Today’s malware is complex, and often comes with a wide assortment of evasion methods.
Many families got so good at evading automated sandboxes, that traditional methods often fall short in detecting them. This is where interactive malware sandboxes like ANY.RUN come into play — it offers a powerful tool for cybersecurity professionals to engage directly with potential threats, and study evasive malware.
What is an Interactive Malware Sandbox?
An interactive malware sandbox is a specialized environment designed to safely execute and analyze potentially harmful software.
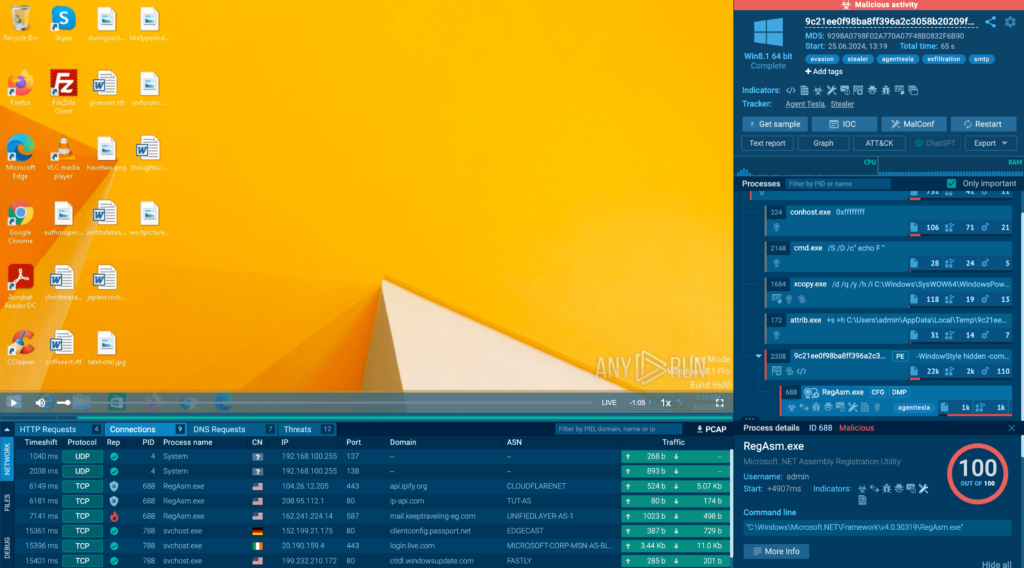
Unlike traditional sandboxes that run malware in a closed, automated system, interactive sandboxes allow users to actively participate in the analysis process.
This hands-on approach enables a deeper exploration of the malware’s behavior, allowing for real-time adjustments and observations.
By interacting directly with the malware, analysts can observe how it responds to different inputs, network conditions, and system configurations. This level of interaction is particularly valuable in identifying sophisticated threats that might evade detection in automated systems.
How Interactive Malware Sandboxes Work?
When a sample is uploaded to the sandbox, the environment is immediately prepared to execute the malware.
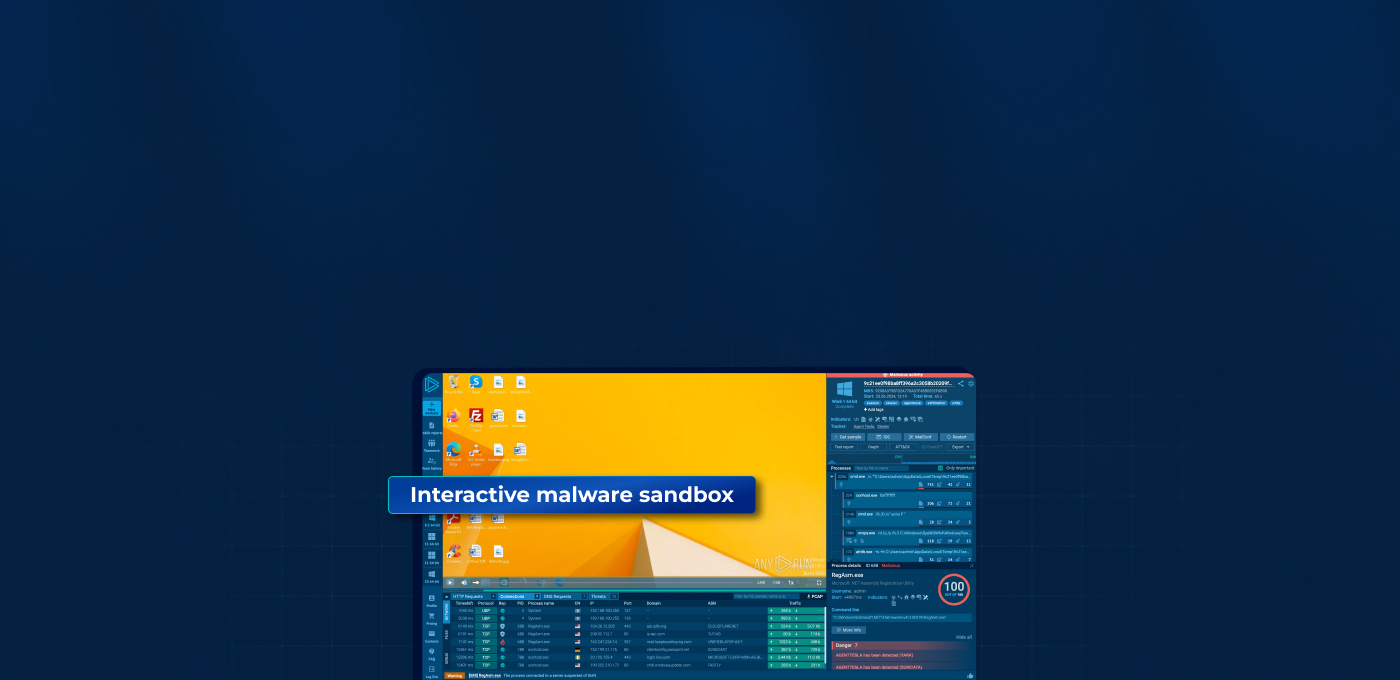
What sets interactive sandboxes apart is the ability for the analyst to step in and guide the process. For instance, if the malware attempts to open a webpage, the analyst can observe the page content, monitor network traffic, and see how the malware interacts with the site.
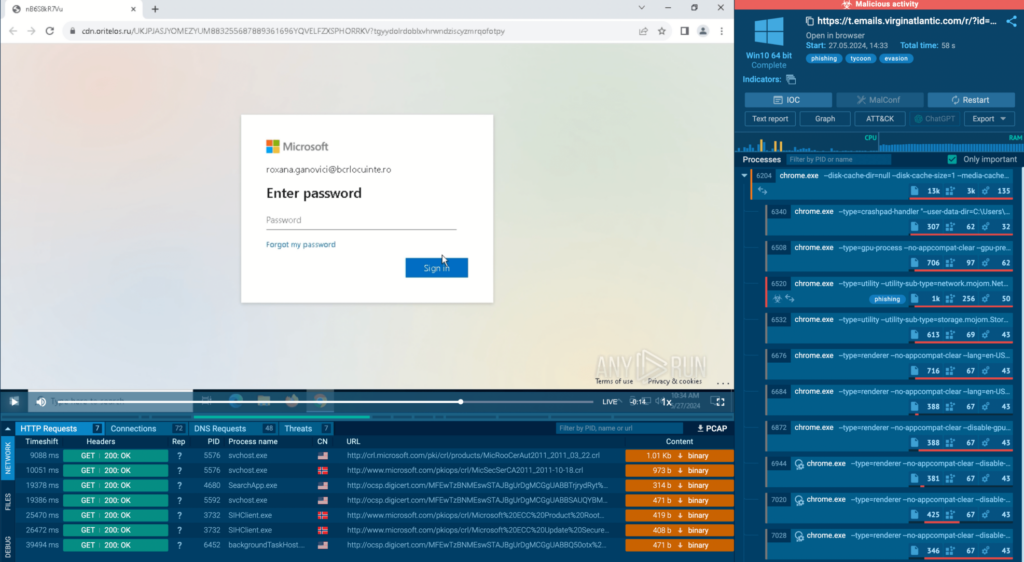
Or, if the malware involves unpacking files or completing installer instructions, the analyst can manually execute each step and see exactly what the malware does at every stage.
This real-time interaction also means that the analyst can simulate different user behaviors:
- Enable macros in Microsoft Office.
- Click through an installation wizard.
- Open attachments.
- Navigate through system prompts.
- Paste or copy content from the VM clipboard.
All of it helps progress the analysis session forward and collect valuable information on the malware’s triggers and the full scope of its capabilities, which might remain hidden in a fully automated system.
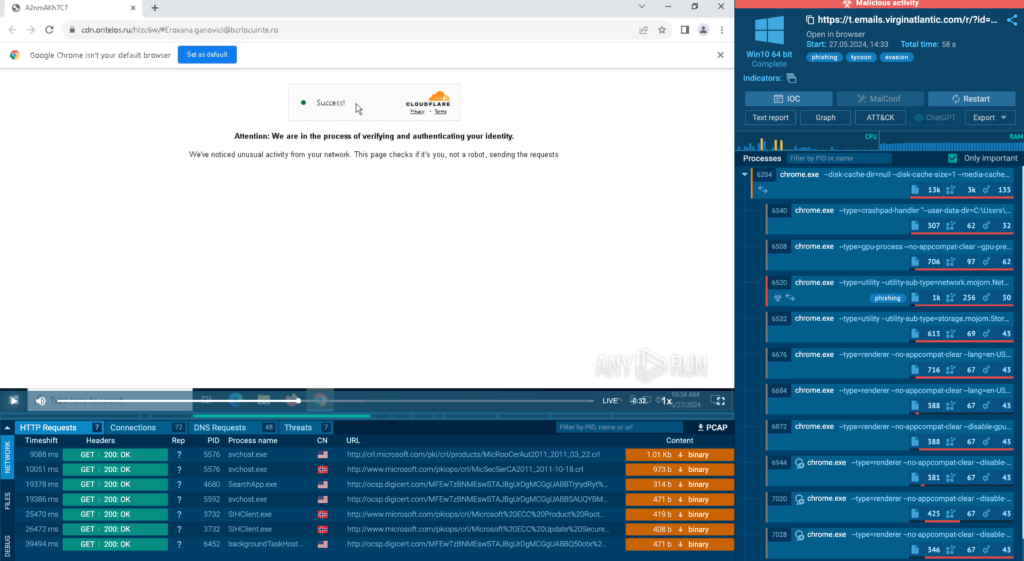
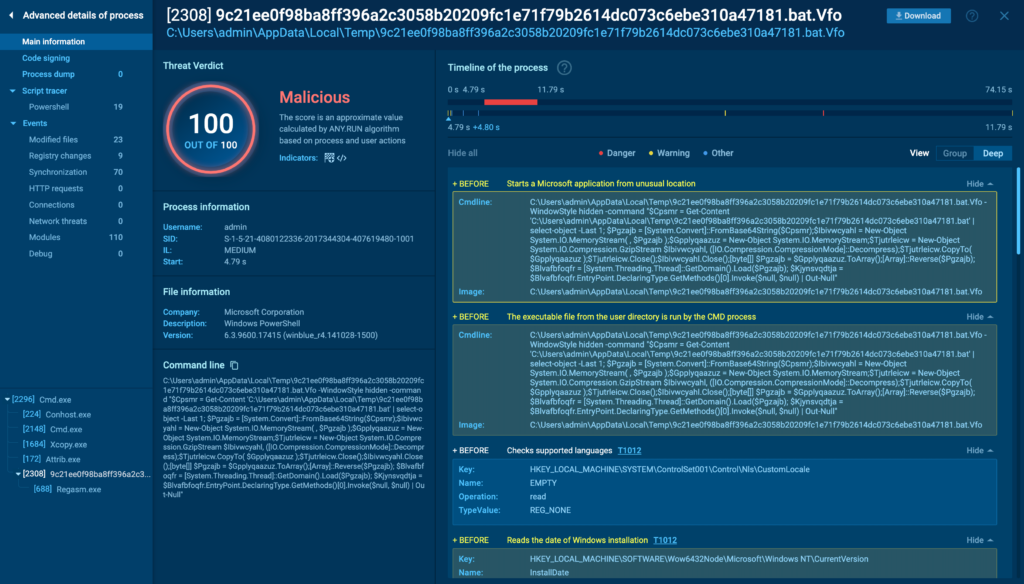
After the analysis session, like the example above, ANY.RUN saves the recording. You can pause, rewind, and replay specific actions within the sandbox and dive deep into each process spawned by the sample.
Benefits of Using an Interactive Malware Sandbox
Interactive malware sandboxes offer several advantages:
- Better detection. Many advanced malware strains can detect a sandbox, and then “play dead,” which leads to false negatives. An interactive sandbox, however, allows analysts to trigger execution. For example, by mimicking user inputs like realistic mouse movement or typing.
- Speed. Because you can interact directly with the malware and see effects of your actions in real-time, you can quickly identify and understand the threat.
- Deep insights. By manually navigating through the malware’s processes — whether it’s completing an installation, opening files, or executing commands — you can get a holistic view of the threat.
Finally, there is the collaborative potential of interactive sandboxes. For example, at ANY.RUN, we offer features that allow multiple analysts to work together on a single sample or easily share different reports. This helps to share insights within the team, or works great when a pair of senior and junior analysts analyze a sample together.
Who is an Interactive Malware Analysis Sandbox For?
Interactive malware analysis sandboxes are primarily for cybersecurity professionals, particularly those involved in malware analysis, SOC and incident response.
- Cybersecurity Analysts and SOC team members are the primary users of interactive sandboxes.
- Incident Responders also benefit greatly from these tools — in the event of a security breach, time is critical and interactive sandboxes help rapidly analyze threats.
- Threat Intelligence Teams can use interactive sandboxes to gather detailed information about emerging threats.
In terms of types of companies, large enterprises, financial institutions, managed service providers, and healthcare organizations are prime examples, but the list is not limited to them. These organizations are often targets of cyberattacks and deal with sensitive data that must be protected at all costs.
Conclusion
Interactive malware sandboxes are powerful when it comes to understanding and combating complex threats.
By allowing real-time interaction and detailed exploration, they provide insights that are often missed in traditional, automated analysis — in a landscape where new threats emerge constantly, having the ability to actively engage with and analyze malware in a controlled environment is essential.
About ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
With ANY.RUN you can:
- Detect malware in seconds.
- Interact with samples in real time.
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior.
- Collaborate with your team
- Scale as you need.







0 comments