ANY.RUN interactive sandbox excels in analyzing malware that evades automated solutions, which means that we always have a supply of interesting samples. Trusted by top security teams worldwide, the ANY.RUN malware sandbox sees over 14,000 sample submissions daily from our community.
Our malware analysts at ANY.RUN use this — and other resources — to continuously scan the threat landscape. Make sure to follow our ambassador Jane and ANY.RUN’s official page on Twitter for interesting findings and timely updates.
But in case you missed some of recent posts, this article compiles our notable observations about the threat landscape from the past month.
1. Steganography
We identified a new phishing campaign utilizing steganography, a technique historically seldom used due to its complexity. However, its application has notably increased.
Read our analysis of steganography in phishing.
As of recently, the campaign subsided, but new samples suggest its resurgence — as seen in this sample.
This new campaign employs steganography in multiple stages:
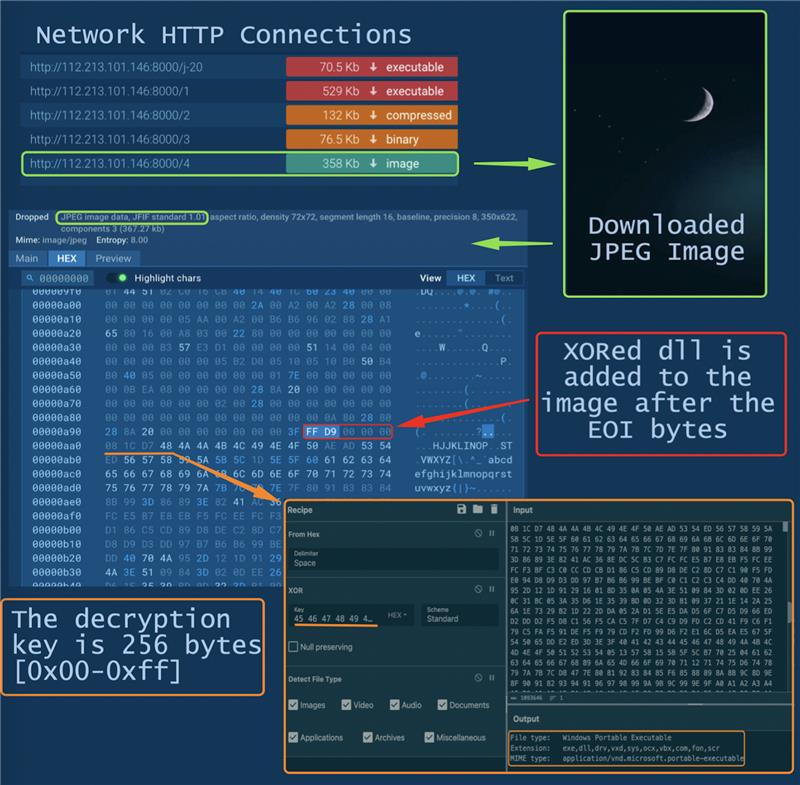
- The modified “Google Update” app downloads multiple PE files and an image containing a DLL
- TrueUpdate, downloaded in the previous step, extracts and decrypts the DLL from the image file with 256 bytes XOR key and transfers control to the received DLL
- Then a malicious module comes into play, hosting a Remote Access Trojan and intercepting control. The actions of gh0strat become evident on the network at the specified address: 112.213.101.146:7700
You can find more samples that employ steganography in ANY.RUN’s public submissions — just search by tag #stego or use this link.
2. Tycoon platform using WebSocket to communicate
Tycoon is a 2FA – Adversary-in-the-Middle (AiTM) and Phishing-as-a-Service (PhaaS) platform.
Let’s examine the network traffic using this sample. Our example consists of 3 stages separated by a CAPTCHA verification challenge:
First Stage
This initial phase involves loading obfuscated script bodies, supplementary libraries, content, and page construction scripts. The process unfolds as follows:
- Loads the obfuscated loader script body
- Myscr685428.js
- Loads additional libraries, content and page construction scripts
- jquery-3.6.0.min.js
- http://socket.io.min.js
- css, woff2
- pages-head-top-web.min.js
- pages-head-web.min.js
- Implementing CAPTCHA verification challenge
- challenges[.]cloudflare[.]com/turnstile
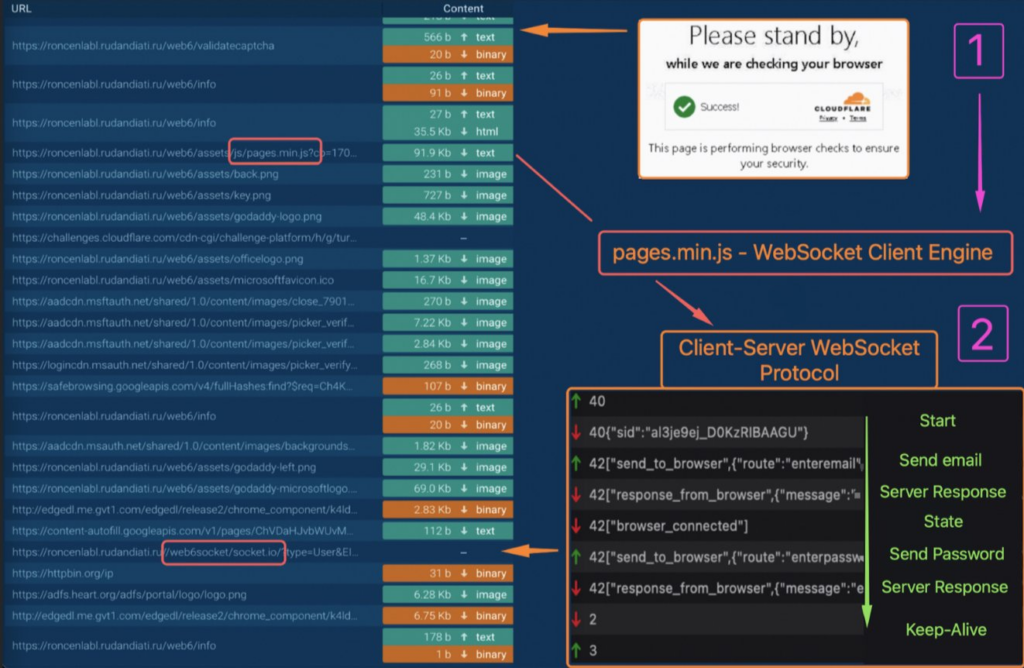
️Second stage
The rest of the content is loaded, and connection begins with a proprietary protocol via WebSocket.
- For this purpose, the obfuscated client engine is loaded
- Pages.min.js
- Makes an external IP address request to httpbin[.]org/ip
After that, the engine upgrades the connection to WebSocket:
web6socket/socket.io/?type=User&EIO=4&transport=websocket
Third stage
During interaction with the server, the client engine creates a login page on the browser side according to the server’s responses. The connection with the server stays active via Keep-Alive packets, ensuring that there is low latency in the victim’s browser.
3. Continued abuse of legitimate services and techniques
A prevalent trend is the misuse of legitimate services to spread phishing scams.
In our example, attackers have exploited the InterPlanetary File System (IPFS), Google Translate, and the page jump anchor technique to embed an email within a phishing script. Let’s examine the URL structure to understand this method better:
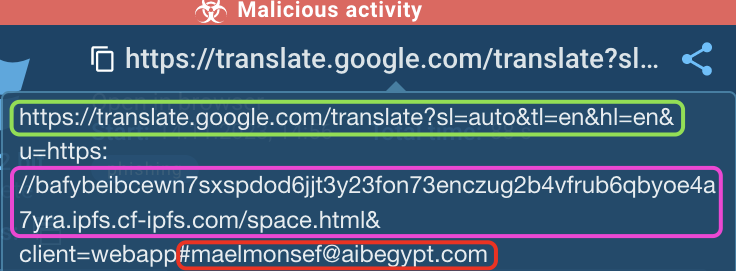
We’ve outlined notable parts in different colors. Here’s what they mean:
Green
- sl: Source language code
- tl: Translation language
- hl: Language of the interface
- u: URL
Purple
The file ‘space.html’ is stored using IPFS
Red
Victim’s email address – maelmonsef@aibegypt[.]com
4. Ransomware research with good intentions but a disastrous result
This case study underscores how careful you need to be when doing malware research. Always ask yourself: can it end up in the wrong hands and potentially cause harm?
One student developed an academic proof of concept of a Windows crypto-ransomware called MauriCrypt. You can find it in this Github repo. His public research didn’t go unnoticed by adversaries.
The students’s malware was flagged in attacks under the CryptGh0st ransomware name. Here’s a CryptGh0st sample in ANY.RUN for reference.
And here’s how you can be decrypt the files, as long as there’s network traffic:
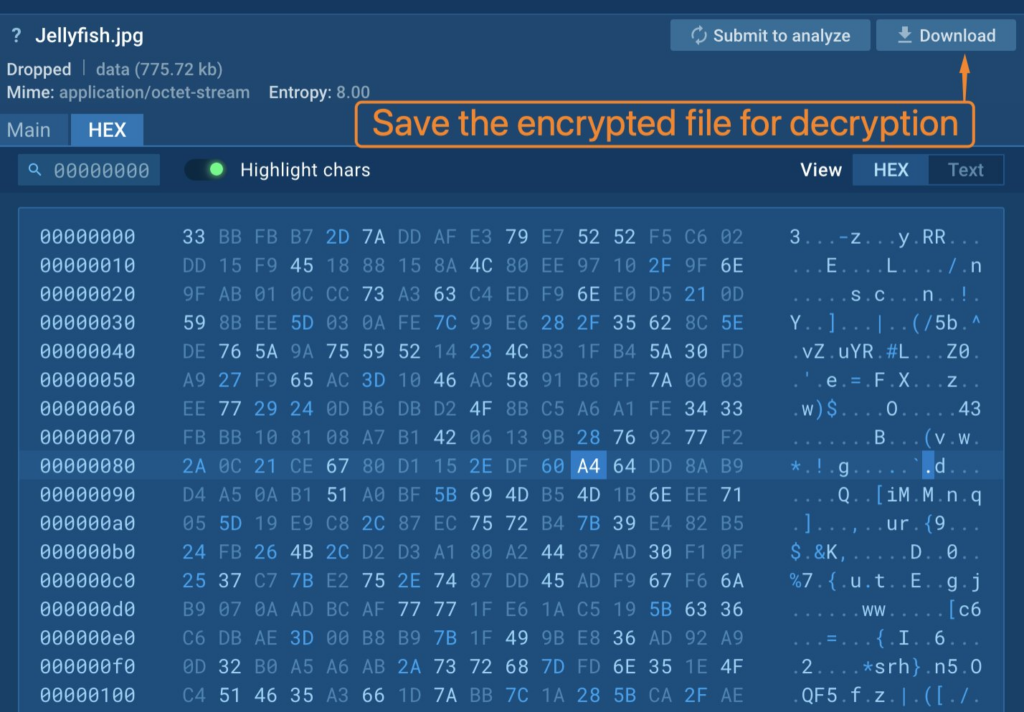
First, copy the encryption key to the clipboard.
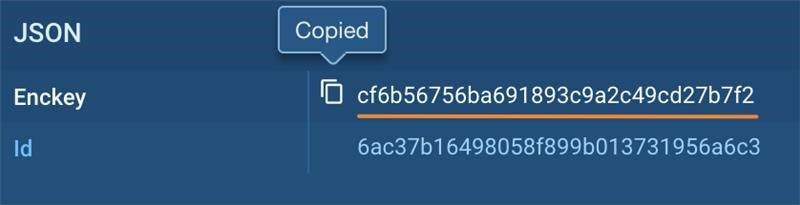
Then, save the encrypted and zipped file for decryption.
Decrypt the file using a CyberChef recipe we’ve prepared:
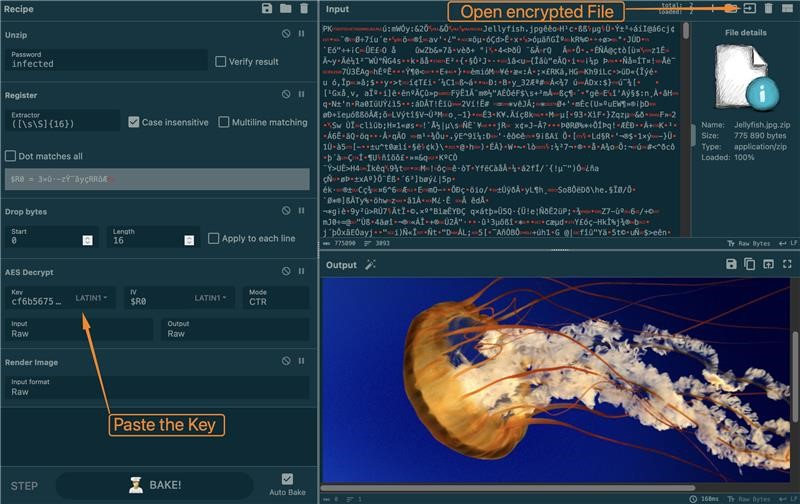
Be careful when publishing your projects or research results!
5. socks5systemz malware
This malware, first spotted by our sandbox 3 years ago, turns victims’ devices into proxies for forwarding traffic.
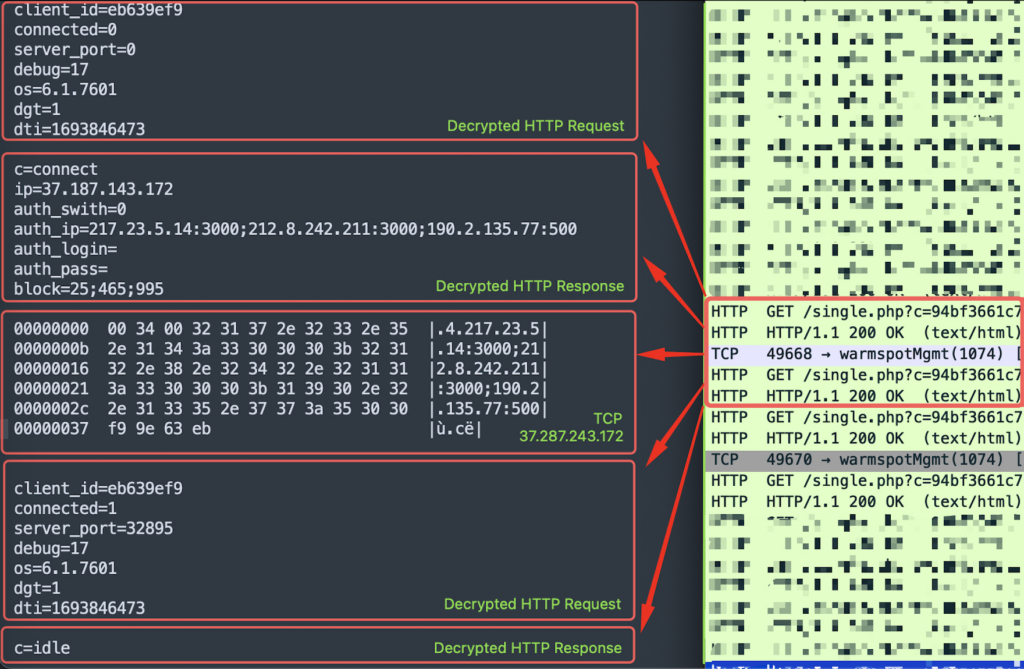
The malware attempts to connect via HTTP request to port 80 and a backconnect server over port 1074/TCP. By combining these two connections for the connect and updips commands, we illustrate on the screenshot above how socks5systemz can be used to proxy traffic.
Find samples of this malware in public submissions by searching with #socks5systemz tag. You can also find socks5systemz in the public database using the signature 2829008.
We’ve also prepared a CyberChef recipe for decrypting command connections.
Wrapping up
This was our compilation of notable samples, case studies, and threat-landscape observations from this month. Did you find this format informative? Let us know in the comments below.
A few words about ANY.RUN
ANY.RUN is a cloud malware sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams. Every day, 300,000 professionals use our platform to investigate incidents and streamline threat analysis.
Request a demo today and enjoy 14 days of free access to our Enterprise plan.










0 comments