Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


Caminho Loader is a Brazilian-origin Loader-as-a-Service operation that uses steganography to conceal .NET payloads within image files hosted on legitimate platforms. Active since March 2025, it has delivered a variety of malware and infostealers to victims within multiple industries across South America, Africa, and Eastern Europe.
|
Loader
Type
:
|
Unknown
Origin
:
|
|
1 March, 2025
First seen
:
|
9 February, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 March, 2025
First seen
:
|
9 February, 2026
Last seen
:
|

 736
736
 0
0

 460
460
 0
0

 2688
2688
 0
0
Caminho hides malicious .NET payloads inside innocent-looking images using Least Significant Bit steganography, making detection extremely challenging for traditional security controls.
The malware loads and executes entirely in memory without writing files to disk, defeating file-based antivirus scanning and leaving minimal forensic artifacts.
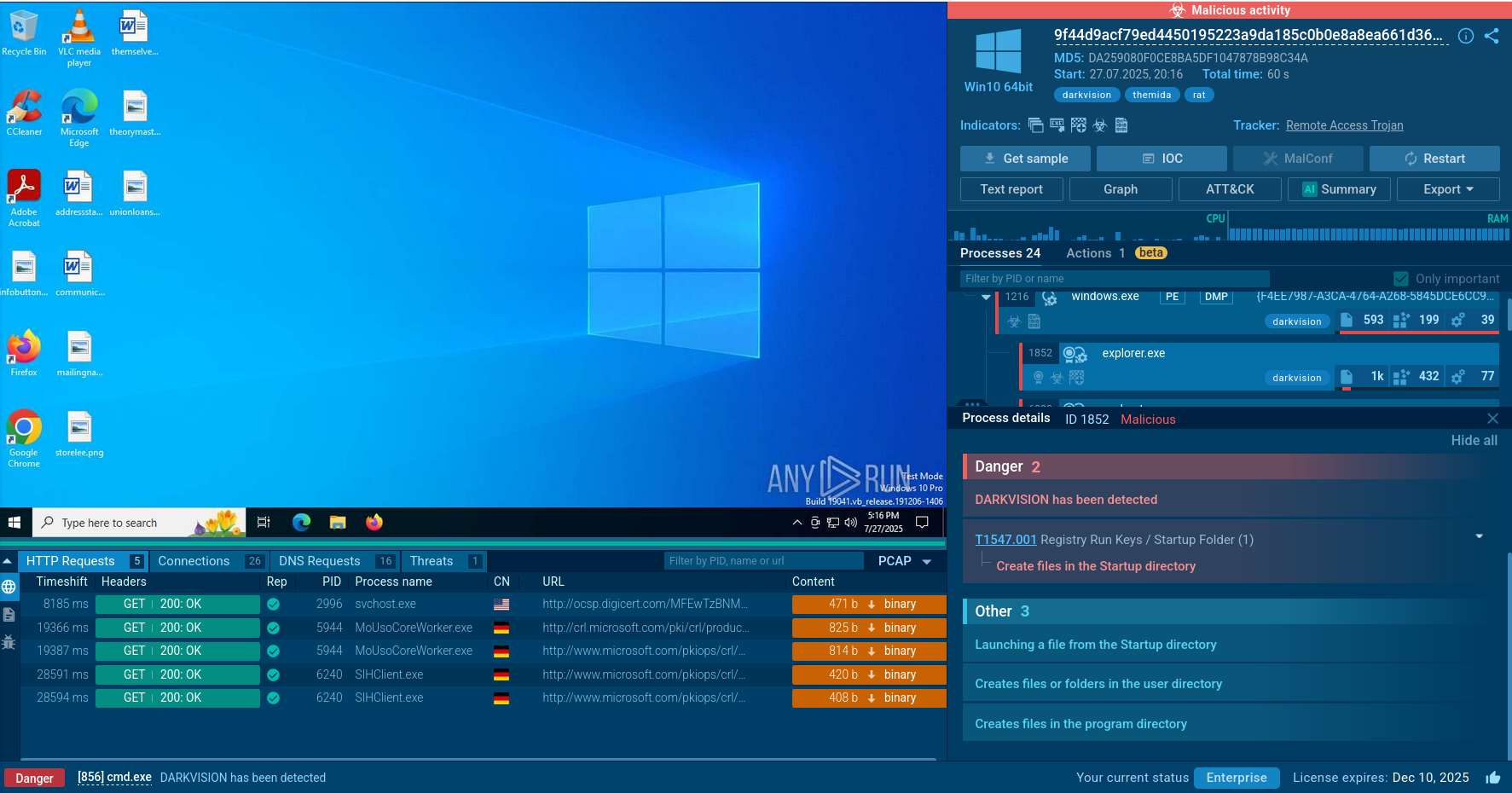
Caminho operates as a commercial service where multiple cybercriminal customers rent access to the delivery infrastructure while providing their own final payloads including REMCOS RAT, XWorm, and Katz Stealer.
The operation exploits trusted services like archive.org for hosting steganographic images and Pastebin services for script staging, evading reputation-based security controls.
56 Active since March 2025 with confirmed victims in Brazil, South Africa, Ukraine, and Poland, demonstrating rapid geographic expansion beyond initial South American targeting.
threatName:"caminholoader" or threatName:"caminho".
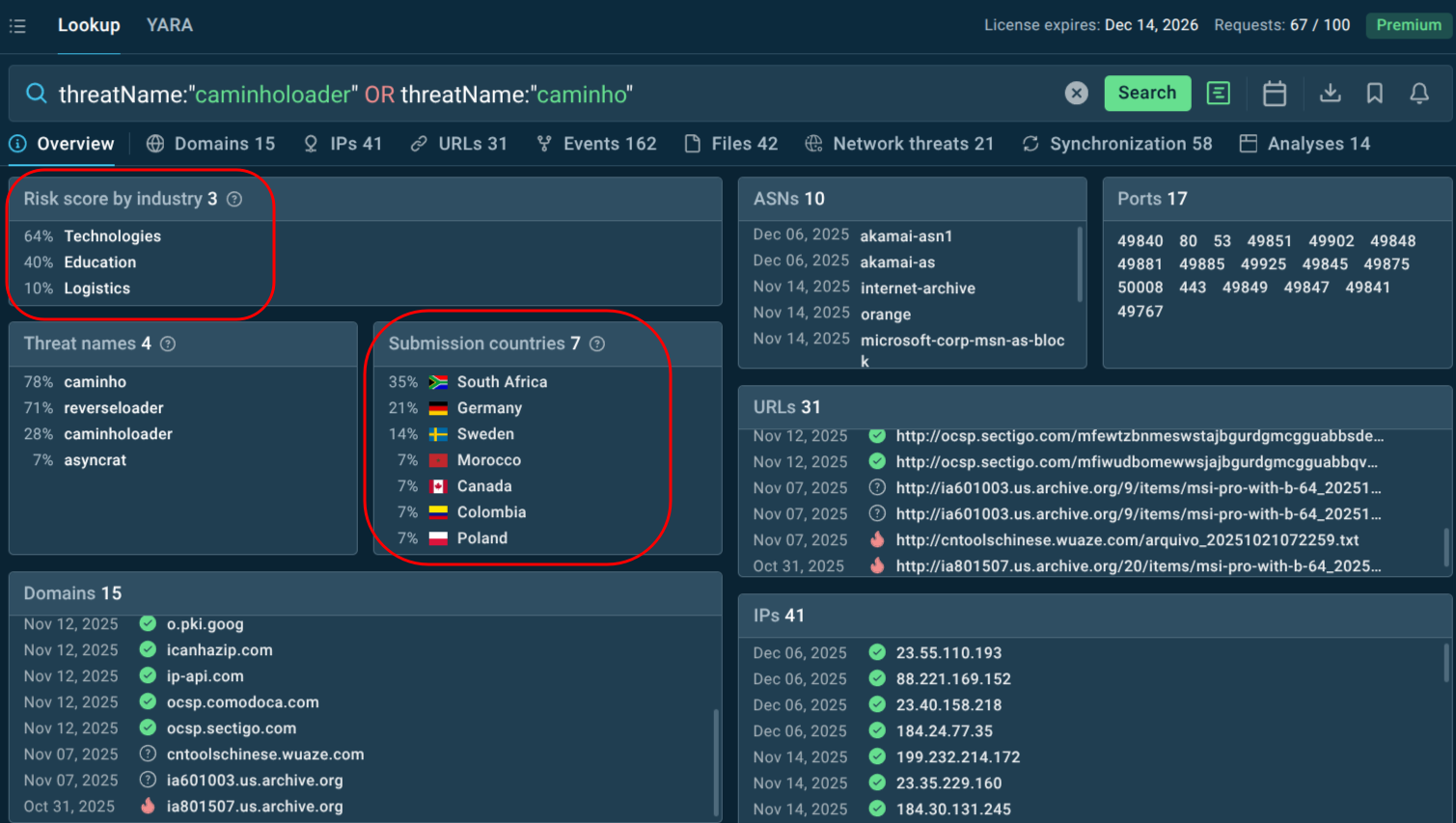 Search for malware’s name to see active campaigns and fresh samples
Search for malware’s name to see active campaigns and fresh samples
 Caminho Loader malware analysis
Caminho Loader malware analysis
Caminho Loader is a sophisticated Brazilian-origin Loader-as-a-Service (LaaS) malware, active since March 2025. It employs Least Significant Bit (LSB) steganography to conceal .NET payloads within innocuous image files, enabling fileless execution and delivery of various remote access trojans (RATs) and stealers like REMCOS, XWorm, and DCRAT.
Caminho, which means "path" in Portuguese, represents a significant evolution in malware delivery techniques. The PowerShell next extracts a concealed .NET Loader from the image using LSB steganography, loads it directly into memory, and invokes it with arguments specifying the final payload URL. What makes Caminho particularly dangerous is its fileless execution model that bypasses disk-based detection systems.
Analysis of 71 Caminho Loader samples reveals consistent architectural patterns despite varying obfuscation, with all samples containing Portuguese-language strings and the distinctive HackForums[.]gigajew namespace artifact. The loader implements extensive anti-analysis measures including virtual machine detection, sandbox identification, and debugging tool recognition, making it extremely difficult for security researchers to analyze.
The malware operates as a Loader-as-a-Service business model, meaning multiple cybercriminal customers can rent access to the delivery infrastructure while supplying their own final payloads. The standardized invocation interface accepts arbitrary payload URLs as arguments, allowing multiple customers to deploy different malware families using the same delivery infrastructure. This modular architecture explains why the same steganographic images appear across multiple campaigns delivering entirely different malware families.
Caminho primarily targets organizations in South America (especially Brazil), Africa (e.g., South Africa), and Eastern Europe (Ukraine, Poland). One notable campaign by the BlindEagle APT group (also known as APT-C-54) targeted a Colombian government agency under the Ministry of Commerce, Industry, and Tourism in September 2025. Victims span various industries, lured by business-themed phishing emails (invoices, quotations). Attacks are opportunistic rather than highly targeted at specific sectors, focusing on entities where users are likely to open attachments or links.
The multi-stage infection chain begins with spear-phishing emails containing archived JavaScript (JS) or VBScript files using business-themed social engineering lures. The attackers craft convincing emails impersonating legitimate business communications, with compressed RAR or ZIP archives attached.
The archives use file names that are socially engineered to entice victims to open them. A fake invoice is one of the most common formats used for phishing, because the recipient's concern of missing a financial payment or being required to make one invokes a sense of urgency. Other common lures include quotation requests, business proposals, and shipping notifications.
When victims open these attachments and execute the JavaScript or VBScript file, the initial script contacts Pastebin-style services like paste.ee or pastefy.app to retrieve obfuscated PowerShell code. These legitimate pasting services provide free hosting and are difficult to block without disrupting legitimate business operations.
The PowerShell payload then downloads seemingly innocent images from trusted platforms like archive.org. Because these platforms enjoy high reputation scores and are used for legitimate purposes, security systems typically allow these downloads without raising alerts.
The PowerShell script then performs the steganographic extraction, loading the hidden Caminho Loader directly into memory. The loader subsequently reaches out to attacker-controlled infrastructure to download the final payload — REMCOS RAT, XWorm, Katz Stealer, or another malware family depending on the customer's choice.
Lateral movement and spreading depend on the final payload deployed. Remote access trojans like REMCOS and XWorm enable attackers to manually spread through networks by stealing credentials, mapping network resources, and deploying additional malware to other systems. However, Caminho Loader itself does not include self-propagation or worm-like spreading mechanisms.
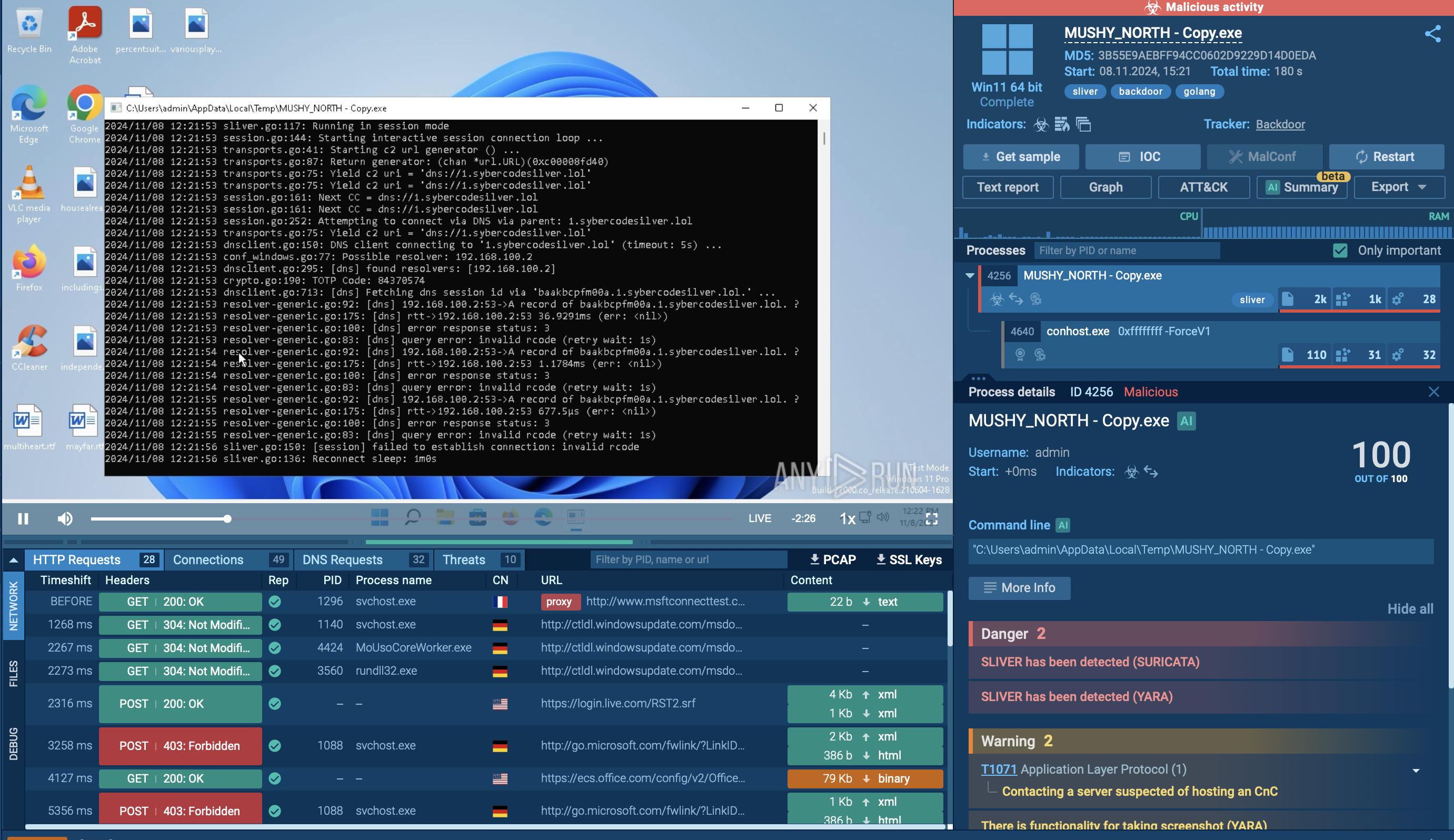
ANY.RUN’s Interactive Sandbox overcomes Caminho’s ant-detection and sandbox-evasion mechanics, exposing the full attack chain.
View a Caminho Loader sample analysis
 Caminho Loader dissected in the Interactive Sandbox
Caminho Loader dissected in the Interactive Sandbox
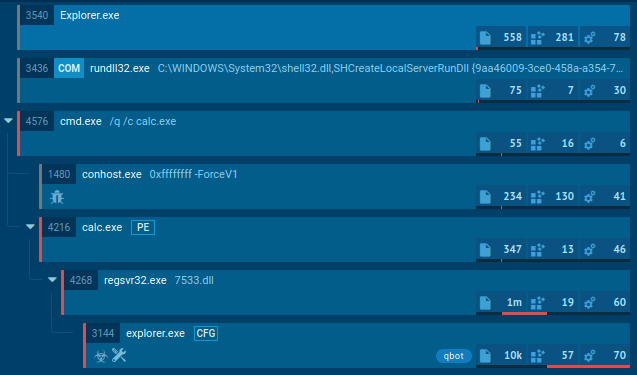
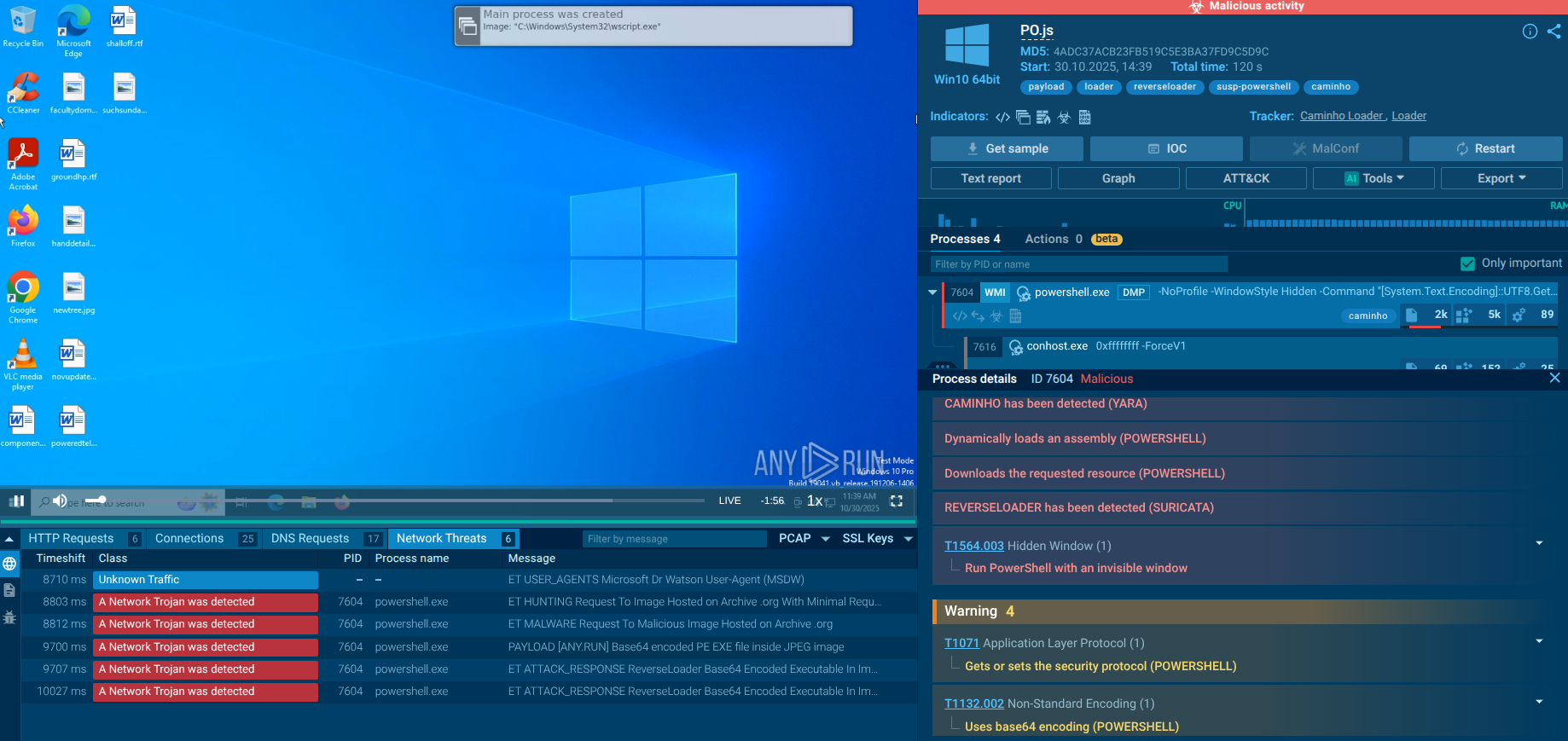
The loader is a JavaScript script that uses several obfuscation techniques. Based on the tracer output, the following conclusion can be drawn:
The script initializes tools for file and network operations, determines its own current path, pauses for 5 seconds, and then silently launches a hidden PowerShell instance. After that, it prepares to download or process data from the internet.
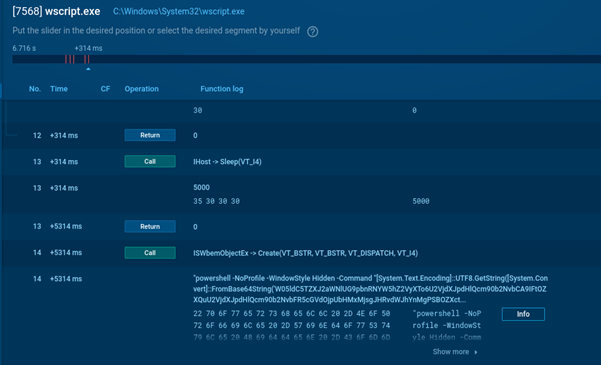 Malicious script launching a PowerShell process
Malicious script launching a PowerShell process
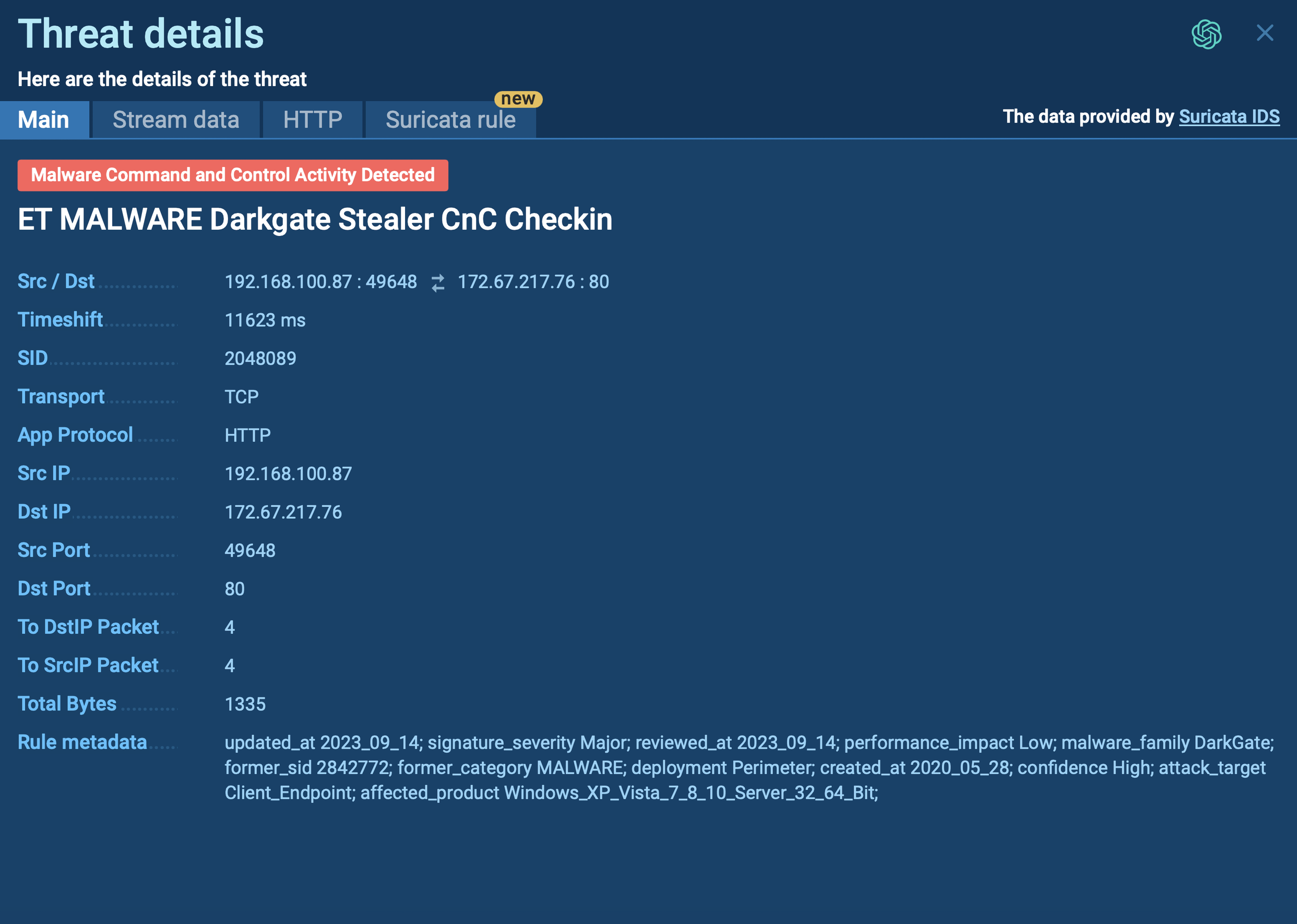
When the Base64 is decoded, it becomes clear that PowerShell downloads content from an image file hosted on archive.org, locates embedded Base64 data within it, converts that data into an executable program directly in memory, and then invokes a specific function with additional encrypted parameters and references to folders and files on the disk.
 Loader retrieves its functionality from a web archive picture
Loader retrieves its functionality from a web archive picture
In this sample analysis, the malicious payload has not been delivered. View another sandbox session to see how this might happen:
View another Caminho Loader analysis
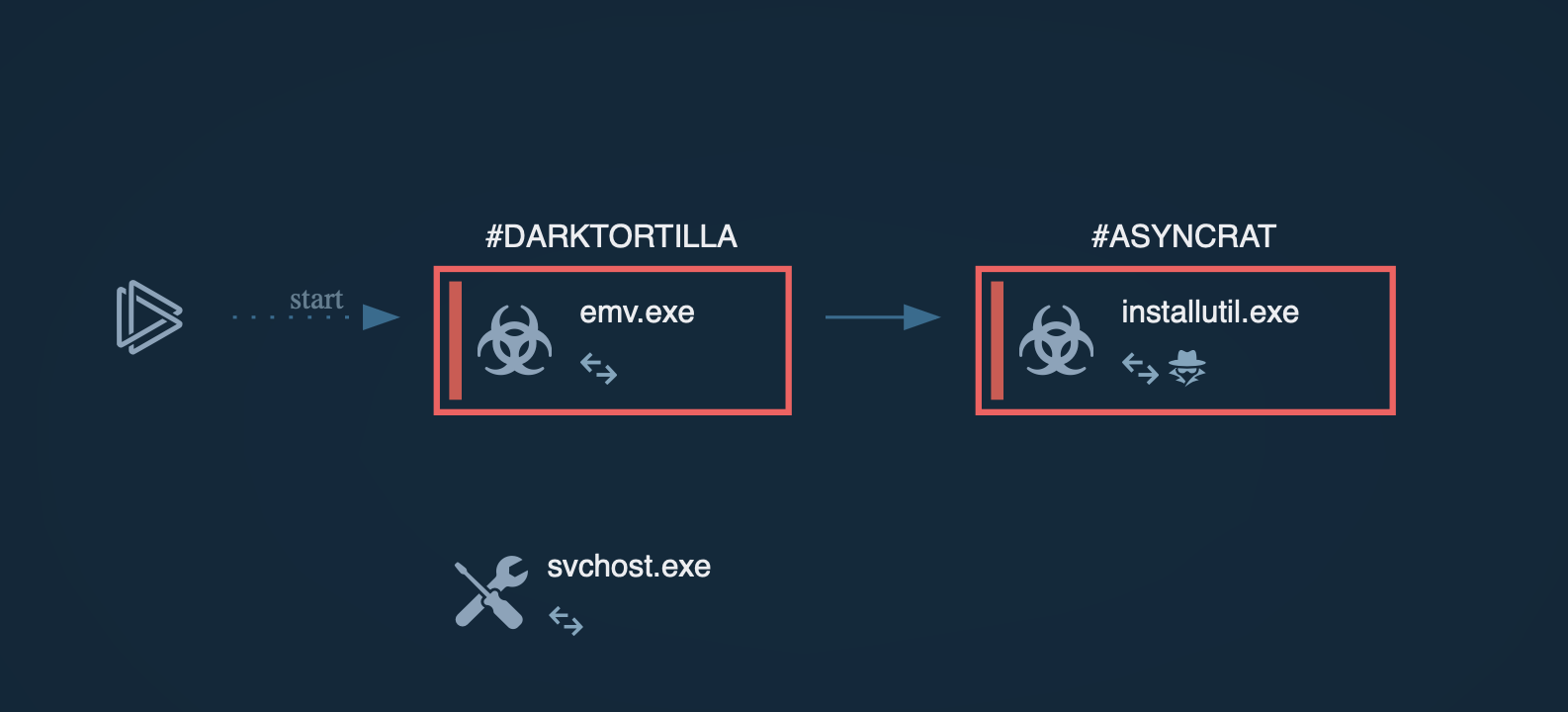
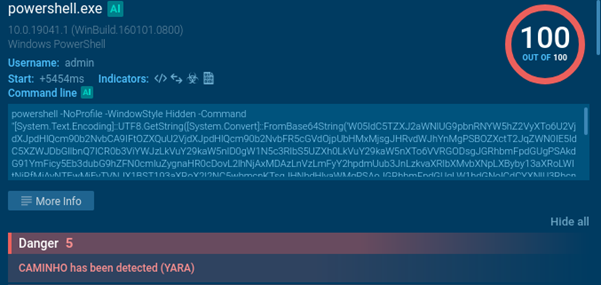
As a result of the loader’s activity, we observe AsyncRAT injected into the AddInProcess32 process.
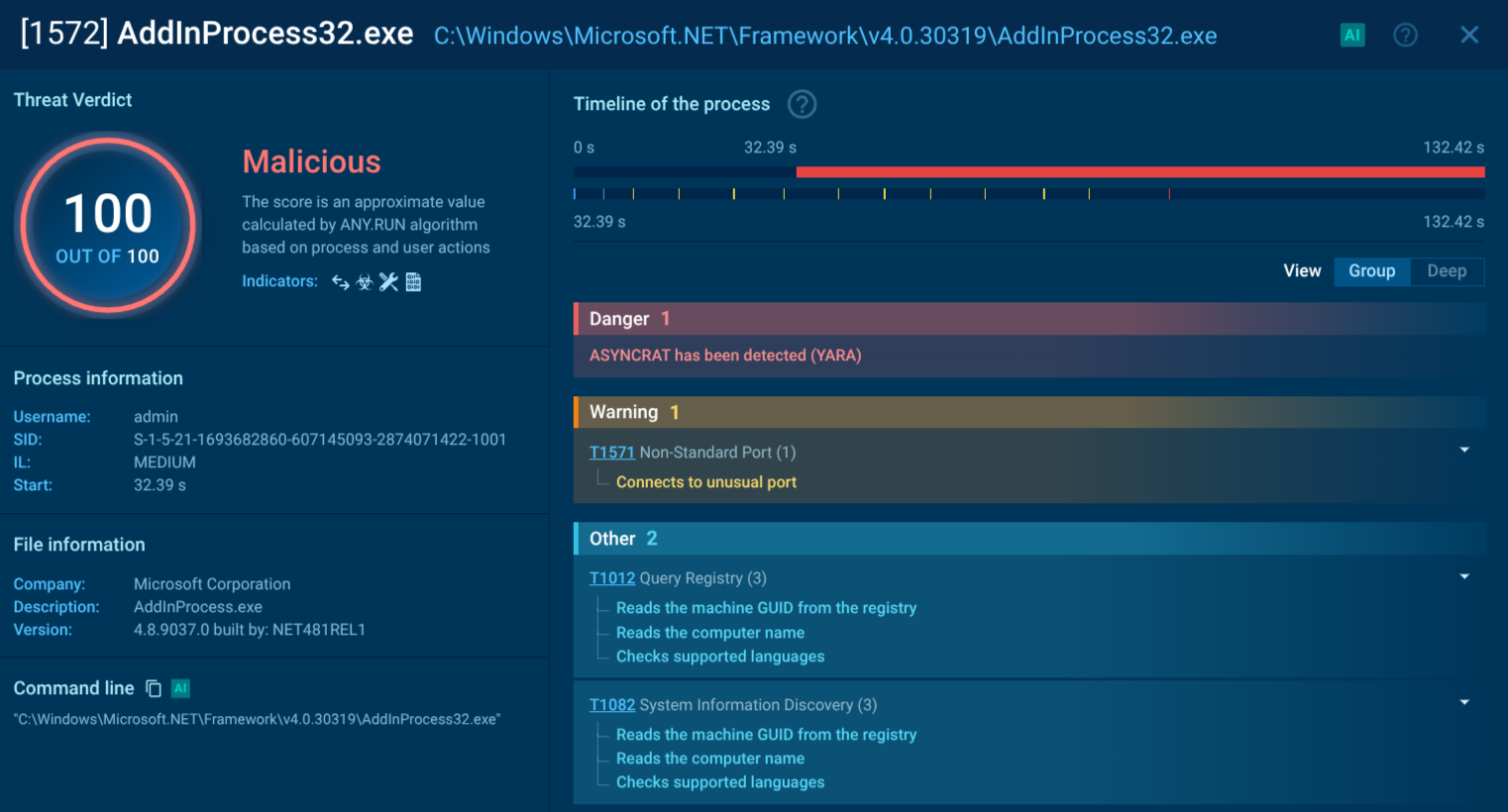 Caminho Loader delivers payload: AsyncRAT trojan
Caminho Loader delivers payload: AsyncRAT trojan
ANY.RUN's Threat Intelligence Lookup gives security teams instant access to a vast database of analyzed malware samples. Businesses can quickly search for Caminho-related hashes, domains, IPs, explore YARA/Sigma rules. This enables rapid blocking of indicators, enrichment of detection rules, and proactive threat hunting — helping organizations stop steganographic loaders and similar fileless threats before they cause damage.
Use TI Lookup to explore fresh Caminho samples analyzed in the Sandbox by a community of over 600K ANY.RUN’s users:
threatName:"caminholoader" or threatName:"caminho".
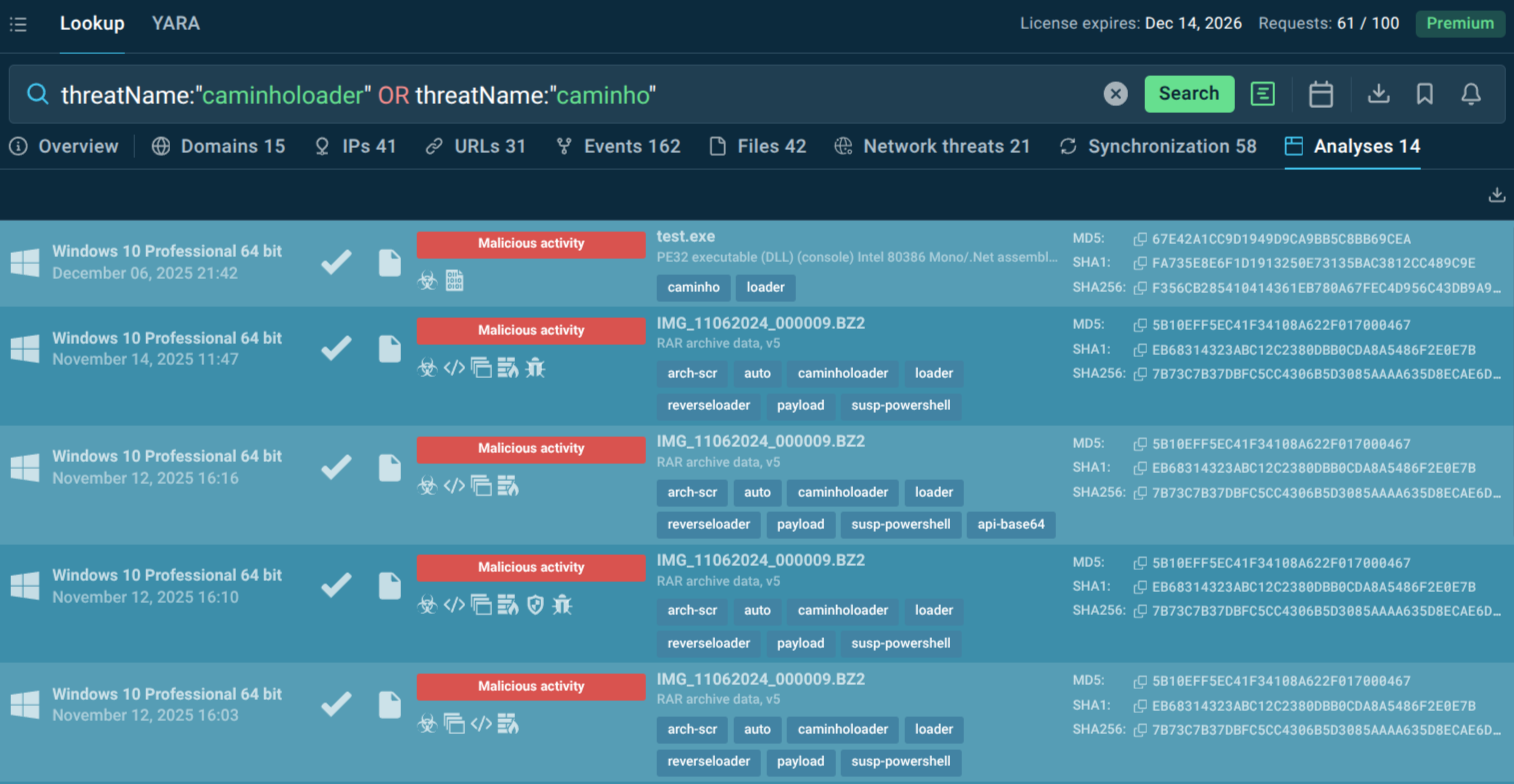
Caminho Loader sandbox analyses
Caminho Loader exemplifies modern malware evolution: blending steganography, fileless execution, and a service-based model to evade defenses. Originating from Brazil but impacting global victims, it underscores the need for layered security, user awareness, and advanced analysis tools to counter such stealthy threats.
Trial TI Lookup to start gathering actionable threat intelligence on the malware that threatens your business sector and region: just sign up to ANY.RUN.