Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


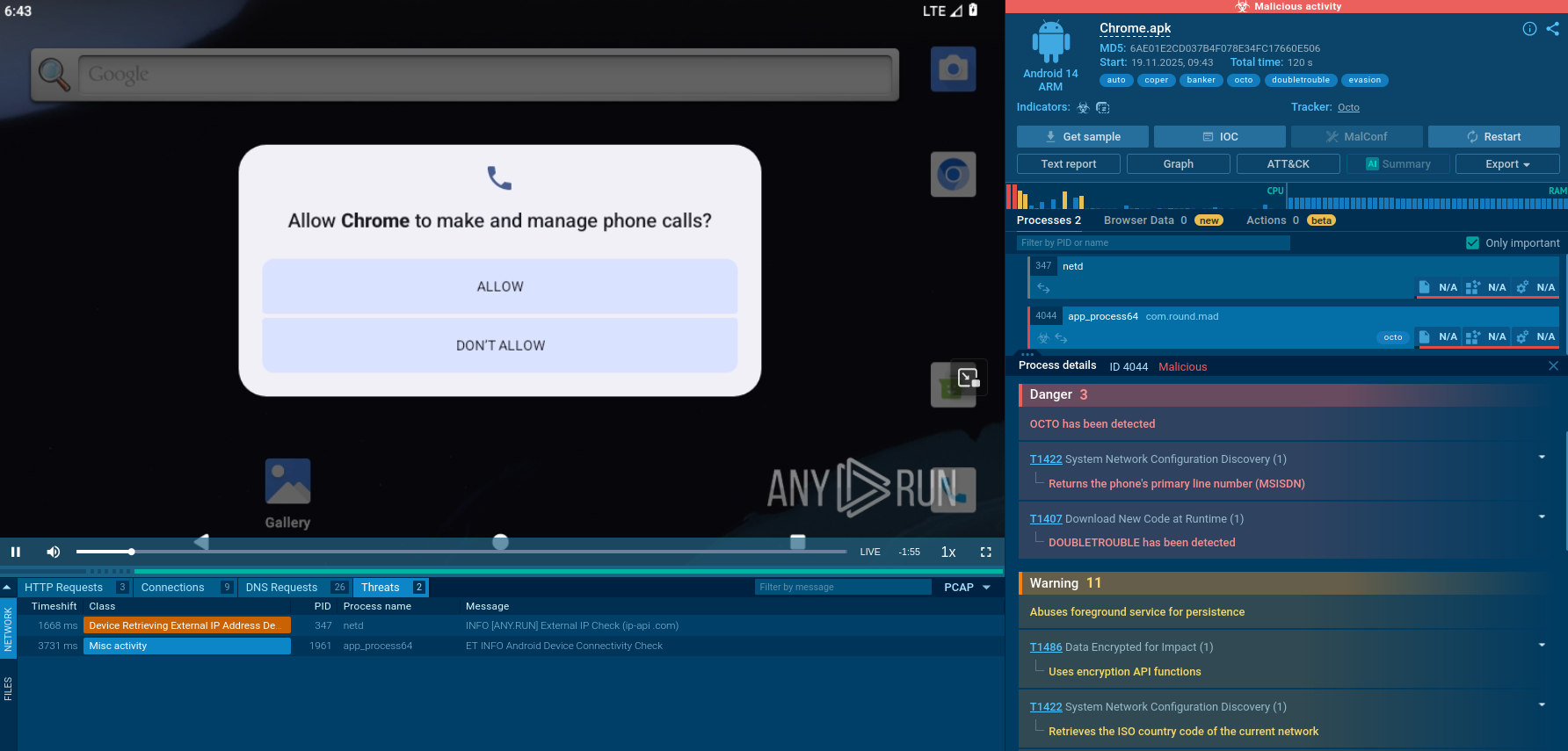
DEVMAN is a fast-evolving malware family targeting Windows environments with a mix of credential theft, remote control capabilities, and persistence techniques typical of modern crimeware. Initially observed in early 2025, DEVMAN quickly became a favorite tool among cybercriminal groups thanks to its stealth, modular structure, and ability to bypass traditional AV solutions.
|
Ransomware
Type
:
|
Unknown
Origin
:
|
|
1 April, 2025
First seen
:
|
5 February, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 April, 2025
First seen
:
|
5 February, 2026
Last seen
:
|

 820
820
 0
0

 491
491
 0
0

 2756
2756
 0
0
 DEVMAN sandbox analyses with IOCs and TTPs
DEVMAN sandbox analyses with IOCs and TTPs
 DEVMAN malware detonated in ANY.RUN’s Sandbox
DEVMAN malware detonated in ANY.RUN’s Sandbox
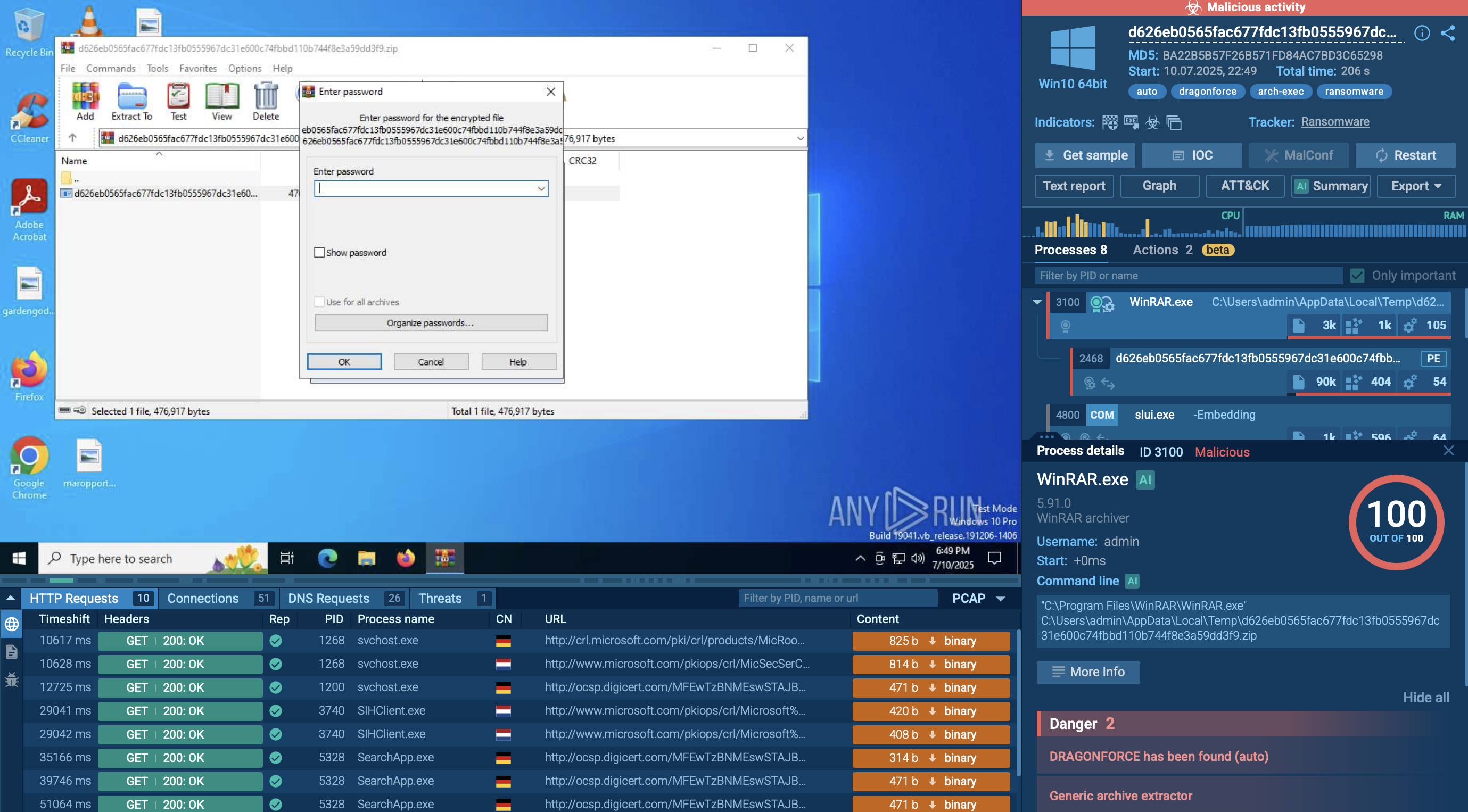
DEVMAN ransomware emerged in early 2025 as a sophisticated threat that shares its genetic code with two notorious predecessors: DragonForce and Conti. This ransomware uses the .devman file extension for encrypted files and evolved from DragonForce code, representing a new chapter in the ongoing evolution of ransomware-as-a-service operations. It has proven to be a persistent and evolving threat with over 120 documented victims across multiple continents.
The malware implements three distinct encryption modes: full encryption for comprehensive data corruption, header-only encryption for speed optimization, and custom encryption for targeted scenarios. This flexibility allows attackers to balance speed against thoroughness depending on their objectives.
The ransomware operates almost entirely offline, with no external command-and-control communication observed during analysis. Instead, it relies on local SMB probing to facilitate lateral movement within compromised networks. DEVMAN creates a temporary session under the registry key HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 to bypass file locks, a technique inherited from its Conti lineage that enables encryption of active user session files.
One of the most distinctive characteristics is its use of a hardcoded mutex named "hsfjuukjzloqu28oajh727190" to prevent multiple instances from running simultaneously. This anti-reentry mechanism is standard among Conti-derived ransomware families and provides a reliable indicator of compromise for defenders.
The ransomware also contains notable flaws that suggest rushed development or incomplete testing. Due to builder misconfiguration, the malware often encrypts its own ransom notes, making them inaccessible to victims. Additionally, the wallpaper-changing function works on Windows 10 but fails on Windows 11, indicating compatibility issues or incomplete adaptation to newer operating systems.
DEVMAN primarily targets mid-to-large enterprises in non-Western markets, with a heavy focus on Asia (e.g., Thailand, Indonesia) and Africa (e.g., healthcare and government sectors), though it has expanded to Europe, Latin America, and North America.
The group favors critical infrastructure, including transportation, social security funds, and media outlets, as well as healthcare providers (excluding pediatric cases to avoid backlash).
Early victims included government agencies and funds with massive data hauls (e.g., 2.5 TB exfiltrated from a national social security entity via compromised RDP). By May 2025, DevMan claimed 13 victims in a single month, rivaling top-tier groups, and has since amassed nearly 120 confirmed cases. Sectors hit hardest include manufacturing, finance, and public services, with ransoms scaling from $50,000 for smaller entities to over $2.5 million for high-revenue targets, often auctioned if unpaid.
The group functions as an affiliate across multiple Ransomware-as-a-Service platforms while also conducting direct attacks with their proprietary toolset.
Primary infection vectors include compromised Remote Desktop Protocol (RDP) connections. The group gains initial access via VPN and RDP connections, often using stolen credentials or password spraying attacks.
Phishing campaigns serve as another significant attack vector. Exploitation of edge-facing services represents a third major vector. The group exploits VPN gateways and remote management interfaces through vulnerabilities in public-facing applications.
DEVMAN implements faster lateral movement via Group Policy Object deployment from compromised domain controllers. This allows rapid propagation across enterprise environments once administrative credentials are obtained.
DEVMAN’s evolution includes the use of various tools for reconnaissance and privilege escalation. BloodHound is deployed for Active Directory attack path visualization, while SoftPerfect Network Scanner facilitates network reconnaissance. These tools enable sophisticated understanding of the target environment before encryption begins.
The ransomware uses hybrid cryptography combining AES-256 symmetric encryption for speed with RSA-2048 asymmetric encryption for key protection. This combination ensures both rapid file processing and cryptographic security that prevents decryption without the attacker's private key.
The execution flow begins with environment reconnaissance. DEVMAN enumerates all accessible drives and network shares, building a comprehensive target list. The malware specifically probes for SMB shares within local network ranges, attempting to spread laterally to maximize impact across the organization.
Persistence mechanisms leverage the Windows Restart Manager API in a manner characteristic of Conti-derived malware. The ransomware logs metadata for critical files, identifies processes locking those files, and forces their termination or restart to gain encryption access. Registry entries are created under the Restart Manager session key, then rapidly deleted to minimize forensic traces.
Process execution follows a carefully orchestrated sequence. The malware first disables security tools where possible, deletes shadow copies to prevent recovery, and empties recycle bins. Only then does encryption begin, with the ransomware processing files according to the selected mode while avoiding system-critical extensions that would render the machine unbootable.
The ransom note generation process contains a critical flaw. Due to a builder flaw, the ransomware encrypts its own ransom note files, renaming them deterministically to e47qfsnz2trbkhnt.devman. This means victims may not receive payment instructions, effectively severing the communication channel needed for ransom negotiation.
Network activity is deliberately minimal. Unlike many modern ransomware variants that maintain constant communication with command servers, DEVMAN operates in an almost completely offline mode. The only network traffic involves SMB scanning for lateral movement opportunities, making network-based detection more challenging.
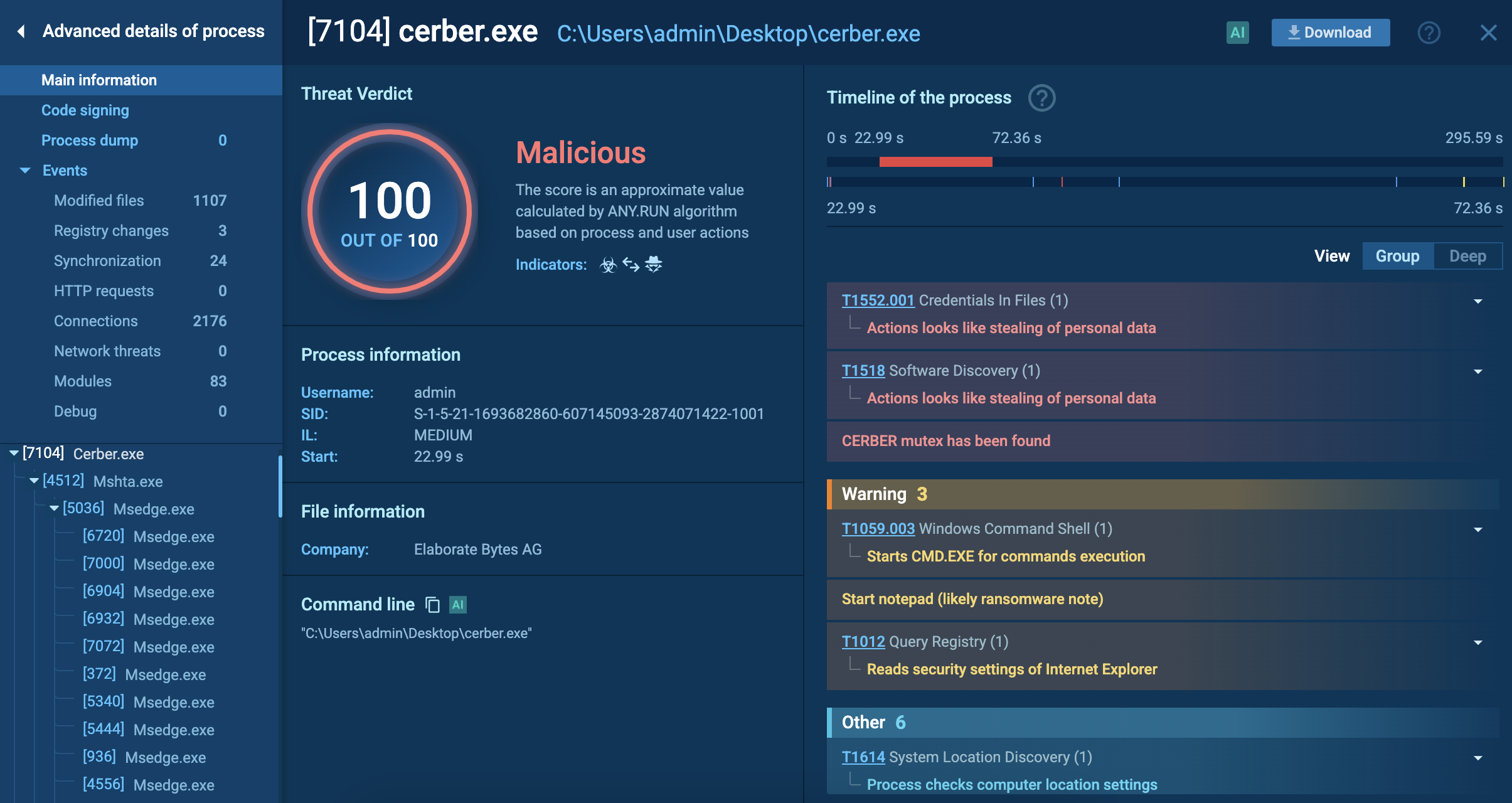
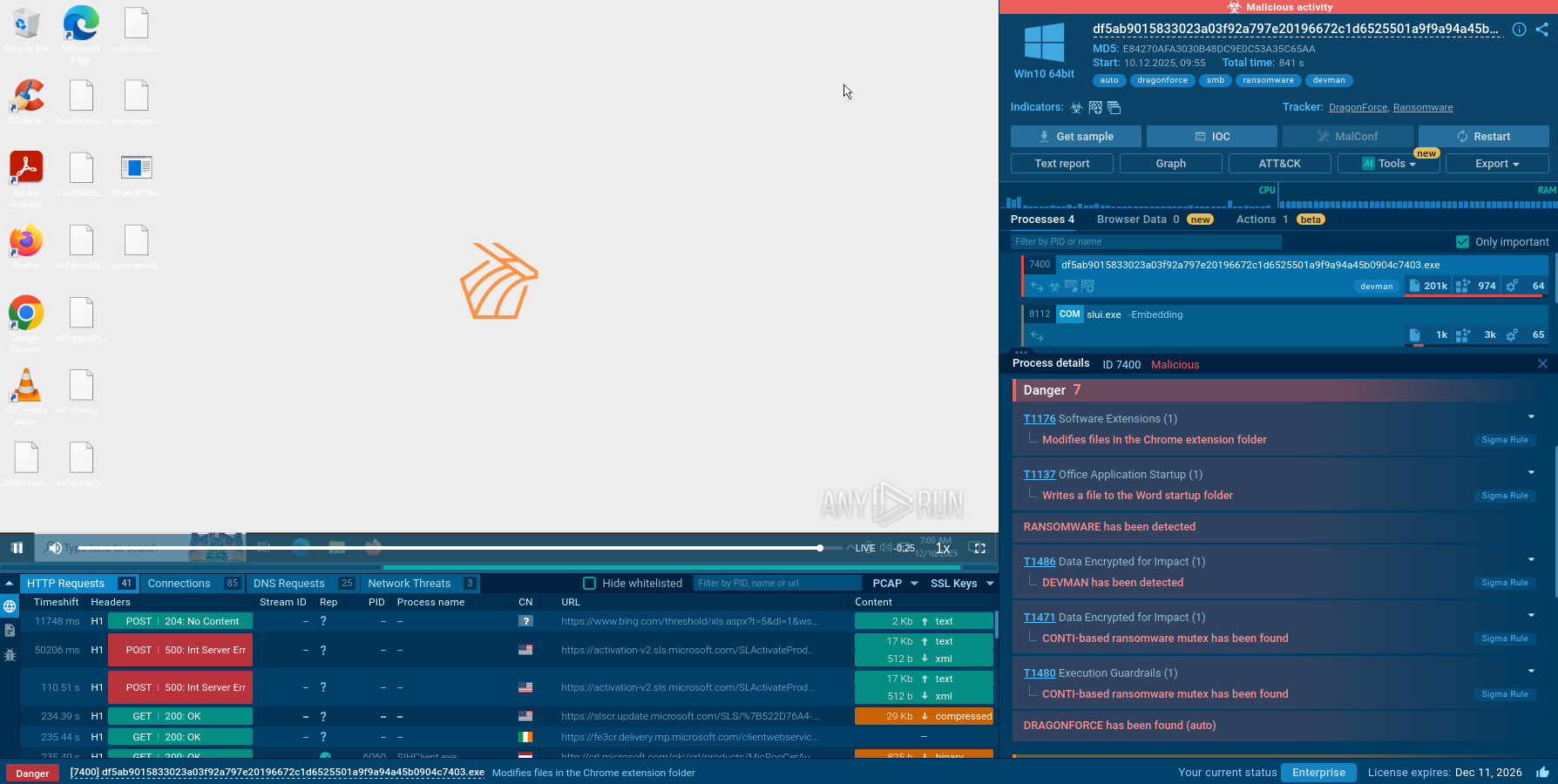
ANY.RUN’s Interactive Sandbox provides isolated, instrumented environments where security researchers and analysts can safely execute suspicious files without risking production systems.
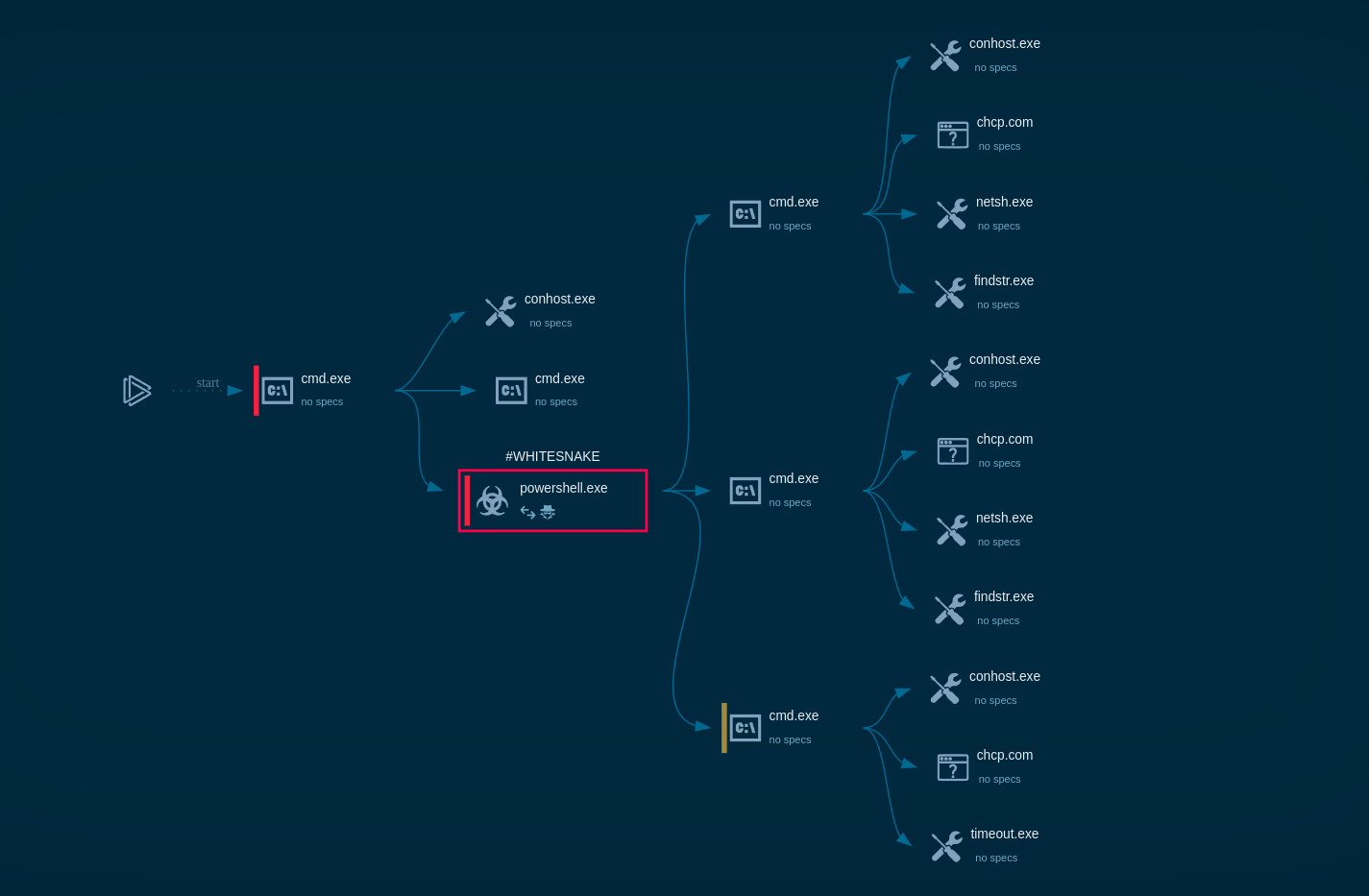
 DEVMAN’s processes and artifacts in the Interactive Sandbox
DEVMAN’s processes and artifacts in the Interactive Sandbox
An analyst can view the ransomware’s process tree mapped to MITRE ATT&CK Matrix, explore connections, files, scripts, registry changes and more.
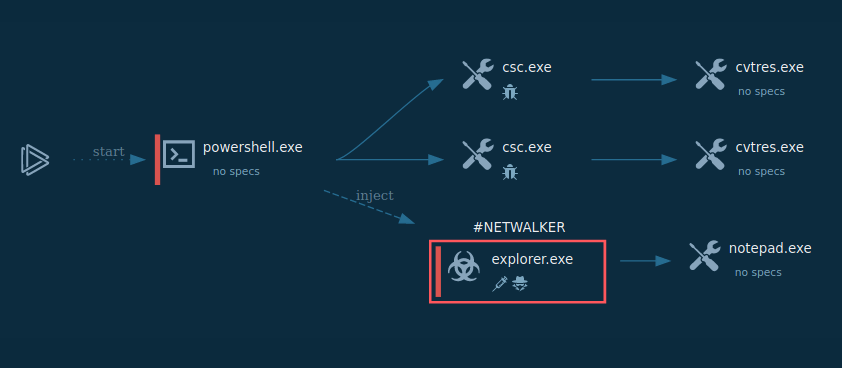
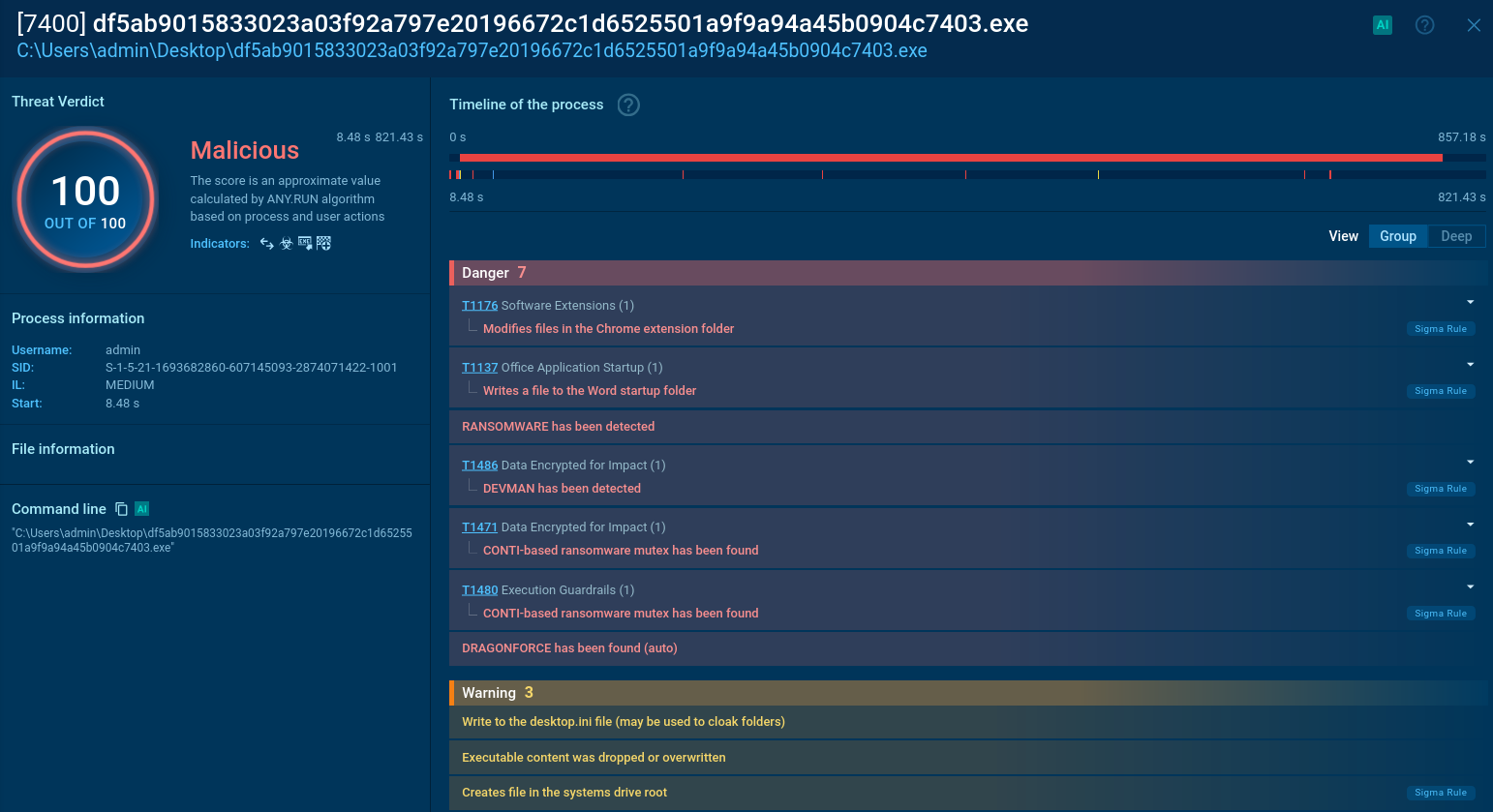 DEVMAN’s processes
DEVMAN’s processes
For example, one can view DEVMAN’s ransom note with a reference to DragonForce:
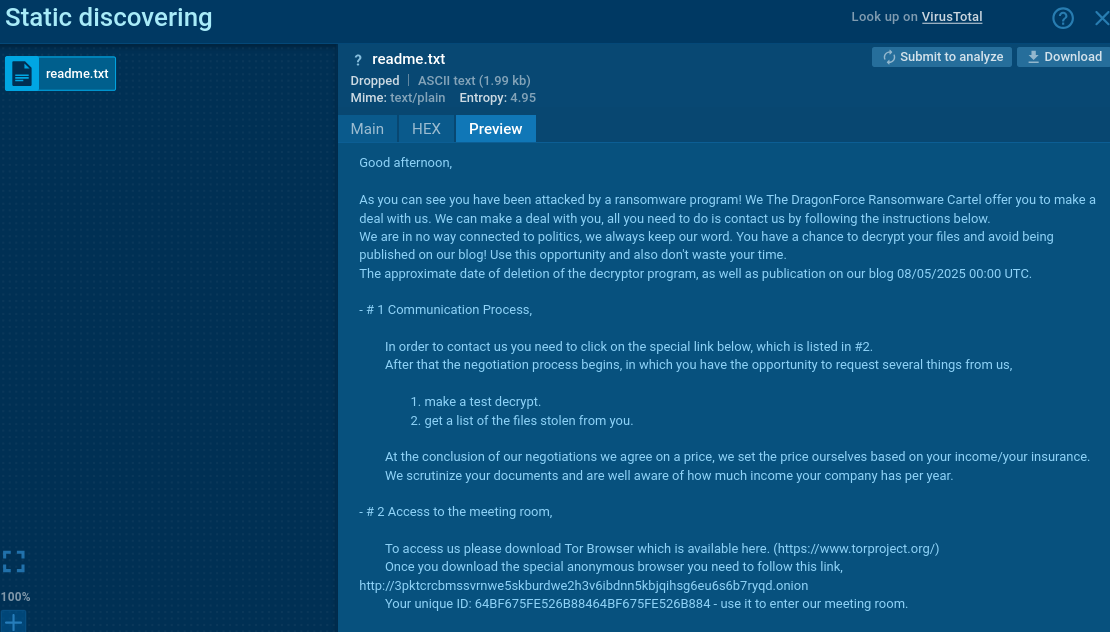 Ransom note with decryption instructions
Ransom note with decryption instructions
Or observe DEVMAN converting filenames via a specific function and adding a .devman extension.
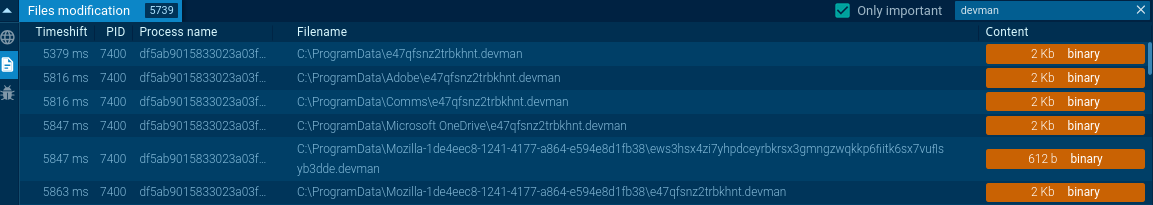 DEVMAN encrypts and renames files
DEVMAN encrypts and renames files
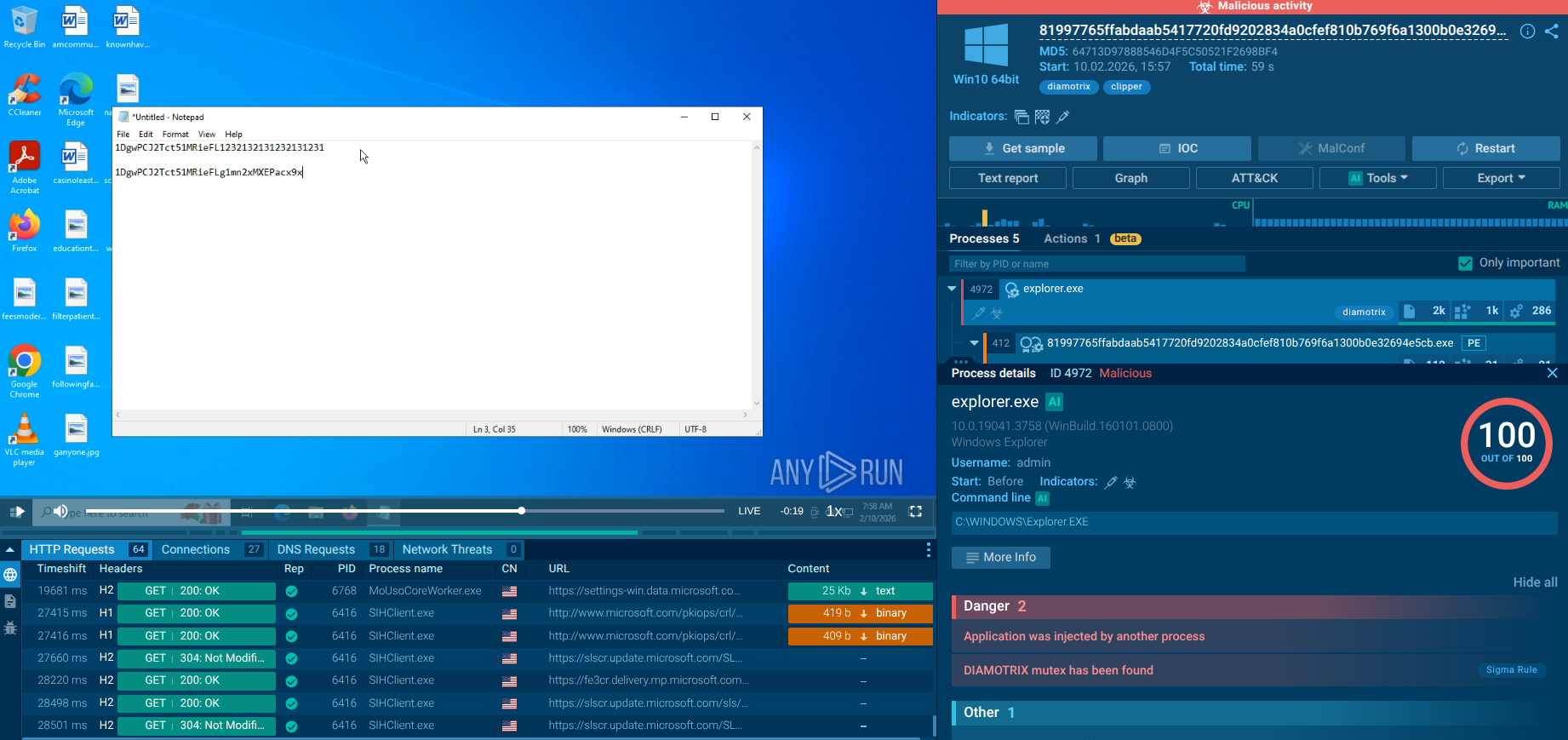
The ransomware scans for SMB shares for lateral movement.
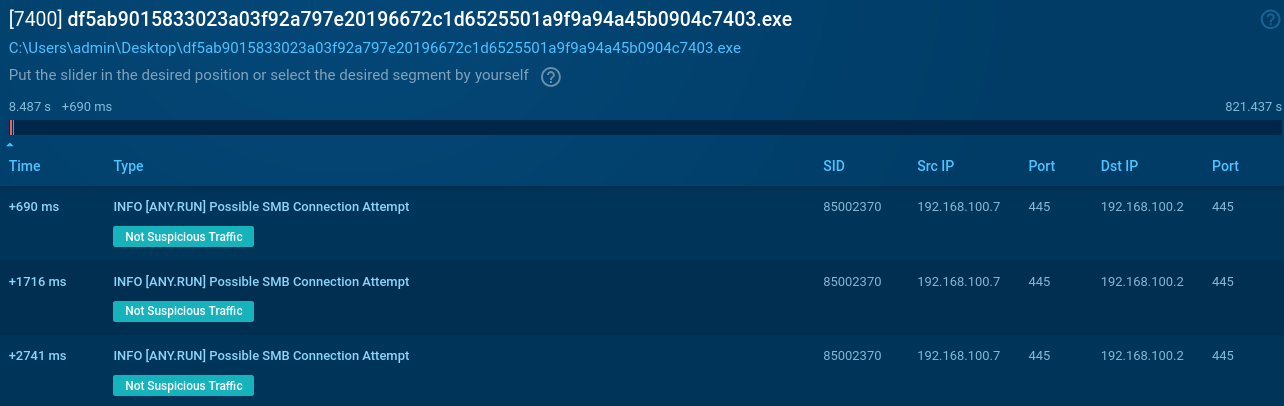 DEVMAN network activity
DEVMAN network activity
DEVMAN’s most impactful strikes highlight its efficiency in high-stakes sectors:
French Transport Authority (April 2025): Initial claim via X (formerly Twitter), with full network encryption disrupting operations; exact ransom undisclosed but marked DEVMAN’s debut as a standalone threat.
Thai Media Outlet (May 2025): Exfiltrated 170 GB using a customized encryptor with ".devman" extension; screenshots showed domain controller access and GPO deployment, with data offered for single-buyer sale post-encryption.
National Social Security Fund (Early 2025): Compromised via RDP, yielding 2.5 TB exfiltration; ransom demand hit $2.5 million, showcasing DevMan's scale against critical public services.
Abdulhadi Hospital and Easter Seals (December 2025): Recent healthcare hits with 246 GB and 236 GB stolen, respectively; ransoms of $350k and $90k, emphasizing permissible targeting of adult medical data.
By querying suspicious files or network indicators against a vast database of malware samples analyzed in the Sandbox by over 15K SOCs worldwide, security teams can quickly determine whether observed activity relates to known DEVMAN campaigns.
You can also use Threat Intelligence Lookup to find more live DEVMAN samples and indicators by searching a signature IOC like the mutex this ransomware usually features:
syncObjectName:"hsfjuukjzloqu28oajh727190" and filePath:"devman"
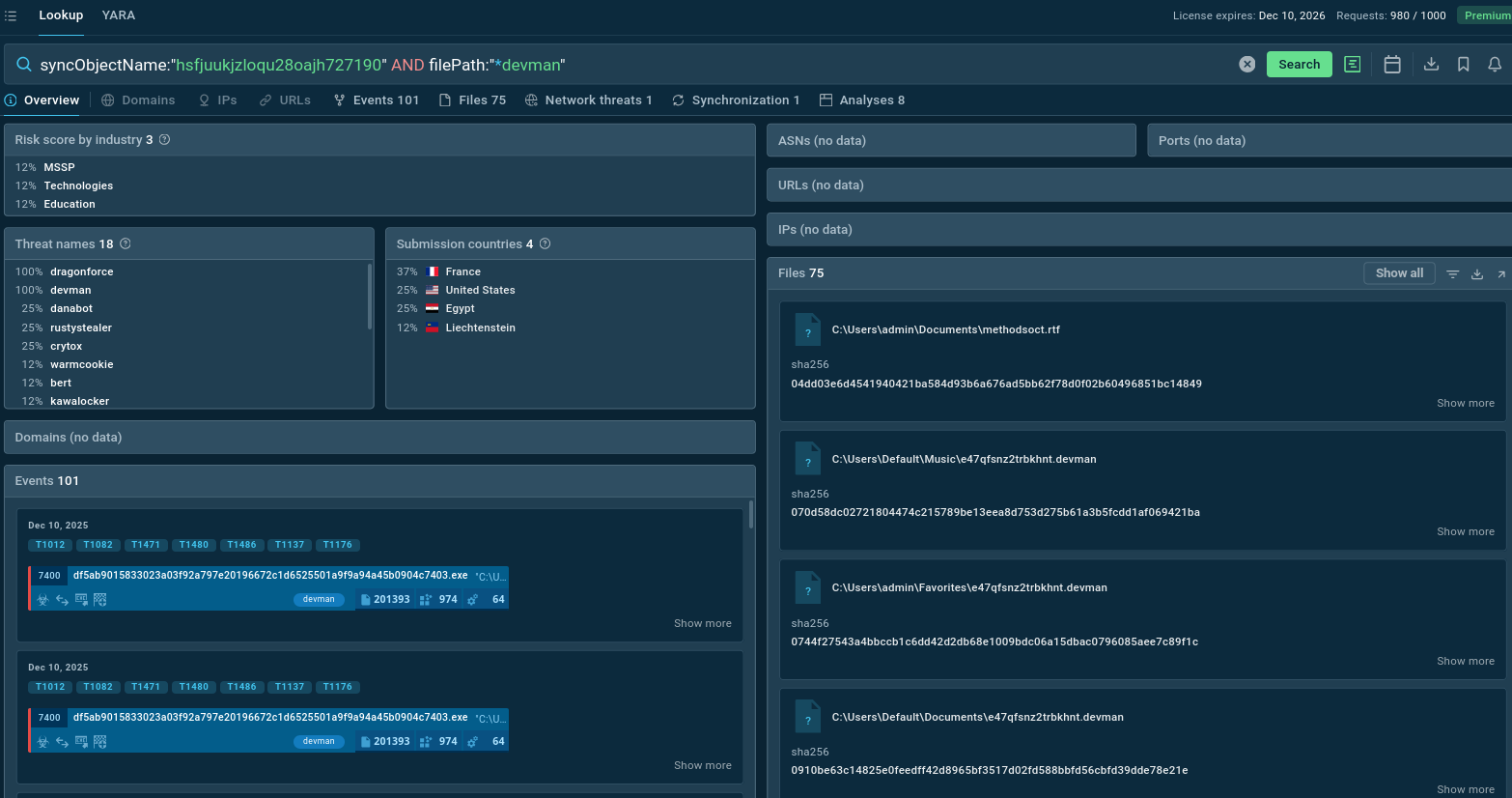 DEVMAN mutex in TI Lookup
DEVMAN mutex in TI Lookup
DEVMAN exemplifies the ransomware ecosystem's resilience, recycling Conti-era code into a profitable RaaS machine that preys on global enterprises with surgical precision. From its affiliate roots to independent empire-building, it underscores the need for vigilant, layered defenses amid code-sharing cartels. As attacks proliferate (now over 120 victims), organizations must invest in TI, sandboxes, and resilience to outpace these digital extortionists, turning potential catastrophes into manageable risk.
Trial TI Lookup to start gathering actionable threat intelligence on emerging malware: just sign up to ANY.RUN.