ANY.RUN is a malware sandbox that has a database with more than 2 million submissions. Every day 8,000 tasks are run by users all over the world. And a lot of samples are connected with COVID-19.
On November 17, 2019, the first case of Coronavirus was recorded. More than a year ago the virus hit the world, all spheres, organizations, and people, forcing everybody to get used to the new reality.
And cybersecurity has been affected by it, too. This topic is still taking over as the most popular decoy used by spammers and phishers. Cybercriminals apply social engineering to capitalize on people’s concerns about the global outbreak of disease.
Today we’ll discuss how a year with COVID-19 impacted cybersecurity from ANY.RUN’s point of view.
Phishing decoys with COVID-19
Criminals always take advantage of major events in phishing campaigns. The COVID-19 outbreak has become the reason for fear and uncertainty in all spheres, so it has become an ideal disguise for attacks. Phishing has increased a lot due to the Coronavirus. And threat authors spread malware to steal personal information using various options.
Based on the ANY.RUN’s submissions, we can report that there are different kinds of phishing decoys that malware uses. Thanks to the service’s interactivity we could detect various malicious programs that were hiding behind these examples:
- Advertisements for Coronavirus services and products
Facemasks, medical supplies, special offers – these advertisements make users fall for the clickbait. But these actions can lead to information extraction from the victim’s computer system, its infection, and collecting credit card data.
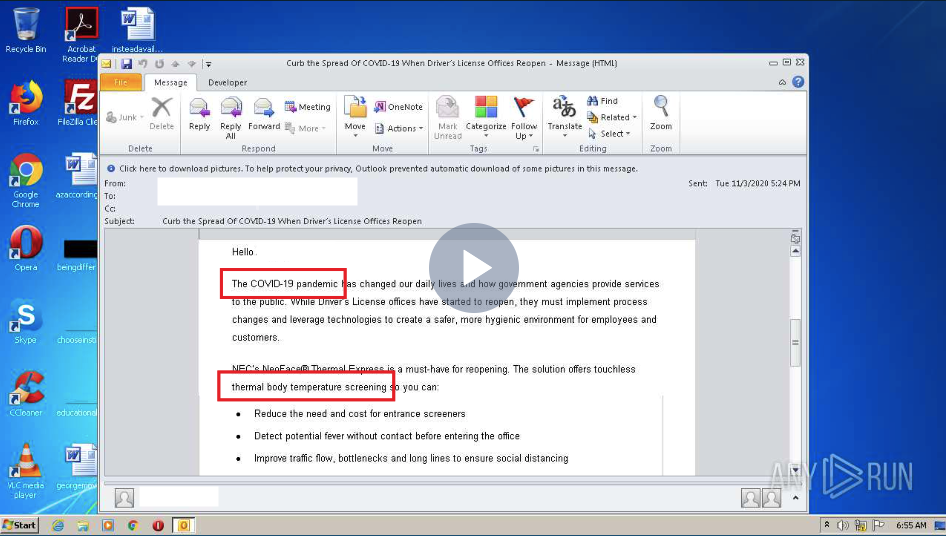
If you like you can check out the tasks with the smell test sample and the temperature screening example.
The dark web also contributes to the corona sale: cybercriminals sell malware and exploitation tools using COVID-19 codes and discounts. Hackers are offered to buy phishing email kits, Facebook account hacking tools, or malware-as-a-service.
- Coronavirus-Related Maps
Threat actors create different attachments and websites that display a map representing Coronavirus spread. It offers users to click or download an application to stay informed of everything that happens. The map generates a malicious binary file and infects targets’ computers.
In this case, criminals may use AZORult malware to steal users’ browsing history, cookies, IDs, passwords as well as install other malware.
The map task is available for your research, don’t forget to have a look!
- Vaccine
Promises of a vaccine are actively used in phishing. Drug companies developing vaccines as well as common users become targets of malicious attacks.
- Coronavirus News Stories
The Coronavirus latest updates are a very popular topic in spam and malicious emails. They pretend to be the Ministry of Health newsletters or others. It can provide recommendations on how to avoid infection in an attachment but instead of advice, you get malware.
Try out the statistics example and the updates example by yourself.
- Coronavirus funds and payments, job listings
Cybercriminals send emails faking reliable and official organizations like the Federal Trade Commission, with information about the virus and special funds, that can provide some financial help. Hundreds of people found themselves unemployed because of the pandemic. And it drives them to click on opening malicious emails with job possibilities or payment offers and forms. However, embedded links and attachments are most likely to lead to the infection by malware.
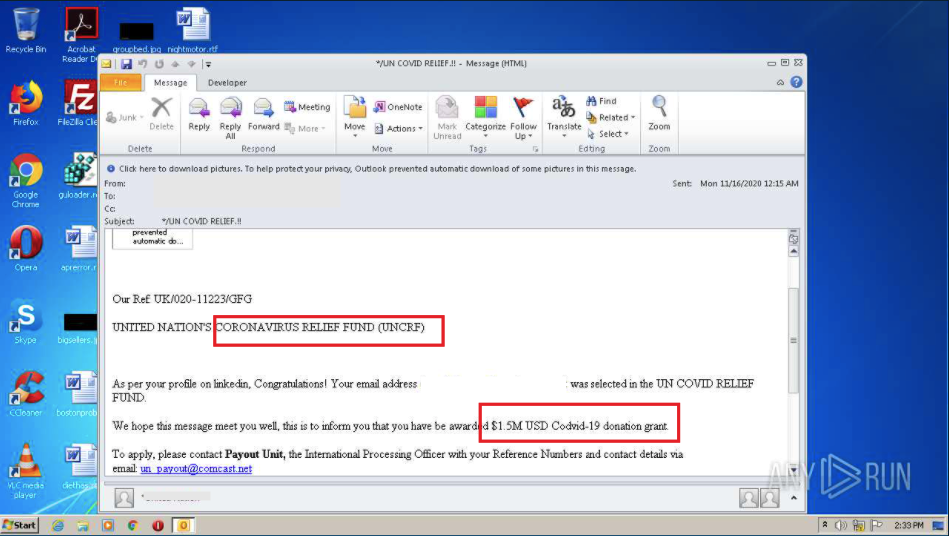
Would you like to trace the fund sample and find out what malware this decoy contains? Just go ahead and do it!
- School updates
Instead of faking information on the virus, threat actors leverage school updates and job listings related to the topic. For example, many schools require the health information of students as part of their safety protocols. In October, the University of British Columbia staff suffered from ransomware while completing a phony health survey.
File extensions types of COVID-19 decoys
Crooks lure people into taking risky actions by various phishing decoys. And victims buy for them without a second thought about the consequences, because all baits look valid. Everything is applied: from malicious documents to web pages that save files with the “Coronavirus” name in the system.
First of all, it’s worth mentioning the file names that trigger users the most:
- Name list for funds or payments
- Donation proposal
- COVID-19 update/situation report/news summary
- General information on Coronavirus disease
- Coronavirus Checklist/guidelines for employees and organizations
- COVID-19 Measures
- Test form/application
Here are the most common file extensions with examples. And don’t forget that you can investigate all the tasks mentioned by yourself.
– PDF
The PDF task‘s file is supposed to contain hospital information on the virus, but the link leads to stealing a password.
– documents
For example, the document sample offers coronavirus-related tax relief measures and a Netwire as a bonus.
– sites
Every day 1,767 high-risk Coronavirus-themed domain names are created. There are more than 5 billion pages related to the topic on the Internet. Have a look at one of them in the site task.
– EXE
The following file from the EXE sample is a live tracker, that attacks the network and has several malicious connections.
– archives
Malicious connections and a detected Network trojan come as a surprise in this archive example. We bet, this opposite of what you’re hoping to unpack.
These tempting decoys are spread and used widely. But what’s waiting for the victim if they can’t resist a clickbait? Let’s talk about the top malware that hackers prefer during the Coronavirus outbreak.
Malware used during the pandemic
Malware writers exploit all kinds of malware and tactics masking behind the virus and benefiting from it. There is no unified structure that criminals follow and all sectors are at risk.
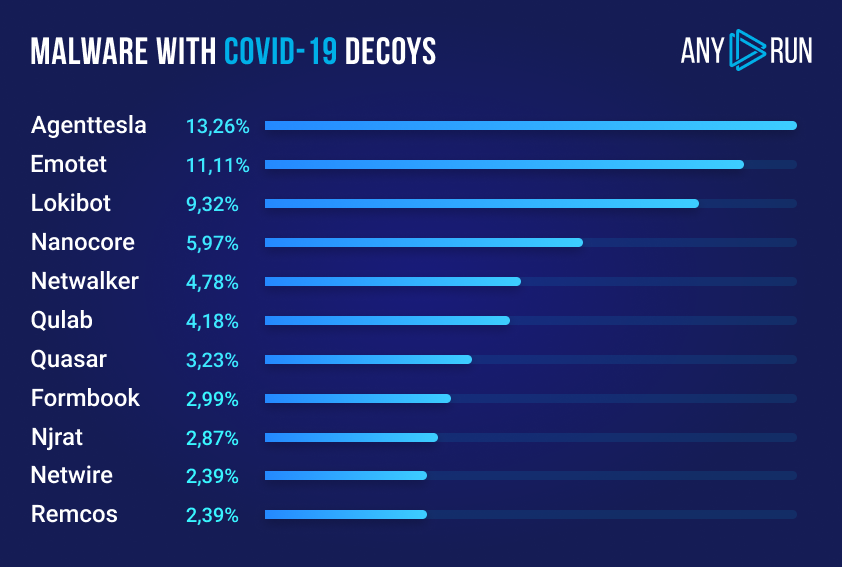
In the figure above you can see the statistics of threats by uploads with the Covid-19 theme for the December 2019 to December 2020 period. There are 13192 virus-themed samples from the public submissions that we analyzed. Of course, not every sample with the COVID-19 tag is malicious. But 6052 tasks appeared to contain malware or do any other harmful activities.
And there are some notable results of our analytics:
Agent Tesla, Emotet, Lokibot, Nanocore, and Netwalker are the top 5 malware capitalizing on the virus. Here are the reasons why they’ve become so successful.
1. Agent Tesla
The spyware is very affordable for attackers, about $15-70. Authors of the malware are ready to help criminals who have even no technical background with support, customizable options, and expanded functionality. Moreover, it has good evasion techniques.
2. Emotet
A sophisticated malware that developed from a standard Trojan to the polymorphic distributor of other malicious programs. Emotet is extremely hard to clean up. In addition, it can evade sandboxes, change its code, receive updates, and adapt to different attacks.
3. Lokibot
Criminals who use Lokibot in their attacks are able to install additional malicious software. Besides, it contains a keylogging feature.
4. Nanocore
This accessible RAT is very easy to use and has a big range of configurations for attackers’ needs.
5. Netwalker
The notable Netware feature is that it’s written in PowerShell so it executes directly in memory and without storing the actual ransomware binary into the disk. This makes the ransomware a real challenge to detect.
The usage of the malware above is constantly increasing. And it’s no surprise, as they have such an environment to thrive in. Let’s have a closer look at the most popular malware types, their features, and tactics to be aware of how they usually act.
Popular malware types
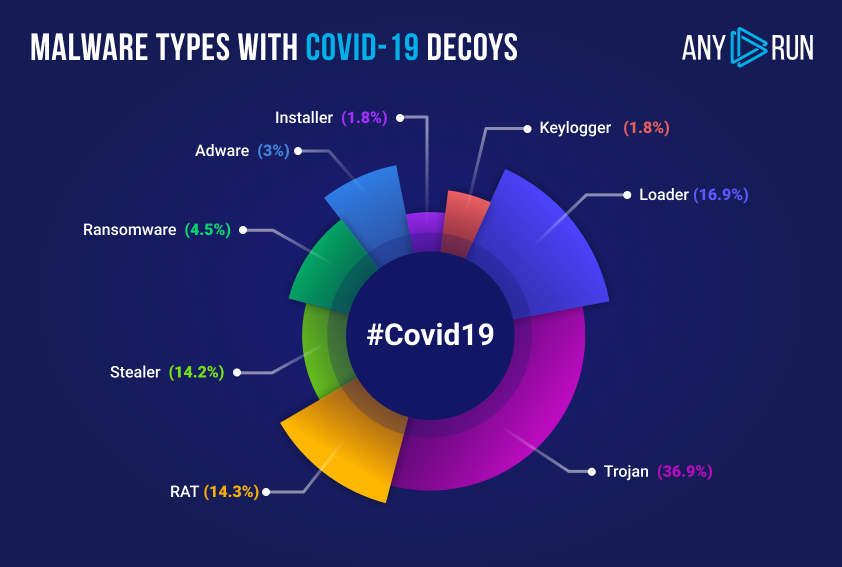
Here are the most popular malware types that are on the rise during the pandemic according to the ANY.RUN’s uploads:
1. Trojan
Trojan malware is designed to take over your machine. It is capable of damaging, disrupting, stealing, or other harmful actions with data or networks.
2. Loader
These viruses’ main goal is to install other malware on the infected system. Basically, this type drops an infected payload. However, they can steal data or be engaged in spying.
3. RAT
With Remote Access Trojan a victim doesn’t even know that their computer is monitored and controlled. The remote access gives attackers the possibility to control infected machines completely and anonymously.
4. Stealer
As you know, an information stealer gets into an infected device and collects your personal information to send it to criminals.
5. Ransomware
Some of the “teams” behind ransomware such as Netwalker besides encrypting data and demanding a ransom to restore it, use the double-extortion ransomware. It threatens to publish or sell the enciphered data if there is no payment.
According to the latest research, the number of ransomware attacks is estimated at 199.7 million cases in the 3d quarter of 2020 globally. Considering that the US only suffered from 145.2 million ransomware hits, which is a 139% year-over-year increase compared to the previous year.
Remote work
COVID-19 forced organizations to get adapted to remote work very quickly. There is no corporate perimeter now, where companies used to organize everything centrally. Working remotely requires profound security improvements. You should also get ready that remote work isn’t going anywhere in 2021.
And every employee needs to contribute to avoid any data exposure and securely navigate their work tools. Being aware of possible threats and getting to know even basic precautions can help to prevent damage. So, staff education should be one of the main concerns, especially taking into account social engineering schemes in attacks. You should also know how to work remotely in the cybersecurity sphere and the way to structure your work from home.
How can ANY.RUN help?
The more and more types of malware use the decoys connected to COVID-19. And in ANY.RUN, we try to help users get through scams, bring malware to light, and not fall for its tricks.
Here are several perks you can use to avoid pandemic related threats:
- ANY.RUN is an online sandbox: it’s essential, especially with remote work. You can investigate suspicious attachments or other files received by your organization’s employees, and that is totally safe. Export IOCs from your tasks or other users public tasks and import them into your security tools, so you can block access to phishing sites from your network or detect suspicious activity in it;
- ANY.RUN’s interactive approach: malware from files, emails, web pages, or apps can require some human engagement to start its execution. So, any user can go ahead and do it in the virtual machine – you can click, move a mouse, open a browser, input data to provoke a malicious program.
- ANY.RUN provides a database of COVID-19 samples to research examples. You can analyze all existing cases to improve your security. And if you’re interested in various kinds of malware, you’re free to explore more than 2 million samples that are updated daily.
If you want to know more about how Coronavirus malware was detected in ANY.RUN, check this video for more samples and reviews.
Conclusion
Malware develops as it usually does when major events happen. The pandemic struck hard, and cybersecurity faced a lot of attacks. If you don’t want to break under the malware pressure, get prepared. With ANY.RUN, you can improve your work and become stronger – exactly what we need these days.
Stay safe!








0 comments