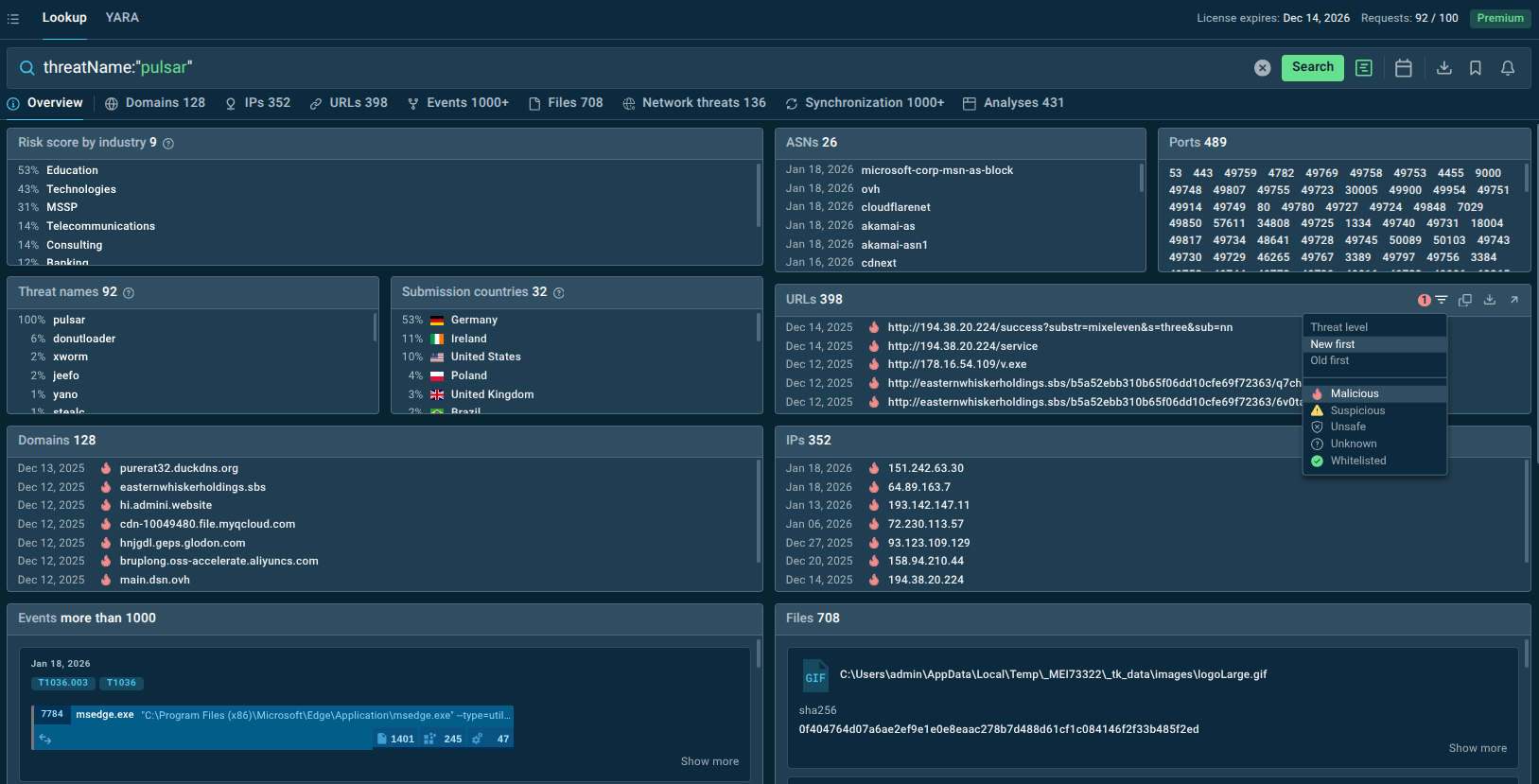 Pulsar indicators and targeted industries
Pulsar indicators and targeted industries
Pulsar RAT is a reminder that quiet threats can be the most dangerous. By prioritizing persistence and access, it enables attackers to move patiently, exploit trust, and maximize long-term impact. Organizations that combine proactive detection, sandbox analysis, and high-quality threat intelligence stand the best chance of uncovering and stopping such intrusions early.
Trial TI Lookup to start gathering actionable threat intelligence on the malware that threatens your business sector and region: just sign up to ANY.RUN.