Cyber Threat Intelligence is a powerful tool that helps organizations make sense of the vast amounts of data generated by their cybersecurity systems.
By analyzing this data, cyber threat intelligence provides insights into the specific details of an organization’s security posture. It enables security teams to identify risks, anticipate potential threats, and assess the effectiveness of their remediation methods.
The Three Levels of Cyber Threat Intelligence
To effectively combat cyber threats, it’s essential to understand the three levels of CTI: tactical, operational, and strategic.
1. Tactical Intelligence (real-time): focuses on specific threats as they occur. It operates in real-time, collecting data from ongoing security incidents. This intelligence directly informs the actions of an organization’s security tools, such as SIEM, TIP, firewalls, and EDR systems.
2. Operational Intelligence (proactive): takes a step back to assess potential threats and gauge the overall risk to an organization. It provides information about the origins of potential attacks and the likelihood of their occurrence. This intelligence helps shape remediation policies and guides the configuration of security tools.
3. Strategic Intelligence (far outlook): offers a high-level overview of an organization’s threat landscape, considering geographic, political, and business trends. It presents broad patterns and identifies areas where new security tools or strategies may be required.
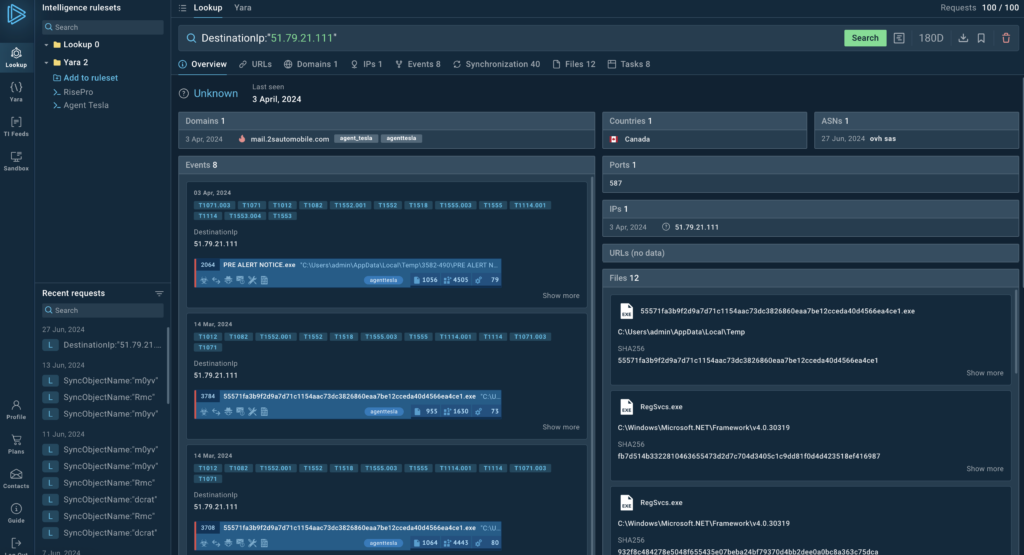
For example, ANY.RUN’s TI Lookup is a CTI tool that helps security teams find many different types of ICOs associated with a single search parameter, in this case an IP. It’s an example of tactical intelligence.
Let’s explore each of the 3 CTI levels in more detail.
Tactical intelligence
Tactical CTI identifies specific, real-time threats, enabling swift and appropriate responses. It is designed for security professionals responsible for daily threat identification and remediation to:
- Proactively resolve ongoing cyber events
- Inform users about TTPs used by malicious actors
- Predict attack evolution and guide remediation efforts
Tactical CTI focuses on specific, identified threats rather than abstract, potential risks.
Types of tactical TI data:
- Malware signatures
- IP and URL blacklists
- Traffic patterns
- File hashes
- System events
Operational intelligence
Operational CTI identifies potential threats and assesses their likelihood of affecting an organization. It is designed for security managers and network defense teams who need technical details about potential attacks while understanding broader trends.
Operational CTI is used to:
- Configure policies and tailor security solutions to block likely attacks
- Provide actionable insights that directly impact cybersecurity setup
- Identify threats before they become attacks
Operational CTI is updated frequently (daily or every few days) to ensure the effectiveness of the cybersecurity infrastructure.
Types of Operational CTI Data:
- Command and control channels
- Malware implementation details
- Malicious file names and traffic
- Suspicious IP addresses and domains
- Attack tools and URLs
Strategic intelligence
Strategic CTI identifies the actors targeting an organization and their motivations. It is designed for high-level decision-makers, such as executive boards and C-level executives, responsible for the overall direction of the organization.
Strategic intelligence helps to:
- Plan cybersecurity budgets and allocate resources effectively
- Understand broad trends, risk areas, and the repercussions of cybersecurity threats
- Decide whether to invest in further security based on emerging threats within the industry or region
Types of strategic CTI data:
- New attack types and trends
- Economic and business impact of attacks and compromise
- Regulatory and compliance legislation
- Organizational and industry-wide vulnerabilities
A fourth level — technical intelligence
In addition to the three levels of TI we’ve covered above, there is a fourth level called Technical Intelligence. It specializes in the most low-level, machine-readable technical data, such as IOCs delivered via threat intelligence feeds.
TI feeds are essentially streaming services for indicators that can be fed directly into an organization’s security tools to automatically detect and respond to threats.
About ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
With TI Lookup you can:
- Search across a large database the latest malware and phishing threat data
- Refine your search using over 40 parameters and their combinations
- Get results in seconds, each with a corresponding sandbox session
- Leverage YARA Search with a built-in rule editor
- Integrate with your security infrastructure using API








0 comments