Today, cyberattacks are frequent and indiscriminate, striking small businesses and large corporations alike. Research shows that over 60% of organizations worldwide have experienced a cyber security incident at least once, and over 50% of attacks targeted SMBs.
Dealing with a cyber incident can be costly business. In a recent example, an attack directed at INRS — a university in Quebec — put the systems of this Canadian academy completely out of order. The cost of restoring them amounted to almost $270,000.
But despite just how devastating these attacks are, 77% of organizations still lack incident response strategies or apply them haphazardly, an IBM Security study shows.
Having no clear instructions on what to do during a breach puts security teams in a vulnerable state — it is unlikely that under stress such teams will perform optimally. And this means mistakes and exacerbated damages.
One of the steps to correcting this is creating a cyber incident response plan.
What is a cyber incident?
But before we jump into the details of creating a plan, let’s first establish a definition to understand what constitutes a cyber incident.
NCSC defines a cyber incident as a breach of security policy that compromises the integrity of the system or gives unauthorized access to a third party.
There are many cybersecurity threats capable of creating a breach. Here are just some, that small and medium businesses have to grapple with:
- Malware: malicious programs such as trojans, info stealers, and ransomware
- Phishing: social engineering attempts to trick employes into revealing login credentials or installing destructive malware
- Password Hacking: gaining access by cracking weak passwords
- Insider Threats: confidential information accidentally or purposefully leaked by employes
Why do you need a cyber incident response plan?
Here are 3 reasons why a cybersecurity incident response plan is crucial for effective defense:
1. It prepares you to fend off cyber threats
And reduces the amount of damages incurred during incidents. Without a plan, security teams are forced to wing it every time they deal with a threat. This can leave them scumbling, not knowing where to look and what to search for. The result? Higher recovery costs.
2. You may be lawfully required to have a cyber response plan
Depending on the jurisdiction and the type of business, creating a response plan might be a requirement for you, not a choice. This is especially true for companies that deal with finance or personal data. For example, the California Consumer Privacy Act (CCPA) mandates that companies have a cyber incident response strategy. It’s also a must for the ISO 27001 certification.
3. It makes your defense more resilient in the long run
With a cyber incident response plan, you will implement a policy of constant evaluation and reiteration. You will learn how to collect data during an incident, then, use the findings to harden your defenses. All of this will help avoid similar incidents going forward.
What is a cyber incident response plan?
An incident response plan is a document that provides a systematic approach to handling different cyber threats.
At the very least, the plan should outline how to prepare for, detect, contain and eradicate the threat. Then, restore the system to its pre-attack state while also hardening it. Finally, correct the errors that made the incident possible.
But a great plan goes beyond just dealing with malware. It should also consider your communication, PR, legal repercussions, and even cybersecurity insurance.
- How do you notify users that their data is not safe?
- Are you legally protected in case of a leak?
- Will you control potential public fallout yourself or with a PR partner?
- Who in your team is responsible for communication with the users?
These are the types of questions you want to have prepared answers for.
6 phases of an incident response process
Incident response plans are structured in such a way as to provide directions chronologically, preventive actions at the top of the document and post-incident recovery towards the end.
Depending on a school of thought, response plans will have 4 to 6 phases. (Sometimes containment, eradication, and recovery are merged into one large block).
Here’s a quick summary of what to consider as you make out the plan for each:
1. Preparation
This phase is all about getting ready: naming people in charge, assigning battle stations, preparing a war room (yes, that’s an actual thing that people do), and listing attack vectors and attack handling procedures. This way if a breach does happen, your team will know exactly how to act and will stay organized.
2. Identification
Detecting that you’ve been hit is probably the most difficult part of incident response. But you can increase the chances of finding attack precursors and early indicators by establishing and following logging and monitoring policies. Also, you can use ANY.RUN online malware sandbox to view processes created by certain malware and cross-reference them with the activity in your own system.
3. Containment
The containment phase is about quarantining the infection: shutting down a system, revoking account permissions or disabling certain functions are some of the available strategies for isolating malware. Keep in mind that your tactics and instruments will change based on what type of attack you’re experiencing.
4. Eradication
The goal of the eradication phase is to stop the attack completely in its tracks. Some of the instruments used at this stage overlap with the containment phase, and again, your options will change depending on the nature of the incident. For example, in a phishing attack you can suspend a compromised account to disarm the attacker. And a malware infection can be eradicated by restoring the system from a clean snapshot.
5. Recovery
During the recovery stage, your goal is to get the business process up and running again while also hardening the system. For instance, restore affected components from a trusted backup and patch out any vulnerabilities that were exploited in the incident.
6. Lessons Learned
The final phase of the plan deals with reiterating on your security practices, armed with the knowledge obtained during the incident. Evaluate the errors that led to the attack, make corrections, and add new policies to the incident response plan.
Going in-depth
And if you really want to sink your teeth into all the details of creating a response plan, reference the NIST Computer Security Incident Handling Guide. Just remember that not every organization needs to go this in-depth. It all depends on the type and size of your business.
Useful tools in the incident response jump kit
Here, we’ve listed some tools that you’ll want to keep handy, as well as useful practices for different stages of the response process.
| Preparation | Identification | Containment, eradication, recovery |
|---|---|---|
Emergency phonebook So you know who to contact in an incident, both inside the team and out. | ANY.RUN to analyze suspicious files and links, perform digital forensics | System snapshots To roll back the system to a clean state using a trusted backup |
| Log Retention Policy Determines how long the data is kept to help security specialists perform analysis | Incident Databases Resources such as the ANY.RUN trends tracker help keep track of and study existing threats | Incident Prioritization Table A formal classification of incident difficulty that helps choose a containment approach: immediate or strategic |
Normal behavior threshold Establish a guideline for what is normal system behavior to detect anomalies | Event correlation This is a practice of comparing logs to find discrepancies | File backups Backups of the code stored on a dedicated server can be used to replace compromised files with clean ones |
Using a sandbox to identify threats
Identifying malware in an infected machine is pretty much like looking for a needle in a haystack.
But if you know exactly where to search, suddenly you’re scanning that same haystack with a metal detector, and pulling the needle out with a magnet.
Malicious programs leave behind bread crumbs in the form of files, processes, and network activity — these are Indications of Compromise or IOCs, and they are unique to each malware family. There are organizations that record and catalog such traces in public databases. For example, ATT&CK MATRIX.
As long as you know what activity hints at the presence of malware, you can check if such activity took place in a system. This can be useful, for example, to quickly identify which clients have been infected in an organization.
This is where sandboxes come into place. Using an isolated virtual environment, you can force the malware to execute and collect as many bread crumbs as you need.
For example, in this FormBook task, we can see how ANY.RUN generated a cyber security incident report which revealed all processes created by the trojan.
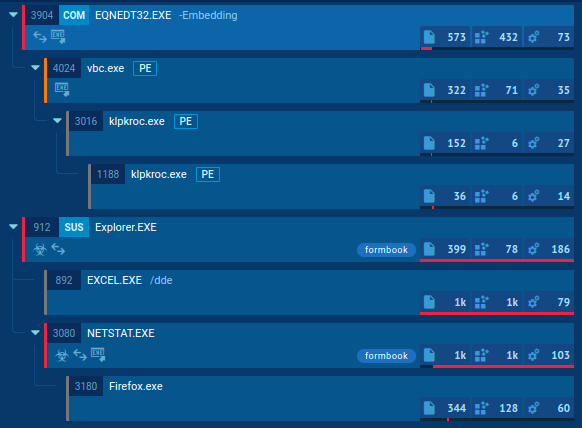
We can see them even more clearly in the process graph — an informative ANY.RUN feature.
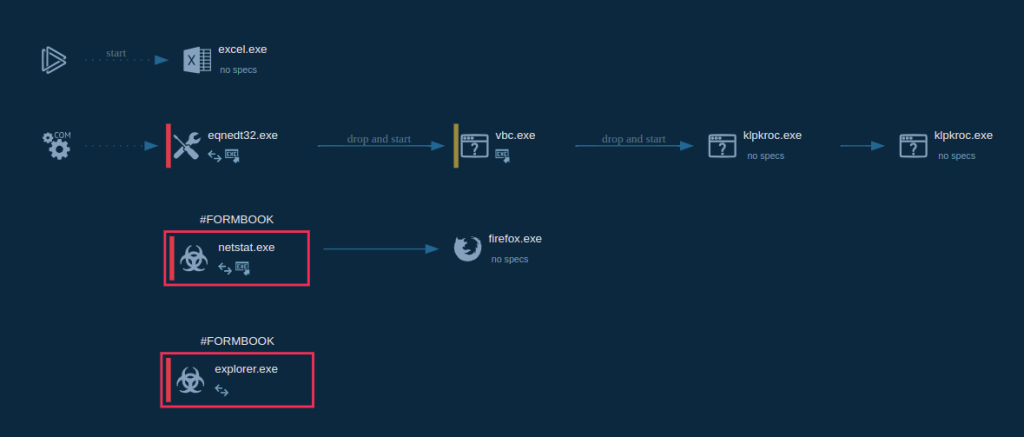
This overview gives us a broad idea how to identify this sample in hosts, where it could potentially evade detection and persist. We can do this by running triage sessions over our assets, for instance, using PowerShell.
Conclusion
Cyber incident response is a broad topic — every company is a little bit different and requires a unique approach to security. There are countless threats, attack vectors and handling strategies to consider, and they change based on the type of business and industry.
Perhaps, this is why so many organizations avoid creating cyber incident response plans. And it really does seem like a daunting task. But don’t let this stop you — even a basic strategy is better than no strategy at all. And a lot of smaller businesses can keep it basic.
Just remember the generation old wisdom — better safe, than sorry.
Questions and answers (Q&A)
- What is a cyber incident?
A cyber incident is a breach of security policy that compromises a system’s integrity or gives a perpetrator an unauthorized access to a system.
- What is a cyber incident response plan?
A cyber incident response plan is a document that outlines a company’s incident handling policies in 6 phases: Preparation, Identification, Containment, Eradication, Recovery and Lessons Learned.
- Why do I need a cyber incident response plan?
A cyber incident response plan helps security teams respond to breaches in an organized and thorough way, ensuring complete recovery from an incident.
- What is the main reason for an organization to develop an incident response plan?
A cyber incident response plan helps organizations manage threats in an effective manner, and leads to lower recovery costs. This is important because a successful cyberattack can induce hundreds of thousands of dollars worth of damages.
- What tools can help me respond to incidents effectively?
There are many digital forensics tools that are useful during the identification and containment stages. For example, ANY.RUN online malware sandbox can help collect Indicators of Compromise (IOCs) quickly and efficiently.






0 comments