Editor’s note: The current article was originally published on August 16, 2022, and updated on October 21, 2024.
Malware analysis is a challenge as it is. But after your hard work on cracking a new sample, it is important to present all your results to the company and colleagues. And today, we will talk about how to write a malware analysis report in one click.
How to write a malware analysis report?
To write a typical malware analysis report, you should cover the following points:
- Summary. Provide the highlights of your research with the malicious program’s name, origin, and main characteristics.
- General information. Include malware type, file’s name, size, and current antivirus detection capabilities. Don’t forget about hashes: MD5, SHA1, SHA256, and SSDEEP. And if a sample has different family names, it’s worth mentioning them, too.
- Characteristics. Write how the sample infects a system, self-preserves, distributes, communicates with servers, collects data, etc.
- Dependencies. Note malware functionality with the required OS version, software set, executables and initialization files, DLLs, list of URLs, and scripts.
- Behavior activities. Give a review of the behavior activities like what executable files malware drops, if it checks the language, runs injected code in another process, or changes any settings.
- Static information. Code analysis results, headers information.
- Additional data. Attach screenshots, logs, string lines excerpts, etc.
- IOCs. Show indicators of compromise that are necessary for successful detection and future prevention.
Get an automated malware analysis report with ANY.RUN
It’s essential to save and share your reports for further cybersecurity strategy and investigation. And ANY.RUN sandbox allows you to do it effortlessly and with just one click.
You can download text reports with detailed information, get PCAP and SSL keys, check request/response content, copy malware config information from the memory dump, use the process graph and MITRE ATT&CK matrix. Besides that, you can export data in JSON format.
We took the RedLine malware sample to show all report examples.
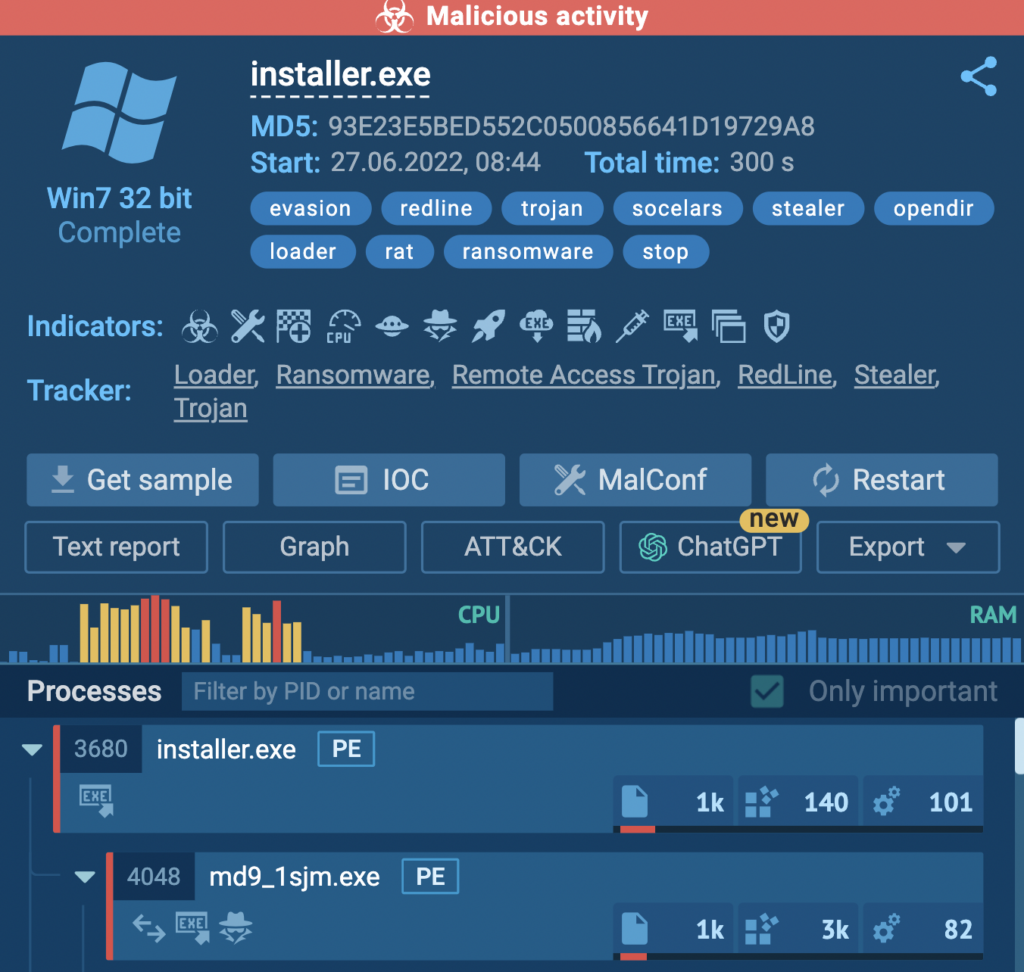
1. Text reports
Our HTML report is a one-click option to get all data about a sample. It’s a ready-made solution, so you don’t need to write a malware report by yourself. Information is displayed conveniently, so you can easily find whatever you need.
You can also adjust the document online, share and print it. Also, get the report via API.
The text report includes all data from the task:
- created processes
- events and files in the registry
- information about network activity
- IOCs
- screenshots
- process behavior graph
Depending on your goal, you can customize an HTML report and choose what sections to include.
2. JSON reports
Download a summary of all task information in JSON format. You can parse the maximum information with this file and analyze precisely the data you need. Then include it in the final report to show all malware footprints.
3. STIX reports
ANY.RUN lets you export collected threat data in the Structured Threat Information eXpression (STIX) format. It is a standardized language used to transfer cyber threat intelligence in a consistent and machine-readable format.
The provided report contains a variety of data related to the threat analysis, including the link to the sandbox session, hashes, network traffic details, file system modifications, TTPs, and more.
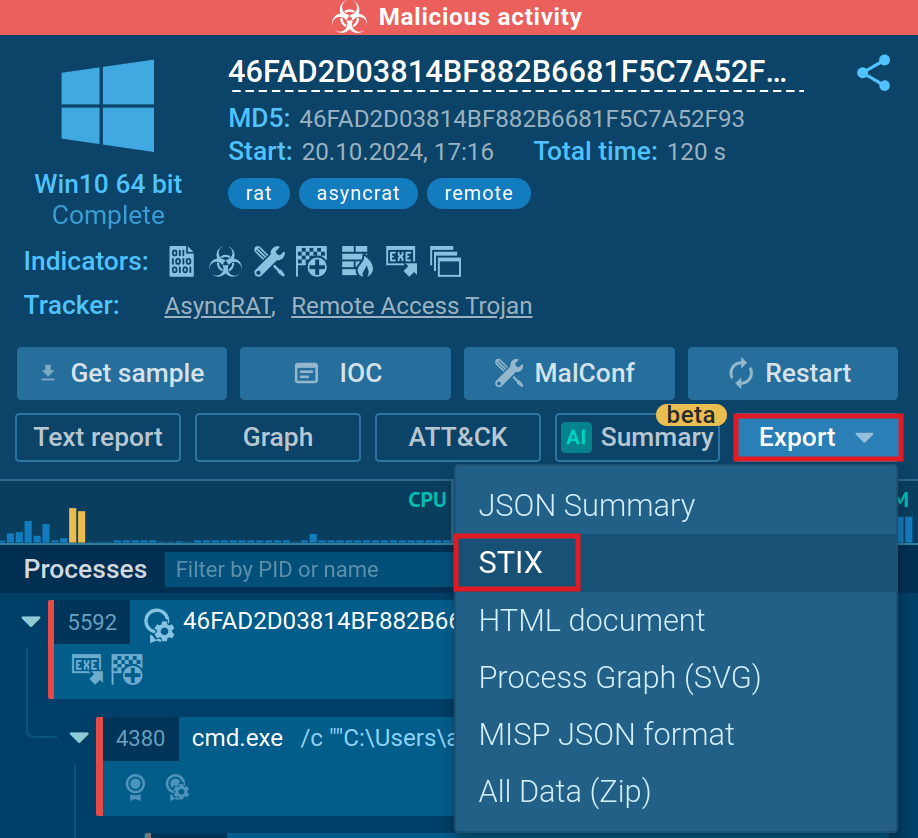
To export data in STIX:
- Run your analysis in the ANY.RUN sandbox or open any report from Public submissions.
- Click Export.
- Choose STIX from the list of options.
These reports can be ingested by Security Information and Event Management (SIEM) systems and other automated tools, enabling faster and more efficient threat detection and response.
Using STIX reports, your analysts and incident response teams can share threat data across different platforms in a more convenient way.
4. PCAP and SSL keys
One of ANY.RUN features is to intercept network traffic. SSL Keys and network dump in a PCAP format are available for your report and further analysis. Just download it from the task and include it in your final report.
5. Request/response content
Take a look at the content from HTTP/HTTPS requests and responses. Besides, connection streams are also available. You can also investigate the header’s query. And this data should be highlighted in the report.
6. Malware configuration
ANY.RUN extracts the content of the malicious process’s memory dump, so you can dive into analysis with malware configuration: encrypted strings, IP addresses, ports that communicate with the C2 server, family name, version, mutex, and other data.
7. Process graph
One of the most effective ways to get a summary of malicious execution is to use a process graph of behavior activities. All processes are presented clearly and logically, especially if the process tree is large. The graph gives you a new angle to look at the processes’ relations and maybe discover something new. Also, it helps to point out the conclusion about the program’s behavior quickly.
8. MITRE ATT&CK matrix
Research sample’s tactics and techniques. In ANY.RUN, you can analyze malware functionality with the MITRE ATT&CK matrix.
Check how to get free malware samples and reports from ANY.RUN’s 6 million database. It will help to see other versions of malware samples and provide a more profound investigation for your research.
9. AI reports
AI reports are highly useful when you need a detailed, easy-to-understand perspective on the threat at hand. These reports detail what occurred during the interactive session and highlight traits that may indicate malicious activity, explaining the rationale behind such assessments.
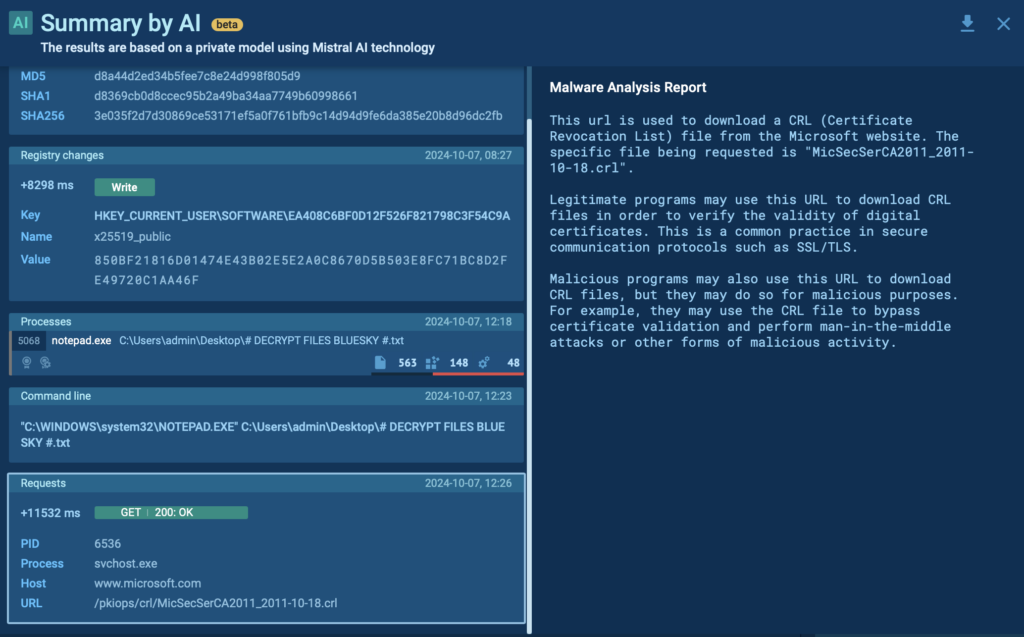
To generate a comprehensive report on any specific event registered during the malware’s execution, click the AI icon next to it.
Wrapping up
Check how to get free malware samples and reports from ANY.RUN’s 6 million database. It will help to see other versions of malware samples and provide a more profound investigation for your research.
About ANY.RUN
ANY.RUN is a cloud malware sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams. Every day, 300,000 professionals use our platform to investigate incidents and streamline threat analysis.
Request a demo today and enjoy 14 days of free access to our Enterprise plan.








0 comments