Big news: Windows 10 is now available to ALL our users, including those on the Community plan. Curious about what this means for you? Keep reading to find out!
Why we did this
We want to provide an up-to-date operating system for all users to analyze current threats. Previously, Community plan users were limited to a basic Windows 7 32-bit VM. This led to lower detection rates for 64-bit systems than we’d like. By offering Windows 10 64-bit to everyone, we’re aiming to improve overall threat detection and analysis capabilities.
By using Windows 10 for your analysis, you’ll be able to:
- Analyze newer threats that target the most popular systems
- Catch more potential issues (detection rates are higher on Windows 10)
- Get more accurate results in your reports
- Emulate 64-bit malware
How this helps everyone
We believe everyone should have good security analysis tools, whether you’re paying or using our free plan. This update is our way of making that happen.
But this update also benefits our entire community. As more users use Windows 10, our sandbox environment will become more effective at detecting a wider range of threats.
A practical Windows 10 example
Certain modern malware families won’t run on older systems. For example, the Latrodectus malware won’t complete its full execution chain on Windows 7, but successfully executes and reveals itself on Windows 10.
Why Windows 10 64 bits
We’ve decided to make the 64-bit architecture available as a more modern option. There are examples of malware that won’t run on 32-bit systems, here are a few examples that only work on 64-bit operating systems.
How to Access Windows 10 for analysis
When creating a new task as a Community Plan user, you’ll now see that Windows 10 64 bit is no longer grayed out in the list of available VMs:
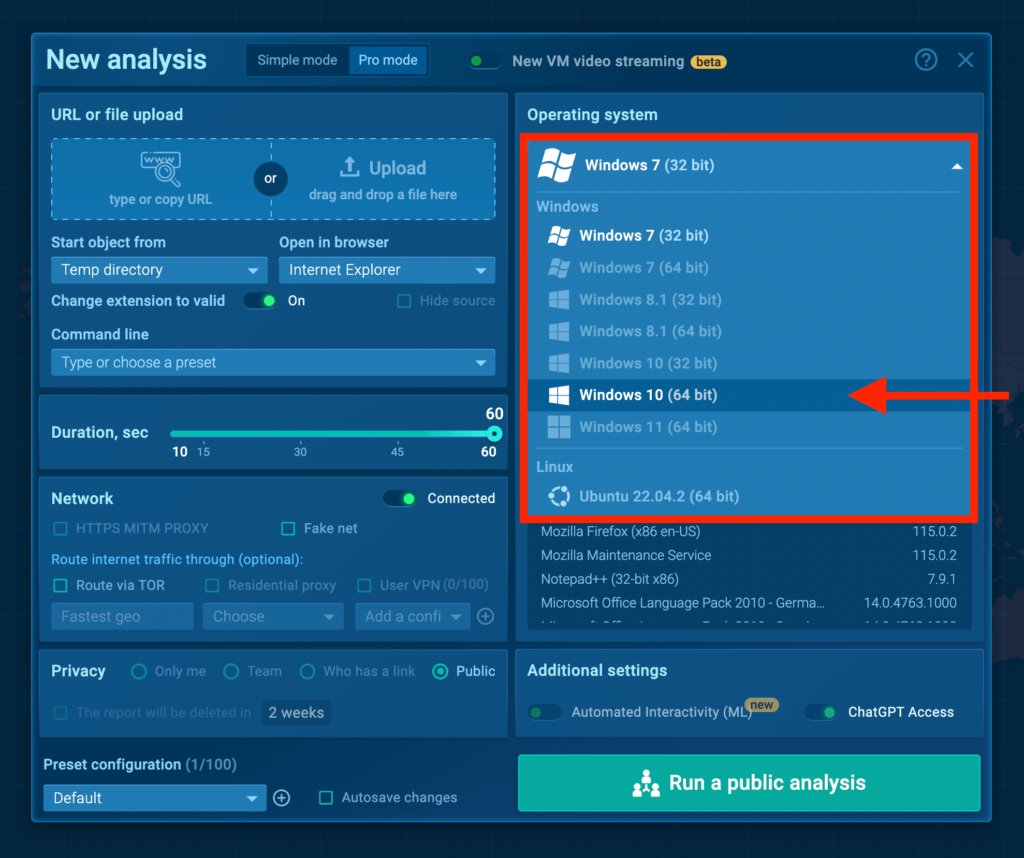
Just click on it in the drop-down menu and your analysis will be performed in a Windows 10 VM.
About ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Advantages of ANY.RUN
ANY.RUN helps you analyze threats faster while improving detection rates. The platform detects common malware families with YARA and Suricata rules and identifies malware behavior with signatures when detection by family is not possible.
With ANY.RUN you can:
- Detect malware in under 40s.
- Interact with samples in real time.
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior.
- Collaborate with your team
- Scale as you need.
Try the full power of ANY.RUN for free







0 comments